mirror of https://github.com/fluxcd/flagger.git
Update roadmap and readme
This commit is contained in:
parent
23e6209789
commit
eced0f45c6
39
CHANGELOG.md
39
CHANGELOG.md
|
|
@ -16,19 +16,21 @@ canary basis for Slack, MS Teams, Discord and Rocket.
|
|||
|
||||
#### Features
|
||||
|
||||
- Implement metric templates for Prometheus [#419](https://github.com/weaveworks/flagger/pull/419)
|
||||
Datadog [#460](https://github.com/weaveworks/flagger/pull/460) and
|
||||
- Implement metric templates for Prometheus [#419](https://github.com/weaveworks/flagger/pull/419),
|
||||
Datadog [#460](https://github.com/weaveworks/flagger/pull/460) and
|
||||
CloudWatch [#464](https://github.com/weaveworks/flagger/pull/464)
|
||||
- Implement metric range validation [#424](https://github.com/weaveworks/flagger/pull/424)
|
||||
- Add support for targeting DaemonSets [#455](https://github.com/weaveworks/flagger/pull/455)
|
||||
- Implement canary alerts and alert providers (Slack, MS Teams, Discord and Rocket) [#429](https://github.com/weaveworks/flagger/pull/429)
|
||||
- Implement canary alerts and alert providers (Slack, MS Teams, Discord and Rocket)
|
||||
[#429](https://github.com/weaveworks/flagger/pull/429)
|
||||
|
||||
#### Improvements
|
||||
|
||||
- Add support for Istio multi-cluster [#447](https://github.com/weaveworks/flagger/pull/447) [#450](https://github.com/weaveworks/flagger/pull/450)
|
||||
- Add support for Istio multi-cluster
|
||||
[#447](https://github.com/weaveworks/flagger/pull/447) [#450](https://github.com/weaveworks/flagger/pull/450)
|
||||
- Extend Istio traffic policy [#441](https://github.com/weaveworks/flagger/pull/441),
|
||||
add support for header operations [#442](https://github.com/weaveworks/flagger/pull/442) and
|
||||
set ingress destination port when multiple ports are discovered [#436](https://github.com/weaveworks/flagger/pull/436).
|
||||
set ingress destination port when multiple ports are discovered [#436](https://github.com/weaveworks/flagger/pull/436)
|
||||
- Add support for rollback gating [#449](https://github.com/weaveworks/flagger/pull/449)
|
||||
- Allow disabling ConfigMaps and Secrets tracking [#425](https://github.com/weaveworks/flagger/pull/425)
|
||||
|
||||
|
|
@ -126,7 +128,8 @@ Fixes promql execution and updates the load testing tools
|
|||
|
||||
## 0.20.0 (2019-10-21)
|
||||
|
||||
Adds support for [A/B Testing](https://docs.flagger.app/usage/progressive-delivery#traffic-mirroring) and retry policies when using App Mesh
|
||||
Adds support for [A/B Testing](https://docs.flagger.app/usage/progressive-delivery#traffic-mirroring)
|
||||
and retry policies when using App Mesh
|
||||
|
||||
#### Features
|
||||
|
||||
|
|
@ -161,7 +164,8 @@ Adds support for canary and blue/green [traffic mirroring](https://docs.flagger.
|
|||
#### Fixes
|
||||
|
||||
- Fix port discovery diff [#324](https://github.com/weaveworks/flagger/pull/324)
|
||||
- Helm chart: Enable Prometheus scraping of Flagger metrics [#2141d88](https://github.com/weaveworks/flagger/commit/2141d88ce1cc6be220dab34171c215a334ecde24)
|
||||
- Helm chart: Enable Prometheus scraping of Flagger metrics
|
||||
[#2141d88](https://github.com/weaveworks/flagger/commit/2141d88ce1cc6be220dab34171c215a334ecde24)
|
||||
|
||||
## 0.18.6 (2019-10-03)
|
||||
|
||||
|
|
@ -179,7 +183,8 @@ Adds support for App Mesh conformance tests and latency metric checks
|
|||
|
||||
## 0.18.5 (2019-10-02)
|
||||
|
||||
Adds support for [confirm-promotion](https://docs.flagger.app/how-it-works#webhooks) webhooks and blue/green deployments when using a service mesh
|
||||
Adds support for [confirm-promotion](https://docs.flagger.app/how-it-works#webhooks)
|
||||
webhooks and blue/green deployments when using a service mesh
|
||||
|
||||
#### Features
|
||||
|
||||
|
|
@ -264,8 +269,10 @@ Adds support for [manual gating](https://docs.flagger.app/how-it-works#manual-ga
|
|||
|
||||
#### Breaking changes
|
||||
|
||||
- Due to the status sub-resource changes in [#240](https://github.com/weaveworks/flagger/pull/240), when upgrading Flagger the canaries status phase will be reset to `Initialized`
|
||||
- Upgrading Flagger with Helm will fail due to Helm poor support of CRDs, see [workaround](https://github.com/weaveworks/flagger/issues/223)
|
||||
- Due to the status sub-resource changes in [#240](https://github.com/weaveworks/flagger/pull/240),
|
||||
when upgrading Flagger the canaries status phase will be reset to `Initialized`
|
||||
- Upgrading Flagger with Helm will fail due to Helm poor support of CRDs,
|
||||
see [workaround](https://github.com/weaveworks/flagger/issues/223)
|
||||
|
||||
## 0.17.0 (2019-07-08)
|
||||
|
||||
|
|
@ -279,12 +286,14 @@ Adds support for Linkerd (SMI Traffic Split API), MS Teams notifications and HA
|
|||
|
||||
#### Improvements
|
||||
|
||||
- Add [Kustomize](https://docs.flagger.app/install/flagger-install-on-kubernetes#install-flagger-with-kustomize) installer [#232](https://github.com/weaveworks/flagger/pull/232)
|
||||
- Add [Kustomize](https://docs.flagger.app/install/flagger-install-on-kubernetes#install-flagger-with-kustomize)
|
||||
installer [#232](https://github.com/weaveworks/flagger/pull/232)
|
||||
- Add Pod Security Policy to Helm chart [#234](https://github.com/weaveworks/flagger/pull/234)
|
||||
|
||||
## 0.16.0 (2019-06-23)
|
||||
|
||||
Adds support for running [Blue/Green deployments](https://docs.flagger.app/usage/blue-green) without a service mesh or ingress controller
|
||||
Adds support for running [Blue/Green deployments](https://docs.flagger.app/usage/blue-green)
|
||||
without a service mesh or ingress controller
|
||||
|
||||
#### Features
|
||||
|
||||
|
|
@ -316,7 +325,8 @@ Adds support for customising the Istio [traffic policy](https://docs.flagger.app
|
|||
|
||||
## 0.14.1 (2019-06-05)
|
||||
|
||||
Adds support for running [acceptance/integration tests](https://docs.flagger.app/how-it-works#integration-testing) with Helm test or Bash Bats using pre-rollout hooks
|
||||
Adds support for running [acceptance/integration tests](https://docs.flagger.app/how-it-works#integration-testing)
|
||||
with Helm test or Bash Bats using pre-rollout hooks
|
||||
|
||||
#### Features
|
||||
|
||||
|
|
@ -363,7 +373,8 @@ Adds support for [NGINX](https://docs.flagger.app/usage/nginx-progressive-delive
|
|||
#### Features
|
||||
|
||||
- Add support for nginx ingress controller (weighted traffic and A/B testing) [#170](https://github.com/weaveworks/flagger/pull/170)
|
||||
- Add Prometheus add-on to Flagger Helm chart for App Mesh and NGINX [79b3370](https://github.com/weaveworks/flagger/pull/170/commits/79b337089294a92961bc8446fd185b38c50a32df)
|
||||
- Add Prometheus add-on to Flagger Helm chart for App Mesh and
|
||||
NGINX [79b3370](https://github.com/weaveworks/flagger/pull/170/commits/79b337089294a92961bc8446fd185b38c50a32df)
|
||||
|
||||
#### Fixes
|
||||
|
||||
|
|
|
|||
77
README.md
77
README.md
|
|
@ -6,53 +6,40 @@
|
|||
[](https://github.com/weaveworks/flagger/blob/master/LICENSE)
|
||||
[](https://github.com/weaveworks/flagger/releases)
|
||||
|
||||
Flagger is a Kubernetes operator that automates the promotion of canary deployments
|
||||
using Istio, Linkerd, App Mesh, NGINX, Contour or Gloo routing for traffic shifting and Prometheus metrics for canary analysis.
|
||||
The canary analysis can be extended with webhooks for running acceptance tests,
|
||||
load tests or any other custom validation.
|
||||
|
||||
Flagger implements a control loop that gradually shifts traffic to the canary while measuring key performance
|
||||
indicators like HTTP requests success rate, requests average duration and pods health.
|
||||
Based on analysis of the KPIs a canary is promoted or aborted, and the analysis result is published to Slack or MS Teams.
|
||||
Flagger is a progressive delivery tool that automates the release process for applications running on Kubernetes.
|
||||
It reduces the risk of introducing a new software version in production
|
||||
by gradually shifting traffic to the new version while measuring metrics and running conformance tests.
|
||||
|
||||
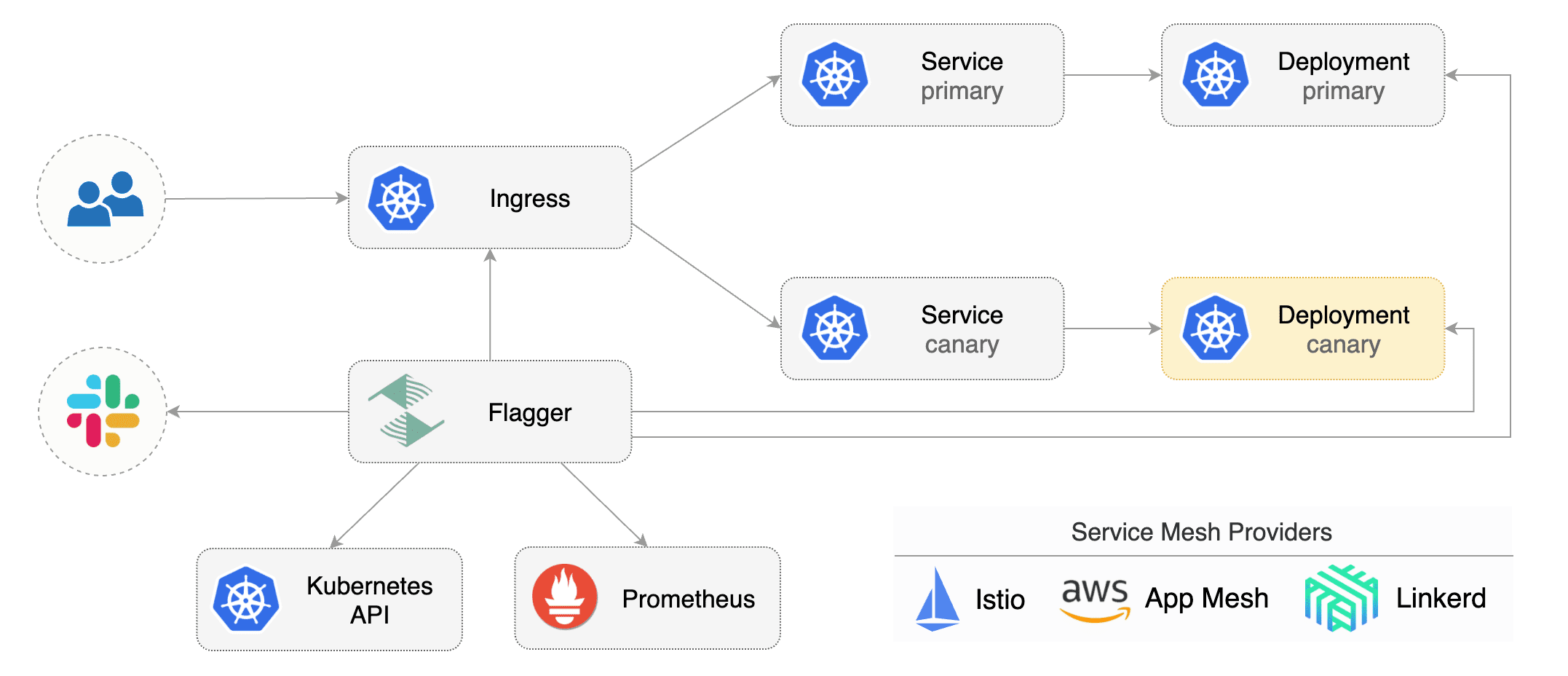
|
||||
|
||||
## Documentation
|
||||
Flagger implements several deployment strategies (Canary releases, A/B testing, Blue/Green mirroring)
|
||||
using a service mesh (App Mesh, Istio, Linkerd) or an ingress controller (Contour, Gloo, NGINX) for traffic routing.
|
||||
For release analysis, Flagger can query Prometheus, Datadog or CloudWatch
|
||||
and for alerting it uses Slack, MS Teams, Discord and Rocket.
|
||||
|
||||
Flagger documentation can be found at [docs.flagger.app](https://docs.flagger.app)
|
||||
### Documentation
|
||||
|
||||
Flagger documentation can be found at [docs.flagger.app](https://docs.flagger.app).
|
||||
|
||||
* Install
|
||||
* [Flagger install on Kubernetes](https://docs.flagger.app/install/flagger-install-on-kubernetes)
|
||||
* [Flagger install on GKE Istio](https://docs.flagger.app/install/flagger-install-on-google-cloud)
|
||||
* [Flagger install on EKS App Mesh](https://docs.flagger.app/install/flagger-install-on-eks-appmesh)
|
||||
* How it works
|
||||
* [Canary custom resource](https://docs.flagger.app/how-it-works#canary-custom-resource)
|
||||
* [Routing](https://docs.flagger.app/how-it-works#istio-routing)
|
||||
* [Canary deployment stages](https://docs.flagger.app/how-it-works#canary-deployment)
|
||||
* [Canary analysis](https://docs.flagger.app/how-it-works#canary-analysis)
|
||||
* [HTTP metrics](https://docs.flagger.app/how-it-works#http-metrics)
|
||||
* [Custom metrics](https://docs.flagger.app/how-it-works#custom-metrics)
|
||||
* [Webhooks](https://docs.flagger.app/how-it-works#webhooks)
|
||||
* [Load testing](https://docs.flagger.app/how-it-works#load-testing)
|
||||
* [Manual gating](https://docs.flagger.app/how-it-works#manual-gating)
|
||||
* [FAQ](https://docs.flagger.app/faq)
|
||||
* [Development guide](https://docs.flagger.app/dev-guide)
|
||||
* Usage
|
||||
* [Deployment Strategies](https://docs.flagger.app/usage/deployment-strategies)
|
||||
* [Monitoring](https://docs.flagger.app/usage/monitoring)
|
||||
* [How it works](https://docs.flagger.app/usage/how-it-works)
|
||||
* [Deployment strategies](https://docs.flagger.app/usage/deployment-strategies)
|
||||
* [Metrics analysis](https://docs.flagger.app/usage/webhooks)
|
||||
* [Webhooks](https://docs.flagger.app/usage/webhooks)
|
||||
* [Alerting](https://docs.flagger.app/usage/alerting)
|
||||
* [Monitoring](https://docs.flagger.app/usage/monitoring)
|
||||
* Tutorials
|
||||
* [Istio Canary Deployments](https://docs.flagger.app/tutorials/istio-progressive-delivery)
|
||||
* [Istio A/B Testing](https://docs.flagger.app/tutorials/istio-ab-testing)
|
||||
* [Linkerd Canary Deployments](https://docs.flagger.app/tutorials/linkerd-progressive-delivery)
|
||||
* [App Mesh Canary Deployments](https://docs.flagger.app/tutorials/appmesh-progressive-delivery)
|
||||
* [NGINX Canary Deployments](https://docs.flagger.app/tutorials/nginx-progressive-delivery)
|
||||
* [Gloo Canary Deployments](https://docs.flagger.app/tutorials/gloo-progressive-delivery)
|
||||
* [Contour Canary Deployments](https://docs.flagger.app/tutorials/contour-progressive-delivery)
|
||||
* [Kubernetes Blue/Green Deployments](https://docs.flagger.app/tutorials/kubernetes-blue-green)
|
||||
* [Canary deployments with Helm charts and Weave Flux](https://docs.flagger.app/tutorials/canary-helm-gitops)
|
||||
* [App Mesh](https://docs.flagger.app/tutorials/appmesh-progressive-delivery)
|
||||
* [Istio](https://docs.flagger.app/tutorials/istio-progressive-delivery)
|
||||
* [Linkerd](https://docs.flagger.app/tutorials/linkerd-progressive-delivery)
|
||||
* [Contour](https://docs.flagger.app/tutorials/contour-progressive-delivery)
|
||||
* [Gloo](https://docs.flagger.app/tutorials/gloo-progressive-delivery)
|
||||
* [NGINX Ingress](https://docs.flagger.app/tutorials/nginx-progressive-delivery)
|
||||
* [Kubernetes Blue/Green](https://docs.flagger.app/tutorials/kubernetes-blue-green)
|
||||
|
||||
## Who is using Flagger
|
||||
### Who is using Flagger
|
||||
|
||||
List of organizations using Flagger:
|
||||
|
||||
|
|
@ -63,10 +50,10 @@ List of organizations using Flagger:
|
|||
|
||||
If you are using Flagger, please submit a PR to add your organization to the list!
|
||||
|
||||
## Canary CRD
|
||||
### Canary CRD
|
||||
|
||||
Flagger takes a Kubernetes deployment and optionally a horizontal pod autoscaler (HPA),
|
||||
then creates a series of objects (Kubernetes deployments, ClusterIP services and Istio or App Mesh virtual services).
|
||||
then creates a series of objects (Kubernetes deployments, ClusterIP services, service mesh or ingress routes).
|
||||
These objects expose the application on the mesh and drive the canary analysis and promotion.
|
||||
|
||||
Flagger keeps track of ConfigMaps and Secrets referenced by a Kubernetes Deployment and triggers a canary analysis if any of those objects change.
|
||||
|
|
@ -187,9 +174,9 @@ spec:
|
|||
name: on-call-msteams
|
||||
```
|
||||
|
||||
For more details on how the canary analysis and promotion works please [read the docs](https://docs.flagger.app/how-it-works).
|
||||
For more details on how the canary analysis and promotion works please [read the docs](https://docs.flagger.app/usage/how-it-works).
|
||||
|
||||
## Features
|
||||
### Features
|
||||
|
||||
| Feature | Istio | Linkerd | App Mesh | NGINX | Gloo | Contour | CNI |
|
||||
| -------------------------------------------- | ------------------ | ------------------ |------------------ |------------------ |------------------ |------------------ |------------------ |
|
||||
|
|
@ -203,14 +190,16 @@ For more details on how the canary analysis and promotion works please [read the
|
|||
| Custom promql checks | :heavy_check_mark: | :heavy_check_mark: | :heavy_check_mark: | :heavy_check_mark: | :heavy_check_mark: | :heavy_check_mark: | :heavy_check_mark: |
|
||||
| Traffic policy, CORS, retries and timeouts | :heavy_check_mark: | :heavy_minus_sign: | :heavy_minus_sign: | :heavy_minus_sign: | :heavy_minus_sign: | :heavy_check_mark: | :heavy_minus_sign: |
|
||||
|
||||
## Roadmap
|
||||
### Roadmap
|
||||
|
||||
* Integrate with other service mesh like Consul Connect and ingress controllers like HAProxy, ALB
|
||||
* Integrate with other metrics providers like InfluxDB, Stackdriver, SignalFX
|
||||
* Add support for comparing the canary metrics to the primary ones and do the validation based on the derivation between the two
|
||||
|
||||
## Contributing
|
||||
### Contributing
|
||||
|
||||
Flagger is Apache 2.0 licensed and accepts contributions via GitHub pull requests.
|
||||
To start contributing please read the [development guide](https://docs.flagger.app/dev-guide).
|
||||
|
||||
When submitting bug reports please include as much details as possible:
|
||||
|
||||
|
|
@ -220,7 +209,7 @@ When submitting bug reports please include as much details as possible:
|
|||
* what configuration (canary, ingress and workloads definitions)
|
||||
* what happened (Flagger and Proxy logs)
|
||||
|
||||
## Getting Help
|
||||
### Getting Help
|
||||
|
||||
If you have any questions about Flagger and progressive delivery:
|
||||
|
||||
|
|
@ -231,4 +220,4 @@ If you have any questions about Flagger and progressive delivery:
|
|||
hands-on training and meetups in your area.
|
||||
* File an [issue](https://github.com/weaveworks/flagger/issues/new).
|
||||
|
||||
Your feedback is always welcome!
|
||||
Your feedback is always welcome!
|
||||
|
|
|
|||
|
|
@ -26,7 +26,7 @@ This project is sponsored by [Weaveworks](https://www.weave.works/)
|
|||
To get started with Flagger, chose one of the supported routing providers
|
||||
and [install](install/flagger-install-on-kubernetes.md) Flagger with Helm or Kustomize.
|
||||
|
||||
After install Flagger you can follow one the tutorials:
|
||||
After install Flagger, you can follow one of the tutorials:
|
||||
|
||||
**Service mesh tutorials**
|
||||
|
||||
|
|
@ -45,4 +45,3 @@ After install Flagger you can follow one the tutorials:
|
|||
* [Istio](https://github.com/stefanprodan/gitops-istio)
|
||||
* [Linkerd](https://helm.workshop.flagger.dev)
|
||||
* [AWS App Mesh](https://eks.hands-on.flagger.dev)
|
||||
|
||||
|
|
|
|||
|
|
@ -235,18 +235,17 @@ Reference the template in the canary analysis:
|
|||
```
|
||||
|
||||
|
||||
### AWS CloudWatch metrics
|
||||
### Amazon CloudWatch
|
||||
|
||||
You can create custom metric checks using the AWS CloudWatch metrics provider.
|
||||
You can create custom metric checks using the CloudWatch metrics provider.
|
||||
|
||||
The template example:
|
||||
CloudWatch template example:
|
||||
|
||||
```yaml
|
||||
apiVersion: flagger.app/v1alpha1
|
||||
kind: MetricTemplate
|
||||
metadata:
|
||||
name: cloudwatch-error-rate
|
||||
namespace: istio-system
|
||||
spec:
|
||||
provider:
|
||||
type: cloudwatch
|
||||
|
|
@ -299,20 +298,19 @@ spec:
|
|||
]
|
||||
```
|
||||
|
||||
where the query is in the form as in [the AWS' official document](https://aws.amazon.com/premiumsupport/knowledge-center/cloudwatch-getmetricdata-api/).
|
||||
The query format documentation can be found [here](https://aws.amazon.com/premiumsupport/knowledge-center/cloudwatch-getmetricdata-api/).
|
||||
|
||||
Reference the template in the canary analysis:
|
||||
|
||||
```yaml
|
||||
analysis:
|
||||
metrics:
|
||||
- name: "cw custom error rate"
|
||||
- name: "app error rate"
|
||||
templateRef:
|
||||
name: cloudwatch-error-rate
|
||||
namespace: istio-system
|
||||
thresholdRange:
|
||||
max: 0.1
|
||||
interval: 1m
|
||||
```
|
||||
|
||||
Please note that the flagger need AWS IAM permission to perform `cloudwatch:GetMetricData` to use this provider.
|
||||
**Note** that Flagger need AWS IAM permission to perform `cloudwatch:GetMetricData` to use this provider.
|
||||
|
|
|
|||
|
|
@ -25,4 +25,4 @@ download() {
|
|||
|
||||
download
|
||||
tar -xf "$TAR_FILE" -C "$TMPDIR"
|
||||
"${TMPDIR}/goreleaser" --release-notes <(github-release-notes -org weaveworks -repo flagger -since-latest-release)
|
||||
"${TMPDIR}/goreleaser" --release-notes <(github-release-notes -org weaveworks -repo flagger -since-latest-release -include-author)
|
||||
|
|
|
|||
Loading…
Reference in New Issue