mirror of https://github.com/fluxcd/flagger.git
Release v1.6.0
Signed-off-by: Stefan Prodan <stefan.prodan@gmail.com>
This commit is contained in:
parent
c6aa66ab94
commit
0ae4ccede1
19
CHANGELOG.md
19
CHANGELOG.md
|
|
@ -2,6 +2,25 @@
|
|||
|
||||
All notable changes to this project are documented in this file.
|
||||
|
||||
## 1.6.0
|
||||
|
||||
**Release date:** 2021-01-05
|
||||
|
||||
**Breaking change:** the minimum supported version of Kubernetes is v1.16.0.
|
||||
|
||||
This release comes with support for A/B testing using [Gloo Edge](https://docs.flagger.app/tutorials/gloo-progressive-delivery)
|
||||
HTTP headers based routing.
|
||||
|
||||
#### Features
|
||||
|
||||
- A/B testing support for Gloo Edge ingress controller
|
||||
[#765](https://github.com/fluxcd/flagger/pull/765)
|
||||
|
||||
#### Improvements
|
||||
|
||||
- Upgrade the Kubernetes packages to `v1.20.1` and Flagger's CRDs to `apiextensions.k8s.io/v1`
|
||||
[#772](https://github.com/fluxcd/flagger/pull/772)
|
||||
|
||||
## 1.5.0
|
||||
|
||||
**Release date:** 2020-12-22
|
||||
|
|
|
|||
|
|
@ -22,7 +22,7 @@ spec:
|
|||
serviceAccountName: flagger
|
||||
containers:
|
||||
- name: flagger
|
||||
image: ghcr.io/fluxcd/flagger:1.5.0
|
||||
image: ghcr.io/fluxcd/flagger:1.6.0
|
||||
imagePullPolicy: IfNotPresent
|
||||
ports:
|
||||
- name: http
|
||||
|
|
|
|||
|
|
@ -1,7 +1,7 @@
|
|||
apiVersion: v1
|
||||
name: flagger
|
||||
version: 1.5.0
|
||||
appVersion: 1.5.0
|
||||
version: 1.6.0
|
||||
appVersion: 1.6.0
|
||||
kubeVersion: ">=1.16.0-0"
|
||||
engine: gotpl
|
||||
description: Flagger is a progressive delivery operator for Kubernetes
|
||||
|
|
|
|||
|
|
@ -2,7 +2,7 @@
|
|||
|
||||
image:
|
||||
repository: ghcr.io/fluxcd/flagger
|
||||
tag: 1.5.0
|
||||
tag: 1.6.0
|
||||
pullPolicy: IfNotPresent
|
||||
pullSecret:
|
||||
|
||||
|
|
|
|||
|
|
@ -383,5 +383,90 @@ Canary failed! Scaling down podinfo.test
|
|||
If you have [alerting](../usage/alerting.md) configured,
|
||||
Flagger will send a notification with the reason why the canary failed.
|
||||
|
||||
For an in-depth look at the analysis process read the [usage docs](../usage/how-it-works.md).
|
||||
## A/B Testing
|
||||
|
||||
Besides weighted routing, Flagger can be configured to route traffic to the canary based on HTTP match conditions.
|
||||
In an A/B testing scenario, you'll be using HTTP headers or cookies to target a certain segment of your users.
|
||||
This is particularly useful for frontend applications that require session affinity.
|
||||
|
||||
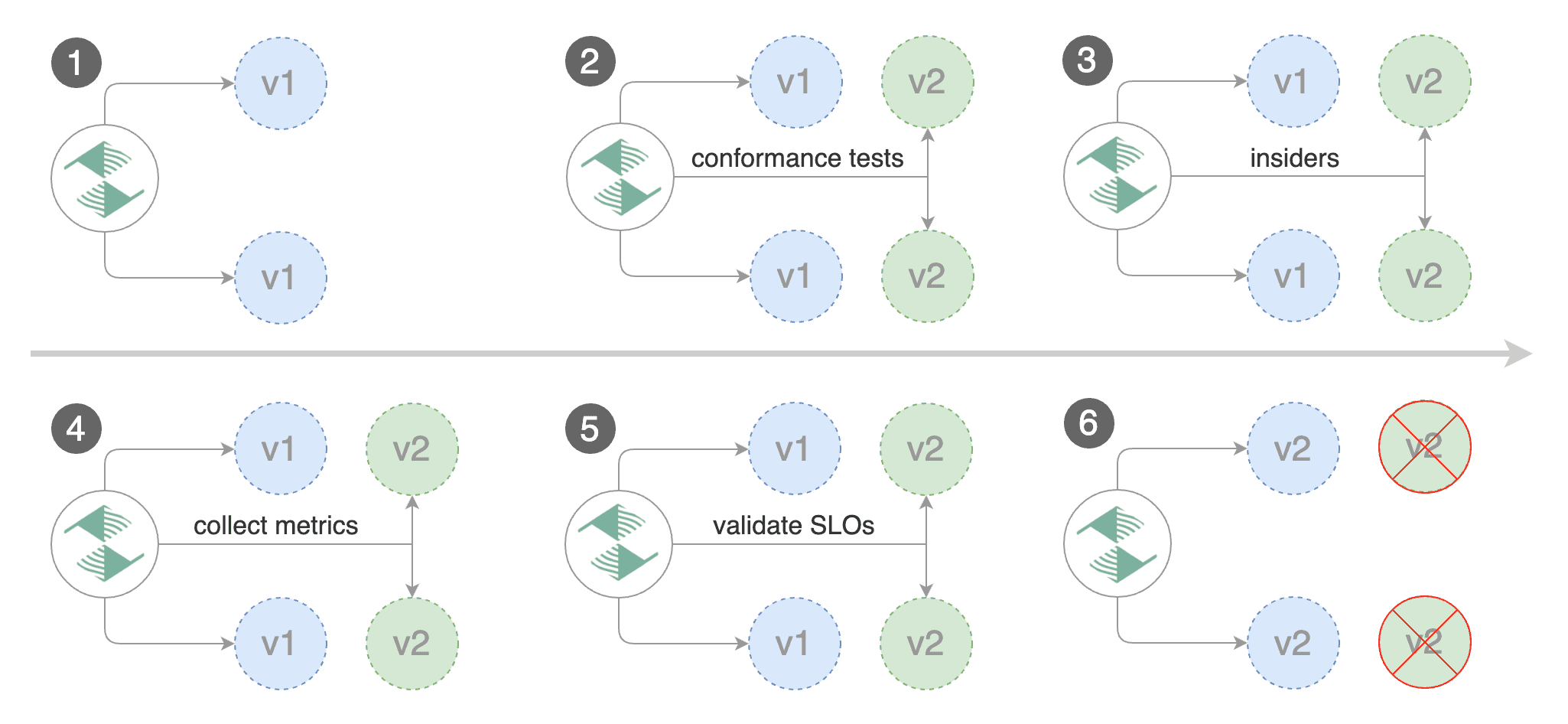
|
||||
|
||||
Edit the canary analysis, remove the max/step weight and add the match conditions and iterations:
|
||||
|
||||
```yaml
|
||||
analysis:
|
||||
interval: 1m
|
||||
threshold: 5
|
||||
iterations: 10
|
||||
match:
|
||||
- headers:
|
||||
x-canary:
|
||||
exact: "insider"
|
||||
webhooks:
|
||||
- name: load-test
|
||||
url: http://flagger-loadtester.test/
|
||||
metadata:
|
||||
cmd: "hey -z 1m -q 5 -c 5 -H 'X-Canary: insider' -host app.example.com http://gateway-proxy.gloo-system"
|
||||
```
|
||||
|
||||
The above configuration will run an analysis for ten minutes targeting users that have a `X-Canary: insider` header.
|
||||
|
||||
Trigger a canary deployment by updating the container image:
|
||||
|
||||
```bash
|
||||
kubectl -n test set image deployment/podinfo \
|
||||
podinfod=stefanprodan/podinfo:3.1.4
|
||||
```
|
||||
|
||||
Flagger detects that the deployment revision changed and starts the A/B test:
|
||||
|
||||
```text
|
||||
kubectl -n gloo-system logs deploy/flagger -f | jq .msg
|
||||
|
||||
New revision detected! Progressing canary analysis for podinfo.test
|
||||
Advance podinfo.test canary iteration 1/10
|
||||
Advance podinfo.test canary iteration 2/10
|
||||
Advance podinfo.test canary iteration 3/10
|
||||
Advance podinfo.test canary iteration 4/10
|
||||
Advance podinfo.test canary iteration 5/10
|
||||
Advance podinfo.test canary iteration 6/10
|
||||
Advance podinfo.test canary iteration 7/10
|
||||
Advance podinfo.test canary iteration 8/10
|
||||
Advance podinfo.test canary iteration 9/10
|
||||
Advance podinfo.test canary iteration 10/10
|
||||
Copying podinfo.test template spec to podinfo-primary.test
|
||||
Waiting for podinfo-primary.test rollout to finish: 1 of 2 updated replicas are available
|
||||
Routing all traffic to primary
|
||||
Promotion completed! Scaling down podinfo.test
|
||||
```
|
||||
|
||||
The web browser user agent header allows user segmentation based on device or OS.
|
||||
|
||||
For example, if you want to route all mobile users to the canary instance:
|
||||
|
||||
```yaml
|
||||
match:
|
||||
- headers:
|
||||
user-agent:
|
||||
regex: ".*Mobile.*"
|
||||
```
|
||||
|
||||
Or if you want to target only Android users:
|
||||
|
||||
```yaml
|
||||
match:
|
||||
- headers:
|
||||
user-agent:
|
||||
regex: ".*Android.*"
|
||||
```
|
||||
|
||||
Or a specific browser version:
|
||||
|
||||
```yaml
|
||||
match:
|
||||
- headers:
|
||||
user-agent:
|
||||
regex: ".*Firefox.*"
|
||||
```
|
||||
|
||||
For an in-depth look at the analysis process read the [usage docs](../usage/how-it-works.md).
|
||||
|
|
|
|||
|
|
@ -7,5 +7,6 @@ resources:
|
|||
- crd.yaml
|
||||
- deployment.yaml
|
||||
images:
|
||||
- name: fluxcd/flagger
|
||||
newTag: 1.5.0
|
||||
- name: ghcr.io/fluxcd/flagger
|
||||
newName: ghcr.io/fluxcd/flagger
|
||||
newTag: 1.6.0
|
||||
|
|
|
|||
|
|
@ -16,5 +16,5 @@ limitations under the License.
|
|||
|
||||
package version
|
||||
|
||||
var VERSION = "1.5.0"
|
||||
var VERSION = "1.6.0"
|
||||
var REVISION = "unknown"
|
||||
|
|
|
|||
Loading…
Reference in New Issue