mirror of https://github.com/docker/docs.git
Merge branch 'master' into spelling
This commit is contained in:
commit
eb608ee28d
|
|
@ -116,6 +116,16 @@ You only need to set up the repository once, after which you can install Docker
|
|||
|
||||
{% endif %}
|
||||
|
||||
{% if linux-dist == "oraclelinux" %}
|
||||
|
||||
5. Enable the `ol7_addons` Oracle repository. This ensures access to the `container-selinux` package required by `docker-ee`.
|
||||
|
||||
```bash
|
||||
$ sudo yum-config-manager --enable ol7_addons
|
||||
```
|
||||
|
||||
{% endif %}
|
||||
|
||||
6. Add the Docker EE **stable** repository:
|
||||
|
||||
```bash
|
||||
|
|
|
|||
|
|
@ -42,20 +42,24 @@ $ curl -fsSL https://get.docker.com -o get-docker.sh
|
|||
$ sudo sh get-docker.sh
|
||||
|
||||
<output truncated>
|
||||
```
|
||||
|
||||
If you would like to use Docker as a non-root user, you should now consider
|
||||
adding your user to the "docker" group with something like:
|
||||
|
||||
```bash
|
||||
sudo usermod -aG docker your-user
|
||||
```
|
||||
|
||||
Remember to log out and back in for this to take effect!
|
||||
|
||||
WARNING: Adding a user to the "docker" group grants the ability to run
|
||||
containers which can be used to obtain root privileges on the
|
||||
docker host.
|
||||
Refer to https://docs.docker.com/engine/security/security/#docker-daemon-attack-surface
|
||||
for more information.
|
||||
```
|
||||
> **Warning**:
|
||||
>
|
||||
> Adding a user to the "docker" group grants the ability to run containers
|
||||
> which can be used to obtain root privileges on the docker host. Refer to
|
||||
> [Docker Daemon Attack Surface](https://docs.docker.com/engine/security/security/#docker-daemon-attack-surface)
|
||||
> for more information.
|
||||
{:.warning}
|
||||
|
||||
Docker CE is installed. It starts automatically on `DEB`-based distributions. On
|
||||
`RPM`-based distributions, you need to start it manually using the appropriate
|
||||
|
|
|
|||
|
|
@ -12,11 +12,12 @@ Usage: {% include kubernetes-mac-win.md platform="mac" %}
|
|||
{% if platform == "mac" %}
|
||||
{% assign product = "Docker for Mac" %}
|
||||
|
||||
{% capture min-version %}{{ product }} 17.12 CE Edge{% endcapture %}
|
||||
{% capture min-version %}{{ product }} 17.12 CE{% endcapture %}
|
||||
{% capture min-stable-version %}{{ product }} 18.06 CE{% endcapture %}
|
||||
|
||||
{% capture version-caveat %}
|
||||
**Kubernetes is only available in {{ min-version }} and higher, on the Edge
|
||||
channel.** Kubernetes support is not included in Docker for Mac Stable releases.
|
||||
**Kubernetes is only available in {{ min-version }} and higher on the Edge channel, and in {{ in-stable-version }} and higher in the Stable channel**
|
||||
|
||||
{% endcapture %}
|
||||
|
||||
{% capture local-kubectl-warning %}
|
||||
|
|
@ -32,11 +33,11 @@ channel.** Kubernetes support is not included in Docker for Mac Stable releases.
|
|||
{% elsif platform == "windows" %}
|
||||
{% assign product = "Docker for Windows" %}
|
||||
|
||||
{% capture min-version %}{{ product }} 18.02 CE Edge{% endcapture %}
|
||||
{% capture min-version %}{{ product }} 18.02 CE{% endcapture %}
|
||||
{% capture min-stable-version %}{{ product }} 18.06 CE{% endcapture %}
|
||||
|
||||
{% capture version-caveat %}
|
||||
**Kubernetes is only available in {{ min-version }}.** Kubernetes
|
||||
support is not included in {{ product }} 18.02 CE Stable.
|
||||
**Kubernetes is only available in {{ min-version }} and higher on the Edge channel, and in {{ in-stable-version }} and higher in the Stable channel**
|
||||
{% endcapture %}
|
||||
|
||||
{% capture local-kubectl-warning %}
|
||||
|
|
|
|||
|
|
@ -55,8 +55,8 @@ configure this app to use our SQL Server database, and then create a
|
|||
|
||||
This file defines how to build the web app image. It uses the
|
||||
[microsoft/aspnetcore-build](https://hub.docker.com/r/microsoft/aspnetcore-build/),
|
||||
map the volume with the generated code, restore the dependencies, build the
|
||||
project and expose port 80. After that, it calls an `entrypoint` script
|
||||
maps the volume with the generated code, restores the dependencies, builds the
|
||||
project and exposes port 80. After that, it calls an `entrypoint` script
|
||||
that we create in the next step.
|
||||
|
||||
1. The `Dockerfile` makes use of an entrypoint to your webapp Docker
|
||||
|
|
|
|||
|
|
@ -29,7 +29,7 @@ On a Mac, add the following to your `~/.bash_profile`:
|
|||
|
||||
```shell
|
||||
if [ -f $(brew --prefix)/etc/bash_completion ]; then
|
||||
. $(brew --prefix)/etc/bash_completion
|
||||
. $(brew --prefix)/etc/bash_completion
|
||||
fi
|
||||
```
|
||||
|
||||
|
|
|
|||
|
|
@ -54,7 +54,7 @@ script:
|
|||
check. For example, you might want to wait until Postgres is definitely
|
||||
ready to accept commands:
|
||||
|
||||
#!/bin/bash
|
||||
#!/bin/sh
|
||||
# wait-for-postgres.sh
|
||||
|
||||
set -e
|
||||
|
|
|
|||
|
|
@ -57,7 +57,7 @@ driver options.
|
|||
| Option | Required | Description |
|
||||
|:------------|:---------|:-------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------|
|
||||
| `tag` | optional | Specify template to set `CONTAINER_TAG` and `SYSLOG_IDENTIFIER` value in journald logs. Refer to [log tag option documentation](/engine/admin/logging/log_tags/) to customize the log tag format |
|
||||
| `label` | optional | Comma-separated list of keys of labels, which should be included in message, if these labels are specified for the container. |
|
||||
| `labels` | optional | Comma-separated list of keys of labels, which should be included in message, if these labels are specified for the container. |
|
||||
| `env` | optional | Comma-separated list of keys of environment variables, which should be included in message, if these variables are specified for the container. |
|
||||
| `env-regex` | optional | Similar to and compatible with env. A regular expression to match logging-related environment variables. Used for advanced [log tag options](/engine/admin/logging/log_tags/). |
|
||||
|
||||
|
|
|
|||
|
|
@ -9,7 +9,7 @@ keywords: "docker, daemon, configuration"
|
|||
|
||||
By default, a container has no resource constraints and can use as much of a
|
||||
given resource as the host's kernel scheduler allows. Docker provides ways
|
||||
to control how much memory, CPU, or block IO a container can use, setting runtime
|
||||
to control how much memory, or CPU a container can use, setting runtime
|
||||
configuration flags of the `docker run` command. This section provides details
|
||||
on when you should set such limits and the possible implications of setting them.
|
||||
|
||||
|
|
|
|||
|
|
@ -97,5 +97,5 @@ pipelines.
|
|||
Also, users don't need access to all repositories in the promotion pipeline.
|
||||
A repository admin can define the promotion policies, and only
|
||||
allow access to push to the first repository in that pipeline. Once users push
|
||||
to the fist repository, the image gets promoted to the other repositories as
|
||||
to the first repository, the image gets promoted to the other repositories as
|
||||
long as it satisfies the promotion policies.
|
||||
|
|
|
|||
|
|
@ -47,7 +47,7 @@ need to do the same procedure for every one of them.
|
|||
### Configure your Notary client
|
||||
|
||||
Start by [configuring your Notary client](../../access-dtr/configure-your-notary-client.md).
|
||||
This ensures the Docker an Notary CLI clients know about your UCP private keys.
|
||||
This ensures the Docker and Notary CLI clients know about your UCP private keys.
|
||||
|
||||
### Initialize the trust metadata
|
||||
|
||||
|
|
|
|||
|
|
@ -9,7 +9,7 @@ title: Docker for Azure Release Notes
|
|||
## Enterprise Edition
|
||||
[Docker Enterprise Edition Lifecycle](https://success.docker.com/Policies/Maintenance_Lifecycle){: target="_blank"}<!--_-->
|
||||
|
||||
[Deploy Docker Enterprise Edition (EE) for AWS](https://store.docker.com/editions/enterprise/docker-ee-aws?tab=description){: target="_blank" class="button outline-btn"}
|
||||
[Deploy Docker Enterprise Edition (EE) for Azure](https://store.docker.com/editions/enterprise/docker-ee-azure?tab=description){: target="_blank" class="button outline-btn"}
|
||||
|
||||
### 17.06 EE
|
||||
|
||||
|
|
|
|||
|
|
@ -18,6 +18,27 @@ for Windows](install.md#download-docker-for-windows).
|
|||
|
||||
## Edge Releases of 2018
|
||||
|
||||
### Docker Community Edition 2.0.0.0-beta1-win75 2018-09-14
|
||||
|
||||
[Download](https://download.docker.com/win/edge/19925/Docker%20for%20Windows%20Installer.exe)
|
||||
|
||||
* Upgrades
|
||||
- [Docker 18.09.0-ce-beta1](https://github.com/docker/docker-ce/releases/tag/v18.09.0-ce-beta1)
|
||||
- Linux Kernel 4.9.125
|
||||
|
||||
* New
|
||||
- New version scheme
|
||||
|
||||
* Deprecation
|
||||
- Removed support of AUFS
|
||||
|
||||
* Bug fixes and minor changes
|
||||
- LCOW does not anymore need --platform flag on multi-arch images
|
||||
- Better WCOW host.docker.internal resolution on host, don't rewrite it if not modified. From [docker/for-win#1976](https://github.com/docker/for-win/issues/1976)
|
||||
- Disk size can now be ajusted from 32GiB to drive space.
|
||||
- Fix dns update too verbose in logs
|
||||
- Fix panic in diagnose
|
||||
|
||||
### Docker Community Edition 18.06.1-ce-win74 2018-08-29
|
||||
|
||||
[Download](https://download.docker.com/win/edge/19508/Docker%20for%20Windows%20Installer.exe)
|
||||
|
|
|
|||
|
|
@ -69,7 +69,7 @@ Do the following each time:
|
|||
4. Install a different version of the app (Stable or Edge).
|
||||
|
||||
|
||||
### Feeback
|
||||
### Feedback
|
||||
#### What kind of feedback are we looking for?
|
||||
|
||||
Everything is fair game. We'd like your impressions on the download-install
|
||||
|
|
|
|||
|
|
@ -39,7 +39,7 @@ guarantees. For more information, see
|
|||
|
||||
Looking for information on using Windows containers?
|
||||
|
||||
* [Switch between Windows and Linux containers](index.md#switch-between-windows-and-linux-containers) describes the Linux / Windows containers toggle in Docker for Windows and points you to the tutorial mentioned above.
|
||||
* [Switch between Windows and Linux containers](https://docs.docker.com/docker-for-windows/#switch-between-windows-and-linux-containers) describes the Linux / Windows containers toggle in Docker for Windows and points you to the tutorial mentioned above.
|
||||
* [Getting Started with Windows Containers (Lab)](https://github.com/docker/labs/blob/master/windows/windows-containers/README.md)
|
||||
provides a tutorial on how to set up and run Windows containers on Windows 10 or
|
||||
with Windows Server 2016. It shows you how to use a MusicStore application with
|
||||
|
|
|
|||
|
|
@ -76,7 +76,7 @@ This is for development purpose and will not work in a production environment ou
|
|||
|
||||
The gateway is also reachable as `gateway.docker.internal`.
|
||||
|
||||
#### I want to connect to a container from the Windows
|
||||
#### I want to connect to a container from Windows
|
||||
|
||||
Port forwarding works for `localhost`; `--publish`, `-p`, or `-P` all work.
|
||||
Ports exposed from Linux are forwarded to the host.
|
||||
|
|
|
|||
|
|
@ -11,29 +11,28 @@ skip to [Creating an Automated Build](github.md#creating-an-automated-build).
|
|||
|
||||
> *Note:*
|
||||
> Automated Builds currently require *read* and *write* access since
|
||||
> [Docker Hub](https://hub.docker.com) needs to set up a GitHub service
|
||||
> hook. We have no choice here, this is how GitHub manages permissions.
|
||||
> [Docker Hub](https://hub.docker.com) needs to set up a GitHub webhook.
|
||||
> We have no choice here – this is how GitHub manages permissions.
|
||||
> We do guarantee nothing else is touched in your account.
|
||||
|
||||
To set up an Automated Build of a repository on GitHub, you need to
|
||||
link [Docker Hub](https://hub.docker.com/account/authorized-services/) to your
|
||||
GitHub account. This allows the registry to see your GitHub repositories.
|
||||
|
||||
To add, remove or view your linked account, go to the "Linked Accounts &
|
||||
Services" section of your Hub profile "Settings".
|
||||
To add, remove or view your linked account, log in to your Docker Hub account. Select **Settings > Linked Accounts & Services**.
|
||||
|
||||

|
||||
|
||||
When linking to GitHub, select either "Public and Private",
|
||||
or "Limited Access" linking.
|
||||
When linking to GitHub, select either ***Public and Private***,
|
||||
or ***Limited Access***.
|
||||
|
||||

|
||||
|
||||
The "Public and Private" option is the easiest to use, as it grants the Docker
|
||||
The ***Public and Private*** option is the easiest to use, as it grants the Docker
|
||||
Hub full access to all of your repositories. GitHub also allows you to grant
|
||||
access to repositories belonging to your GitHub organizations.
|
||||
|
||||
If you choose "Limited Access", Docker Hub only gets permission to access your
|
||||
If you choose ***Limited Access***, Docker Hub only gets permission to access your
|
||||
public data and public repositories.
|
||||
|
||||
Follow the onscreen instructions to authorize and link your GitHub account to
|
||||
|
|
@ -43,30 +42,30 @@ which to create the Automatic Build.
|
|||
You can review and revoke Docker Hub's access by visiting the
|
||||
[GitHub User's Applications settings](https://github.com/settings/applications).
|
||||
|
||||
> **Note**: If you delete the GitHub account linkage that is used for one of your
|
||||
> automated build repositories, the previously built images are still available.
|
||||
> **Note**: If you delete the connection to the GitHub account that is used for one of your
|
||||
> automated build repositories, previously built images are still available.
|
||||
> If you re-link to that GitHub account later, the automated build can be started
|
||||
> using the "Start Build" button on the Hub, or if the webhook on the GitHub repository
|
||||
> using the **Start Build** button on the Hub, or if the webhook on the GitHub repository
|
||||
> still exists, it is triggered by any subsequent commits.
|
||||
|
||||
## Auto builds and limited linked GitHub accounts.
|
||||
## Auto builds and limited linked GitHub accounts
|
||||
|
||||
If you selected to link your GitHub account with only a "Limited Access" link,
|
||||
then after creating your automated build, you need to either manually
|
||||
trigger a Docker Hub build using the "Start a Build" button, or add the GitHub
|
||||
webhook manually, as described in [GitHub Service
|
||||
Hooks](github.md#github-service-hooks). This only works for repositories
|
||||
under the user account, and adding an automated build to a public GitHub
|
||||
organization using a "Limited Access" link is not possible.
|
||||
If you chose ***Limited Access*** for your Github account connection, after creating your automated build,
|
||||
you will need to either:
|
||||
* Manually trigger a Docker Hub build using the **Start a Build** button, or
|
||||
* Add the GitHub webhook manually, as described in [GitHub Webhook](github.md#github-webhook).
|
||||
|
||||
This only works for repositories under the user account, and adding an automated build to a public GitHub
|
||||
organization using a ***Limited Access*** link is not possible.
|
||||
|
||||
## Changing the GitHub user link
|
||||
|
||||
If you want to remove, or change the level of linking between your GitHub
|
||||
account and the Docker Hub, you need to do this in two places.
|
||||
account and the Docker Hub, you need to make the change in two places.
|
||||
|
||||
First, remove the "Linked Account" from your Docker Hub "Settings". Then go to
|
||||
your GitHub account's Personal settings, and in the "Applications" section,
|
||||
"Revoke access".
|
||||
First, remove the **Linked Account** from your Docker Hub **Settings**. Then go to
|
||||
your GitHub account's Personal settings, and in the **Applications** section,
|
||||
***Revoke access***.
|
||||
|
||||
You can now re-link your account at any time.
|
||||
|
||||
|
|
@ -76,20 +75,20 @@ GitHub organizations and private repositories forked from organizations are
|
|||
made available to auto build using the "Docker Hub Registry" application, which
|
||||
needs to be added to the organization - and then applies to all users.
|
||||
|
||||
To check, or request access, go to your GitHub user's "Setting" page, select the
|
||||
"Applications" section from the left side bar, then click the "View" button for
|
||||
To check, or request access, go to your GitHub **Settings** page, select the
|
||||
**Applications** section from the left side bar, then click the **View** button for
|
||||
"Docker Hub Registry".
|
||||
|
||||

|
||||
|
||||
The organization's administrators may need to go to the Organization's "Third
|
||||
party access" screen in "Settings" to grant or deny access to the Docker Hub
|
||||
The organization's administrators may need to go to the Organization's **Third
|
||||
party access** screen in **Settings** to grant or deny access to the Docker Hub
|
||||
Registry application. This change applies to all organization members.
|
||||
|
||||

|
||||
|
||||
More detailed access controls to specific users and GitHub repositories can be
|
||||
managed using the GitHub "People and Teams" interfaces.
|
||||
managed using the GitHub **People and Teams** interfaces.
|
||||
|
||||
## Creating an Automated Build
|
||||
|
||||
|
|
@ -178,26 +177,36 @@ build.
|
|||
</tbody>
|
||||
</table>
|
||||
|
||||
## GitHub service hooks
|
||||
## GitHub webhook
|
||||
|
||||
A GitHub Service hook allows GitHub to notify the Docker Hub when something has
|
||||
A GitHub webhook allows GitHub to notify the Docker Hub when something has
|
||||
been committed to a given git repository.
|
||||
|
||||
When you create an Automated Build from a GitHub user that has full "Public and
|
||||
Private" linking, a Service Hook should get automatically added to your GitHub
|
||||
When you create an Automated Build from a GitHub user that has full **Public and
|
||||
Private** linking, a Service Hook should get automatically added to your GitHub
|
||||
repository.
|
||||
|
||||
If your GitHub account link to the Docker Hub is "Limited Access", then you
|
||||
need to add the Service Hook manually.
|
||||
If your GitHub account link to the Docker Hub is **Limited Access**, then you
|
||||
need to add the webhook manually.
|
||||
|
||||
To add, confirm, or modify the service hook, log in to GitHub, then navigate to
|
||||
the repository, click "Settings" (the gear), then select "Webhooks & Services".
|
||||
You must have Administrator privileges on the repository to view or modify
|
||||
this setting.
|
||||
To add, confirm, or modify the webhook, log in to GitHub, then navigate to
|
||||
the repository. Within the repository, select **Settings > Webhooks**.
|
||||
You must have admin privileges on the repository to view or modify
|
||||
this setting. Click **Add webhook**, and use the following settings:
|
||||
|
||||
The image below shows the "Docker" Service Hook.
|
||||
|
||||

|
||||
| Field | Value |
|
||||
| ------|------ |
|
||||
| Payload URL | https://registry.hub.docker.com/hooks/github |
|
||||
| Content type | application/json |
|
||||
| Which events would you like to trigger this webhook? | Just the push event |
|
||||
| Active | checked |
|
||||
|
||||
The image below shows the **Webhooks/Add webhook** form with the above settings reflected:
|
||||
|
||||

|
||||
|
||||
If configured correctly, you'll see this in the **Webhooks** view
|
||||

|
||||
|
||||
|
||||
If you add the "Docker" service manually, make sure the "Active" checkbox is
|
||||
selected and click the "Update service" button to save your changes.
|
||||
|
|
|
|||
Binary file not shown.
|
After Width: | Height: | Size: 255 KiB |
Binary file not shown.
|
After Width: | Height: | Size: 125 KiB |
|
|
@ -18,8 +18,11 @@ If you're unable to submit a new case using the support page, fill in the
|
|||
company email address.
|
||||
|
||||
Docker Support engineers may ask you to provide a UCP support dump, which is an
|
||||
archive that contains UCP system logs and diagnostic information. To obtain a
|
||||
support dump:
|
||||
archive that contains UCP system logs and diagnostic information. If a node is not joined to the cluster and healthy, the support dump from the web UI will not contain logs from the unhealthy node. For unhealthy nodes use the CLI to get a support dump.
|
||||
|
||||
## Use the Web UI to get a support dump
|
||||
|
||||
To get the support dump from the Web UI:
|
||||
|
||||
1. Log into the UCP web UI with an administrator account.
|
||||
2. In the top-left menu, click your username and choose
|
||||
|
|
|
|||
|
|
@ -141,6 +141,8 @@ Click **Yes** to enable integrating UCP users and teams with LDAP servers.
|
|||
| No simple pagination | If your LDAP server doesn't support pagination. |
|
||||
| Just-In-Time User Provisioning | Whether to create user accounts only when users log in for the first time. The default value of `true` is recommended. If you upgraded from UCP 2.0.x, the default is `false`. |
|
||||
|
||||
> **Note:** LDAP connections using certificates created with TLS v1.2 do not currently advertise support for sha512WithRSAEncryption in the TLS handshake which leads to issues establishing connections with some clients. Support for advertising sha512WithRSAEncryption will be added in UCP 3.1.0.
|
||||
|
||||
{: .with-border}
|
||||
|
||||
Click **Confirm** to add your LDAP domain.
|
||||
|
|
|
|||
|
|
@ -126,7 +126,7 @@ Follow the steps below to configure multiple IP addresses per VM NIC.
|
|||
--secret=azure_ucp_admin.toml \
|
||||
--log-driver json-file \
|
||||
--log-opt max-size=1m \
|
||||
--env IPCOUNT=128 \
|
||||
--env IP_COUNT=128 \
|
||||
--name ipallocator \
|
||||
--constraint "node.platform.os == linux" \
|
||||
docker4x/az-nic-ips
|
||||
|
|
|
|||
|
|
@ -66,7 +66,7 @@ host types:
|
|||
| managers | TCP 2376 (configurable) | Internal | Port for the Docker Swarm manager. Used for backwards compatibility |
|
||||
| managers | TCP 2377 (configurable) | Internal, | Port for control communication between swarm nodes |
|
||||
| managers, workers | UDP 4789 | Internal, | Port for overlay networking |
|
||||
| managers | TCP 6443 (configurable) | External, Internal | Port for Kubernetes API server |
|
||||
| managers | TCP 6443 (configurable) | External, Internal | Port for Kubernetes API server endpoint |
|
||||
| managers, workers | TCP 6444 | Self | Port for Kubernetes API reverse proxy |
|
||||
| managers, workers | TCP, UDP 7946 | Internal | Port for gossip-based clustering |
|
||||
| managers, workers | TCP 10250 | Internal | Port for Kubelet |
|
||||
|
|
@ -80,7 +80,7 @@ host types:
|
|||
| managers | TCP 12384 | Internal | Port for the authentication storage backend for replication across managers |
|
||||
| managers | TCP 12385 | Internal | Port for the authentication service API |
|
||||
| managers | TCP 12386 | Internal | Port for the authentication worker |
|
||||
| managers | TCP 12387 | Internal | Port for the metrics service |
|
||||
| managers | TCP 12388 | Internal | Internal Port for the Kubernetes API Server |
|
||||
|
||||
## Enable ESP traffic
|
||||
|
||||
|
|
|
|||
Binary file not shown.
|
Before Width: | Height: | Size: 25 KiB After Width: | Height: | Size: 107 KiB |
|
|
@ -22,9 +22,9 @@ routing in UCP:
|
|||
|
||||

|
||||
|
||||
An Interlock service starts running on a manager node, an Interlock-extension
|
||||
service starts running on a worker node, and two replicas of the
|
||||
Interlock-proxy service run on worker nodes.
|
||||
The Interlock service starts a single replica on a manager node. The
|
||||
Interlock-extension service runs a single replica on any available node, and
|
||||
the Interlock-proxy service starts two replicas on any available node.
|
||||
|
||||
If you don't have any worker nodes in your cluster, then all Interlock
|
||||
components run on manager nodes.
|
||||
|
|
|
|||
|
|
@ -7,7 +7,7 @@ keywords: routing, proxy
|
|||
|
||||
To enable support for layer 7 routing, also known as HTTP routing mesh,
|
||||
log in to the UCP web UI as an administrator, navigate to the **Admin Settings**
|
||||
page, and click the **Routing Mesh** option. Check the **Enable routing mesh** option.
|
||||
page, and click the **Layer 7 Routing** option. Check the **Enable Layer 7 Routing** option.
|
||||
|
||||
{: .with-border}
|
||||
|
||||
|
|
|
|||
|
|
@ -7,7 +7,7 @@ redirect_from:
|
|||
---
|
||||
|
||||
Docker Enterprise Edition enables deploying [Docker Compose](/compose/overview.md/)
|
||||
files to Kubernetes clusters. Starting in Compile file version 3.3, you use the
|
||||
files to Kubernetes clusters. Starting in Compose file version 3.3, you use the
|
||||
same `docker-compose.yml` file that you use for Swarm deployments, but you
|
||||
specify **Kubernetes workloads** when you deploy the stack. The result is a
|
||||
true Kubernetes app.
|
||||
|
|
|
|||
|
|
@ -68,7 +68,7 @@ on a node depend on whether the node is a manager or a worker.
|
|||
|
||||
Internally, UCP uses the following components:
|
||||
|
||||
* Calico 3.0.1
|
||||
* Calico 3.0.8
|
||||
* Kubernetes 1.8.11
|
||||
|
||||
### UCP components in manager nodes
|
||||
|
|
|
|||
|
|
@ -11,9 +11,9 @@ This example demonstrates how to dockerize an ASP.NET Core application.
|
|||
## Why build ASP.NET Core?
|
||||
|
||||
- [Open-source](https://github.com/aspnet/home)
|
||||
- Develop and run your ASP.NET Core apps cross-platform on Windows, MacOS and
|
||||
- Develop and run your ASP.NET Core apps cross-platform on Windows, MacOS, and
|
||||
Linux
|
||||
- Great for modern cloud-based apps, such as web apps, IoT apps and mobile
|
||||
- Great for modern cloud-based apps, such as web apps, IoT apps, and mobile
|
||||
backends
|
||||
- ASP.NET Core apps can run on [.NET
|
||||
Core](https://www.microsoft.com/net/core/platform) or on the full [.NET
|
||||
|
|
@ -90,7 +90,7 @@ $ docker run -d -p 8080:80 --name myapp aspnetapp
|
|||
directly. You can get the IP address of your container with the following
|
||||
steps:
|
||||
1. Run `docker inspect -f "{% raw %}{{ .NetworkSettings.Networks.nat.IPAddress }}{% endraw %}" myapp`
|
||||
2. Copy the container ip address and paste into your browser.
|
||||
2. Copy the container IP address and paste into your browser.
|
||||
(For example, `172.16.240.197`)
|
||||
|
||||
## Further reading
|
||||
|
|
|
|||
|
|
@ -1,10 +1,10 @@
|
|||
---
|
||||
description: Running and installing a PostgreSQL service
|
||||
keywords: docker, example, package installation, postgresql
|
||||
keywords: docker, example, package installation, postgresql
|
||||
title: Dockerize PostgreSQL
|
||||
---
|
||||
|
||||
## Installing PostgreSQL on Docker
|
||||
## Install PostgreSQL on Docker
|
||||
|
||||
Assuming there is no Docker image that suits your needs on the [Docker
|
||||
Hub](http://hub.docker.com), you can create one yourself.
|
||||
|
|
@ -67,7 +67,7 @@ VOLUME ["/etc/postgresql", "/var/log/postgresql", "/var/lib/postgresql"]
|
|||
CMD ["/usr/lib/postgresql/9.3/bin/postgres", "-D", "/var/lib/postgresql/9.3/main", "-c", "config_file=/etc/postgresql/9.3/main/postgresql.conf"]
|
||||
```
|
||||
|
||||
Build an image from the Dockerfile assign it a name.
|
||||
Build an image from the Dockerfile and assign it a name.
|
||||
|
||||
```bash
|
||||
$ docker build -t eg_postgresql .
|
||||
|
|
@ -79,14 +79,14 @@ Run the PostgreSQL server container (in the foreground):
|
|||
$ docker run --rm -P --name pg_test eg_postgresql
|
||||
```
|
||||
|
||||
There are 2 ways to connect to the PostgreSQL server. We can use [*Link
|
||||
There are two ways to connect to the PostgreSQL server. We can use [*Link
|
||||
Containers*](../userguide/networking/default_network/dockerlinks.md), or we can access it from our host
|
||||
(or the network).
|
||||
|
||||
> **Note**: The `--rm` removes the container and its image when
|
||||
the container exits successfully.
|
||||
|
||||
### Using container linking
|
||||
### Use container linking
|
||||
|
||||
Containers can be linked to another container's ports directly using
|
||||
`-link remote_name:local_alias` in the client's
|
||||
|
|
@ -99,7 +99,7 @@ $ docker run --rm -t -i --link pg_test:pg eg_postgresql bash
|
|||
postgres@7ef98b1b7243:/$ psql -h $PG_PORT_5432_TCP_ADDR -p $PG_PORT_5432_TCP_PORT -d docker -U docker --password
|
||||
```
|
||||
|
||||
### Connecting from your host system
|
||||
### Connect from your host system
|
||||
|
||||
Assuming you have the postgresql-client installed, you can use the
|
||||
host-mapped port to test as well. You need to use `docker ps`
|
||||
|
|
@ -115,7 +115,7 @@ CONTAINER ID IMAGE COMMAND CREATED
|
|||
$ psql -h localhost -p 49153 -d docker -U docker --password
|
||||
```
|
||||
|
||||
### Testing the database
|
||||
### Test the database
|
||||
|
||||
Once you have authenticated and have a `docker =#`
|
||||
prompt, you can create a table and populate it.
|
||||
|
|
@ -138,7 +138,7 @@ $ docker=# select * from cities;
|
|||
(1 row)
|
||||
```
|
||||
|
||||
### Using the container volumes
|
||||
### Use the container volumes
|
||||
|
||||
You can use the defined volumes to inspect the PostgreSQL log files and
|
||||
to backup your configuration and data:
|
||||
|
|
|
|||
|
|
@ -7,7 +7,7 @@ title: Dockerize a Riak service
|
|||
The goal of this example is to show you how to build a Docker image with
|
||||
Riak pre-installed.
|
||||
|
||||
## Creating a Dockerfile
|
||||
## Create a Dockerfile
|
||||
|
||||
Create an empty file called `Dockerfile`:
|
||||
|
||||
|
|
|
|||
|
|
@ -621,20 +621,20 @@ labels to ensure that your service is deployed to the appropriate swarm nodes.
|
|||
|
||||
Use placement constraints to control the nodes a service can be assigned to. In
|
||||
the following example, the service only runs on nodes with the
|
||||
[label](engine/swarm/manage-nodes.md#add-or-remove-label-metadata)
|
||||
`region` set to `east`. If no appropriately-labelled nodes are available,
|
||||
deployment fails. The `--constraint` flag uses an equality operator
|
||||
(`==` or `!=`). For replicated services, it is possible that all services
|
||||
run on the same node, or each node only runs one replica, or that some nodes
|
||||
don't run any replicas. For global services, the service runs on every node
|
||||
that meets the placement constraint and any
|
||||
[resource requirements](#reserve-cpu-or-memory-for-a-service).
|
||||
[label](manage-nodes.md#add-or-remove-label-metadata) `region` set
|
||||
to `east`. If no appropriately-labelled nodes are available, tasks will wait in
|
||||
`Pending` until they become available. The `--constraint` flag uses an equality
|
||||
operator (`==` or `!=`). For replicated services, it is possible that all
|
||||
services run on the same node, or each node only runs one replica, or that some
|
||||
nodes don't run any replicas. For global services, the service runs on every
|
||||
node that meets the placement constraint and any [resource
|
||||
requirements](#reserve-cpu-or-memory-for-a-service).
|
||||
|
||||
```bash
|
||||
$ docker service create \
|
||||
--name my-nginx \
|
||||
--replicas 5 \
|
||||
--constraint region==east \
|
||||
--constraint node.labels.region==east \
|
||||
nginx
|
||||
```
|
||||
|
||||
|
|
@ -648,9 +648,9 @@ all nodes where `region` is set to `east` and `type` is not set to `devel`:
|
|||
```bash
|
||||
$ docker service create \
|
||||
--name my-nginx \
|
||||
--global \
|
||||
--constraint region==east \
|
||||
--constraint type!=devel \
|
||||
--mode global \
|
||||
--constraint node.labels.region==east \
|
||||
--constraint node.labels.type!=devel \
|
||||
nginx
|
||||
```
|
||||
|
||||
|
|
|
|||
|
|
@ -28,7 +28,7 @@ meets the prerequisites:
|
|||
|
||||
- A 64-bit installation
|
||||
- Version 3.10 or higher of the Linux kernel. The latest version of the kernel
|
||||
available for you platform is recommended.
|
||||
available for your platform is recommended.
|
||||
- `iptables` version 1.4 or higher
|
||||
- `git` version 1.7 or higher
|
||||
- A `ps` executable, usually provided by `procps` or a similar package.
|
||||
|
|
|
|||
|
|
@ -201,7 +201,7 @@ steps.
|
|||
#### Upgrade Docker CE
|
||||
|
||||
To upgrade Docker CE, follow the
|
||||
[installation instructions](#install-docker), choosing the new version you want
|
||||
[installation instructions](#install-docker-ce), choosing the new version you want
|
||||
to install.
|
||||
|
||||
### Install from a package
|
||||
|
|
|
|||
|
|
@ -280,7 +280,7 @@ steps. For Raspbian, you can optionally
|
|||
#### Upgrade Docker CE
|
||||
|
||||
To upgrade Docker CE, first run `sudo apt-get update`, then follow the
|
||||
[installation instructions](#install-docker), choosing the new version you want
|
||||
[installation instructions](#install-docker-ce), choosing the new version you want
|
||||
to install.
|
||||
|
||||
### Install from a package
|
||||
|
|
|
|||
|
|
@ -11,7 +11,7 @@ toc_max: 4
|
|||
|
||||
To get started with Docker CE on Fedora, make sure you
|
||||
[meet the prerequisites](#prerequisites), then
|
||||
[install Docker](#install-docker).
|
||||
[install Docker](#install-docker-ce).
|
||||
|
||||
## Prerequisites
|
||||
|
||||
|
|
@ -192,7 +192,7 @@ steps.
|
|||
#### Upgrade Docker CE
|
||||
|
||||
To upgrade Docker CE, follow the
|
||||
[installation instructions](#install-docker), choosing the new version you want
|
||||
[installation instructions](#install-docker-ce), choosing the new version you want
|
||||
to install.
|
||||
|
||||
### Install from a package
|
||||
|
|
|
|||
|
|
@ -33,7 +33,6 @@ To install Docker CE, you need the 64-bit version of one of these Ubuntu
|
|||
versions:
|
||||
|
||||
- Bionic 18.04 (LTS)
|
||||
- Artful 17.10
|
||||
- Xenial 16.04 (LTS)
|
||||
- Trusty 14.04 (LTS)
|
||||
|
||||
|
|
@ -289,7 +288,7 @@ steps.
|
|||
#### Upgrade Docker CE
|
||||
|
||||
To upgrade Docker CE, first run `sudo apt-get update`, then follow the
|
||||
[installation instructions](#install-docker), choosing the new version you want
|
||||
[installation instructions](#install-docker-ce), choosing the new version you want
|
||||
to install.
|
||||
|
||||
### Install from a package
|
||||
|
|
|
|||
|
|
@ -53,14 +53,6 @@ $ sudo yum remove docker \
|
|||
|
||||
{% include ee-linux-install-reuse.md section="using-yum-repo" %}
|
||||
|
||||
{% capture selinux-warning %}
|
||||
> Docker EE cannot install on {{ linux-dist-long }} with SELinux enabled
|
||||
>
|
||||
> If you have `selinux` enabled and you attempt to install Docker EE 17.06.1 or newer, you get an error that the `container-selinux` package cannot be found..
|
||||
{:.warning}
|
||||
{% endcapture %}
|
||||
{{ selinux-warning }}
|
||||
|
||||
### Set up the repository
|
||||
|
||||
{% include ee-linux-install-reuse.md section="set-up-yum-repo" %}
|
||||
|
|
|
|||
|
|
@ -32,7 +32,7 @@ This section lists what you need to consider before installing Docker EE. Items
|
|||
|
||||
### Architectures and storage drivers
|
||||
|
||||
Docker EE supports {{ linux-dist-long }} 64-bit, versions 7.1 and higher (7.1, 7.2, 7.3, 7.4), running on one of the following architectures: `x86_64`, `s390x` (IBM Z), or `ppc64le` (IBM Power, little endian format). To ensure you have `ppc64le` (and not `ppc64`), run the command, `uname -m`.
|
||||
Docker EE supports {{ linux-dist-long }} 64-bit, versions 7.1 and higher (7.1, 7.2, 7.3, 7.4, 7.5), running on one of the following architectures: `x86_64`, `s390x` (IBM Z), or `ppc64le` (IBM Power, little endian format). To ensure you have `ppc64le` (and not `ppc64`), run the command, `uname -m`.
|
||||
|
||||
> Little endian format only
|
||||
>
|
||||
|
|
|
|||
|
|
@ -313,7 +313,7 @@ To upgrade Docker EE:
|
|||
2. Run `sudo zypper refresh`.
|
||||
|
||||
3. Follow the
|
||||
[installation instructions](#install-docker), choosing the new version you want
|
||||
[installation instructions](#install-docker-ee), choosing the new version you want
|
||||
to install.
|
||||
|
||||
### Install from a package
|
||||
|
|
|
|||
|
|
@ -185,7 +185,7 @@ from the repository.
|
|||
$ sudo add-apt-repository \
|
||||
"deb [arch=amd64] $DOCKER_EE_URL/ubuntu \
|
||||
$(lsb_release -cs) \
|
||||
$DOCKER_EE_VERSION"
|
||||
stable-17.06"
|
||||
```
|
||||
|
||||
</div>
|
||||
|
|
@ -195,7 +195,7 @@ from the repository.
|
|||
$ sudo add-apt-repository \
|
||||
"deb [arch=s390x] $DOCKER_EE_URL/ubuntu \
|
||||
$(lsb_release -cs) \
|
||||
$DOCKER_EE_VERSION"
|
||||
stable-17.06"
|
||||
```
|
||||
|
||||
</div>
|
||||
|
|
@ -205,7 +205,7 @@ from the repository.
|
|||
$ sudo add-apt-repository \
|
||||
"deb [arch=ppc64el] $DOCKER_EE_URL/ubuntu \
|
||||
$(lsb_release -cs) \
|
||||
$DOCKER_EE_VERSION"
|
||||
stable-17.06"
|
||||
```
|
||||
|
||||
</div>
|
||||
|
|
@ -285,7 +285,7 @@ To upgrade Docker EE:
|
|||
2. Run `sudo apt-get update`.
|
||||
|
||||
3. Follow the
|
||||
[installation instructions](#install-docker), choosing the new version you want
|
||||
[installation instructions](#install-docker-ee), choosing the new version you want
|
||||
to install.
|
||||
|
||||
### Install from a package
|
||||
|
|
|
|||
|
|
@ -73,7 +73,7 @@ To create the `docker` group and add your user:
|
|||
|
||||
```bash
|
||||
$ sudo chown "$USER":"$USER" /home/"$USER"/.docker -R
|
||||
$ sudo chmod g+rwx "/home/$USER/.docker" -R
|
||||
$ sudo chmod g+rwx "$HOME/.docker" -R
|
||||
```
|
||||
|
||||
## Configure Docker to start on boot
|
||||
|
|
|
|||
|
|
@ -73,7 +73,7 @@ such as EC2 security groups), and then to follow the
|
|||
At the end of this procedure, all three Docker hosts will be joined to the swarm
|
||||
and will be connected together using an overlay network called `ingress`.
|
||||
|
||||
1. On `master`. initialize the swarm. If the host only has one network
|
||||
1. On `manager`. initialize the swarm. If the host only has one network
|
||||
interface, the `--advertise-addr` flag is optional.
|
||||
|
||||
```bash
|
||||
|
|
@ -192,7 +192,7 @@ connect a service to each of them.
|
|||
3. Run `docker service ls` to monitor the progress of service bring-up, which
|
||||
may take a few seconds.
|
||||
|
||||
4. Inspect the `nginx-net` network on `master`, `worker-1`, and `worker-2`.
|
||||
4. Inspect the `nginx-net` network on `manager`, `worker-1`, and `worker-2`.
|
||||
Remember that you did not need to create it manually on `worker-1` and
|
||||
`worker-2` because Docker created it for you. The output will be long, but
|
||||
notice the `Containers` and `Peers` sections. `Containers` lists all
|
||||
|
|
@ -295,7 +295,7 @@ open between the two Docker hosts:
|
|||
- TCP and UDP port 7946
|
||||
- UDP port 4789
|
||||
|
||||
One easy way to set this is up is to have two VMs (either local or on a cloud
|
||||
One easy way to set this up is to have two VMs (either local or on a cloud
|
||||
provider like AWS), each with Docker installed and running. If you're using AWS
|
||||
or a similar cloud computing platform, the easiest configuration is to use a
|
||||
security group that opens all incoming ports between the two hosts and the SSH
|
||||
|
|
|
|||
|
|
@ -241,9 +241,9 @@ When you connect to a published port on any swarm node (whether it is running a
|
|||
given service or not), you are redirected to a worker which is running that
|
||||
service, transparently. Effectively, Docker acts as a load balancer for your
|
||||
swarm services. Services using the routing mesh are running in _virtual IP (VIP)
|
||||
mode_. Even a service running on each node (by means of the `--global` flag)
|
||||
uses the routing mesh. When using the routing mesh, there is no guarantee about
|
||||
which Docker node services client requests.
|
||||
mode_. Even a service running on each node (by means of the `--mode global`
|
||||
flag) uses the routing mesh. When using the routing mesh, there is no guarantee
|
||||
about which Docker node services client requests.
|
||||
|
||||
To bypass the routing mesh, you can start a service using _DNS Round Robin
|
||||
(DNSRR) mode_, by setting the `--endpoint-mode` flag to `dnsrr`. You must run
|
||||
|
|
|
|||
|
|
@ -125,7 +125,7 @@ but the pinned certificates take highest priority for validation, followed
|
|||
by the pinned CA, followed by TOFUS (TOFU over HTTPS). The diagram below
|
||||
describes this validation flow:
|
||||
|
||||

|
||||
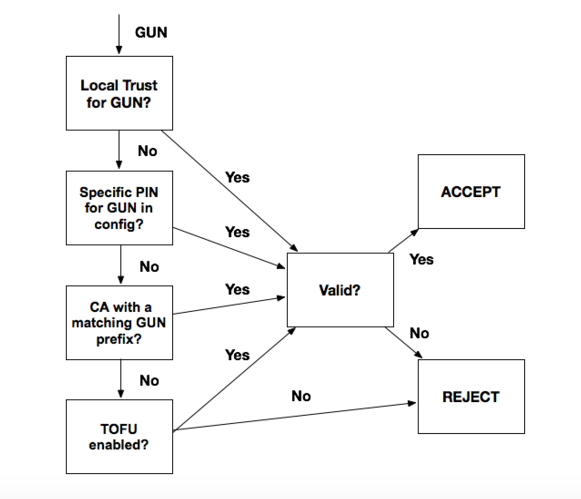
|
||||
|
||||
Only one trust pinning option is used to validate a GUN even if multiple
|
||||
sections are specified, and any validation failure results in a failed
|
||||
|
|
@ -176,6 +176,7 @@ passphrase.
|
|||
|`NOTARY_TARGETS_PASSPHRASE` | The targets (an online) key passphrase |
|
||||
|`NOTARY_SNAPSHOT_PASSPHRASE` | The snapshot (an online) key passphrase |
|
||||
|`NOTARY_DELEGATION_PASSPHRASE` | The delegation (an online) key passphrase |
|
||||
|`NOTARY_AUTH` | The notary server credentials: `<username>:<password>` encoded in base64 |
|
||||
|
||||
|
||||
If provided, the passphrase in `NOTARY_DELEGATION_PASSPHRASE`
|
||||
|
|
|
|||
|
|
@ -20,6 +20,206 @@ Release notes for stable versions are listed first. You can
|
|||
|
||||
# Stable releases
|
||||
|
||||
## 18.06.1-ce (2018-08-21)
|
||||
|
||||
### Builder
|
||||
|
||||
- Fix no error if build args are missing during docker build. [docker/engine#25](https://github.com/docker/engine/pull/25)
|
||||
+ Set BuildKit's ExportedProduct variable to show useful errors. [docker/engine#21](https://github.com/docker/engine/pull/21)
|
||||
|
||||
### Client
|
||||
|
||||
+ Various shell completion script updates: [docker/cli#1229](https://github.com/docker/cli/pull/1229),
|
||||
[docker/cli#1268](https://github.com/docker/cli/pull/1268), and [docker/cli#1272](https://github.com/docker/cli/pull/1272)
|
||||
- Fix `DOCKER_CONFIG` warning message and fallback search. [docker/cli#1241](https://github.com/docker/cli/pull/1241)
|
||||
- Fix help message flags on `docker stack` commands and sub-commands. [docker/cli#1267](https://github.com/docker/cli/pull/1267)
|
||||
|
||||
### Runtime
|
||||
|
||||
* Disable CRI plugin listening on port 10010 by default. [docker/engine#29](https://github.com/docker/engine/pull/29)
|
||||
* Update containerd to v1.1.2. [docker/engine#33](https://github.com/docker/engine/pull/33)
|
||||
- Windows: Do not invoke HCS shutdown if terminate called. [docker/engine#31](https://github.com/docker/engine/pull/31)
|
||||
* Windows: Select polling-based watcher for Windows log watcher. [docker/engine#34](https://github.com/docker/engine/pull/34)
|
||||
|
||||
### Swarm Mode
|
||||
|
||||
- Fix the condition used for skipping over running tasks. [docker/swarmkit#2677](https://github.com/docker/swarmkit/pull/2677)
|
||||
- Fix task sorting. [docker/swarmkit#2712](https://github.com/docker/swarmkit/pull/2712)
|
||||
|
||||
## 18.06.0-ce (2018-07-18)
|
||||
|
||||
### Important notes about this release
|
||||
|
||||
- Docker 18.06 CE will be the last release with a 4-month maintenance lifecycle. The planned Docker 18.09 CE release will be supported for 7 months with Docker 19.03 CE being the next release in line. More details about the release process can be found [here](https://docs.docker.com/install/).
|
||||
|
||||
### Builder
|
||||
|
||||
* Builder: fix layer leak on multi-stage wildcard copy. [moby/moby#37178](https://github.com/moby/moby/pull/37178)
|
||||
* Fix parsing of invalid environment variable substitution . [moby/moby#37134](https://github.com/moby/moby/pull/37134)
|
||||
* Builder: use the arch info from base image. [moby/moby#36816](https://github.com/moby/moby/pull/36816) [moby/moby#37197](https://github.com/moby/moby/pull/37197)
|
||||
+ New experimental builder backend based on [BuildKit](https://github.com/moby/buildkit). To enable, run daemon in experimental mode and set `DOCKER_BUILDKIT=1` environment variable on the docker CLI. [moby/moby#37151](https://github.com/moby/moby/pull/37151) [docker/cli#1111](https://github.com/docker/cli/pull/1111)
|
||||
- Fix handling uppercase targets names in multi-stage builds. [moby/moby#36960](https://github.com/moby/moby/pull/36960)
|
||||
|
||||
### Client
|
||||
|
||||
* Bump spf13/cobra to v0.0.3, pflag to v1.0.1. [moby/moby#37106](https://github.com/moby/moby/pull/37106)
|
||||
* Add support for the new Stack API for Kubernetes v1beta2. [docker/cli#899](https://github.com/docker/cli/pull/899)
|
||||
* K8s: more robust stack error detection on deploy. [docker/cli#948](https://github.com/docker/cli/pull/948)
|
||||
* Support for rollback config in compose 3.7. [docker/cli#409](https://github.com/docker/cli/pull/409)
|
||||
* Update Cobra and pflag, and use built-in --version feature. [docker/cli#1069](https://github.com/docker/cli/pull/1069)
|
||||
* Fix `docker stack deploy --prune` with empty name removing all services. [docker/cli#1088](https://github.com/docker/cli/pull/1088)
|
||||
* [Kubernetes] stack services filters. [docker/cli#1023](https://github.com/docker/cli/pull/1023)
|
||||
+ Only show orchestrator flag in root, stack and version commands in help. [docker/cli#1106](https://github.com/docker/cli/pull/1106)
|
||||
+ Add an `Extras` field on the compose config types. [docker/cli#1126](https://github.com/docker/cli/pull/1126)
|
||||
+ Add options to the compose loader. [docker/cli#1128](https://github.com/docker/cli/pull/1128)
|
||||
- Fix always listing nodes in docker stack ps command on Kubernetes. [docker/cli#1093](https://github.com/docker/cli/pull/1093)
|
||||
- Fix output being shown twice on stack rm error message. [docker/cli#1093](https://github.com/docker/cli/pull/1093)
|
||||
* Extend client API with custom HTTP requests. [moby/moby#37071](https://github.com/moby/moby/pull/37071)
|
||||
* Changed error message for unreadable files to clarify possibility of a .Dockerignore entry. [docker/cli#1053](https://github.com/docker/cli/pull/1053)
|
||||
* Restrict kubernetes.allNamespaces value to 'enabled' or 'disabled' in configuration file. [docker/cli#1087](https://github.com/docker/cli/pull/1087)
|
||||
* Check errors when initializing the docker client in the help command. [docker/cli#1119](https://github.com/docker/cli/pull/1119)
|
||||
* Better namespace experience with Kubernetes. Fix using namespace defined in ~/.kube/config for stack commands. Add a NAMESPACE column for docker stack ls command. Add a --all-namespaces flag for docker stack ls command. [docker/cli#991](https://github.com/docker/cli/pull/991)
|
||||
* Export Push and Save. [docker/cli#1123](https://github.com/docker/cli/pull/1123)
|
||||
* Export pull as a public function. [docker/cli#1026](https://github.com/docker/cli/pull/1026)
|
||||
* Remove Kubernetes commands from experimental. [docker/cli#1068](https://github.com/docker/cli/pull/1068)
|
||||
* Adding configs/secrets to service inspect pretty. [docker/cli#1006](https://github.com/docker/cli/pull/1006)
|
||||
- Fix service filtering by name on Kubernetes. [docker/cli#1101](https://github.com/docker/cli/pull/1101)
|
||||
- Fix component information alignment in `docker version`. [docker/cli#1065](https://github.com/docker/cli/pull/1065)
|
||||
- Fix cpu/memory limits and reservations being reset on service update. [docker/cli#1079](https://github.com/docker/cli/pull/1079)
|
||||
* Manifest list: request specific permissions. [docker/cli#1024](https://github.com/docker/cli/pull/1024)
|
||||
* Setting --orchestrator=all also sets --all-namespaces unless specific --namespace are set. [docker/cli#1059](https://github.com/docker/cli/pull/1059)
|
||||
- Fix panics when --compress and --stream are used together. [docker/cli#1105](https://github.com/docker/cli/pull/1105)
|
||||
* Switch from x/net/context to context. [docker/cli#1038](https://github.com/docker/cli/pull/1038)
|
||||
+ Add --init option to `docker service create`. [docker/cli#479](https://github.com/docker/cli/pull/479)
|
||||
+ Fixed bug displaying garbage output for build command when --stream and --quiet flags combined. [docker/cli#1090](https://github.com/docker/cli/pull/1090)
|
||||
+ Add `init` support in 3.7 schema. [docker/cli#1129](https://github.com/docker/cli/pull/1129)
|
||||
- Fix docker trust signer removal. [docker/cli#1112](https://github.com/docker/cli/pull/1112)
|
||||
- Fix error message from docker inspect. [docker/cli#1071](https://github.com/docker/cli/pull/1071)
|
||||
* Allow `x-*` extension on 3rd level objects. [docker/cli#1097](https://github.com/docker/cli/pull/1097)
|
||||
* An invalid orchestrator now generates an error instead of being silently ignored. [docker/cli#1055](https://github.com/docker/cli/pull/1055)
|
||||
* Added ORCHESTRATOR column to docker stack ls command. [docker/cli#973](https://github.com/docker/cli/pull/973)
|
||||
* Warn when using host-ip for published ports for services. [docker/cli#1017](https://github.com/docker/cli/pull/1017)
|
||||
+ Added the option to enable experimental cli features through the `DOCKER_CLI_EXPERIMENTAL` environment variable. [docker/cli#1138](https://github.com/docker/cli/pull/1138)
|
||||
+ Add exec_die to the list of known container events. [docker/cli#1028](https://github.com/docker/cli/pull/1028)
|
||||
* [K8s] Do env-variable expansion on the uninterpreted Config files. [docker/cli#974](https://github.com/docker/cli/pull/974)
|
||||
+ Print warnings on stderr for each unsupported features while parsing a compose file for deployment on Kubernetes. [docker/cli#903](https://github.com/docker/cli/pull/903)
|
||||
+ Added description about pids count. [docker/cli#1045](https://github.com/docker/cli/pull/1045)
|
||||
- Warn user of filter when pruning. [docker/cli#1043](https://github.com/docker/cli/pull/1043)
|
||||
- Fix `--rollback-*` options overwriting `--update-*` options. [docker/cli#1052](https://github.com/docker/cli/pull/1052)
|
||||
* Update Attach, Build, Commit, Cp, Create subcommand fish completions. [docker/cli#1005](https://github.com/docker/cli/pull/1005)
|
||||
+ Add bash completion for `dockerd --default-address-pool`. [docker/cli#1173](https://github.com/docker/cli/pull/1173)
|
||||
+ Add bash completion for `exec_die` event. [docker/cli#1173](https://github.com/docker/cli/pull/1173)
|
||||
* Update docker-credential-helper so `pass` is not called on every docker command. [docker/cli#1184](https://github.com/docker/cli/pull/1184)
|
||||
* Fix for rotating swarm external CA. [docker/cli#1199](https://github.com/docker/cli/pull/1199)
|
||||
* Improve version output alignment. [docker/cli#1207](https://github.com/docker/cli/pull/1207)
|
||||
+ Add bash completion for `service create|update --init`. [docker/cli#1210](https://github.com/docker/cli/pull/1210)
|
||||
|
||||
### Deprecation
|
||||
|
||||
* Document reserved namespaces deprecation. [docker/cli#1040](https://github.com/docker/cli/pull/1040)
|
||||
|
||||
### Logging
|
||||
|
||||
* Allow awslogs to use non-blocking mode. [moby/moby#36522](https://github.com/moby/moby/pull/36522)
|
||||
* Improve logging of long log lines on fluentd log driver.. [moby/moby#36159](https://github.com/moby/moby/pull/36159)
|
||||
* Re-order CHANGELOG.md to pass `make validate` test. [moby/moby#37047](https://github.com/moby/moby/pull/37047)
|
||||
* Update Events, Exec, Export, History, Images, Import, Inspect, Load, and Login subcommand fish completions. [docker/cli#1061](https://github.com/docker/cli/pull/1061)
|
||||
* Update documentation for RingLogger's ring buffer. [moby/moby#37084](https://github.com/moby/moby/pull/37084)
|
||||
+ Add metrics for log failures/partials. [moby/moby#37034](https://github.com/moby/moby/pull/37034)
|
||||
- Fix logging plugin crash unrecoverable. [moby/moby#37028](https://github.com/moby/moby/pull/37028)
|
||||
- Fix logging test type. [moby/moby#37070](https://github.com/moby/moby/pull/37070)
|
||||
- Fix race conditions in logs API. [moby/moby#37062](https://github.com/moby/moby/pull/37062)
|
||||
- Fix some issues in logfile reader and rotation. [moby/moby#37063](https://github.com/moby/moby/pull/37063)
|
||||
|
||||
### Networking
|
||||
|
||||
* Allow user to specify default address pools for docker networks. [moby/moby#36396](https://github.com/moby/moby/pull/36396) [docker/cli#818](https://github.com/docker/cli/pull/818)
|
||||
* Adding logs for ipam state [doccker/libnetwork#2417](https://github.com/docker/libnetwork/pull/2147)
|
||||
* Fix race conditions in the overlay network driver [doccker/libnetwork#2143](https://github.com/docker/libnetwork/pull/2143)
|
||||
* Add wait time into xtables lock warning [doccker/libnetwork#2142](https://github.com/docker/libnetwork/pull/2142)
|
||||
* filter xtables lock warnings when firewalld is active [doccker/libnetwork#2135](https://github.com/docker/libnetwork/pull/2135)
|
||||
* Switch from x/net/context to context [doccker/libnetwork#2140](https://github.com/docker/libnetwork/pull/2140)
|
||||
* Adding a recovery mechanism for a split gossip cluster [doccker/libnetwork#2134](https://github.com/docker/libnetwork/pull/2134)
|
||||
* Running docker inspect on network attachment tasks now returns a full task object. [moby/moby#35246](https://github.com/moby/moby/pull/35246)
|
||||
* Some container/network cleanups. [moby/moby#37033](https://github.com/moby/moby/pull/37033)
|
||||
- Fix network inspect for overlay network. [moby/moby#37045](https://github.com/moby/moby/pull/37045)
|
||||
* Improve Scalability of the Linux load balancing. [docker/engine#16](https://github.com/docker/engine/pull/16)
|
||||
* Change log level from error to warning. [docker/engine#19](https://github.com/docker/engine/pull/19)
|
||||
|
||||
### Runtime
|
||||
|
||||
* Aufs: log why aufs is not supported. [moby/moby#36995](https://github.com/moby/moby/pull/36995)
|
||||
* Hide experimental checkpoint features on Windows. [docker/cli#1094](https://github.com/docker/cli/pull/1094)
|
||||
* Lcow: Allow the client to customize capabilities and device cgroup rules for LCOW containers. [moby/moby#37294](https://github.com/moby/moby/pull/37294)
|
||||
* Changed path given for executable output in windows to actual location of executable output. [moby/moby#37295](https://github.com/moby/moby/pull/37295)
|
||||
+ Add windows recycle bin test and update hcsshim to v0.6.11. [moby/moby#36994](https://github.com/moby/moby/pull/36994)
|
||||
* Allow to add any args when doing a make run. [moby/moby#37190](https://github.com/moby/moby/pull/37190)
|
||||
* Optimize ContainerTop() aka docker top. [moby/moby#37131](https://github.com/moby/moby/pull/37131)
|
||||
- Fix compilation on 32bit machines. [moby/moby#37292](https://github.com/moby/moby/pull/37292)
|
||||
* Update API version to v1 38. [moby/moby#37141](https://github.com/moby/moby/pull/37141)
|
||||
- Fix `docker service update --host-add` does not update existing host entry. [docker/cli#1054](https://github.com/docker/cli/pull/1054)
|
||||
- Fix swagger file type for ExecIds. [moby/moby#36962](https://github.com/moby/moby/pull/36962)
|
||||
- Fix swagger volume type generation. [moby/moby#37060](https://github.com/moby/moby/pull/37060)
|
||||
- Fix wrong assertion in volume/service package. [moby/moby#37211](https://github.com/moby/moby/pull/37211)
|
||||
- Fix daemon panic on restart when a plugin is running. [moby/moby#37234](https://github.com/moby/moby/pull/37234)
|
||||
* Construct and add 'LABEL' command from 'label' option to last stage. [moby/moby#37011](https://github.com/moby/moby/pull/37011)
|
||||
- Fix race condition between exec start and resize.. [moby/moby#37172](https://github.com/moby/moby/pull/37172)
|
||||
* Alternative failure mitigation of `TestExecInteractiveStdinClose`. [moby/moby#37143](https://github.com/moby/moby/pull/37143)
|
||||
* RawAccess allows a set of paths to be not set as masked or readonly. [moby/moby#36644](https://github.com/moby/moby/pull/36644)
|
||||
* Be explicit about github.com prefix being a legacy feature. [moby/moby#37174](https://github.com/moby/moby/pull/37174)
|
||||
* Bump Golang to 1.10.3. [docker/cli#1122](https://github.com/docker/cli/pull/1122)
|
||||
* Close ReadClosers to prevent xz zombies. [moby/moby#34218](https://github.com/moby/moby/pull/34218)
|
||||
* Daemon.ContainerStop(): fix for a negative timeout. [moby/moby#36874](https://github.com/moby/moby/pull/36874)
|
||||
* Daemon.setMounts(): copy slice in place. [moby/moby#36991](https://github.com/moby/moby/pull/36991)
|
||||
* Describe IP field of swagger Port definition. [moby/moby#36971](https://github.com/moby/moby/pull/36971)
|
||||
* Extract volume interaction to a volumes service. [moby/moby#36688](https://github.com/moby/moby/pull/36688)
|
||||
* Fixed markdown formatting in docker image v1, v1.1, and v1.2 spec. [moby/moby#37051](https://github.com/moby/moby/pull/37051)
|
||||
* Improve GetTimestamp parsing. [moby/moby#35402](https://github.com/moby/moby/pull/35402)
|
||||
* Jsonmessage: pass message to aux callback. [moby/moby#37064](https://github.com/moby/moby/pull/37064)
|
||||
* Overlay2: remove unused cdMountFrom() helper function. [moby/moby#37041](https://github.com/moby/moby/pull/37041)
|
||||
- Overlay: Fix overlay storage-driver silently ignoring unknown storage-driver options. [moby/moby#37040](https://github.com/moby/moby/pull/37040)
|
||||
* Remove some unused contrib items. [moby/moby#36977](https://github.com/moby/moby/pull/36977)
|
||||
* Restartmanager: do not apply restart policy on created containers. [moby/moby#36924](https://github.com/moby/moby/pull/36924)
|
||||
* Set item-type for ExecIDs. [moby/moby#37121](https://github.com/moby/moby/pull/37121)
|
||||
* Use go-systemd const instead of magic string in Linux version of dockerd. [moby/moby#37136](https://github.com/moby/moby/pull/37136)
|
||||
* Use stdlib TLS dialer. [moby/moby#36687](https://github.com/moby/moby/pull/36687)
|
||||
* Warn when an engine label using a reserved namespace (com.docker.\*, io.docker.\*, or org.dockerproject.\*) is configured, as per https://docs.docker.com/config/labels-custom-metadata/. [moby/moby#36921](https://github.com/moby/moby/pull/36921)
|
||||
- Fix missing plugin name in message. [moby/moby#37052](https://github.com/moby/moby/pull/37052)
|
||||
- Fix link anchors in CONTRIBUTING.md. [moby/moby#37276](https://github.com/moby/moby/pull/37276)
|
||||
- Fix link to Docker Toolbox. [moby/moby#37240](https://github.com/moby/moby/pull/37240)
|
||||
- Fix mis-used skip condition. [moby/moby#37179](https://github.com/moby/moby/pull/37179)
|
||||
- Fix bind mounts not working in some cases. [moby/moby#37031](https://github.com/moby/moby/pull/37031)
|
||||
- Fix fd leak on attach. [moby/moby#37184](https://github.com/moby/moby/pull/37184)
|
||||
- Fix fluentd partial detection. [moby/moby#37029](https://github.com/moby/moby/pull/37029)
|
||||
- Fix incorrect link in version-history.md. [moby/moby#37049](https://github.com/moby/moby/pull/37049)
|
||||
* Allow vim to be case insensitive for D in dockerfile. [moby/moby#37235](https://github.com/moby/moby/pull/37235)
|
||||
+ Add `t.Name()` to tests so that service names are unique. [moby/moby#37166](https://github.com/moby/moby/pull/37166)
|
||||
+ Add additional message when backendfs is extfs without d_type support. [moby/moby#37022](https://github.com/moby/moby/pull/37022)
|
||||
+ Add api version checking for tests from new feature. [moby/moby#37169](https://github.com/moby/moby/pull/37169)
|
||||
+ Add image metrics for push and pull. [moby/moby#37233](https://github.com/moby/moby/pull/37233)
|
||||
+ Add support for `init` on services. [moby/moby#37183](https://github.com/moby/moby/pull/37183)
|
||||
+ Add verification of escapeKeys array length in pkg/term/proxy.go. [moby/moby#36918](https://github.com/moby/moby/pull/36918)
|
||||
* When link id is empty for overlay2, do not remove this link.. [moby/moby#36161](https://github.com/moby/moby/pull/36161)
|
||||
- Fix build on OpenBSD by defining Self(). [moby/moby#37301](https://github.com/moby/moby/pull/37301)
|
||||
- Windows: Fix named pipe support for hyper-v isolated containers. [docker/engine#2](https://github.com/docker/engine/pull/2) [docker/cli#1165](https://github.com/docker/cli/pull/1165)
|
||||
- Fix manifest lists to always use correct size. [docker/cli#1183](https://github.com/docker/cli/pull/1183)
|
||||
* Register OCI media types. [docker/engine#4](https://github.com/docker/engine/pull/4)
|
||||
* Update containerd to v1.1.1 [docker/engine#17](https://github.com/docker/engine/pull/17)
|
||||
* LCOW: Prefer Windows over Linux in a manifest list. [docker/engine#3](https://github.com/docker/engine/pull/3)
|
||||
* Add updated `MaskPaths` that are used in code paths directly using containerd to address [CVE-2018-10892](https://cve.mitre.org/cgi-bin/cvename.cgi?name=2018-10892). [docker/engine#15](https://github.com/docker/engine/pull/15)
|
||||
* Add `/proc/acpi` to masked paths to address [CVE-2018-10892](https://cve.mitre.org/cgi-bin/cvename.cgi?name=2018-10892). [docker/engine#14](https://github.com/docker/engine/pull/14)
|
||||
- Fix bindmount autocreate race. [docker/engine#11](https://github.com/docker/engine/pull/11)
|
||||
|
||||
### Swarm Mode
|
||||
|
||||
* List stacks for both Swarm and Kubernetes with --orchestrator=all in docker stack ls. Allow several occurrences of --namespace for Kubernetes with docker stack ls. [docker/cli#1031](https://github.com/docker/cli/pull/1031)
|
||||
* Bump SwarmKit to remove deprecated grpc metadata wrappers. [moby/moby#36905](https://github.com/moby/moby/pull/36905)
|
||||
* Issue an error for --orchestrator=all when working on mismatched Swarm and Kubernetes hosts. [docker/cli#1035](https://github.com/docker/cli/pull/1035)
|
||||
- Fix broken swarm commands with Kubernetes defined as orchestrator. "--orchestrator" flag is no longer global but local to stack commands and subcommands [docker/cli#1137](https://github.com/docker/cli/pull/1137) [docker/cli#1139](https://github.com/docker/cli/pull/1139)
|
||||
* Bump swarmkit to include task reaper fixes and more metrics. [docker/engine#13](https://github.com/docker/engine/pull/13)
|
||||
- Avoid a leak when a service with unassigned tasks is deleted. [docker/engine#27](https://github.com/docker/engine/pull/27)
|
||||
- Fix racy batching on the dispatcher. [docker/engine#27](https://github.com/docker/engine/pull/27)
|
||||
|
||||
## 18.03.1-ce (2018-04-26)
|
||||
|
||||
### Client
|
||||
|
|
|
|||
|
|
@ -90,7 +90,7 @@ you, but generates an error.
|
|||
## Start a container with a bind mount
|
||||
|
||||
Consider a case where you have a directory `source` and that when you build the
|
||||
source code, the artifacts are saved into another directory `source/target/`.
|
||||
source code, the artifacts are saved into another directory, `source/target/`.
|
||||
You want the artifacts to be available to the container at `/app/`, and you
|
||||
want the container to get access to a new build each time you build the source
|
||||
on your development host. Use the following command to bind-mount the `target/`
|
||||
|
|
|
|||
|
|
@ -32,7 +32,6 @@ potential performance advantages over the `aufs` storage driver.
|
|||
`ecryptfs`. This means that the filesystem which contains
|
||||
`/var/lib/docker/aufs` cannot be one of these filesystem types.
|
||||
|
||||
|
||||
## Configure Docker with the `aufs` storage driver
|
||||
|
||||
If the AUFS driver is loaded into the kernel when you start Docker, and no other
|
||||
|
|
@ -66,13 +65,13 @@ storage driver is configured, Docker uses it by default.
|
|||
`/etc/docker/daemon.json` or the output of `ps auxw | grep dockerd` to see
|
||||
if Docker has been started with the `--storage-driver` flag.
|
||||
|
||||
|
||||
## How the `aufs` storage driver works
|
||||
|
||||
AUFS is a *union filesystem*, which means that it layers multiple directories on
|
||||
a single Linux host and presents them as a single directory. These directories
|
||||
are called _branches_ in AUFS terminology, and _layers_ in Docker terminology.
|
||||
The unification process is referred to a _union mount_.
|
||||
|
||||
The unification process is referred to as a _union mount_.
|
||||
|
||||
The diagram below shows a Docker container based on the `ubuntu:latest` image.
|
||||
|
||||
|
|
@ -228,7 +227,6 @@ The following generic performance best practices also apply to AUFS.
|
|||
|
||||
## Related information
|
||||
|
||||
* [Volumes](/storage/volumes.md)
|
||||
* [Understand images, containers, and storage drivers](imagesandcontainers.md)
|
||||
* [Select a storage driver](selectadriver.md)
|
||||
|
||||
- [Volumes](/storage/volumes.md)
|
||||
- [Understand images, containers, and storage drivers](imagesandcontainers.md)
|
||||
- [Select a storage driver](selectadriver.md)
|
||||
|
|
|
|||
|
|
@ -15,10 +15,10 @@ information to make informed choices about the best way to persist data from
|
|||
your applications and avoid performance problems along the way.
|
||||
|
||||
Storage drivers allow you to create data in the writable layer of your container.
|
||||
The files won't be persisted after the container stops, and both read and
|
||||
The files won't be persisted after the container is deleted, and both read and
|
||||
write speeds are low.
|
||||
|
||||
[Learn how to use volumes](../index.md) to persist data and improve performance.
|
||||
[Learn how to use volumes](../volumes.md) to persist data and improve performance.
|
||||
|
||||
## Images and layers
|
||||
|
||||
|
|
@ -33,7 +33,7 @@ RUN make /app
|
|||
CMD python /app/app.py
|
||||
```
|
||||
|
||||
This Dockerfile contains four commands, each of which creates a layer. The
|
||||
This Dockerfile contains four commands, each of which creates a layer. The
|
||||
`FROM` statement starts out by creating a layer from the `ubuntu:15.04` image.
|
||||
The `COPY` command adds some files from your Docker client's current directory.
|
||||
The `RUN` command builds your application using the `make` command. Finally,
|
||||
|
|
@ -82,7 +82,7 @@ To view the approximate size of a running container, you can use the `docker ps
|
|||
command. Two different columns relate to size.
|
||||
|
||||
- `size`: the amount of data (on disk) that is used for the writable layer of
|
||||
each container
|
||||
each container.
|
||||
|
||||
- `virtual size`: the amount of data used for the read-only image data
|
||||
used by the container plus the container's writable layer `size`.
|
||||
|
|
@ -143,8 +143,8 @@ Status: Downloaded newer image for ubuntu:15.04
|
|||
|
||||
Each of these layers is stored in its own directory inside the Docker host's
|
||||
local storage area. To examine the layers on the filesystem, list the contents
|
||||
of `/var/lib/docker/<storage-driver>/layers/`. This example uses `aufs`, which
|
||||
is the default storage driver:
|
||||
of `/var/lib/docker/<storage-driver>/layers/`. This example uses the `aufs`
|
||||
storage driver:
|
||||
|
||||
```bash
|
||||
$ ls /var/lib/docker/aufs/layers
|
||||
|
|
@ -292,8 +292,8 @@ layer. This means that the writable layer is as small as possible.
|
|||
|
||||
When an existing file in a container is modified, the storage driver performs a
|
||||
copy-on-write operation. The specifics steps involved depend on the specific
|
||||
storage driver. For the default `aufs` driver and the `overlay` and `overlay2`
|
||||
drivers, the copy-on-write operation follows this rough sequence:
|
||||
storage driver. For the `aufs`, `overlay`, and `overlay2` drivers, the
|
||||
copy-on-write operation follows this rough sequence:
|
||||
|
||||
* Search through the image layers for the file to update. The process starts
|
||||
at the newest layer and works down to the base layer one layer at a time.
|
||||
|
|
|
|||
|
|
@ -269,7 +269,7 @@ for `overlay2`.
|
|||
|
||||
OverlayFS layers two directories on a single Linux host and presents them as
|
||||
a single directory. These directories are called _layers_ and the unification
|
||||
process is referred to a _union mount_. OverlayFS refers to the lower directory
|
||||
process is referred to as a _union mount_. OverlayFS refers to the lower directory
|
||||
as `lowerdir` and the upper directory a `upperdir`. The unified view is exposed
|
||||
through its own directory called `merged`.
|
||||
|
||||
|
|
|
|||
|
|
@ -42,7 +42,7 @@ use unless you have substantial experience with ZFS on Linux.
|
|||
- Changing the storage driver makes any containers you have already
|
||||
created inaccessible on the local system. Use `docker save` to save containers,
|
||||
and push existing images to Docker Hub or a private repository, so that you
|
||||
not need to re-create them later.
|
||||
do not need to re-create them later.
|
||||
|
||||
## Configure Docker with the `zfs` storage driver
|
||||
|
||||
|
|
|
|||
|
|
@ -38,7 +38,7 @@ the `--mount` flag was used for swarm services. However, starting with Docker
|
|||
`--tmpfs` flag does not support any configurable options.
|
||||
|
||||
- **`--tmpfs`**: Mounts a `tmpfs` mount without allowing you to specify any
|
||||
configurable options, and can only be used with standalone containers.
|
||||
configurable options, and can only be used with standalone containers.
|
||||
|
||||
- **`--mount`**: Consists of multiple key-value pairs, separated by commas and each
|
||||
consisting of a `<key>=<value>` tuple. The `--mount` syntax is more verbose
|
||||
|
|
|
|||
Loading…
Reference in New Issue