mirror of https://github.com/fluxcd/flux2.git
Compare commits
446 Commits
| Author | SHA1 | Date |
|---|---|---|
|
|
ccb9d12927 | |
|
|
8b95a09319 | |
|
|
8176d88801 | |
|
|
2f850743fa | |
|
|
4e53b6cb8d | |
|
|
0bb2e3929f | |
|
|
82b38dfa68 | |
|
|
b3b404ed30 | |
|
|
45990633e6 | |
|
|
97937c55bf | |
|
|
f79c44ee0a | |
|
|
16eb212609 | |
|
|
5da5186b3b | |
|
|
158618e632 | |
|
|
81bd619abd | |
|
|
d2aa9fb996 | |
|
|
315dad8682 | |
|
|
600ec37524 | |
|
|
1af7e08f07 | |
|
|
61a19cac84 | |
|
|
fa8ef5b9d1 | |
|
|
eb5904fb9d | |
|
|
fda72a014c | |
|
|
f4d6934a6f | |
|
|
545b338004 | |
|
|
a8425f50bd | |
|
|
24bf751d4d | |
|
|
cf157ad8a3 | |
|
|
5a4bc9410b | |
|
|
de594183bd | |
|
|
4c343893c5 | |
|
|
8ae0aaa46c | |
|
|
6b3a1134bd | |
|
|
40a9b495b2 | |
|
|
1d34e5355b | |
|
|
00d0e1af25 | |
|
|
9f29702f54 | |
|
|
7626cd0c86 | |
|
|
5291902fd7 | |
|
|
1757d964c0 | |
|
|
999f61c02e | |
|
|
5eb43e4566 | |
|
|
ec3804cc6f | |
|
|
4c3aed9faf | |
|
|
06e3047a2f | |
|
|
99e6791f4b | |
|
|
9cad95dda5 | |
|
|
76c584e751 | |
|
|
cd4244ae65 | |
|
|
1d6137d39d | |
|
|
be8acc0cfb | |
|
|
2f5f40d593 | |
|
|
4172a8a7f9 | |
|
|
4addf8a528 | |
|
|
1df7697811 | |
|
|
4c66d37545 | |
|
|
481c3c6e1e | |
|
|
1d1d96b489 | |
|
|
0b972771fd | |
|
|
650732109e | |
|
|
79fed691ca | |
|
|
b37ba736fa | |
|
|
65766ff4fc | |
|
|
19d9b87c62 | |
|
|
d82ec5a211 | |
|
|
5e5ffdbcc3 | |
|
|
13ec11da58 | |
|
|
2948d5e70f | |
|
|
bb9a119456 | |
|
|
22ac16f3a1 | |
|
|
79a654d605 | |
|
|
a421ce4266 | |
|
|
4b42c9e746 | |
|
|
5ffca1b157 | |
|
|
0951061b5e | |
|
|
ad9d63ac52 | |
|
|
dccc658273 | |
|
|
ef5389cd56 | |
|
|
3f63b3e864 | |
|
|
656d9d892d | |
|
|
e979df122a | |
|
|
8804b856ea | |
|
|
3ba170e4d4 | |
|
|
6150fe9942 | |
|
|
3e80c5809e | |
|
|
8928ac7d39 | |
|
|
289645f142 | |
|
|
8d9cbe7693 | |
|
|
392a33d425 | |
|
|
6af448e037 | |
|
|
ac66adc24c | |
|
|
0a64800784 | |
|
|
941af6a648 | |
|
|
a6b5013649 | |
|
|
c18ab38877 | |
|
|
8738712cfa | |
|
|
8816c5f7de | |
|
|
e9e15c5f7a | |
|
|
5b582917ec | |
|
|
d9b66f6959 | |
|
|
1b98e16940 | |
|
|
0c73420ccf | |
|
|
8cb7188919 | |
|
|
72a2866508 | |
|
|
912718103c | |
|
|
a7e41df1e3 | |
|
|
c436708a13 | |
|
|
3f4743037b | |
|
|
7b551b0d35 | |
|
|
bb8a10bab8 | |
|
|
09af0becc5 | |
|
|
d84bff7d1b | |
|
|
a4c513487e | |
|
|
2046003714 | |
|
|
f07ee355ea | |
|
|
5e02724e49 | |
|
|
e5926bcaad | |
|
|
355f2bc5f3 | |
|
|
7e8e0ab772 | |
|
|
f0fecf7399 | |
|
|
54db4ffc8b | |
|
|
73fff7404f | |
|
|
24057743bb | |
|
|
04d87be082 | |
|
|
e7c6ebccc3 | |
|
|
48382f885b | |
|
|
511d8346f2 | |
|
|
f0e8e84ee0 | |
|
|
c277fbf14e | |
|
|
28570296a9 | |
|
|
39ec0cb594 | |
|
|
af67405ee4 | |
|
|
6f65c92fe7 | |
|
|
c84d312289 | |
|
|
d37473ff44 | |
|
|
712b03727a | |
|
|
14da7d58be | |
|
|
45da6a86f8 | |
|
|
3053a0b840 | |
|
|
96f95b6b4c | |
|
|
cf92e02f53 | |
|
|
ce50286a92 | |
|
|
c15eb30b0d | |
|
|
8bedcc46d4 | |
|
|
5d64a9fc76 | |
|
|
035afd9533 | |
|
|
c859688b37 | |
|
|
13b1d199ee | |
|
|
5f9108c53f | |
|
|
abf52ff866 | |
|
|
b319ee1ddf | |
|
|
b564d2fb3b | |
|
|
d9e25d86aa | |
|
|
dcc4251a2a | |
|
|
960f72fe6a | |
|
|
6f815a36fe | |
|
|
1d08cace4f | |
|
|
cfd369df47 | |
|
|
9e6f723436 | |
|
|
e4325961af | |
|
|
74d748f547 | |
|
|
6f6d3fb269 | |
|
|
e51e5df9da | |
|
|
f604d7f342 | |
|
|
3346542917 | |
|
|
f0e7f92ef1 | |
|
|
e09ba7a8e6 | |
|
|
f29bcfb108 | |
|
|
2e9e8e2690 | |
|
|
3478fe343d | |
|
|
8b10a32088 | |
|
|
16ae23a3a6 | |
|
|
055958d533 | |
|
|
0cc68e0521 | |
|
|
fae5d62b07 | |
|
|
16f55bbf22 | |
|
|
83c16f9c4a | |
|
|
b232bbe004 | |
|
|
5208515604 | |
|
|
928ea24bcb | |
|
|
9b1b5e8a51 | |
|
|
5b740c45d1 | |
|
|
19568eb94e | |
|
|
5cf0dcc77d | |
|
|
b45a8b5c1f | |
|
|
2b68c8c664 | |
|
|
939cffa561 | |
|
|
30ed414938 | |
|
|
d51a2f8bce | |
|
|
120ec049f9 | |
|
|
aa9de2c6bc | |
|
|
226cb462c2 | |
|
|
b1bdab4e6a | |
|
|
8110d2f05d | |
|
|
13c56f3e4e | |
|
|
1013e98c0f | |
|
|
85405928a7 | |
|
|
570bc81278 | |
|
|
f42a17de54 | |
|
|
7697699e65 | |
|
|
9f854cb7e2 | |
|
|
995e1dcc32 | |
|
|
5b83111dc6 | |
|
|
9abc802f15 | |
|
|
2a5948fe42 | |
|
|
af765388d2 | |
|
|
5350425cdc | |
|
|
6611a4fba6 | |
|
|
297b15b82b | |
|
|
56a3d08bf8 | |
|
|
cf26cf25f1 | |
|
|
a3dbf31e87 | |
|
|
3e4524b987 | |
|
|
8470f23ad2 | |
|
|
e17f3f0168 | |
|
|
e0b8464a6c | |
|
|
2c7d781ec5 | |
|
|
c7daf6466f | |
|
|
0d101e0e36 | |
|
|
0a5d263f77 | |
|
|
7d7a8f81f4 | |
|
|
cbda2be6b8 | |
|
|
d5427d12cf | |
|
|
e970a2d6a7 | |
|
|
a4ef1f6992 | |
|
|
055d85fc18 | |
|
|
927f3e50f6 | |
|
|
d13dec297a | |
|
|
2d37544b06 | |
|
|
1b4de026dd | |
|
|
9af1e85b93 | |
|
|
cb327a793e | |
|
|
82671cfd24 | |
|
|
69964519e7 | |
|
|
1ac06fd859 | |
|
|
1563d2b81b | |
|
|
285495a0e7 | |
|
|
16e30439b7 | |
|
|
36dec31fd7 | |
|
|
bd1ff8f771 | |
|
|
83402e8834 | |
|
|
cc87ffd66e | |
|
|
c39af08b47 | |
|
|
18e0087439 | |
|
|
1b0eecd145 | |
|
|
2694dfd489 | |
|
|
466d30047a | |
|
|
2281013050 | |
|
|
e06e561150 | |
|
|
41bdb88be2 | |
|
|
52512a94a8 | |
|
|
170e4f6f57 | |
|
|
b8bf44e0ae | |
|
|
f6a0250712 | |
|
|
31d160b309 | |
|
|
fabdbaaf92 | |
|
|
a9017239b7 | |
|
|
9f873c0a07 | |
|
|
0720935fb4 | |
|
|
298e28b63e | |
|
|
ec141c63c4 | |
|
|
b45cd59b7c | |
|
|
e42aa8e448 | |
|
|
a5447e4c77 | |
|
|
638e537b40 | |
|
|
d95e8b63e0 | |
|
|
f5f799b5fc | |
|
|
f42c91448d | |
|
|
bde7489e45 | |
|
|
dcca1328a3 | |
|
|
ffc1f721ac | |
|
|
6b062fb82f | |
|
|
896e0fa46d | |
|
|
8d75df8fc3 | |
|
|
dd7ef7d0c1 | |
|
|
5feee5c73d | |
|
|
0d0285ad09 | |
|
|
86b3581f5e | |
|
|
32804f6518 | |
|
|
070fa0ff8e | |
|
|
9ef9464e77 | |
|
|
d8e6199b2a | |
|
|
6552ced272 | |
|
|
6edf2bc5a2 | |
|
|
0948d1440d | |
|
|
55728ce6d7 | |
|
|
b87d04e629 | |
|
|
6b1f0fedd9 | |
|
|
299a5423ef | |
|
|
6981683dcc | |
|
|
d5aedaca7d | |
|
|
83b7b17f11 | |
|
|
52f1ae2df7 | |
|
|
8856de1478 | |
|
|
472396728b | |
|
|
b85d34644b | |
|
|
54f33ece2a | |
|
|
18d5ec4ecd | |
|
|
9325eac0d3 | |
|
|
227b124f02 | |
|
|
c1ff78c68e | |
|
|
26109ee821 | |
|
|
eaf1c0fab6 | |
|
|
8006c3ddc8 | |
|
|
7640afc852 | |
|
|
ff3ca3a355 | |
|
|
3322b52786 | |
|
|
008326ec22 | |
|
|
d413503244 | |
|
|
d86838902d | |
|
|
4edc640d0c | |
|
|
7b8906fe41 | |
|
|
47e30e2e5f | |
|
|
de46bae6fe | |
|
|
7eba0aedde | |
|
|
46bb1a0b47 | |
|
|
2ab0a7506b | |
|
|
214a273f66 | |
|
|
aae086c508 | |
|
|
e40961c6d0 | |
|
|
315c53a717 | |
|
|
6baefa2586 | |
|
|
1aaa48fa09 | |
|
|
89038b7300 | |
|
|
e25823ab28 | |
|
|
856ff67f34 | |
|
|
2338cc24a6 | |
|
|
7027e823d8 | |
|
|
ad1d33262d | |
|
|
86b3075535 | |
|
|
88b028fd50 | |
|
|
37d139c462 | |
|
|
01ebcf864d | |
|
|
d97221423f | |
|
|
acad6ca73f | |
|
|
c49ba9d310 | |
|
|
0cb24f9c6a | |
|
|
e17d429df2 | |
|
|
6b7a93961c | |
|
|
8d4454d0c1 | |
|
|
cc6b170c4b | |
|
|
d0f558c7ab | |
|
|
1299387408 | |
|
|
cbe41a6bf9 | |
|
|
b3a29b56bb | |
|
|
2dfb536600 | |
|
|
ec62b84c5d | |
|
|
1bb92548e4 | |
|
|
90f3c5a5cb | |
|
|
9ff9f2beba | |
|
|
5456635ee7 | |
|
|
5b619d8001 | |
|
|
e573800c1b | |
|
|
26168b1241 | |
|
|
205314e363 | |
|
|
f93da6fa76 | |
|
|
493c1fbdf9 | |
|
|
4d86311c11 | |
|
|
7d52267fc4 | |
|
|
9e52b3ff41 | |
|
|
0672c8add2 | |
|
|
05903e2171 | |
|
|
afa648933b | |
|
|
8d11b2742f | |
|
|
80c886c0cf | |
|
|
f63385a43f | |
|
|
45faebb6b3 | |
|
|
0dda09408c | |
|
|
c7db0c6b9f | |
|
|
f03a1d19c1 | |
|
|
60bb4ff983 | |
|
|
539dfa0942 | |
|
|
d9e435c041 | |
|
|
bb4f27a070 | |
|
|
35e0ba6eda | |
|
|
af44bae621 | |
|
|
30dbfa399a | |
|
|
54a7132f14 | |
|
|
d48cbe3fcb | |
|
|
03ee7a3c26 | |
|
|
51b0cbfe28 | |
|
|
229d40cc93 | |
|
|
1e7dc1b392 | |
|
|
127a742db0 | |
|
|
43437bf2d5 | |
|
|
a3038865be | |
|
|
8fdfbcd251 | |
|
|
2460a79026 | |
|
|
9c06883ccf | |
|
|
b326e5616b | |
|
|
a30020a6d6 | |
|
|
dfdfe45b5b | |
|
|
976f40b642 | |
|
|
adb77740b5 | |
|
|
5e14014e37 | |
|
|
475bcb63b5 | |
|
|
cccb044dd1 | |
|
|
cdbad4d946 | |
|
|
933cf9db02 | |
|
|
40bf47f41a | |
|
|
1a0d931ab5 | |
|
|
779156cf9a | |
|
|
2726da5b85 | |
|
|
09b157d74c | |
|
|
145fd1c2f2 | |
|
|
33e9a89305 | |
|
|
417e3d02d1 | |
|
|
ba555de7da | |
|
|
83450ab1d2 | |
|
|
1296b4d16b | |
|
|
2924af5074 | |
|
|
2a8492a053 | |
|
|
94c9b13fbd | |
|
|
1532687191 | |
|
|
128301199d | |
|
|
fbce734ab6 | |
|
|
3294c7c008 | |
|
|
20fbcfadac | |
|
|
4b0cda68b1 | |
|
|
b91a185641 | |
|
|
954e682da8 | |
|
|
3f3009e507 | |
|
|
b93d4a4a17 | |
|
|
d321644e30 | |
|
|
4f20be427e | |
|
|
b4b0eee142 | |
|
|
2935bea6a2 | |
|
|
2bf80d8644 | |
|
|
284dfc05c6 | |
|
|
4a97a13300 | |
|
|
9db8c4a990 | |
|
|
eafbb753da | |
|
|
0e75d96911 | |
|
|
3ae3327a13 | |
|
|
9ec8e717ae | |
|
|
a995989961 | |
|
|
0cf855f16f | |
|
|
88f973fc56 | |
|
|
59e5f4c887 | |
|
|
e0181209c9 | |
|
|
056189265b | |
|
|
36adfff99e | |
|
|
6c45df8c46 | |
|
|
bf6754e20c | |
|
|
bae59fde6a | |
|
|
5ede32b327 |
|
|
@ -6,11 +6,9 @@ updates:
|
||||||
labels: ["area/ci", "dependencies"]
|
labels: ["area/ci", "dependencies"]
|
||||||
groups:
|
groups:
|
||||||
# Group all updates together, so that they are all applied in a single PR.
|
# Group all updates together, so that they are all applied in a single PR.
|
||||||
# Grouped updates are currently in beta and is subject to change.
|
|
||||||
# xref: https://docs.github.com/en/code-security/dependabot/dependabot-version-updates/configuration-options-for-the-dependabot.yml-file#groups
|
# xref: https://docs.github.com/en/code-security/dependabot/dependabot-version-updates/configuration-options-for-the-dependabot.yml-file#groups
|
||||||
ci:
|
ci:
|
||||||
patterns:
|
patterns:
|
||||||
- "*"
|
- "*"
|
||||||
schedule:
|
schedule:
|
||||||
# By default, this will be on a monday.
|
interval: "monthly"
|
||||||
interval: "weekly"
|
|
||||||
|
|
|
||||||
|
|
@ -1,5 +1,9 @@
|
||||||
kind: Cluster
|
kind: Cluster
|
||||||
apiVersion: kind.x-k8s.io/v1alpha4
|
apiVersion: kind.x-k8s.io/v1alpha4
|
||||||
|
nodes:
|
||||||
|
- role: control-plane
|
||||||
|
- role: worker
|
||||||
|
- role: worker
|
||||||
networking:
|
networking:
|
||||||
disableDefaultCNI: true # disable kindnet
|
disableDefaultCNI: true # disable kindnet
|
||||||
podSubnet: 192.168.0.0/16 # set to Calico's default subnet
|
podSubnet: 192.168.0.0/16 # set to Calico's default subnet
|
||||||
|
|
|
||||||
|
|
@ -44,9 +44,12 @@
|
||||||
description: Feature request proposals in the RFC format
|
description: Feature request proposals in the RFC format
|
||||||
color: '#D621C3'
|
color: '#D621C3'
|
||||||
aliases: ['area/RFC']
|
aliases: ['area/RFC']
|
||||||
- name: backport:release/v2.0.x
|
- name: backport:release/v2.4.x
|
||||||
description: To be backported to release/v2.0.x
|
description: To be backported to release/v2.4.x
|
||||||
color: '#ffd700'
|
color: '#ffd700'
|
||||||
- name: backport:release/v2.1.x
|
- name: backport:release/v2.5.x
|
||||||
description: To be backported to release/v2.1.x
|
description: To be backported to release/v2.5.x
|
||||||
|
color: '#ffd700'
|
||||||
|
- name: backport:release/v2.6.x
|
||||||
|
description: To be backported to release/v2.6.x
|
||||||
color: '#ffd700'
|
color: '#ffd700'
|
||||||
|
|
|
||||||
|
|
@ -4,16 +4,18 @@ The Flux ARM64 end-to-end tests run on Equinix Metal instances provisioned with
|
||||||
|
|
||||||
## Current instances
|
## Current instances
|
||||||
|
|
||||||
| Repository | Runner | Instance | Location |
|
| Repository | Runner | Instance | Location |
|
||||||
|-----------------------------|------------------|------------------------|---------------|
|
|-----------------------------|------------------|----------------|---------------|
|
||||||
| flux2 | equinix-arm-dc-1 | flux-equinix-arm-dc-01 | Washington DC |
|
| flux2 | equinix-arm-dc-1 | flux-arm-dc-01 | Washington DC |
|
||||||
| flux2 | equinix-arm-dc-2 | flux-equinix-arm-dc-01 | Washington DC |
|
| flux2 | equinix-arm-dc-2 | flux-arm-dc-01 | Washington DC |
|
||||||
| flux2 | equinix-arm-da-1 | flux-equinix-arm-da-01 | Dallas |
|
| flux2 | equinix-arm-da-1 | flux-arm-da-01 | Dallas |
|
||||||
| flux2 | equinix-arm-da-2 | flux-equinix-arm-da-01 | Dallas |
|
| flux2 | equinix-arm-da-2 | flux-arm-da-01 | Dallas |
|
||||||
| source-controller | equinix-arm-dc-1 | flux-equinix-arm-dc-01 | Washington DC |
|
| flux-benchmark | equinix-arm-dc-1 | flux-arm-dc-01 | Washington DC |
|
||||||
| source-controller | equinix-arm-da-1 | flux-equinix-arm-da-01 | Dallas |
|
| flux-benchmark | equinix-arm-da-1 | flux-arm-da-01 | Dallas |
|
||||||
| image-automation-controller | equinix-arm-dc-1 | flux-equinix-arm-dc-01 | Washington DC |
|
| source-controller | equinix-arm-dc-1 | flux-arm-dc-01 | Washington DC |
|
||||||
| image-automation-controller | equinix-arm-da-1 | flux-equinix-arm-da-01 | Dallas |
|
| source-controller | equinix-arm-da-1 | flux-arm-da-01 | Dallas |
|
||||||
|
| image-automation-controller | equinix-arm-dc-1 | flux-arm-dc-01 | Washington DC |
|
||||||
|
| image-automation-controller | equinix-arm-da-1 | flux-arm-da-01 | Dallas |
|
||||||
|
|
||||||
Instance spec:
|
Instance spec:
|
||||||
- Ampere Altra Q80-30 80-core processor @ 2.8GHz
|
- Ampere Altra Q80-30 80-core processor @ 2.8GHz
|
||||||
|
|
|
||||||
|
|
@ -18,11 +18,11 @@
|
||||||
|
|
||||||
set -eu
|
set -eu
|
||||||
|
|
||||||
KIND_VERSION=0.17.0
|
KIND_VERSION=0.22.0
|
||||||
KUBECTL_VERSION=1.24.0
|
KUBECTL_VERSION=1.29.0
|
||||||
KUSTOMIZE_VERSION=4.5.7
|
KUSTOMIZE_VERSION=5.3.0
|
||||||
HELM_VERSION=3.10.1
|
HELM_VERSION=3.14.1
|
||||||
GITHUB_RUNNER_VERSION=2.298.2
|
GITHUB_RUNNER_VERSION=2.313.0
|
||||||
PACKAGES="apt-transport-https ca-certificates software-properties-common build-essential libssl-dev gnupg lsb-release jq pkg-config"
|
PACKAGES="apt-transport-https ca-certificates software-properties-common build-essential libssl-dev gnupg lsb-release jq pkg-config"
|
||||||
|
|
||||||
# install prerequisites
|
# install prerequisites
|
||||||
|
|
|
||||||
|
|
@ -22,7 +22,7 @@ RUNNER_NAME=$1
|
||||||
REPOSITORY_TOKEN=$2
|
REPOSITORY_TOKEN=$2
|
||||||
REPOSITORY_URL=${3:-https://github.com/fluxcd/flux2}
|
REPOSITORY_URL=${3:-https://github.com/fluxcd/flux2}
|
||||||
|
|
||||||
GITHUB_RUNNER_VERSION=2.298.2
|
GITHUB_RUNNER_VERSION=2.313.0
|
||||||
|
|
||||||
# download runner
|
# download runner
|
||||||
curl -o actions-runner-linux-arm64.tar.gz -L https://github.com/actions/runner/releases/download/v${GITHUB_RUNNER_VERSION}/actions-runner-linux-arm64-${GITHUB_RUNNER_VERSION}.tar.gz \
|
curl -o actions-runner-linux-arm64.tar.gz -L https://github.com/actions/runner/releases/download/v${GITHUB_RUNNER_VERSION}/actions-runner-linux-arm64-${GITHUB_RUNNER_VERSION}.tar.gz \
|
||||||
|
|
|
||||||
|
|
@ -24,6 +24,6 @@ jobs:
|
||||||
name: action on ${{ matrix.version }}
|
name: action on ${{ matrix.version }}
|
||||||
steps:
|
steps:
|
||||||
- name: Checkout
|
- name: Checkout
|
||||||
uses: actions/checkout@b4ffde65f46336ab88eb53be808477a3936bae11 # v4.1.1
|
uses: actions/checkout@11bd71901bbe5b1630ceea73d27597364c9af683 # v4.2.2
|
||||||
- name: Setup flux
|
- name: Setup flux
|
||||||
uses: ./action
|
uses: ./action
|
||||||
|
|
|
||||||
|
|
@ -4,6 +4,9 @@ on:
|
||||||
pull_request_target:
|
pull_request_target:
|
||||||
types: [closed, labeled]
|
types: [closed, labeled]
|
||||||
|
|
||||||
|
permissions:
|
||||||
|
contents: read
|
||||||
|
|
||||||
jobs:
|
jobs:
|
||||||
pull-request:
|
pull-request:
|
||||||
runs-on: ubuntu-latest
|
runs-on: ubuntu-latest
|
||||||
|
|
@ -13,11 +16,11 @@ jobs:
|
||||||
if: github.event.pull_request.state == 'closed' && github.event.pull_request.merged && (github.event_name != 'labeled' || startsWith('backport:', github.event.label.name))
|
if: github.event.pull_request.state == 'closed' && github.event.pull_request.merged && (github.event_name != 'labeled' || startsWith('backport:', github.event.label.name))
|
||||||
steps:
|
steps:
|
||||||
- name: Checkout
|
- name: Checkout
|
||||||
uses: actions/checkout@b4ffde65f46336ab88eb53be808477a3936bae11 # v4.1.1
|
uses: actions/checkout@11bd71901bbe5b1630ceea73d27597364c9af683 # v4.2.2
|
||||||
with:
|
with:
|
||||||
ref: ${{ github.event.pull_request.head.sha }}
|
ref: ${{ github.event.pull_request.head.sha }}
|
||||||
- name: Create backport PRs
|
- name: Create backport PRs
|
||||||
uses: korthout/backport-action@b982d297e31f500652b2246cf26714796312bd23 # v2.2.0
|
uses: korthout/backport-action@0193454f0c5947491d348f33a275c119f30eb736 # v3.2.1
|
||||||
# xref: https://github.com/korthout/backport-action#inputs
|
# xref: https://github.com/korthout/backport-action#inputs
|
||||||
with:
|
with:
|
||||||
# Use token to allow workflows to be triggered for the created PR
|
# Use token to allow workflows to be triggered for the created PR
|
||||||
|
|
|
||||||
|
|
@ -0,0 +1,256 @@
|
||||||
|
name: conformance
|
||||||
|
|
||||||
|
on:
|
||||||
|
workflow_dispatch:
|
||||||
|
push:
|
||||||
|
branches: [ 'main', 'update-components', 'release/**', 'conform*' ]
|
||||||
|
|
||||||
|
permissions:
|
||||||
|
contents: read
|
||||||
|
|
||||||
|
env:
|
||||||
|
GO_VERSION: 1.24.x
|
||||||
|
|
||||||
|
jobs:
|
||||||
|
conform-kubernetes:
|
||||||
|
runs-on:
|
||||||
|
group: "ARM64"
|
||||||
|
strategy:
|
||||||
|
matrix:
|
||||||
|
# Keep this list up-to-date with https://endoflife.date/kubernetes
|
||||||
|
# Build images with https://github.com/fluxcd/flux-benchmark/actions/workflows/build-kind.yaml
|
||||||
|
KUBERNETES_VERSION: [1.31.5, 1.32.1, 1.33.0]
|
||||||
|
fail-fast: false
|
||||||
|
steps:
|
||||||
|
- name: Checkout
|
||||||
|
uses: actions/checkout@11bd71901bbe5b1630ceea73d27597364c9af683 # v4.2.2
|
||||||
|
- name: Setup Go
|
||||||
|
uses: actions/setup-go@d35c59abb061a4a6fb18e82ac0862c26744d6ab5 # v5.5.0
|
||||||
|
with:
|
||||||
|
go-version: ${{ env.GO_VERSION }}
|
||||||
|
cache-dependency-path: |
|
||||||
|
**/go.sum
|
||||||
|
**/go.mod
|
||||||
|
- name: Prepare
|
||||||
|
id: prep
|
||||||
|
run: |
|
||||||
|
ID=${GITHUB_SHA:0:7}-${{ matrix.KUBERNETES_VERSION }}-$(date +%s)
|
||||||
|
echo "CLUSTER=arm64-${ID}" >> $GITHUB_OUTPUT
|
||||||
|
- name: Build
|
||||||
|
run: |
|
||||||
|
make build
|
||||||
|
- name: Setup Kubernetes
|
||||||
|
uses: helm/kind-action@a1b0e391336a6ee6713a0583f8c6240d70863de3 # v1.12.0
|
||||||
|
with:
|
||||||
|
version: v0.27.0
|
||||||
|
cluster_name: ${{ steps.prep.outputs.CLUSTER }}
|
||||||
|
node_image: ghcr.io/fluxcd/kindest/node:v${{ matrix.KUBERNETES_VERSION }}-arm64
|
||||||
|
- name: Run e2e tests
|
||||||
|
run: TEST_KUBECONFIG=$HOME/.kube/config make e2e
|
||||||
|
- name: Run multi-tenancy tests
|
||||||
|
run: |
|
||||||
|
./bin/flux install
|
||||||
|
./bin/flux create source git flux-system \
|
||||||
|
--interval=15m \
|
||||||
|
--url=https://github.com/fluxcd/flux2-multi-tenancy \
|
||||||
|
--branch=main \
|
||||||
|
--ignore-paths="./clusters/**/flux-system/"
|
||||||
|
./bin/flux create kustomization flux-system \
|
||||||
|
--interval=15m \
|
||||||
|
--source=flux-system \
|
||||||
|
--path=./clusters/staging
|
||||||
|
kubectl -n flux-system wait kustomization/tenants --for=condition=ready --timeout=5m
|
||||||
|
kubectl -n apps wait kustomization/dev-team --for=condition=ready --timeout=1m
|
||||||
|
kubectl -n apps wait helmrelease/podinfo --for=condition=ready --timeout=1m
|
||||||
|
- name: Debug failure
|
||||||
|
if: failure()
|
||||||
|
run: |
|
||||||
|
kubectl -n flux-system get all
|
||||||
|
kubectl -n flux-system describe po
|
||||||
|
kubectl -n flux-system logs deploy/source-controller
|
||||||
|
kubectl -n flux-system logs deploy/kustomize-controller
|
||||||
|
|
||||||
|
conform-k3s:
|
||||||
|
runs-on: ubuntu-latest
|
||||||
|
strategy:
|
||||||
|
matrix:
|
||||||
|
# Keep this list up-to-date with https://endoflife.date/kubernetes
|
||||||
|
# Available versions can be found with "replicated cluster versions"
|
||||||
|
K3S_VERSION: [ 1.31.8, 1.32.4, 1.33.0 ]
|
||||||
|
fail-fast: false
|
||||||
|
steps:
|
||||||
|
- name: Checkout
|
||||||
|
uses: actions/checkout@11bd71901bbe5b1630ceea73d27597364c9af683 # v4.2.2
|
||||||
|
- name: Setup Go
|
||||||
|
uses: actions/setup-go@d35c59abb061a4a6fb18e82ac0862c26744d6ab5 # v5.5.0
|
||||||
|
with:
|
||||||
|
go-version: ${{ env.GO_VERSION }}
|
||||||
|
cache-dependency-path: |
|
||||||
|
**/go.sum
|
||||||
|
**/go.mod
|
||||||
|
- name: Prepare
|
||||||
|
id: prep
|
||||||
|
run: |
|
||||||
|
ID=${GITHUB_SHA:0:7}-${{ matrix.K3S_VERSION }}-$(date +%s)
|
||||||
|
PSEUDO_RAND_SUFFIX=$(echo "${ID}" | shasum | awk '{print $1}')
|
||||||
|
echo "cluster=flux2-k3s-${PSEUDO_RAND_SUFFIX}" >> $GITHUB_OUTPUT
|
||||||
|
KUBECONFIG_PATH="$(git rev-parse --show-toplevel)/bin/kubeconfig.yaml"
|
||||||
|
echo "kubeconfig-path=${KUBECONFIG_PATH}" >> $GITHUB_OUTPUT
|
||||||
|
- name: Setup Kustomize
|
||||||
|
uses: fluxcd/pkg/actions/kustomize@9e79277372c4746ff091eba1f10aee82974ecdaa # main
|
||||||
|
- name: Build
|
||||||
|
run: make build-dev
|
||||||
|
- name: Create repository
|
||||||
|
run: |
|
||||||
|
gh repo create --private --add-readme fluxcd-testing/${{ steps.prep.outputs.cluster }}
|
||||||
|
env:
|
||||||
|
GITHUB_TOKEN: ${{ secrets.GITPROVIDER_BOT_TOKEN }}
|
||||||
|
- name: Create cluster
|
||||||
|
id: create-cluster
|
||||||
|
uses: replicatedhq/replicated-actions/create-cluster@49b440dabd7e0e868cbbabda5cfc0d8332a279fa # v1.19.0
|
||||||
|
with:
|
||||||
|
api-token: ${{ secrets.REPLICATED_API_TOKEN }}
|
||||||
|
kubernetes-distribution: "k3s"
|
||||||
|
kubernetes-version: ${{ matrix.K3S_VERSION }}
|
||||||
|
ttl: 20m
|
||||||
|
cluster-name: "${{ steps.prep.outputs.cluster }}"
|
||||||
|
kubeconfig-path: ${{ steps.prep.outputs.kubeconfig-path }}
|
||||||
|
export-kubeconfig: true
|
||||||
|
- name: Run e2e tests
|
||||||
|
run: TEST_KUBECONFIG=${{ steps.prep.outputs.kubeconfig-path }} make e2e
|
||||||
|
- name: Run flux bootstrap
|
||||||
|
run: |
|
||||||
|
./bin/flux bootstrap git --manifests ./manifests/install/ \
|
||||||
|
--components-extra=image-reflector-controller,image-automation-controller \
|
||||||
|
--url=https://github.com/fluxcd-testing/${{ steps.prep.outputs.cluster }} \
|
||||||
|
--branch=main \
|
||||||
|
--path=clusters/k3s \
|
||||||
|
--token-auth
|
||||||
|
env:
|
||||||
|
GIT_PASSWORD: ${{ secrets.GITPROVIDER_BOT_TOKEN }}
|
||||||
|
- name: Run flux check
|
||||||
|
run: |
|
||||||
|
./bin/flux check
|
||||||
|
- name: Run flux reconcile
|
||||||
|
run: |
|
||||||
|
./bin/flux reconcile ks flux-system --with-source
|
||||||
|
./bin/flux get all
|
||||||
|
./bin/flux events
|
||||||
|
- name: Collect reconcile logs
|
||||||
|
if: ${{ always() }}
|
||||||
|
continue-on-error: true
|
||||||
|
run: |
|
||||||
|
kubectl -n flux-system get all
|
||||||
|
kubectl -n flux-system describe pods
|
||||||
|
kubectl -n flux-system logs deploy/source-controller
|
||||||
|
kubectl -n flux-system logs deploy/kustomize-controller
|
||||||
|
kubectl -n flux-system logs deploy/notification-controller
|
||||||
|
- name: Delete flux
|
||||||
|
run: |
|
||||||
|
./bin/flux uninstall -s --keep-namespace
|
||||||
|
kubectl delete ns flux-system --wait
|
||||||
|
- name: Delete cluster
|
||||||
|
if: ${{ always() }}
|
||||||
|
uses: replicatedhq/replicated-actions/remove-cluster@49b440dabd7e0e868cbbabda5cfc0d8332a279fa # v1.19.0
|
||||||
|
continue-on-error: true
|
||||||
|
with:
|
||||||
|
api-token: ${{ secrets.REPLICATED_API_TOKEN }}
|
||||||
|
cluster-id: ${{ steps.create-cluster.outputs.cluster-id }}
|
||||||
|
- name: Delete repository
|
||||||
|
if: ${{ always() }}
|
||||||
|
continue-on-error: true
|
||||||
|
run: |
|
||||||
|
gh repo delete fluxcd-testing/${{ steps.prep.outputs.cluster }} --yes
|
||||||
|
env:
|
||||||
|
GITHUB_TOKEN: ${{ secrets.GITPROVIDER_BOT_TOKEN }}
|
||||||
|
|
||||||
|
conform-openshift:
|
||||||
|
runs-on: ubuntu-latest
|
||||||
|
strategy:
|
||||||
|
matrix:
|
||||||
|
# Keep this list up-to-date with https://endoflife.date/red-hat-openshift
|
||||||
|
OPENSHIFT_VERSION: [ 4.18.0-okd ]
|
||||||
|
fail-fast: false
|
||||||
|
steps:
|
||||||
|
- name: Checkout
|
||||||
|
uses: actions/checkout@11bd71901bbe5b1630ceea73d27597364c9af683 # v4.2.2
|
||||||
|
- name: Setup Go
|
||||||
|
uses: actions/setup-go@d35c59abb061a4a6fb18e82ac0862c26744d6ab5 # v5.5.0
|
||||||
|
with:
|
||||||
|
go-version: ${{ env.GO_VERSION }}
|
||||||
|
cache-dependency-path: |
|
||||||
|
**/go.sum
|
||||||
|
**/go.mod
|
||||||
|
- name: Prepare
|
||||||
|
id: prep
|
||||||
|
run: |
|
||||||
|
ID=${GITHUB_SHA:0:7}-${{ matrix.OPENSHIFT_VERSION }}-$(date +%s)
|
||||||
|
PSEUDO_RAND_SUFFIX=$(echo "${ID}" | shasum | awk '{print $1}')
|
||||||
|
echo "cluster=flux2-openshift-${PSEUDO_RAND_SUFFIX}" >> $GITHUB_OUTPUT
|
||||||
|
KUBECONFIG_PATH="$(git rev-parse --show-toplevel)/bin/kubeconfig.yaml"
|
||||||
|
echo "kubeconfig-path=${KUBECONFIG_PATH}" >> $GITHUB_OUTPUT
|
||||||
|
- name: Setup Kustomize
|
||||||
|
uses: fluxcd/pkg/actions/kustomize@9e79277372c4746ff091eba1f10aee82974ecdaa # main
|
||||||
|
- name: Build
|
||||||
|
run: make build-dev
|
||||||
|
- name: Create repository
|
||||||
|
run: |
|
||||||
|
gh repo create --private --add-readme fluxcd-testing/${{ steps.prep.outputs.cluster }}
|
||||||
|
env:
|
||||||
|
GITHUB_TOKEN: ${{ secrets.GITPROVIDER_BOT_TOKEN }}
|
||||||
|
- name: Create cluster
|
||||||
|
id: create-cluster
|
||||||
|
uses: replicatedhq/replicated-actions/create-cluster@49b440dabd7e0e868cbbabda5cfc0d8332a279fa # v1.19.0
|
||||||
|
with:
|
||||||
|
api-token: ${{ secrets.REPLICATED_API_TOKEN }}
|
||||||
|
kubernetes-distribution: "openshift"
|
||||||
|
kubernetes-version: ${{ matrix.OPENSHIFT_VERSION }}
|
||||||
|
ttl: 20m
|
||||||
|
cluster-name: "${{ steps.prep.outputs.cluster }}"
|
||||||
|
kubeconfig-path: ${{ steps.prep.outputs.kubeconfig-path }}
|
||||||
|
export-kubeconfig: true
|
||||||
|
- name: Run flux bootstrap
|
||||||
|
run: |
|
||||||
|
./bin/flux bootstrap git --manifests ./manifests/openshift/ \
|
||||||
|
--components-extra=image-reflector-controller,image-automation-controller \
|
||||||
|
--url=https://github.com/fluxcd-testing/${{ steps.prep.outputs.cluster }} \
|
||||||
|
--branch=main \
|
||||||
|
--path=clusters/openshift \
|
||||||
|
--token-auth
|
||||||
|
env:
|
||||||
|
GIT_PASSWORD: ${{ secrets.GITPROVIDER_BOT_TOKEN }}
|
||||||
|
- name: Run flux check
|
||||||
|
run: |
|
||||||
|
./bin/flux check
|
||||||
|
- name: Run flux reconcile
|
||||||
|
run: |
|
||||||
|
./bin/flux reconcile ks flux-system --with-source
|
||||||
|
./bin/flux get all
|
||||||
|
./bin/flux events
|
||||||
|
- name: Collect reconcile logs
|
||||||
|
if: ${{ always() }}
|
||||||
|
continue-on-error: true
|
||||||
|
run: |
|
||||||
|
kubectl -n flux-system get all
|
||||||
|
kubectl -n flux-system describe pods
|
||||||
|
kubectl -n flux-system logs deploy/source-controller
|
||||||
|
kubectl -n flux-system logs deploy/kustomize-controller
|
||||||
|
kubectl -n flux-system logs deploy/notification-controller
|
||||||
|
- name: Delete flux
|
||||||
|
run: |
|
||||||
|
./bin/flux uninstall -s --keep-namespace
|
||||||
|
kubectl delete ns flux-system --wait
|
||||||
|
- name: Delete cluster
|
||||||
|
if: ${{ always() }}
|
||||||
|
uses: replicatedhq/replicated-actions/remove-cluster@49b440dabd7e0e868cbbabda5cfc0d8332a279fa # v1.19.0
|
||||||
|
continue-on-error: true
|
||||||
|
with:
|
||||||
|
api-token: ${{ secrets.REPLICATED_API_TOKEN }}
|
||||||
|
cluster-id: ${{ steps.create-cluster.outputs.cluster-id }}
|
||||||
|
- name: Delete repository
|
||||||
|
if: ${{ always() }}
|
||||||
|
continue-on-error: true
|
||||||
|
run: |
|
||||||
|
gh repo delete fluxcd-testing/${{ steps.prep.outputs.cluster }} --yes
|
||||||
|
env:
|
||||||
|
GITHUB_TOKEN: ${{ secrets.GITPROVIDER_BOT_TOKEN }}
|
||||||
|
|
@ -1,106 +0,0 @@
|
||||||
name: e2e-arm64
|
|
||||||
|
|
||||||
on:
|
|
||||||
workflow_dispatch:
|
|
||||||
push:
|
|
||||||
branches: [ 'main', 'update-components', 'e2e-*', 'release/**' ]
|
|
||||||
|
|
||||||
permissions:
|
|
||||||
contents: read
|
|
||||||
|
|
||||||
jobs:
|
|
||||||
e2e-arm64-kubernetes:
|
|
||||||
# Hosted on Equinix
|
|
||||||
# Docs: https://github.com/fluxcd/flux2/tree/main/.github/runners
|
|
||||||
runs-on: [self-hosted, Linux, ARM64, equinix]
|
|
||||||
strategy:
|
|
||||||
matrix:
|
|
||||||
# Keep this list up-to-date with https://endoflife.date/kubernetes
|
|
||||||
# Check which versions are available on DockerHub with 'crane ls kindest/node'
|
|
||||||
KUBERNETES_VERSION: [ 1.26.6, 1.27.3, 1.28.0 ]
|
|
||||||
fail-fast: false
|
|
||||||
steps:
|
|
||||||
- name: Checkout
|
|
||||||
uses: actions/checkout@b4ffde65f46336ab88eb53be808477a3936bae11 # v4.1.1
|
|
||||||
- name: Setup Go
|
|
||||||
uses: actions/setup-go@0c52d547c9bc32b1aa3301fd7a9cb496313a4491 # v5.0.0
|
|
||||||
with:
|
|
||||||
go-version: 1.20.x
|
|
||||||
cache-dependency-path: |
|
|
||||||
**/go.sum
|
|
||||||
**/go.mod
|
|
||||||
- name: Prepare
|
|
||||||
id: prep
|
|
||||||
run: |
|
|
||||||
ID=${GITHUB_SHA:0:7}-${{ matrix.KUBERNETES_VERSION }}-$(date +%s)
|
|
||||||
echo "CLUSTER=arm64-${ID}" >> $GITHUB_OUTPUT
|
|
||||||
- name: Build
|
|
||||||
run: |
|
|
||||||
make build
|
|
||||||
- name: Setup Kubernetes Kind
|
|
||||||
run: |
|
|
||||||
kind create cluster \
|
|
||||||
--wait 5m \
|
|
||||||
--name ${{ steps.prep.outputs.CLUSTER }} \
|
|
||||||
--kubeconfig=/tmp/${{ steps.prep.outputs.CLUSTER }} \
|
|
||||||
--image=kindest/node:v${{ matrix.KUBERNETES_VERSION }}
|
|
||||||
- name: Run e2e tests
|
|
||||||
run: TEST_KUBECONFIG=/tmp/${{ steps.prep.outputs.CLUSTER }} make e2e
|
|
||||||
- name: Run multi-tenancy tests
|
|
||||||
env:
|
|
||||||
KUBECONFIG: /tmp/${{ steps.prep.outputs.CLUSTER }}
|
|
||||||
run: |
|
|
||||||
./bin/flux install
|
|
||||||
./bin/flux create source git flux-system \
|
|
||||||
--interval=15m \
|
|
||||||
--url=https://github.com/fluxcd/flux2-multi-tenancy \
|
|
||||||
--branch=main \
|
|
||||||
--ignore-paths="./clusters/**/flux-system/"
|
|
||||||
./bin/flux create kustomization flux-system \
|
|
||||||
--interval=15m \
|
|
||||||
--source=flux-system \
|
|
||||||
--path=./clusters/staging
|
|
||||||
kubectl -n flux-system wait kustomization/tenants --for=condition=ready --timeout=5m
|
|
||||||
kubectl -n apps wait kustomization/dev-team --for=condition=ready --timeout=1m
|
|
||||||
kubectl -n apps wait helmrelease/podinfo --for=condition=ready --timeout=1m
|
|
||||||
- name: Run monitoring tests
|
|
||||||
# Keep this test in sync with https://fluxcd.io/flux/guides/monitoring/
|
|
||||||
env:
|
|
||||||
KUBECONFIG: /tmp/${{ steps.prep.outputs.CLUSTER }}
|
|
||||||
run: |
|
|
||||||
./bin/flux create source git flux-monitoring \
|
|
||||||
--interval=30m \
|
|
||||||
--url=https://github.com/fluxcd/flux2 \
|
|
||||||
--branch=${GITHUB_REF#refs/heads/}
|
|
||||||
./bin/flux create kustomization kube-prometheus-stack \
|
|
||||||
--interval=1h \
|
|
||||||
--prune \
|
|
||||||
--source=flux-monitoring \
|
|
||||||
--path="./manifests/monitoring/kube-prometheus-stack" \
|
|
||||||
--health-check-timeout=5m \
|
|
||||||
--wait
|
|
||||||
./bin/flux create kustomization monitoring-config \
|
|
||||||
--depends-on=kube-prometheus-stack \
|
|
||||||
--interval=1h \
|
|
||||||
--prune=true \
|
|
||||||
--source=flux-monitoring \
|
|
||||||
--path="./manifests/monitoring/monitoring-config" \
|
|
||||||
--health-check-timeout=1m \
|
|
||||||
--wait
|
|
||||||
kubectl -n flux-system wait kustomization/kube-prometheus-stack --for=condition=ready --timeout=5m
|
|
||||||
kubectl -n flux-system wait kustomization/monitoring-config --for=condition=ready --timeout=5m
|
|
||||||
kubectl -n monitoring wait helmrelease/kube-prometheus-stack --for=condition=ready --timeout=1m
|
|
||||||
- name: Debug failure
|
|
||||||
if: failure()
|
|
||||||
env:
|
|
||||||
KUBECONFIG: /tmp/${{ steps.prep.outputs.CLUSTER }}
|
|
||||||
run: |
|
|
||||||
kubectl -n flux-system get all
|
|
||||||
kubectl -n flux-system describe po
|
|
||||||
kubectl -n flux-system logs deploy/source-controller
|
|
||||||
kubectl -n flux-system logs deploy/kustomize-controller
|
|
||||||
- name: Cleanup
|
|
||||||
if: always()
|
|
||||||
run: |
|
|
||||||
kind delete cluster --name ${{ steps.prep.outputs.CLUSTER }}
|
|
||||||
rm /tmp/${{ steps.prep.outputs.CLUSTER }}
|
|
||||||
|
|
@ -21,52 +21,7 @@ permissions:
|
||||||
contents: read
|
contents: read
|
||||||
|
|
||||||
jobs:
|
jobs:
|
||||||
e2e-amd64-aks:
|
e2e-aks:
|
||||||
runs-on: ubuntu-22.04
|
|
||||||
defaults:
|
|
||||||
run:
|
|
||||||
working-directory: ./tests/azure
|
|
||||||
# This job is currently disabled. Remove the false check when Azure subscription is enabled.
|
|
||||||
if: false && (github.event_name != 'pull_request' || github.event.pull_request.head.repo.full_name == github.repository) && github.actor != 'dependabot[bot]'
|
|
||||||
steps:
|
|
||||||
- name: Checkout
|
|
||||||
uses: actions/checkout@b4ffde65f46336ab88eb53be808477a3936bae11 # v4.1.1
|
|
||||||
- name: Setup Go
|
|
||||||
uses: actions/setup-go@0c52d547c9bc32b1aa3301fd7a9cb496313a4491 # v5.0.0
|
|
||||||
with:
|
|
||||||
go-version: 1.20.x
|
|
||||||
cache-dependency-path: tests/azure/go.sum
|
|
||||||
- name: Setup Flux CLI
|
|
||||||
run: |
|
|
||||||
make build
|
|
||||||
mkdir -p $HOME/.local/bin
|
|
||||||
mv ./bin/flux $HOME/.local/bin
|
|
||||||
working-directory: ./
|
|
||||||
- name: Setup SOPS
|
|
||||||
run: |
|
|
||||||
mkdir -p $HOME/.local/bin
|
|
||||||
wget https://github.com/mozilla/sops/releases/download/v3.7.1/sops-v3.7.1.linux -O $HOME/.local/bin/sops
|
|
||||||
chmod +x $HOME/.local/bin/sops
|
|
||||||
- name: Setup Terraform
|
|
||||||
uses: hashicorp/setup-terraform@a1502cd9e758c50496cc9ac5308c4843bcd56d36 # v2
|
|
||||||
with:
|
|
||||||
terraform_version: 1.2.8
|
|
||||||
terraform_wrapper: false
|
|
||||||
- name: Setup Azure CLI
|
|
||||||
run: |
|
|
||||||
curl -sL https://aka.ms/InstallAzureCLIDeb | sudo bash
|
|
||||||
- name: Run Azure e2e tests
|
|
||||||
env:
|
|
||||||
ARM_CLIENT_ID: ${{ secrets.ARM_CLIENT_ID }}
|
|
||||||
ARM_CLIENT_SECRET: ${{ secrets.ARM_CLIENT_SECRET }}
|
|
||||||
ARM_SUBSCRIPTION_ID: ${{ secrets.ARM_SUBSCRIPTION_ID }}
|
|
||||||
ARM_TENANT_ID: ${{ secrets.ARM_TENANT_ID }}
|
|
||||||
run: |
|
|
||||||
ls $HOME/.local/bin
|
|
||||||
az login --service-principal -u ${ARM_CLIENT_ID} -p ${ARM_CLIENT_SECRET} -t ${ARM_TENANT_ID}
|
|
||||||
go test -v -coverprofile cover.out -timeout 60m .
|
|
||||||
|
|
||||||
refactored-e2e-amd64-aks:
|
|
||||||
runs-on: ubuntu-22.04
|
runs-on: ubuntu-22.04
|
||||||
defaults:
|
defaults:
|
||||||
run:
|
run:
|
||||||
|
|
@ -75,12 +30,14 @@ jobs:
|
||||||
if: false && (github.event_name != 'pull_request' || github.event.pull_request.head.repo.full_name == github.repository) && github.actor != 'dependabot[bot]'
|
if: false && (github.event_name != 'pull_request' || github.event.pull_request.head.repo.full_name == github.repository) && github.actor != 'dependabot[bot]'
|
||||||
steps:
|
steps:
|
||||||
- name: CheckoutD
|
- name: CheckoutD
|
||||||
uses: actions/checkout@b4ffde65f46336ab88eb53be808477a3936bae11 # v4.1.1
|
uses: actions/checkout@11bd71901bbe5b1630ceea73d27597364c9af683 # v4.2.2
|
||||||
- name: Setup Go
|
- name: Setup Go
|
||||||
uses: actions/setup-go@0c52d547c9bc32b1aa3301fd7a9cb496313a4491 # v5.0.0
|
uses: actions/setup-go@d35c59abb061a4a6fb18e82ac0862c26744d6ab5 # v5.5.0
|
||||||
with:
|
with:
|
||||||
go-version: 1.20.x
|
go-version: 1.24.x
|
||||||
cache-dependency-path: tests/integration/go.sum
|
cache-dependency-path: tests/integration/go.sum
|
||||||
|
- name: Setup Terraform
|
||||||
|
uses: hashicorp/setup-terraform@b9cd54a3c349d3f38e8881555d616ced269862dd # v3.1.2
|
||||||
- name: Setup Flux CLI
|
- name: Setup Flux CLI
|
||||||
run: make build
|
run: make build
|
||||||
working-directory: ./
|
working-directory: ./
|
||||||
|
|
@ -92,7 +49,7 @@ jobs:
|
||||||
env:
|
env:
|
||||||
SOPS_VER: 3.7.1
|
SOPS_VER: 3.7.1
|
||||||
- name: Authenticate to Azure
|
- name: Authenticate to Azure
|
||||||
uses: Azure/login@de95379fe4dadc2defb305917eaa7e5dde727294 # v1.4.6
|
uses: Azure/login@a457da9ea143d694b1b9c7c869ebb04ebe844ef5 # v1.4.6
|
||||||
with:
|
with:
|
||||||
creds: '{"clientId":"${{ secrets.AZ_ARM_CLIENT_ID }}","clientSecret":"${{ secrets.AZ_ARM_CLIENT_SECRET }}","subscriptionId":"${{ secrets.AZ_ARM_SUBSCRIPTION_ID }}","tenantId":"${{ secrets.AZ_ARM_TENANT_ID }}"}'
|
creds: '{"clientId":"${{ secrets.AZ_ARM_CLIENT_ID }}","clientSecret":"${{ secrets.AZ_ARM_CLIENT_SECRET }}","subscriptionId":"${{ secrets.AZ_ARM_SUBSCRIPTION_ID }}","tenantId":"${{ secrets.AZ_ARM_TENANT_ID }}"}'
|
||||||
- name: Set dynamic variables in .env
|
- name: Set dynamic variables in .env
|
||||||
|
|
@ -123,3 +80,14 @@ jobs:
|
||||||
echo $GITREPO_SSH_PUB_CONTENTS | base64 -d > ./build/ssh/key.pub
|
echo $GITREPO_SSH_PUB_CONTENTS | base64 -d > ./build/ssh/key.pub
|
||||||
export GITREPO_SSH_PUB_PATH=build/ssh/key.pub
|
export GITREPO_SSH_PUB_PATH=build/ssh/key.pub
|
||||||
make test-azure
|
make test-azure
|
||||||
|
- name: Ensure resource cleanup
|
||||||
|
if: ${{ always() }}
|
||||||
|
env:
|
||||||
|
ARM_CLIENT_ID: ${{ secrets.AZ_ARM_CLIENT_ID }}
|
||||||
|
ARM_CLIENT_SECRET: ${{ secrets.AZ_ARM_CLIENT_SECRET }}
|
||||||
|
ARM_SUBSCRIPTION_ID: ${{ secrets.AZ_ARM_SUBSCRIPTION_ID }}
|
||||||
|
ARM_TENANT_ID: ${{ secrets.AZ_ARM_TENANT_ID }}
|
||||||
|
TF_VAR_azuredevops_org: ${{ secrets.TF_VAR_azuredevops_org }}
|
||||||
|
TF_VAR_azuredevops_pat: ${{ secrets.TF_VAR_azuredevops_pat }}
|
||||||
|
TF_VAR_location: ${{ vars.TF_VAR_azure_location }}
|
||||||
|
run: source .env && make destroy-azure
|
||||||
|
|
|
||||||
|
|
@ -17,29 +17,29 @@ jobs:
|
||||||
if: (github.event_name != 'pull_request' || github.event.pull_request.head.repo.full_name == github.repository) && github.actor != 'dependabot[bot]'
|
if: (github.event_name != 'pull_request' || github.event.pull_request.head.repo.full_name == github.repository) && github.actor != 'dependabot[bot]'
|
||||||
steps:
|
steps:
|
||||||
- name: Checkout
|
- name: Checkout
|
||||||
uses: actions/checkout@b4ffde65f46336ab88eb53be808477a3936bae11 # v4.1.1
|
uses: actions/checkout@11bd71901bbe5b1630ceea73d27597364c9af683 # v4.2.2
|
||||||
- name: Setup Go
|
- name: Setup Go
|
||||||
uses: actions/setup-go@0c52d547c9bc32b1aa3301fd7a9cb496313a4491 # v5.0.0
|
uses: actions/setup-go@d35c59abb061a4a6fb18e82ac0862c26744d6ab5 # v5.5.0
|
||||||
with:
|
with:
|
||||||
go-version: 1.20.x
|
go-version: 1.24.x
|
||||||
cache-dependency-path: |
|
cache-dependency-path: |
|
||||||
**/go.sum
|
**/go.sum
|
||||||
**/go.mod
|
**/go.mod
|
||||||
- name: Setup Kubernetes
|
- name: Setup Kubernetes
|
||||||
uses: helm/kind-action@dda0770415bac9fc20092cacbc54aa298604d140 # v1.8.0
|
uses: helm/kind-action@a1b0e391336a6ee6713a0583f8c6240d70863de3 # v1.12.0
|
||||||
with:
|
with:
|
||||||
version: v0.20.0
|
version: v0.24.0
|
||||||
cluster_name: kind
|
cluster_name: kind
|
||||||
# The versions below should target the newest Kubernetes version
|
# The versions below should target the newest Kubernetes version
|
||||||
# Keep this up-to-date with https://endoflife.date/kubernetes
|
# Keep this up-to-date with https://endoflife.date/kubernetes
|
||||||
node_image: kindest/node:v1.28.0@sha256:9f3ff58f19dcf1a0611d11e8ac989fdb30a28f40f236f59f0bea31fb956ccf5c
|
node_image: ghcr.io/fluxcd/kindest/node:v1.33.0-amd64
|
||||||
kubectl_version: v1.28.0
|
kubectl_version: v1.32.0
|
||||||
- name: Setup Kustomize
|
- name: Setup Kustomize
|
||||||
uses: fluxcd/pkg/actions/kustomize@main
|
uses: fluxcd/pkg/actions/kustomize@9e79277372c4746ff091eba1f10aee82974ecdaa # main
|
||||||
|
- name: Setup yq
|
||||||
|
uses: fluxcd/pkg/actions/yq@9e79277372c4746ff091eba1f10aee82974ecdaa # main
|
||||||
- name: Build
|
- name: Build
|
||||||
run: |
|
run: make build-dev
|
||||||
make cmd/flux/.manifests.done
|
|
||||||
go build -o /tmp/flux ./cmd/flux
|
|
||||||
- name: Set outputs
|
- name: Set outputs
|
||||||
id: vars
|
id: vars
|
||||||
run: |
|
run: |
|
||||||
|
|
@ -51,18 +51,24 @@ jobs:
|
||||||
echo "test_repo_name=$TEST_REPO_NAME" >> $GITHUB_OUTPUT
|
echo "test_repo_name=$TEST_REPO_NAME" >> $GITHUB_OUTPUT
|
||||||
- name: bootstrap init
|
- name: bootstrap init
|
||||||
run: |
|
run: |
|
||||||
/tmp/flux bootstrap github --manifests ./manifests/install/ \
|
./bin/flux bootstrap github --manifests ./manifests/install/ \
|
||||||
--owner=fluxcd-testing \
|
--owner=fluxcd-testing \
|
||||||
|
--image-pull-secret=ghcr-auth \
|
||||||
|
--registry-creds=fluxcd:$GITHUB_TOKEN \
|
||||||
--repository=${{ steps.vars.outputs.test_repo_name }} \
|
--repository=${{ steps.vars.outputs.test_repo_name }} \
|
||||||
--branch=main \
|
--branch=main \
|
||||||
--path=test-cluster \
|
--path=test-cluster \
|
||||||
--team=team-z
|
--team=team-z
|
||||||
env:
|
env:
|
||||||
GITHUB_TOKEN: ${{ secrets.GITPROVIDER_BOT_TOKEN }}
|
GITHUB_TOKEN: ${{ secrets.GITPROVIDER_BOT_TOKEN }}
|
||||||
|
- name: verify image pull secret
|
||||||
|
run: |
|
||||||
|
kubectl -n flux-system get secret ghcr-auth | grep dockerconfigjson
|
||||||
- name: bootstrap no-op
|
- name: bootstrap no-op
|
||||||
run: |
|
run: |
|
||||||
/tmp/flux bootstrap github --manifests ./manifests/install/ \
|
./bin/flux bootstrap github --manifests ./manifests/install/ \
|
||||||
--owner=fluxcd-testing \
|
--owner=fluxcd-testing \
|
||||||
|
--image-pull-secret=ghcr-auth \
|
||||||
--repository=${{ steps.vars.outputs.test_repo_name }} \
|
--repository=${{ steps.vars.outputs.test_repo_name }} \
|
||||||
--branch=main \
|
--branch=main \
|
||||||
--path=test-cluster \
|
--path=test-cluster \
|
||||||
|
|
@ -72,7 +78,7 @@ jobs:
|
||||||
- name: bootstrap customize
|
- name: bootstrap customize
|
||||||
run: |
|
run: |
|
||||||
make setup-bootstrap-patch
|
make setup-bootstrap-patch
|
||||||
/tmp/flux bootstrap github --manifests ./manifests/install/ \
|
./bin/flux bootstrap github --manifests ./manifests/install/ \
|
||||||
--owner=fluxcd-testing \
|
--owner=fluxcd-testing \
|
||||||
--repository=${{ steps.vars.outputs.test_repo_name }} \
|
--repository=${{ steps.vars.outputs.test_repo_name }} \
|
||||||
--branch=main \
|
--branch=main \
|
||||||
|
|
@ -87,46 +93,33 @@ jobs:
|
||||||
GITHUB_ORG_NAME: fluxcd-testing
|
GITHUB_ORG_NAME: fluxcd-testing
|
||||||
- name: uninstall
|
- name: uninstall
|
||||||
run: |
|
run: |
|
||||||
/tmp/flux uninstall -s --keep-namespace
|
./bin/flux uninstall -s --keep-namespace
|
||||||
kubectl delete ns flux-system --timeout=10m --wait=true
|
kubectl delete ns flux-system --timeout=10m --wait=true
|
||||||
- name: test image automation
|
- name: test image automation
|
||||||
run: |
|
run: |
|
||||||
make setup-image-automation
|
make setup-image-automation
|
||||||
/tmp/flux bootstrap github --manifests ./manifests/install/ \
|
./bin/flux bootstrap github --manifests ./manifests/install/ \
|
||||||
--owner=fluxcd-testing \
|
--owner=fluxcd-testing \
|
||||||
--repository=${{ steps.vars.outputs.test_repo_name }} \
|
--repository=${{ steps.vars.outputs.test_repo_name }} \
|
||||||
--branch=main \
|
--branch=main \
|
||||||
--path=test-cluster \
|
--path=test-cluster \
|
||||||
--read-write-key
|
--read-write-key
|
||||||
/tmp/flux reconcile image repository podinfo
|
./bin/flux reconcile image repository podinfo
|
||||||
/tmp/flux get images all
|
./bin/flux reconcile image update flux-system
|
||||||
|
./bin/flux get images all
|
||||||
retries=10
|
./bin/flux -n flux-system events --for ImageUpdateAutomation/flux-system
|
||||||
count=0
|
kubectl -n flux-system get -o yaml ImageUpdateAutomation flux-system
|
||||||
ok=false
|
kubectl -n flux-system get -o yaml ImageUpdateAutomation flux-system | \
|
||||||
until ${ok}; do
|
yq '.status.lastPushCommit | length > 1' | grep 'true'
|
||||||
/tmp/flux get image update flux-system | grep 'commit' && ok=true || ok=false
|
|
||||||
count=$(($count + 1))
|
|
||||||
if [[ ${count} -eq ${retries} ]]; then
|
|
||||||
echo "No more retries left"
|
|
||||||
exit 1
|
|
||||||
fi
|
|
||||||
sleep 6
|
|
||||||
/tmp/flux reconcile image update flux-system
|
|
||||||
done
|
|
||||||
env:
|
env:
|
||||||
GITHUB_TOKEN: ${{ secrets.GITPROVIDER_BOT_TOKEN }}
|
GITHUB_TOKEN: ${{ secrets.GITPROVIDER_BOT_TOKEN }}
|
||||||
GITHUB_REPO_NAME: ${{ steps.vars.outputs.test_repo_name }}
|
GITHUB_REPO_NAME: ${{ steps.vars.outputs.test_repo_name }}
|
||||||
GITHUB_ORG_NAME: fluxcd-testing
|
GITHUB_ORG_NAME: fluxcd-testing
|
||||||
- name: delete repository
|
- name: delete repository
|
||||||
if: ${{ always() }}
|
if: ${{ always() }}
|
||||||
|
continue-on-error: true
|
||||||
run: |
|
run: |
|
||||||
curl \
|
gh repo delete fluxcd-testing/${{ steps.vars.outputs.test_repo_name }} --yes
|
||||||
-X DELETE \
|
|
||||||
-H "Accept: application/vnd.github.v3+json" \
|
|
||||||
-H "Authorization: token ${GITHUB_TOKEN}" \
|
|
||||||
--fail --silent \
|
|
||||||
https://api.github.com/repos/fluxcd-testing/${{ steps.vars.outputs.test_repo_name }}
|
|
||||||
env:
|
env:
|
||||||
GITHUB_TOKEN: ${{ secrets.GITPROVIDER_BOT_TOKEN }}
|
GITHUB_TOKEN: ${{ secrets.GITPROVIDER_BOT_TOKEN }}
|
||||||
- name: Debug failure
|
- name: Debug failure
|
||||||
|
|
|
||||||
|
|
@ -29,12 +29,14 @@ jobs:
|
||||||
if: (github.event_name != 'pull_request' || github.event.pull_request.head.repo.full_name == github.repository) && github.actor != 'dependabot[bot]'
|
if: (github.event_name != 'pull_request' || github.event.pull_request.head.repo.full_name == github.repository) && github.actor != 'dependabot[bot]'
|
||||||
steps:
|
steps:
|
||||||
- name: Checkout
|
- name: Checkout
|
||||||
uses: actions/checkout@b4ffde65f46336ab88eb53be808477a3936bae11 # v4.1.1
|
uses: actions/checkout@11bd71901bbe5b1630ceea73d27597364c9af683 # v4.2.2
|
||||||
- name: Setup Go
|
- name: Setup Go
|
||||||
uses: actions/setup-go@0c52d547c9bc32b1aa3301fd7a9cb496313a4491 # v5.0.0
|
uses: actions/setup-go@d35c59abb061a4a6fb18e82ac0862c26744d6ab5 # v5.5.0
|
||||||
with:
|
with:
|
||||||
go-version: 1.20.x
|
go-version: 1.24.x
|
||||||
cache-dependency-path: tests/integration/go.sum
|
cache-dependency-path: tests/integration/go.sum
|
||||||
|
- name: Setup Terraform
|
||||||
|
uses: hashicorp/setup-terraform@b9cd54a3c349d3f38e8881555d616ced269862dd # v3.1.2
|
||||||
- name: Setup Flux CLI
|
- name: Setup Flux CLI
|
||||||
run: make build
|
run: make build
|
||||||
working-directory: ./
|
working-directory: ./
|
||||||
|
|
@ -46,19 +48,19 @@ jobs:
|
||||||
env:
|
env:
|
||||||
SOPS_VER: 3.7.1
|
SOPS_VER: 3.7.1
|
||||||
- name: Authenticate to Google Cloud
|
- name: Authenticate to Google Cloud
|
||||||
uses: google-github-actions/auth@67e9c72af6e0492df856527b474995862b7b6591 # v2.0.0
|
uses: google-github-actions/auth@ba79af03959ebeac9769e648f473a284504d9193 # v2.1.10
|
||||||
id: 'auth'
|
id: 'auth'
|
||||||
with:
|
with:
|
||||||
credentials_json: '${{ secrets.FLUX2_E2E_GOOGLE_CREDENTIALS }}'
|
credentials_json: '${{ secrets.FLUX2_E2E_GOOGLE_CREDENTIALS }}'
|
||||||
token_format: 'access_token'
|
token_format: 'access_token'
|
||||||
- name: Setup gcloud
|
- name: Setup gcloud
|
||||||
uses: google-github-actions/setup-gcloud@825196879a077b7efa50db2e88409f44de4635c2 # v2.0.0
|
uses: google-github-actions/setup-gcloud@77e7a554d41e2ee56fc945c52dfd3f33d12def9a # v2.1.4
|
||||||
- name: Setup QEMU
|
- name: Setup QEMU
|
||||||
uses: docker/setup-qemu-action@68827325e0b33c7199eb31dd4e31fbe9023e06e3 # v3.0.0
|
uses: docker/setup-qemu-action@29109295f81e9208d7d86ff1c6c12d2833863392 # v3.6.0
|
||||||
- name: Setup Docker Buildx
|
- name: Setup Docker Buildx
|
||||||
uses: docker/setup-buildx-action@f95db51fddba0c2d1ec667646a06c2ce06100226 # v3.0.0
|
uses: docker/setup-buildx-action@e468171a9de216ec08956ac3ada2f0791b6bd435 # v3.11.1
|
||||||
- name: Log into us-central1-docker.pkg.dev
|
- name: Log into us-central1-docker.pkg.dev
|
||||||
uses: docker/login-action@343f7c4344506bcbf9b4de18042ae17996df046d # v3.0.0
|
uses: docker/login-action@74a5d142397b4f367a81961eba4e8cd7edddf772 # v3.4.0
|
||||||
with:
|
with:
|
||||||
registry: us-central1-docker.pkg.dev
|
registry: us-central1-docker.pkg.dev
|
||||||
username: oauth2accesstoken
|
username: oauth2accesstoken
|
||||||
|
|
@ -90,3 +92,13 @@ jobs:
|
||||||
echo $GITREPO_SSH_PUB_CONTENTS | base64 -d > ./build/ssh/key.pub
|
echo $GITREPO_SSH_PUB_CONTENTS | base64 -d > ./build/ssh/key.pub
|
||||||
export GITREPO_SSH_PUB_PATH=build/ssh/key.pub
|
export GITREPO_SSH_PUB_PATH=build/ssh/key.pub
|
||||||
make test-gcp
|
make test-gcp
|
||||||
|
- name: Ensure resource cleanup
|
||||||
|
if: ${{ always() }}
|
||||||
|
env:
|
||||||
|
TF_VAR_gcp_project_id: ${{ vars.TF_VAR_gcp_project_id }}
|
||||||
|
TF_VAR_gcp_region: ${{ vars.TF_VAR_gcp_region }}
|
||||||
|
TF_VAR_gcp_zone: ${{ vars.TF_VAR_gcp_zone }}
|
||||||
|
TF_VAR_gcp_email: ${{ secrets.TF_VAR_gcp_email }}
|
||||||
|
TF_VAR_gcp_keyring: ${{ secrets.TF_VAR_gcp_keyring }}
|
||||||
|
TF_VAR_gcp_crypto_key: ${{ secrets.TF_VAR_gcp_crypto_key }}
|
||||||
|
run: source .env && make destroy-gcp
|
||||||
|
|
|
||||||
|
|
@ -13,7 +13,9 @@ permissions:
|
||||||
|
|
||||||
jobs:
|
jobs:
|
||||||
e2e-amd64-kubernetes:
|
e2e-amd64-kubernetes:
|
||||||
runs-on: ubuntu-latest
|
runs-on:
|
||||||
|
group: "Default Larger Runners"
|
||||||
|
labels: ubuntu-latest-16-cores
|
||||||
services:
|
services:
|
||||||
registry:
|
registry:
|
||||||
image: registry:2
|
image: registry:2
|
||||||
|
|
@ -21,30 +23,30 @@ jobs:
|
||||||
- 5000:5000
|
- 5000:5000
|
||||||
steps:
|
steps:
|
||||||
- name: Checkout
|
- name: Checkout
|
||||||
uses: actions/checkout@b4ffde65f46336ab88eb53be808477a3936bae11 # v4.1.1
|
uses: actions/checkout@11bd71901bbe5b1630ceea73d27597364c9af683 # v4.2.2
|
||||||
- name: Setup Go
|
- name: Setup Go
|
||||||
uses: actions/setup-go@0c52d547c9bc32b1aa3301fd7a9cb496313a4491 # v5.0.0
|
uses: actions/setup-go@d35c59abb061a4a6fb18e82ac0862c26744d6ab5 # v5.5.0
|
||||||
with:
|
with:
|
||||||
go-version: 1.20.x
|
go-version: 1.24.x
|
||||||
cache-dependency-path: |
|
cache-dependency-path: |
|
||||||
**/go.sum
|
**/go.sum
|
||||||
**/go.mod
|
**/go.mod
|
||||||
- name: Setup Kubernetes
|
- name: Setup Kubernetes
|
||||||
uses: helm/kind-action@dda0770415bac9fc20092cacbc54aa298604d140 # v1.8.0
|
uses: helm/kind-action@a1b0e391336a6ee6713a0583f8c6240d70863de3 # v1.12.0
|
||||||
with:
|
with:
|
||||||
version: v0.20.0
|
version: v0.24.0
|
||||||
cluster_name: kind
|
cluster_name: kind
|
||||||
|
wait: 5s
|
||||||
config: .github/kind/config.yaml # disable KIND-net
|
config: .github/kind/config.yaml # disable KIND-net
|
||||||
# The versions below should target the newest Kubernetes version
|
# The versions below should target the oldest supported Kubernetes version
|
||||||
# Keep this up-to-date with https://endoflife.date/kubernetes
|
# Keep this up-to-date with https://endoflife.date/kubernetes
|
||||||
node_image: kindest/node:v1.28.0@sha256:9f3ff58f19dcf1a0611d11e8ac989fdb30a28f40f236f59f0bea31fb956ccf5c
|
node_image: ghcr.io/fluxcd/kindest/node:v1.31.5-amd64
|
||||||
kubectl_version: v1.28.0
|
kubectl_version: v1.32.0
|
||||||
- name: Setup Calico for network policy
|
- name: Setup Calico for network policy
|
||||||
run: |
|
run: |
|
||||||
kubectl apply -f https://docs.projectcalico.org/v3.25/manifests/calico.yaml
|
kubectl apply -f https://raw.githubusercontent.com/projectcalico/calico/v3.27.3/manifests/calico.yaml
|
||||||
kubectl -n kube-system set env daemonset/calico-node FELIX_IGNORELOOSERPF=true
|
|
||||||
- name: Setup Kustomize
|
- name: Setup Kustomize
|
||||||
uses: fluxcd/pkg/actions/kustomize@main
|
uses: fluxcd/pkg/actions/kustomize@9e79277372c4746ff091eba1f10aee82974ecdaa # main
|
||||||
- name: Run tests
|
- name: Run tests
|
||||||
run: make test
|
run: make test
|
||||||
- name: Run e2e tests
|
- name: Run e2e tests
|
||||||
|
|
@ -57,44 +59,43 @@ jobs:
|
||||||
exit 1
|
exit 1
|
||||||
fi
|
fi
|
||||||
- name: Build
|
- name: Build
|
||||||
run: |
|
run: make build-dev
|
||||||
go build -o /tmp/flux ./cmd/flux
|
|
||||||
- name: flux check --pre
|
- name: flux check --pre
|
||||||
run: |
|
run: |
|
||||||
/tmp/flux check --pre
|
./bin/flux check --pre
|
||||||
- name: flux install --manifests
|
- name: flux install --manifests
|
||||||
run: |
|
run: |
|
||||||
/tmp/flux install --manifests ./manifests/install/
|
./bin/flux install --manifests ./manifests/install/
|
||||||
- name: flux create secret
|
- name: flux create secret
|
||||||
run: |
|
run: |
|
||||||
/tmp/flux create secret git git-ssh-test \
|
./bin/flux create secret git git-ssh-test \
|
||||||
--url ssh://git@github.com/stefanprodan/podinfo
|
--url ssh://git@github.com/stefanprodan/podinfo
|
||||||
/tmp/flux create secret git git-https-test \
|
./bin/flux create secret git git-https-test \
|
||||||
--url https://github.com/stefanprodan/podinfo \
|
--url https://github.com/stefanprodan/podinfo \
|
||||||
--username=test --password=test
|
--username=test --password=test
|
||||||
/tmp/flux create secret helm helm-test \
|
./bin/flux create secret helm helm-test \
|
||||||
--username=test --password=test
|
--username=test --password=test
|
||||||
- name: flux create source git
|
- name: flux create source git
|
||||||
run: |
|
run: |
|
||||||
/tmp/flux create source git podinfo \
|
./bin/flux create source git podinfo \
|
||||||
--url https://github.com/stefanprodan/podinfo \
|
--url https://github.com/stefanprodan/podinfo \
|
||||||
--tag-semver=">=6.3.5"
|
--tag-semver=">=6.3.5"
|
||||||
- name: flux create source git export apply
|
- name: flux create source git export apply
|
||||||
run: |
|
run: |
|
||||||
/tmp/flux create source git podinfo-export \
|
./bin/flux create source git podinfo-export \
|
||||||
--url https://github.com/stefanprodan/podinfo \
|
--url https://github.com/stefanprodan/podinfo \
|
||||||
--tag-semver=">=6.3.5" \
|
--tag-semver=">=6.3.5" \
|
||||||
--export | kubectl apply -f -
|
--export | kubectl apply -f -
|
||||||
/tmp/flux delete source git podinfo-export --silent
|
./bin/flux delete source git podinfo-export --silent
|
||||||
- name: flux get sources git
|
- name: flux get sources git
|
||||||
run: |
|
run: |
|
||||||
/tmp/flux get sources git
|
./bin/flux get sources git
|
||||||
- name: flux get sources git --all-namespaces
|
- name: flux get sources git --all-namespaces
|
||||||
run: |
|
run: |
|
||||||
/tmp/flux get sources git --all-namespaces
|
./bin/flux get sources git --all-namespaces
|
||||||
- name: flux create kustomization
|
- name: flux create kustomization
|
||||||
run: |
|
run: |
|
||||||
/tmp/flux create kustomization podinfo \
|
./bin/flux create kustomization podinfo \
|
||||||
--source=podinfo \
|
--source=podinfo \
|
||||||
--path="./deploy/overlays/dev" \
|
--path="./deploy/overlays/dev" \
|
||||||
--prune=true \
|
--prune=true \
|
||||||
|
|
@ -104,89 +105,89 @@ jobs:
|
||||||
--health-check-timeout=3m
|
--health-check-timeout=3m
|
||||||
- name: flux trace
|
- name: flux trace
|
||||||
run: |
|
run: |
|
||||||
/tmp/flux trace frontend \
|
./bin/flux trace frontend \
|
||||||
--kind=deployment \
|
--kind=deployment \
|
||||||
--api-version=apps/v1 \
|
--api-version=apps/v1 \
|
||||||
--namespace=dev
|
--namespace=dev
|
||||||
- name: flux reconcile kustomization --with-source
|
- name: flux reconcile kustomization --with-source
|
||||||
run: |
|
run: |
|
||||||
/tmp/flux reconcile kustomization podinfo --with-source
|
./bin/flux reconcile kustomization podinfo --with-source
|
||||||
- name: flux get kustomizations
|
- name: flux get kustomizations
|
||||||
run: |
|
run: |
|
||||||
/tmp/flux get kustomizations
|
./bin/flux get kustomizations
|
||||||
- name: flux get kustomizations --all-namespaces
|
- name: flux get kustomizations --all-namespaces
|
||||||
run: |
|
run: |
|
||||||
/tmp/flux get kustomizations --all-namespaces
|
./bin/flux get kustomizations --all-namespaces
|
||||||
- name: flux suspend kustomization
|
- name: flux suspend kustomization
|
||||||
run: |
|
run: |
|
||||||
/tmp/flux suspend kustomization podinfo
|
./bin/flux suspend kustomization podinfo
|
||||||
- name: flux resume kustomization
|
- name: flux resume kustomization
|
||||||
run: |
|
run: |
|
||||||
/tmp/flux resume kustomization podinfo
|
./bin/flux resume kustomization podinfo
|
||||||
- name: flux export
|
- name: flux export
|
||||||
run: |
|
run: |
|
||||||
/tmp/flux export source git --all
|
./bin/flux export source git --all
|
||||||
/tmp/flux export kustomization --all
|
./bin/flux export kustomization --all
|
||||||
- name: flux delete kustomization
|
- name: flux delete kustomization
|
||||||
run: |
|
run: |
|
||||||
/tmp/flux delete kustomization podinfo --silent
|
./bin/flux delete kustomization podinfo --silent
|
||||||
- name: flux create source helm
|
- name: flux create source helm
|
||||||
run: |
|
run: |
|
||||||
/tmp/flux create source helm podinfo \
|
./bin/flux create source helm podinfo \
|
||||||
--url https://stefanprodan.github.io/podinfo
|
--url https://stefanprodan.github.io/podinfo
|
||||||
- name: flux create helmrelease --source=HelmRepository/podinfo
|
- name: flux create helmrelease --source=HelmRepository/podinfo
|
||||||
run: |
|
run: |
|
||||||
/tmp/flux create hr podinfo-helm \
|
./bin/flux create hr podinfo-helm \
|
||||||
--target-namespace=default \
|
--target-namespace=default \
|
||||||
--source=HelmRepository/podinfo.flux-system \
|
--source=HelmRepository/podinfo.flux-system \
|
||||||
--chart=podinfo \
|
--chart=podinfo \
|
||||||
--chart-version=">6.0.0 <7.0.0"
|
--chart-version=">6.0.0 <7.0.0"
|
||||||
- name: flux create helmrelease --source=GitRepository/podinfo
|
- name: flux create helmrelease --source=GitRepository/podinfo
|
||||||
run: |
|
run: |
|
||||||
/tmp/flux create hr podinfo-git \
|
./bin/flux create hr podinfo-git \
|
||||||
--target-namespace=default \
|
--target-namespace=default \
|
||||||
--source=GitRepository/podinfo \
|
--source=GitRepository/podinfo \
|
||||||
--chart=./charts/podinfo
|
--chart=./charts/podinfo
|
||||||
- name: flux reconcile helmrelease --with-source
|
- name: flux reconcile helmrelease --with-source
|
||||||
run: |
|
run: |
|
||||||
/tmp/flux reconcile helmrelease podinfo-git --with-source
|
./bin/flux reconcile helmrelease podinfo-git --with-source
|
||||||
- name: flux get helmreleases
|
- name: flux get helmreleases
|
||||||
run: |
|
run: |
|
||||||
/tmp/flux get helmreleases
|
./bin/flux get helmreleases
|
||||||
- name: flux get helmreleases --all-namespaces
|
- name: flux get helmreleases --all-namespaces
|
||||||
run: |
|
run: |
|
||||||
/tmp/flux get helmreleases --all-namespaces
|
./bin/flux get helmreleases --all-namespaces
|
||||||
- name: flux export helmrelease
|
- name: flux export helmrelease
|
||||||
run: |
|
run: |
|
||||||
/tmp/flux export hr --all
|
./bin/flux export hr --all
|
||||||
- name: flux delete helmrelease podinfo-helm
|
- name: flux delete helmrelease podinfo-helm
|
||||||
run: |
|
run: |
|
||||||
/tmp/flux delete hr podinfo-helm --silent
|
./bin/flux delete hr podinfo-helm --silent
|
||||||
- name: flux delete helmrelease podinfo-git
|
- name: flux delete helmrelease podinfo-git
|
||||||
run: |
|
run: |
|
||||||
/tmp/flux delete hr podinfo-git --silent
|
./bin/flux delete hr podinfo-git --silent
|
||||||
- name: flux delete source helm
|
- name: flux delete source helm
|
||||||
run: |
|
run: |
|
||||||
/tmp/flux delete source helm podinfo --silent
|
./bin/flux delete source helm podinfo --silent
|
||||||
- name: flux delete source git
|
- name: flux delete source git
|
||||||
run: |
|
run: |
|
||||||
/tmp/flux delete source git podinfo --silent
|
./bin/flux delete source git podinfo --silent
|
||||||
- name: flux oci artifacts
|
- name: flux oci artifacts
|
||||||
run: |
|
run: |
|
||||||
/tmp/flux push artifact oci://localhost:5000/fluxcd/flux:${{ github.sha }} \
|
./bin/flux push artifact oci://localhost:5000/fluxcd/flux:${{ github.sha }} \
|
||||||
--path="./manifests" \
|
--path="./manifests" \
|
||||||
--source="${{ github.repositoryUrl }}" \
|
--source="${{ github.repositoryUrl }}" \
|
||||||
--revision="${{ github.ref }}@sha1:${{ github.sha }}"
|
--revision="${{ github.ref }}@sha1:${{ github.sha }}"
|
||||||
/tmp/flux tag artifact oci://localhost:5000/fluxcd/flux:${{ github.sha }} \
|
./bin/flux tag artifact oci://localhost:5000/fluxcd/flux:${{ github.sha }} \
|
||||||
--tag latest
|
--tag latest
|
||||||
/tmp/flux list artifacts oci://localhost:5000/fluxcd/flux
|
./bin/flux list artifacts oci://localhost:5000/fluxcd/flux
|
||||||
- name: flux oci repositories
|
- name: flux oci repositories
|
||||||
run: |
|
run: |
|
||||||
/tmp/flux create source oci podinfo-oci \
|
./bin/flux create source oci podinfo-oci \
|
||||||
--url oci://ghcr.io/stefanprodan/manifests/podinfo \
|
--url oci://ghcr.io/stefanprodan/manifests/podinfo \
|
||||||
--tag-semver 6.3.x \
|
--tag-semver 6.3.x \
|
||||||
--interval 10m
|
--interval 10m
|
||||||
/tmp/flux create kustomization podinfo-oci \
|
./bin/flux create kustomization podinfo-oci \
|
||||||
--source=OCIRepository/podinfo-oci \
|
--source=OCIRepository/podinfo-oci \
|
||||||
--path="./" \
|
--path="./" \
|
||||||
--prune=true \
|
--prune=true \
|
||||||
|
|
@ -194,31 +195,31 @@ jobs:
|
||||||
--target-namespace=default \
|
--target-namespace=default \
|
||||||
--wait=true \
|
--wait=true \
|
||||||
--health-check-timeout=3m
|
--health-check-timeout=3m
|
||||||
/tmp/flux reconcile source oci podinfo-oci
|
./bin/flux reconcile source oci podinfo-oci
|
||||||
/tmp/flux suspend source oci podinfo-oci
|
./bin/flux suspend source oci podinfo-oci
|
||||||
/tmp/flux get sources oci
|
./bin/flux get sources oci
|
||||||
/tmp/flux resume source oci podinfo-oci
|
./bin/flux resume source oci podinfo-oci
|
||||||
/tmp/flux export source oci podinfo-oci
|
./bin/flux export source oci podinfo-oci
|
||||||
/tmp/flux delete ks podinfo-oci --silent
|
./bin/flux delete ks podinfo-oci --silent
|
||||||
/tmp/flux delete source oci podinfo-oci --silent
|
./bin/flux delete source oci podinfo-oci --silent
|
||||||
- name: flux create tenant
|
- name: flux create tenant
|
||||||
run: |
|
run: |
|
||||||
/tmp/flux create tenant dev-team --with-namespace=apps
|
./bin/flux create tenant dev-team --with-namespace=apps
|
||||||
/tmp/flux -n apps create source helm podinfo \
|
./bin/flux -n apps create source helm podinfo \
|
||||||
--url https://stefanprodan.github.io/podinfo
|
--url https://stefanprodan.github.io/podinfo
|
||||||
/tmp/flux -n apps create hr podinfo-helm \
|
./bin/flux -n apps create hr podinfo-helm \
|
||||||
--source=HelmRepository/podinfo \
|
--source=HelmRepository/podinfo \
|
||||||
--chart=podinfo \
|
--chart=podinfo \
|
||||||
--chart-version="6.3.x" \
|
--chart-version="6.3.x" \
|
||||||
--service-account=dev-team
|
--service-account=dev-team
|
||||||
- name: flux2-kustomize-helm-example
|
- name: flux2-kustomize-helm-example
|
||||||
run: |
|
run: |
|
||||||
/tmp/flux create source git flux-system \
|
./bin/flux create source git flux-system \
|
||||||
--url=https://github.com/fluxcd/flux2-kustomize-helm-example \
|
--url=https://github.com/fluxcd/flux2-kustomize-helm-example \
|
||||||
--branch=main \
|
--branch=main \
|
||||||
--ignore-paths="./clusters/**/flux-system/" \
|
--ignore-paths="./clusters/**/flux-system/" \
|
||||||
--recurse-submodules
|
--recurse-submodules
|
||||||
/tmp/flux create kustomization flux-system \
|
./bin/flux create kustomization flux-system \
|
||||||
--source=flux-system \
|
--source=flux-system \
|
||||||
--path=./clusters/staging
|
--path=./clusters/staging
|
||||||
kubectl -n flux-system wait kustomization/infra-controllers --for=condition=ready --timeout=5m
|
kubectl -n flux-system wait kustomization/infra-controllers --for=condition=ready --timeout=5m
|
||||||
|
|
@ -226,17 +227,27 @@ jobs:
|
||||||
kubectl -n podinfo wait helmrelease/podinfo --for=condition=ready --timeout=5m
|
kubectl -n podinfo wait helmrelease/podinfo --for=condition=ready --timeout=5m
|
||||||
- name: flux tree
|
- name: flux tree
|
||||||
run: |
|
run: |
|
||||||
/tmp/flux tree kustomization flux-system | grep Service/podinfo
|
./bin/flux tree kustomization flux-system | grep Service/podinfo
|
||||||
|
- name: flux events
|
||||||
|
run: |
|
||||||
|
./bin/flux -n flux-system events --for Kustomization/apps | grep 'HelmRelease/podinfo'
|
||||||
|
./bin/flux -n podinfo events --for HelmRelease/podinfo | grep 'podinfo.v1'
|
||||||
|
- name: flux stats
|
||||||
|
run: |
|
||||||
|
./bin/flux stats -A
|
||||||
- name: flux check
|
- name: flux check
|
||||||
run: |
|
run: |
|
||||||
/tmp/flux check
|
./bin/flux check
|
||||||
|
- name: flux version
|
||||||
|
run: |
|
||||||
|
./bin/flux version
|
||||||
- name: flux uninstall
|
- name: flux uninstall
|
||||||
run: |
|
run: |
|
||||||
/tmp/flux uninstall --silent
|
./bin/flux uninstall --silent
|
||||||
- name: Debug failure
|
- name: Debug failure
|
||||||
if: failure()
|
if: failure()
|
||||||
run: |
|
run: |
|
||||||
kubectl version --client --short
|
kubectl version --client
|
||||||
kubectl -n flux-system get all
|
kubectl -n flux-system get all
|
||||||
kubectl -n flux-system describe pods
|
kubectl -n flux-system describe pods
|
||||||
kubectl -n flux-system get kustomizations -oyaml
|
kubectl -n flux-system get kustomizations -oyaml
|
||||||
|
|
|
||||||
|
|
@ -19,21 +19,21 @@ jobs:
|
||||||
actions: read
|
actions: read
|
||||||
contents: read
|
contents: read
|
||||||
steps:
|
steps:
|
||||||
- uses: actions/checkout@b4ffde65f46336ab88eb53be808477a3936bae11 # v4.1.1
|
- uses: actions/checkout@11bd71901bbe5b1630ceea73d27597364c9af683 # v4.2.2
|
||||||
- name: Run analysis
|
- name: Run analysis
|
||||||
uses: ossf/scorecard-action@0864cf19026789058feabb7e87baa5f140aac736 # v2.3.1
|
uses: ossf/scorecard-action@05b42c624433fc40578a4040d5cf5e36ddca8cde # v2.4.2
|
||||||
with:
|
with:
|
||||||
results_file: results.sarif
|
results_file: results.sarif
|
||||||
results_format: sarif
|
results_format: sarif
|
||||||
repo_token: ${{ secrets.GITHUB_TOKEN }}
|
repo_token: ${{ secrets.GITHUB_TOKEN }}
|
||||||
publish_results: true
|
publish_results: true
|
||||||
- name: Upload artifact
|
- name: Upload artifact
|
||||||
uses: actions/upload-artifact@a8a3f3ad30e3422c9c7b888a15615d19a852ae32 # v3.1.3
|
uses: actions/upload-artifact@ea165f8d65b6e75b540449e92b4886f43607fa02 # v4.6.2
|
||||||
with:
|
with:
|
||||||
name: SARIF file
|
name: SARIF file
|
||||||
path: results.sarif
|
path: results.sarif
|
||||||
retention-days: 5
|
retention-days: 5
|
||||||
- name: Upload SARIF results
|
- name: Upload SARIF results
|
||||||
uses: github/codeql-action/upload-sarif@cdcdbb579706841c47f7063dda365e292e5cad7a # v2.13.4
|
uses: github/codeql-action/upload-sarif@181d5eefc20863364f96762470ba6f862bdef56b # v3.29.2
|
||||||
with:
|
with:
|
||||||
sarif_file: results.sarif
|
sarif_file: results.sarif
|
||||||
|
|
|
||||||
|
|
@ -2,7 +2,7 @@ name: release
|
||||||
|
|
||||||
on:
|
on:
|
||||||
push:
|
push:
|
||||||
tags: [ 'v*' ]
|
tags: ["v*"]
|
||||||
|
|
||||||
permissions:
|
permissions:
|
||||||
contents: read
|
contents: read
|
||||||
|
|
@ -20,33 +20,33 @@ jobs:
|
||||||
packages: write # needed for ghcr access
|
packages: write # needed for ghcr access
|
||||||
steps:
|
steps:
|
||||||
- name: Checkout
|
- name: Checkout
|
||||||
uses: actions/checkout@b4ffde65f46336ab88eb53be808477a3936bae11 # v4.1.1
|
uses: actions/checkout@11bd71901bbe5b1630ceea73d27597364c9af683 # v4.2.2
|
||||||
- name: Unshallow
|
- name: Unshallow
|
||||||
run: git fetch --prune --unshallow
|
run: git fetch --prune --unshallow
|
||||||
- name: Setup Go
|
- name: Setup Go
|
||||||
uses: actions/setup-go@0c52d547c9bc32b1aa3301fd7a9cb496313a4491 # v5.0.0
|
uses: actions/setup-go@d35c59abb061a4a6fb18e82ac0862c26744d6ab5 # v5.5.0
|
||||||
with:
|
with:
|
||||||
go-version: 1.20.x
|
go-version: 1.24.x
|
||||||
cache: false
|
cache: false
|
||||||
- name: Setup QEMU
|
- name: Setup QEMU
|
||||||
uses: docker/setup-qemu-action@68827325e0b33c7199eb31dd4e31fbe9023e06e3 # v3.0.0
|
uses: docker/setup-qemu-action@29109295f81e9208d7d86ff1c6c12d2833863392 # v3.6.0
|
||||||
- name: Setup Docker Buildx
|
- name: Setup Docker Buildx
|
||||||
id: buildx
|
id: buildx
|
||||||
uses: docker/setup-buildx-action@f95db51fddba0c2d1ec667646a06c2ce06100226 # v3.0.0
|
uses: docker/setup-buildx-action@e468171a9de216ec08956ac3ada2f0791b6bd435 # v3.11.1
|
||||||
- name: Setup Syft
|
- name: Setup Syft
|
||||||
uses: anchore/sbom-action/download-syft@5ecf649a417b8ae17dc8383dc32d46c03f2312df # v0.15.1
|
uses: anchore/sbom-action/download-syft@cee1b8e05ae5b2593a75e197229729eabaa9f8ec # v0.20.2
|
||||||
- name: Setup Cosign
|
- name: Setup Cosign
|
||||||
uses: sigstore/cosign-installer@1fc5bd396d372bee37d608f955b336615edf79c8 # v3.2.0
|
uses: sigstore/cosign-installer@398d4b0eeef1380460a10c8013a76f728fb906ac # v3.9.1
|
||||||
- name: Setup Kustomize
|
- name: Setup Kustomize
|
||||||
uses: fluxcd/pkg/actions/kustomize@main
|
uses: fluxcd/pkg/actions/kustomize@9e79277372c4746ff091eba1f10aee82974ecdaa # main
|
||||||
- name: Login to GitHub Container Registry
|
- name: Login to GitHub Container Registry
|
||||||
uses: docker/login-action@343f7c4344506bcbf9b4de18042ae17996df046d # v3.0.0
|
uses: docker/login-action@74a5d142397b4f367a81961eba4e8cd7edddf772 # v3.4.0
|
||||||
with:
|
with:
|
||||||
registry: ghcr.io
|
registry: ghcr.io
|
||||||
username: fluxcdbot
|
username: fluxcdbot
|
||||||
password: ${{ secrets.GHCR_TOKEN }}
|
password: ${{ secrets.GITHUB_TOKEN }}
|
||||||
- name: Login to Docker Hub
|
- name: Login to Docker Hub
|
||||||
uses: docker/login-action@343f7c4344506bcbf9b4de18042ae17996df046d # v3.0.0
|
uses: docker/login-action@74a5d142397b4f367a81961eba4e8cd7edddf772 # v3.4.0
|
||||||
with:
|
with:
|
||||||
username: fluxcdbot
|
username: fluxcdbot
|
||||||
password: ${{ secrets.DOCKER_FLUXCD_PASSWORD }}
|
password: ${{ secrets.DOCKER_FLUXCD_PASSWORD }}
|
||||||
|
|
@ -59,30 +59,19 @@ jobs:
|
||||||
run: |
|
run: |
|
||||||
kustomize build manifests/crds > all-crds.yaml
|
kustomize build manifests/crds > all-crds.yaml
|
||||||
- name: Generate OpenAPI JSON schemas from CRDs
|
- name: Generate OpenAPI JSON schemas from CRDs
|
||||||
uses: fluxcd/pkg/actions/crdjsonschema@main
|
uses: fluxcd/pkg/actions/crdjsonschema@9e79277372c4746ff091eba1f10aee82974ecdaa # main
|
||||||
with:
|
with:
|
||||||
crd: all-crds.yaml
|
crd: all-crds.yaml
|
||||||
output: schemas
|
output: schemas
|
||||||
- name: Archive the OpenAPI JSON schemas
|
- name: Archive the OpenAPI JSON schemas
|
||||||
run: |
|
run: |
|
||||||
tar -czvf ./output/crd-schemas.tar.gz -C schemas .
|
tar -czvf ./output/crd-schemas.tar.gz -C schemas .
|
||||||
- name: Download release notes utility
|
|
||||||
env:
|
|
||||||
GH_REL_URL: https://github.com/buchanae/github-release-notes/releases/download/0.2.0/github-release-notes-linux-amd64-0.2.0.tar.gz
|
|
||||||
run: cd /tmp && curl -sSL ${GH_REL_URL} | tar xz && sudo mv github-release-notes /usr/local/bin/
|
|
||||||
- name: Generate release notes
|
|
||||||
run: |
|
|
||||||
NOTES="./output/notes.md"
|
|
||||||
echo '## CLI Changelog' > ${NOTES}
|
|
||||||
github-release-notes -org fluxcd -repo flux2 -since-latest-release -include-author >> ${NOTES}
|
|
||||||
env:
|
|
||||||
GITHUB_TOKEN: ${{ secrets.GITHUB_TOKEN }}
|
|
||||||
- name: Run GoReleaser
|
- name: Run GoReleaser
|
||||||
id: run-goreleaser
|
id: run-goreleaser
|
||||||
uses: goreleaser/goreleaser-action@7ec5c2b0c6cdda6e8bbb49444bc797dd33d74dd8 # v5.0.0
|
uses: goreleaser/goreleaser-action@9c156ee8a17a598857849441385a2041ef570552 # v6.3.0
|
||||||
with:
|
with:
|
||||||
version: latest
|
version: latest
|
||||||
args: release --release-notes=output/notes.md --skip-validate
|
args: release --skip=validate
|
||||||
env:
|
env:
|
||||||
GITHUB_TOKEN: ${{ secrets.GITHUB_TOKEN }}
|
GITHUB_TOKEN: ${{ secrets.GITHUB_TOKEN }}
|
||||||
HOMEBREW_TAP_GITHUB_TOKEN: ${{ secrets.BOT_GITHUB_TOKEN }}
|
HOMEBREW_TAP_GITHUB_TOKEN: ${{ secrets.BOT_GITHUB_TOKEN }}
|
||||||
|
|
@ -93,13 +82,13 @@ jobs:
|
||||||
ARTIFACTS: "${{ steps.run-goreleaser.outputs.artifacts }}"
|
ARTIFACTS: "${{ steps.run-goreleaser.outputs.artifacts }}"
|
||||||
run: |
|
run: |
|
||||||
set -euo pipefail
|
set -euo pipefail
|
||||||
|
|
||||||
hashes=$(echo -E $ARTIFACTS | jq --raw-output '.[] | {name, "digest": (.extra.Digest // .extra.Checksum)} | select(.digest) | {digest} + {name} | join(" ") | sub("^sha256:";"")' | base64 -w0)
|
hashes=$(echo -E $ARTIFACTS | jq --raw-output '.[] | {name, "digest": (.extra.Digest // .extra.Checksum)} | select(.digest) | {digest} + {name} | join(" ") | sub("^sha256:";"")' | base64 -w0)
|
||||||
echo "hashes=$hashes" >> $GITHUB_OUTPUT
|
echo "hashes=$hashes" >> $GITHUB_OUTPUT
|
||||||
|
|
||||||
image_url=fluxcd/flux-cli:$GITHUB_REF_NAME
|
image_url=fluxcd/flux-cli:$GITHUB_REF_NAME
|
||||||
echo "image_url=$image_url" >> $GITHUB_OUTPUT
|
echo "image_url=$image_url" >> $GITHUB_OUTPUT
|
||||||
|
|
||||||
image_digest=$(docker buildx imagetools inspect ${image_url} --format '{{json .}}' | jq -r .manifest.digest)
|
image_digest=$(docker buildx imagetools inspect ${image_url} --format '{{json .}}' | jq -r .manifest.digest)
|
||||||
echo "image_digest=$image_digest" >> $GITHUB_OUTPUT
|
echo "image_digest=$image_digest" >> $GITHUB_OUTPUT
|
||||||
|
|
||||||
|
|
@ -110,9 +99,9 @@ jobs:
|
||||||
id-token: write
|
id-token: write
|
||||||
packages: write
|
packages: write
|
||||||
steps:
|
steps:
|
||||||
- uses: actions/checkout@b4ffde65f46336ab88eb53be808477a3936bae11 # v4.1.1
|
- uses: actions/checkout@11bd71901bbe5b1630ceea73d27597364c9af683 # v4.2.2
|
||||||
- name: Setup Kustomize
|
- name: Setup Kustomize
|
||||||
uses: fluxcd/pkg/actions/kustomize@main
|
uses: fluxcd/pkg/actions/kustomize@9e79277372c4746ff091eba1f10aee82974ecdaa # main
|
||||||
- name: Setup Flux CLI
|
- name: Setup Flux CLI
|
||||||
uses: ./action/
|
uses: ./action/
|
||||||
- name: Prepare
|
- name: Prepare
|
||||||
|
|
@ -121,13 +110,13 @@ jobs:
|
||||||
VERSION=$(flux version --client | awk '{ print $NF }')
|
VERSION=$(flux version --client | awk '{ print $NF }')
|
||||||
echo "version=${VERSION}" >> $GITHUB_OUTPUT
|
echo "version=${VERSION}" >> $GITHUB_OUTPUT
|
||||||
- name: Login to GHCR
|
- name: Login to GHCR
|
||||||
uses: docker/login-action@343f7c4344506bcbf9b4de18042ae17996df046d # v3.0.0
|
uses: docker/login-action@74a5d142397b4f367a81961eba4e8cd7edddf772 # v3.4.0
|
||||||
with:
|
with:
|
||||||
registry: ghcr.io
|
registry: ghcr.io
|
||||||
username: fluxcdbot
|
username: fluxcdbot
|
||||||
password: ${{ secrets.GHCR_TOKEN }}
|
password: ${{ secrets.GITHUB_TOKEN }}
|
||||||
- name: Login to DockerHub
|
- name: Login to DockerHub
|
||||||
uses: docker/login-action@343f7c4344506bcbf9b4de18042ae17996df046d # v3.0.0
|
uses: docker/login-action@74a5d142397b4f367a81961eba4e8cd7edddf772 # v3.4.0
|
||||||
with:
|
with:
|
||||||
username: fluxcdbot
|
username: fluxcdbot
|
||||||
password: ${{ secrets.DOCKER_FLUXCD_PASSWORD }}
|
password: ${{ secrets.DOCKER_FLUXCD_PASSWORD }}
|
||||||
|
|
@ -137,7 +126,7 @@ jobs:
|
||||||
flux install --registry=ghcr.io/fluxcd \
|
flux install --registry=ghcr.io/fluxcd \
|
||||||
--components-extra=image-reflector-controller,image-automation-controller \
|
--components-extra=image-reflector-controller,image-automation-controller \
|
||||||
--export > ./ghcr.io/flux-system/gotk-components.yaml
|
--export > ./ghcr.io/flux-system/gotk-components.yaml
|
||||||
|
|
||||||
cd ./ghcr.io && flux push artifact \
|
cd ./ghcr.io && flux push artifact \
|
||||||
oci://ghcr.io/fluxcd/flux-manifests:${{ steps.prep.outputs.version }} \
|
oci://ghcr.io/fluxcd/flux-manifests:${{ steps.prep.outputs.version }} \
|
||||||
--path="./flux-system" \
|
--path="./flux-system" \
|
||||||
|
|
@ -149,13 +138,13 @@ jobs:
|
||||||
flux install --registry=docker.io/fluxcd \
|
flux install --registry=docker.io/fluxcd \
|
||||||
--components-extra=image-reflector-controller,image-automation-controller \
|
--components-extra=image-reflector-controller,image-automation-controller \
|
||||||
--export > ./docker.io/flux-system/gotk-components.yaml
|
--export > ./docker.io/flux-system/gotk-components.yaml
|
||||||
|
|
||||||
cd ./docker.io && flux push artifact \
|
cd ./docker.io && flux push artifact \
|
||||||
oci://docker.io/fluxcd/flux-manifests:${{ steps.prep.outputs.version }} \
|
oci://docker.io/fluxcd/flux-manifests:${{ steps.prep.outputs.version }} \
|
||||||
--path="./flux-system" \
|
--path="./flux-system" \
|
||||||
--source=${{ github.repositoryUrl }} \
|
--source=${{ github.repositoryUrl }} \
|
||||||
--revision="${{ github.ref_name }}@sha1:${{ github.sha }}"
|
--revision="${{ github.ref_name }}@sha1:${{ github.sha }}"
|
||||||
- uses: sigstore/cosign-installer@1fc5bd396d372bee37d608f955b336615edf79c8 # v3.2.0
|
- uses: sigstore/cosign-installer@398d4b0eeef1380460a10c8013a76f728fb906ac # v3.9.1
|
||||||
- name: Sign manifests
|
- name: Sign manifests
|
||||||
env:
|
env:
|
||||||
COSIGN_EXPERIMENTAL: 1
|
COSIGN_EXPERIMENTAL: 1
|
||||||
|
|
@ -176,7 +165,7 @@ jobs:
|
||||||
actions: read # for detecting the Github Actions environment.
|
actions: read # for detecting the Github Actions environment.
|
||||||
id-token: write # for creating OIDC tokens for signing.
|
id-token: write # for creating OIDC tokens for signing.
|
||||||
contents: write # for uploading attestations to GitHub releases.
|
contents: write # for uploading attestations to GitHub releases.
|
||||||
uses: slsa-framework/slsa-github-generator/.github/workflows/generator_generic_slsa3.yml@v1.9.0
|
uses: slsa-framework/slsa-github-generator/.github/workflows/generator_generic_slsa3.yml@v2.1.0
|
||||||
with:
|
with:
|
||||||
provenance-name: "provenance.intoto.jsonl"
|
provenance-name: "provenance.intoto.jsonl"
|
||||||
base64-subjects: "${{ needs.release-flux-cli.outputs.hashes }}"
|
base64-subjects: "${{ needs.release-flux-cli.outputs.hashes }}"
|
||||||
|
|
@ -188,7 +177,7 @@ jobs:
|
||||||
actions: read # for detecting the Github Actions environment.
|
actions: read # for detecting the Github Actions environment.
|
||||||
id-token: write # for creating OIDC tokens for signing.
|
id-token: write # for creating OIDC tokens for signing.
|
||||||
packages: write # for uploading attestations.
|
packages: write # for uploading attestations.
|
||||||
uses: slsa-framework/slsa-github-generator/.github/workflows/generator_container_slsa3.yml@v1.9.0
|
uses: slsa-framework/slsa-github-generator/.github/workflows/generator_container_slsa3.yml@v2.1.0
|
||||||
with:
|
with:
|
||||||
image: ${{ needs.release-flux-cli.outputs.image_url }}
|
image: ${{ needs.release-flux-cli.outputs.image_url }}
|
||||||
digest: ${{ needs.release-flux-cli.outputs.image_digest }}
|
digest: ${{ needs.release-flux-cli.outputs.image_digest }}
|
||||||
|
|
@ -202,10 +191,10 @@ jobs:
|
||||||
actions: read # for detecting the Github Actions environment.
|
actions: read # for detecting the Github Actions environment.
|
||||||
id-token: write # for creating OIDC tokens for signing.
|
id-token: write # for creating OIDC tokens for signing.
|
||||||
packages: write # for uploading attestations.
|
packages: write # for uploading attestations.
|
||||||
uses: slsa-framework/slsa-github-generator/.github/workflows/generator_container_slsa3.yml@v1.9.0
|
uses: slsa-framework/slsa-github-generator/.github/workflows/generator_container_slsa3.yml@v2.1.0
|
||||||
with:
|
with:
|
||||||
image: ghcr.io/${{ needs.release-flux-cli.outputs.image_url }}
|
image: ghcr.io/${{ needs.release-flux-cli.outputs.image_url }}
|
||||||
digest: ${{ needs.release-flux-cli.outputs.image_digest }}
|
digest: ${{ needs.release-flux-cli.outputs.image_digest }}
|
||||||
registry-username: fluxcdbot
|
registry-username: fluxcdbot
|
||||||
secrets:
|
secrets:
|
||||||
registry-password: ${{ secrets.GHCR_TOKEN }}
|
registry-password: ${{ secrets.GITHUB_TOKEN }}
|
||||||
|
|
|
||||||
|
|
@ -17,46 +17,14 @@ jobs:
|
||||||
runs-on: ubuntu-latest
|
runs-on: ubuntu-latest
|
||||||
if: github.actor != 'dependabot[bot]'
|
if: github.actor != 'dependabot[bot]'
|
||||||
steps:
|
steps:
|
||||||
- uses: actions/checkout@b4ffde65f46336ab88eb53be808477a3936bae11 # v4.1.1
|
- uses: actions/checkout@11bd71901bbe5b1630ceea73d27597364c9af683 # v4.2.2
|
||||||
- name: Run FOSSA scan and upload build data
|
- name: Run FOSSA scan and upload build data
|
||||||
uses: fossa-contrib/fossa-action@cdc5065bcdee31a32e47d4585df72d66e8e941c2 # v3.0.0
|
uses: fossa-contrib/fossa-action@3d2ef181b1820d6dcd1972f86a767d18167fa19b # v3.0.1
|
||||||
with:
|
with:
|
||||||
# FOSSA Push-Only API Token
|
# FOSSA Push-Only API Token
|
||||||
fossa-api-key: 5ee8bf422db1471e0bcf2bcb289185de
|
fossa-api-key: 5ee8bf422db1471e0bcf2bcb289185de
|
||||||
github-token: ${{ github.token }}
|
github-token: ${{ github.token }}
|
||||||
|
|
||||||
scan-snyk:
|
|
||||||
runs-on: ubuntu-latest
|
|
||||||
permissions:
|
|
||||||
security-events: write
|
|
||||||
if: (github.event_name != 'pull_request' || github.event.pull_request.head.repo.full_name == github.repository) && github.actor != 'dependabot[bot]'
|
|
||||||
steps:
|
|
||||||
- uses: actions/checkout@b4ffde65f46336ab88eb53be808477a3936bae11 # v4.1.1
|
|
||||||
- name: Setup Kustomize
|
|
||||||
uses: fluxcd/pkg/actions/kustomize@main
|
|
||||||
- name: Setup Go
|
|
||||||
uses: actions/setup-go@0c52d547c9bc32b1aa3301fd7a9cb496313a4491 # v5.0.0
|
|
||||||
with:
|
|
||||||
go-version: 1.20.x
|
|
||||||
cache-dependency-path: |
|
|
||||||
**/go.sum
|
|
||||||
**/go.mod
|
|
||||||
- name: Download modules and build manifests
|
|
||||||
run: |
|
|
||||||
make tidy
|
|
||||||
make cmd/flux/.manifests.done
|
|
||||||
- uses: snyk/actions/setup@b98d498629f1c368650224d6d212bf7dfa89e4bf
|
|
||||||
- name: Run Snyk to check for vulnerabilities
|
|
||||||
continue-on-error: true
|
|
||||||
run: |
|
|
||||||
snyk test --sarif-file-output=snyk.sarif
|
|
||||||
env:
|
|
||||||
SNYK_TOKEN: ${{ secrets.SNYK_TOKEN }}
|
|
||||||
- name: Upload result to GitHub Code Scanning
|
|
||||||
uses: github/codeql-action/upload-sarif@cdcdbb579706841c47f7063dda365e292e5cad7a # v2.13.4
|
|
||||||
with:
|
|
||||||
sarif_file: snyk.sarif
|
|
||||||
|
|
||||||
scan-codeql:
|
scan-codeql:
|
||||||
runs-on: ubuntu-latest
|
runs-on: ubuntu-latest
|
||||||
permissions:
|
permissions:
|
||||||
|
|
@ -64,22 +32,22 @@ jobs:
|
||||||
if: github.actor != 'dependabot[bot]'
|
if: github.actor != 'dependabot[bot]'
|
||||||
steps:
|
steps:
|
||||||
- name: Checkout repository
|
- name: Checkout repository
|
||||||
uses: actions/checkout@b4ffde65f46336ab88eb53be808477a3936bae11 # v4.1.1
|
uses: actions/checkout@11bd71901bbe5b1630ceea73d27597364c9af683 # v4.2.2
|
||||||
- name: Setup Go
|
- name: Setup Go
|
||||||
uses: actions/setup-go@0c52d547c9bc32b1aa3301fd7a9cb496313a4491 # v5.0.0
|
uses: actions/setup-go@d35c59abb061a4a6fb18e82ac0862c26744d6ab5 # v5.5.0
|
||||||
with:
|
with:
|
||||||
go-version: 1.20.x
|
go-version-file: 'go.mod'
|
||||||
cache-dependency-path: |
|
cache-dependency-path: |
|
||||||
**/go.sum
|
**/go.sum
|
||||||
**/go.mod
|
**/go.mod
|
||||||
- name: Initialize CodeQL
|
- name: Initialize CodeQL
|
||||||
uses: github/codeql-action/init@cdcdbb579706841c47f7063dda365e292e5cad7a # v2.13.4
|
uses: github/codeql-action/init@181d5eefc20863364f96762470ba6f862bdef56b # v3.29.2
|
||||||
with:
|
with:
|
||||||
languages: go
|
languages: go
|
||||||
# xref: https://docs.github.com/en/code-security/code-scanning/automatically-scanning-your-code-for-vulnerabilities-and-errors/configuring-code-scanning#using-queries-in-ql-packs
|
# xref: https://docs.github.com/en/code-security/code-scanning/automatically-scanning-your-code-for-vulnerabilities-and-errors/configuring-code-scanning#using-queries-in-ql-packs
|
||||||
# xref: https://codeql.github.com/codeql-query-help/go/
|
# xref: https://codeql.github.com/codeql-query-help/go/
|
||||||
queries: security-and-quality
|
queries: security-and-quality
|
||||||
- name: Autobuild
|
- name: Autobuild
|
||||||
uses: github/codeql-action/autobuild@cdcdbb579706841c47f7063dda365e292e5cad7a # v2.13.4
|
uses: github/codeql-action/autobuild@181d5eefc20863364f96762470ba6f862bdef56b # v3.29.2
|
||||||
- name: Perform CodeQL Analysis
|
- name: Perform CodeQL Analysis
|
||||||
uses: github/codeql-action/analyze@cdcdbb579706841c47f7063dda365e292e5cad7a # v2.13.4
|
uses: github/codeql-action/analyze@181d5eefc20863364f96762470ba6f862bdef56b # v3.29.2
|
||||||
|
|
|
||||||
|
|
@ -17,8 +17,8 @@ jobs:
|
||||||
permissions:
|
permissions:
|
||||||
issues: write
|
issues: write
|
||||||
steps:
|
steps:
|
||||||
- uses: actions/checkout@b4ffde65f46336ab88eb53be808477a3936bae11 # v4.1.1
|
- uses: actions/checkout@11bd71901bbe5b1630ceea73d27597364c9af683 # v4.2.2
|
||||||
- uses: EndBug/label-sync@da00f2c11fdb78e4fae44adac2fdd713778ea3e8 # v2.3.2
|
- uses: EndBug/label-sync@52074158190acb45f3077f9099fea818aa43f97a # v2.3.3
|
||||||
with:
|
with:
|
||||||
# Configuration file
|
# Configuration file
|
||||||
config-file: |
|
config-file: |
|
||||||
|
|
|
||||||
|
|
@ -18,21 +18,23 @@ jobs:
|
||||||
pull-requests: write
|
pull-requests: write
|
||||||
steps:
|
steps:
|
||||||
- name: Check out code
|
- name: Check out code
|
||||||
uses: actions/checkout@b4ffde65f46336ab88eb53be808477a3936bae11 # v4.1.1
|
uses: actions/checkout@11bd71901bbe5b1630ceea73d27597364c9af683 # v4.2.2
|
||||||
- name: Setup Go
|
- name: Setup Go
|
||||||
uses: actions/setup-go@0c52d547c9bc32b1aa3301fd7a9cb496313a4491 # v5.0.0
|
uses: actions/setup-go@d35c59abb061a4a6fb18e82ac0862c26744d6ab5 # v5.5.0
|
||||||
with:
|
with:
|
||||||
go-version: 1.20.x
|
go-version: 1.24.x
|
||||||
cache-dependency-path: |
|
cache-dependency-path: |
|
||||||
**/go.sum
|
**/go.sum
|
||||||
**/go.mod
|
**/go.mod
|
||||||
- name: Update component versions
|
- name: Update component versions
|
||||||
id: update
|
id: update
|
||||||
|
env:
|
||||||
|
GITHUB_TOKEN: ${{ secrets.GITHUB_TOKEN }}
|
||||||
run: |
|
run: |
|
||||||
PR_BODY=$(mktemp)
|
PR_BODY=$(mktemp)
|
||||||
|
|
||||||
bump_version() {
|
bump_version() {
|
||||||
local LATEST_VERSION=$(curl -s https://api.github.com/repos/fluxcd/$1/releases | jq -r 'sort_by(.published_at) | .[-1] | .tag_name')
|
local LATEST_VERSION=$(curl -s -H "Authorization: token ${GITHUB_TOKEN}" https://api.github.com/repos/fluxcd/$1/releases | jq -r 'sort_by(.published_at) | .[-1] | .tag_name')
|
||||||
local CTRL_VERSION=$(sed -n "s/.*$1\/releases\/download\/\(.*\)\/.*/\1/p;n" manifests/bases/$1/kustomization.yaml)
|
local CTRL_VERSION=$(sed -n "s/.*$1\/releases\/download\/\(.*\)\/.*/\1/p;n" manifests/bases/$1/kustomization.yaml)
|
||||||
local CRD_VERSION=$(sed -n "s/.*$1\/releases\/download\/\(.*\)\/.*/\1/p" manifests/crds/kustomization.yaml)
|
local CRD_VERSION=$(sed -n "s/.*$1\/releases\/download\/\(.*\)\/.*/\1/p" manifests/crds/kustomization.yaml)
|
||||||
local MOD_VERSION=$(go list -m -f '{{ .Version }}' "github.com/fluxcd/$1/api")
|
local MOD_VERSION=$(go list -m -f '{{ .Version }}' "github.com/fluxcd/$1/api")
|
||||||
|
|
@ -84,7 +86,7 @@ jobs:
|
||||||
|
|
||||||
- name: Create Pull Request
|
- name: Create Pull Request
|
||||||
id: cpr
|
id: cpr
|
||||||
uses: peter-evans/create-pull-request@153407881ec5c347639a548ade7d8ad1d6740e38 # v5.0.2
|
uses: peter-evans/create-pull-request@271a8d0340265f705b14b6d32b9829c1cb33d45e # v7.0.8
|
||||||
with:
|
with:
|
||||||
token: ${{ secrets.BOT_GITHUB_TOKEN }}
|
token: ${{ secrets.BOT_GITHUB_TOKEN }}
|
||||||
commit-message: |
|
commit-message: |
|
||||||
|
|
|
||||||
|
|
@ -1,4 +1,6 @@
|
||||||
project_name: flux
|
project_name: flux
|
||||||
|
changelog:
|
||||||
|
use: github-native
|
||||||
builds:
|
builds:
|
||||||
- <<: &build_defaults
|
- <<: &build_defaults
|
||||||
binary: flux
|
binary: flux
|
||||||
|
|
@ -15,7 +17,7 @@ builds:
|
||||||
- arm64
|
- arm64
|
||||||
- arm
|
- arm
|
||||||
goarm:
|
goarm:
|
||||||
- 7
|
- "7"
|
||||||
- <<: *build_defaults
|
- <<: *build_defaults
|
||||||
id: darwin
|
id: darwin
|
||||||
goos:
|
goos:
|
||||||
|
|
@ -73,11 +75,11 @@ signs:
|
||||||
output: true
|
output: true
|
||||||
brews:
|
brews:
|
||||||
- name: flux
|
- name: flux
|
||||||
tap:
|
repository:
|
||||||
owner: fluxcd
|
owner: fluxcd
|
||||||
name: homebrew-tap
|
name: homebrew-tap
|
||||||
token: "{{ .Env.HOMEBREW_TAP_GITHUB_TOKEN }}"
|
token: "{{ .Env.HOMEBREW_TAP_GITHUB_TOKEN }}"
|
||||||
folder: Formula
|
directory: Formula
|
||||||
homepage: "https://fluxcd.io/"
|
homepage: "https://fluxcd.io/"
|
||||||
description: "Flux CLI"
|
description: "Flux CLI"
|
||||||
install: |
|
install: |
|
||||||
|
|
|
||||||
|
|
@ -0,0 +1,5 @@
|
||||||
|
annotations:
|
||||||
|
- checks:
|
||||||
|
- dangerous-workflow
|
||||||
|
reasons:
|
||||||
|
- reason: not-applicable # This workflow does not run untrusted code, the bot will only backport a code if the a PR was approved and merged into main.
|
||||||
|
|
@ -67,8 +67,8 @@ for source changes.
|
||||||
|
|
||||||
Prerequisites:
|
Prerequisites:
|
||||||
|
|
||||||
* go >= 1.20
|
* go >= 1.24
|
||||||
* kubectl >= 1.24
|
* kubectl >= 1.30
|
||||||
* kustomize >= 5.0
|
* kustomize >= 5.0
|
||||||
* coreutils (on Mac OS)
|
* coreutils (on Mac OS)
|
||||||
|
|
||||||
|
|
|
||||||
13
Dockerfile
13
Dockerfile
|
|
@ -1,15 +1,16 @@
|
||||||
FROM alpine:3.19 as builder
|
FROM alpine:3.21 AS builder
|
||||||
|
|
||||||
RUN apk add --no-cache ca-certificates curl
|
RUN apk add --no-cache ca-certificates curl
|
||||||
|
|
||||||
ARG ARCH=linux/amd64
|
ARG ARCH=linux/amd64
|
||||||
ARG KUBECTL_VER=1.28.4
|
ARG KUBECTL_VER=1.33.0
|
||||||
|
|
||||||
RUN curl -sL https://storage.googleapis.com/kubernetes-release/release/v${KUBECTL_VER}/bin/${ARCH}/kubectl \
|
RUN curl -sL https://dl.k8s.io/release/v${KUBECTL_VER}/bin/${ARCH}/kubectl \
|
||||||
-o /usr/local/bin/kubectl && chmod +x /usr/local/bin/kubectl && \
|
-o /usr/local/bin/kubectl && chmod +x /usr/local/bin/kubectl
|
||||||
kubectl version --client=true
|
|
||||||
|
|
||||||
FROM alpine:3.19 as flux-cli
|
RUN kubectl version --client=true
|
||||||
|
|
||||||
|
FROM alpine:3.21 AS flux-cli
|
||||||
|
|
||||||
RUN apk add --no-cache ca-certificates
|
RUN apk add --no-cache ca-certificates
|
||||||
|
|
||||||
|
|
|
||||||
5
Makefile
5
Makefile
|
|
@ -17,9 +17,8 @@ rwildcard=$(foreach d,$(wildcard $(addsuffix *,$(1))),$(call rwildcard,$(d)/,$(2
|
||||||
all: test build
|
all: test build
|
||||||
|
|
||||||
tidy:
|
tidy:
|
||||||
go mod tidy -compat=1.20
|
go mod tidy -compat=1.24
|
||||||
cd tests/azure && go mod tidy -compat=1.20
|
cd tests/integration && go mod tidy -compat=1.24
|
||||||
cd tests/integration && go mod tidy -compat=1.20
|
|
||||||
|
|
||||||
fmt:
|
fmt:
|
||||||
go fmt ./...
|
go fmt ./...
|
||||||
|
|
|
||||||
|
|
@ -2,7 +2,7 @@
|
||||||
|
|
||||||
[](https://github.com/fluxcd/flux2/releases)
|
[](https://github.com/fluxcd/flux2/releases)
|
||||||
[](https://bestpractices.coreinfrastructure.org/projects/4782)
|
[](https://bestpractices.coreinfrastructure.org/projects/4782)
|
||||||
[](https://api.securityscorecards.dev/projects/github.com/fluxcd/flux2)
|
[](https://scorecard.dev/viewer/?uri=github.com/fluxcd/flux2)
|
||||||
[](https://app.fossa.com/projects/custom%2B162%2Fgithub.com%2Ffluxcd%2Fflux2?ref=badge_shield)
|
[](https://app.fossa.com/projects/custom%2B162%2Fgithub.com%2Ffluxcd%2Fflux2?ref=badge_shield)
|
||||||
[](https://artifacthub.io/packages/helm/fluxcd-community/flux2)
|
[](https://artifacthub.io/packages/helm/fluxcd-community/flux2)
|
||||||
[](https://fluxcd.io/flux/security/slsa-assessment)
|
[](https://fluxcd.io/flux/security/slsa-assessment)
|
||||||
|
|
@ -21,7 +21,7 @@ Flux v2 is constructed with the [GitOps Toolkit](#gitops-toolkit), a
|
||||||
set of composable APIs and specialized tools for building Continuous
|
set of composable APIs and specialized tools for building Continuous
|
||||||
Delivery on top of Kubernetes.
|
Delivery on top of Kubernetes.
|
||||||
|
|
||||||
Flux is a Cloud Native Computing Foundation ([CNCF](https://www.cncf.io/)) project, used in
|
Flux is a Cloud Native Computing Foundation ([CNCF](https://www.cncf.io/)) graduated project, used in
|
||||||
production by various [organisations](https://fluxcd.io/adopters) and [cloud providers](https://fluxcd.io/ecosystem).
|
production by various [organisations](https://fluxcd.io/adopters) and [cloud providers](https://fluxcd.io/ecosystem).
|
||||||
|
|
||||||
## Quickstart and documentation
|
## Quickstart and documentation
|
||||||
|
|
@ -44,7 +44,7 @@ runtime for Flux v2. The APIs comprise Kubernetes custom resources,
|
||||||
which can be created and updated by a cluster user, or by other
|
which can be created and updated by a cluster user, or by other
|
||||||
automation tooling.
|
automation tooling.
|
||||||
|
|
||||||
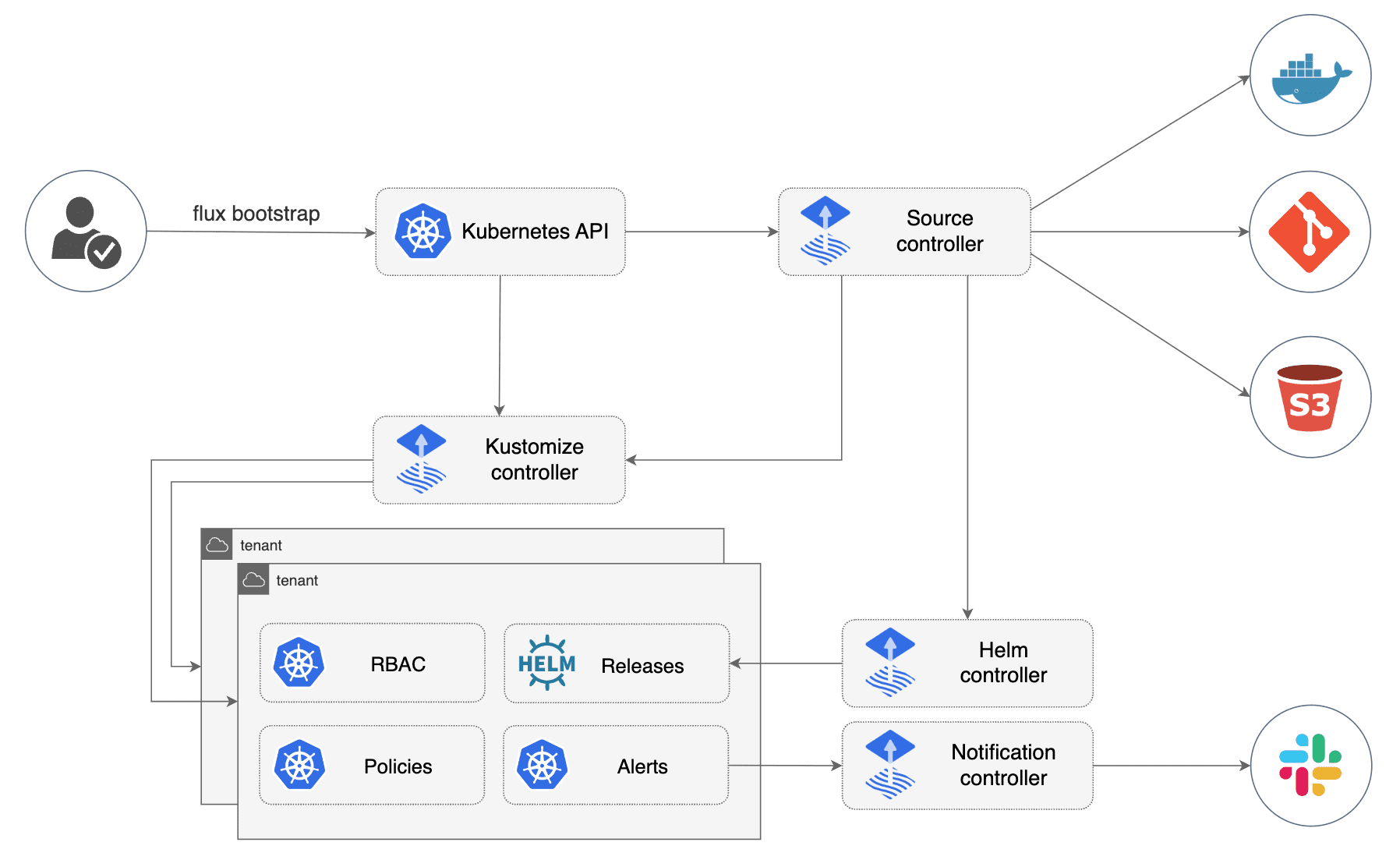
|
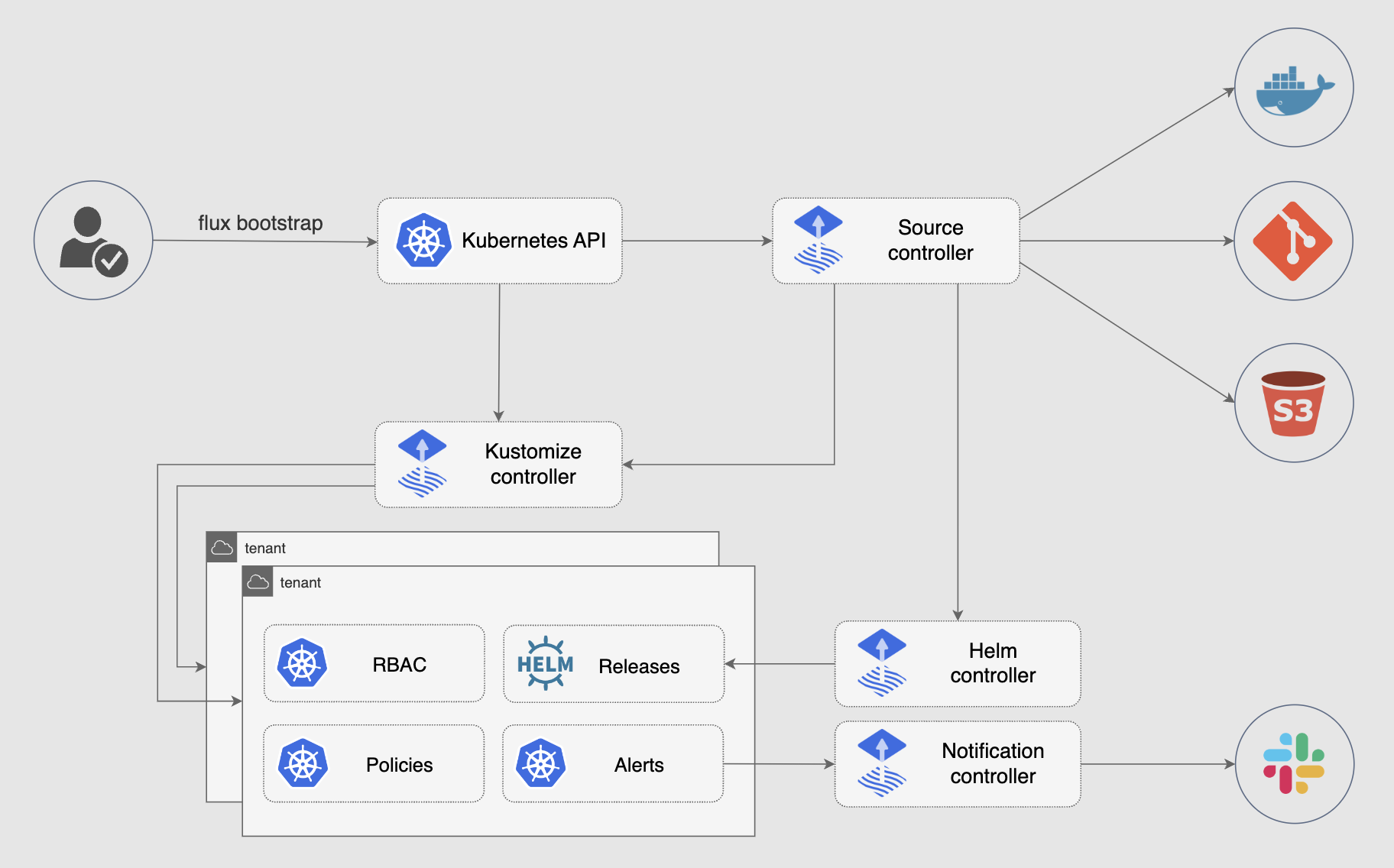
|
||||||
|
|
||||||
You can use the toolkit to extend Flux, or to build your own systems
|
You can use the toolkit to extend Flux, or to build your own systems
|
||||||
for continuous delivery -- see [the developer
|
for continuous delivery -- see [the developer
|
||||||
|
|
|
||||||
|
|
@ -22,6 +22,7 @@ import (
|
||||||
"fmt"
|
"fmt"
|
||||||
"strings"
|
"strings"
|
||||||
|
|
||||||
|
"github.com/fluxcd/pkg/git"
|
||||||
"github.com/manifoldco/promptui"
|
"github.com/manifoldco/promptui"
|
||||||
"github.com/spf13/cobra"
|
"github.com/spf13/cobra"
|
||||||
"k8s.io/apimachinery/pkg/api/errors"
|
"k8s.io/apimachinery/pkg/api/errors"
|
||||||
|
|
@ -52,17 +53,19 @@ type bootstrapFlags struct {
|
||||||
extraComponents []string
|
extraComponents []string
|
||||||
requiredComponents []string
|
requiredComponents []string
|
||||||
|
|
||||||
registry string
|
registry string
|
||||||
imagePullSecret string
|
registryCredential string
|
||||||
|
imagePullSecret string
|
||||||
|
|
||||||
secretName string
|
secretName string
|
||||||
tokenAuth bool
|
tokenAuth bool
|
||||||
keyAlgorithm flags.PublicKeyAlgorithm
|
keyAlgorithm flags.PublicKeyAlgorithm
|
||||||
keyRSABits flags.RSAKeyBits
|
keyRSABits flags.RSAKeyBits
|
||||||
keyECDSACurve flags.ECDSACurve
|
keyECDSACurve flags.ECDSACurve
|
||||||
sshHostname string
|
sshHostname string
|
||||||
caFile string
|
caFile string
|
||||||
privateKeyFile string
|
privateKeyFile string
|
||||||
|
sshHostKeyAlgorithms []string
|
||||||
|
|
||||||
watchAllNamespaces bool
|
watchAllNamespaces bool
|
||||||
networkPolicy bool
|
networkPolicy bool
|
||||||
|
|
@ -98,6 +101,8 @@ func init() {
|
||||||
|
|
||||||
bootstrapCmd.PersistentFlags().StringVar(&bootstrapArgs.registry, "registry", "ghcr.io/fluxcd",
|
bootstrapCmd.PersistentFlags().StringVar(&bootstrapArgs.registry, "registry", "ghcr.io/fluxcd",
|
||||||
"container registry where the Flux controller images are published")
|
"container registry where the Flux controller images are published")
|
||||||
|
bootstrapCmd.PersistentFlags().StringVar(&bootstrapArgs.registryCredential, "registry-creds", "",
|
||||||
|
"container registry credentials in the format 'user:password', requires --image-pull-secret to be set")
|
||||||
bootstrapCmd.PersistentFlags().StringVar(&bootstrapArgs.imagePullSecret, "image-pull-secret", "",
|
bootstrapCmd.PersistentFlags().StringVar(&bootstrapArgs.imagePullSecret, "image-pull-secret", "",
|
||||||
"Kubernetes secret name used for pulling the controller images from a private registry")
|
"Kubernetes secret name used for pulling the controller images from a private registry")
|
||||||
|
|
||||||
|
|
@ -121,6 +126,7 @@ func init() {
|
||||||
bootstrapCmd.PersistentFlags().StringVar(&bootstrapArgs.secretName, "secret-name", rootArgs.defaults.Namespace, "name of the secret the sync credentials can be found in or stored to")
|
bootstrapCmd.PersistentFlags().StringVar(&bootstrapArgs.secretName, "secret-name", rootArgs.defaults.Namespace, "name of the secret the sync credentials can be found in or stored to")
|
||||||
bootstrapCmd.PersistentFlags().Var(&bootstrapArgs.keyAlgorithm, "ssh-key-algorithm", bootstrapArgs.keyAlgorithm.Description())
|
bootstrapCmd.PersistentFlags().Var(&bootstrapArgs.keyAlgorithm, "ssh-key-algorithm", bootstrapArgs.keyAlgorithm.Description())
|
||||||
bootstrapCmd.PersistentFlags().Var(&bootstrapArgs.keyRSABits, "ssh-rsa-bits", bootstrapArgs.keyRSABits.Description())
|
bootstrapCmd.PersistentFlags().Var(&bootstrapArgs.keyRSABits, "ssh-rsa-bits", bootstrapArgs.keyRSABits.Description())
|
||||||
|
bootstrapCmd.PersistentFlags().StringSliceVar(&bootstrapArgs.sshHostKeyAlgorithms, "ssh-hostkey-algos", nil, "list of host key algorithms to be used by the CLI for SSH connections")
|
||||||
bootstrapCmd.PersistentFlags().Var(&bootstrapArgs.keyECDSACurve, "ssh-ecdsa-curve", bootstrapArgs.keyECDSACurve.Description())
|
bootstrapCmd.PersistentFlags().Var(&bootstrapArgs.keyECDSACurve, "ssh-ecdsa-curve", bootstrapArgs.keyECDSACurve.Description())
|
||||||
bootstrapCmd.PersistentFlags().StringVar(&bootstrapArgs.sshHostname, "ssh-hostname", "", "SSH hostname, to be used when the SSH host differs from the HTTPS one")
|
bootstrapCmd.PersistentFlags().StringVar(&bootstrapArgs.sshHostname, "ssh-hostname", "", "SSH hostname, to be used when the SSH host differs from the HTTPS one")
|
||||||
bootstrapCmd.PersistentFlags().StringVar(&bootstrapArgs.caFile, "ca-file", "", "path to TLS CA file used for validating self-signed certificates")
|
bootstrapCmd.PersistentFlags().StringVar(&bootstrapArgs.caFile, "ca-file", "", "path to TLS CA file used for validating self-signed certificates")
|
||||||
|
|
@ -135,7 +141,7 @@ func init() {
|
||||||
|
|
||||||
bootstrapCmd.PersistentFlags().StringVar(&bootstrapArgs.commitMessageAppendix, "commit-message-appendix", "", "string to add to the commit messages, e.g. '[ci skip]'")
|
bootstrapCmd.PersistentFlags().StringVar(&bootstrapArgs.commitMessageAppendix, "commit-message-appendix", "", "string to add to the commit messages, e.g. '[ci skip]'")
|
||||||
|
|
||||||
bootstrapCmd.PersistentFlags().BoolVar(&bootstrapArgs.force, "force", false, "override existing Flux installation if it's managed by a diffrent tool such as Helm")
|
bootstrapCmd.PersistentFlags().BoolVar(&bootstrapArgs.force, "force", false, "override existing Flux installation if it's managed by a different tool such as Helm")
|
||||||
bootstrapCmd.PersistentFlags().MarkHidden("manifests")
|
bootstrapCmd.PersistentFlags().MarkHidden("manifests")
|
||||||
|
|
||||||
rootCmd.AddCommand(bootstrapCmd)
|
rootCmd.AddCommand(bootstrapCmd)
|
||||||
|
|
@ -181,6 +187,18 @@ func bootstrapValidate() error {
|
||||||
return err
|
return err
|
||||||
}
|
}
|
||||||
|
|
||||||
|
if bootstrapArgs.registryCredential != "" && bootstrapArgs.imagePullSecret == "" {
|
||||||
|
return fmt.Errorf("--registry-creds requires --image-pull-secret to be set")
|
||||||
|
}
|
||||||
|
|
||||||
|
if bootstrapArgs.registryCredential != "" && len(strings.Split(bootstrapArgs.registryCredential, ":")) != 2 {
|
||||||
|
return fmt.Errorf("invalid --registry-creds format, expected 'user:password'")
|
||||||
|
}
|
||||||
|
|
||||||
|
if len(bootstrapArgs.sshHostKeyAlgorithms) > 0 {
|
||||||
|
git.HostKeyAlgos = bootstrapArgs.sshHostKeyAlgorithms
|
||||||
|
}
|
||||||
|
|
||||||
return nil
|
return nil
|
||||||
}
|
}
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -196,6 +196,7 @@ func bootstrapBServerCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
Namespace: *kubeconfigArgs.Namespace,
|
Namespace: *kubeconfigArgs.Namespace,
|
||||||
Components: bootstrapComponents(),
|
Components: bootstrapComponents(),
|
||||||
Registry: bootstrapArgs.registry,
|
Registry: bootstrapArgs.registry,
|
||||||
|
RegistryCredential: bootstrapArgs.registryCredential,
|
||||||
ImagePullSecret: bootstrapArgs.imagePullSecret,
|
ImagePullSecret: bootstrapArgs.imagePullSecret,
|
||||||
WatchAllNamespaces: bootstrapArgs.watchAllNamespaces,
|
WatchAllNamespaces: bootstrapArgs.watchAllNamespaces,
|
||||||
NetworkPolicy: bootstrapArgs.networkPolicy,
|
NetworkPolicy: bootstrapArgs.networkPolicy,
|
||||||
|
|
@ -225,7 +226,7 @@ func bootstrapBServerCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
secretOpts.Username = bServerArgs.username
|
secretOpts.Username = bServerArgs.username
|
||||||
}
|
}
|
||||||
secretOpts.Password = bitbucketToken
|
secretOpts.Password = bitbucketToken
|
||||||
secretOpts.CAFile = caBundle
|
secretOpts.CACrt = caBundle
|
||||||
} else {
|
} else {
|
||||||
keypair, err := sourcesecret.LoadKeyPairFromPath(bootstrapArgs.privateKeyFile, gitArgs.password)
|
keypair, err := sourcesecret.LoadKeyPairFromPath(bootstrapArgs.privateKeyFile, gitArgs.password)
|
||||||
if err != nil {
|
if err != nil {
|
||||||
|
|
|
||||||
|
|
@ -28,6 +28,9 @@ import (
|
||||||
"github.com/spf13/cobra"
|
"github.com/spf13/cobra"
|
||||||
corev1 "k8s.io/api/core/v1"
|
corev1 "k8s.io/api/core/v1"
|
||||||
|
|
||||||
|
"github.com/fluxcd/pkg/git"
|
||||||
|
"github.com/fluxcd/pkg/git/gogit"
|
||||||
|
|
||||||
"github.com/fluxcd/flux2/v2/internal/flags"
|
"github.com/fluxcd/flux2/v2/internal/flags"
|
||||||
"github.com/fluxcd/flux2/v2/internal/utils"
|
"github.com/fluxcd/flux2/v2/internal/utils"
|
||||||
"github.com/fluxcd/flux2/v2/pkg/bootstrap"
|
"github.com/fluxcd/flux2/v2/pkg/bootstrap"
|
||||||
|
|
@ -35,8 +38,6 @@ import (
|
||||||
"github.com/fluxcd/flux2/v2/pkg/manifestgen/install"
|
"github.com/fluxcd/flux2/v2/pkg/manifestgen/install"
|
||||||
"github.com/fluxcd/flux2/v2/pkg/manifestgen/sourcesecret"
|
"github.com/fluxcd/flux2/v2/pkg/manifestgen/sourcesecret"
|
||||||
"github.com/fluxcd/flux2/v2/pkg/manifestgen/sync"
|
"github.com/fluxcd/flux2/v2/pkg/manifestgen/sync"
|
||||||
"github.com/fluxcd/pkg/git"
|
|
||||||
"github.com/fluxcd/pkg/git/gogit"
|
|
||||||
)
|
)
|
||||||
|
|
||||||
var bootstrapGitCmd = &cobra.Command{
|
var bootstrapGitCmd = &cobra.Command{
|
||||||
|
|
@ -65,7 +66,10 @@ command will perform an upgrade if needed.`,
|
||||||
flux bootstrap git --url=ssh://<SSH-Key-ID>@git-codecommit.<region>.amazonaws.com/v1/repos/<repository> --private-key-file=<path/to/private.key> --password=<SSH-passphrase> --path=clusters/my-cluster
|
flux bootstrap git --url=ssh://<SSH-Key-ID>@git-codecommit.<region>.amazonaws.com/v1/repos/<repository> --private-key-file=<path/to/private.key> --password=<SSH-passphrase> --path=clusters/my-cluster
|
||||||
|
|
||||||
# Run bootstrap for a Git repository on Azure Devops
|
# Run bootstrap for a Git repository on Azure Devops
|
||||||
flux bootstrap git --url=ssh://git@ssh.dev.azure.com/v3/<org>/<project>/<repository> --ssh-key-algorithm=rsa --ssh-rsa-bits=4096 --path=clusters/my-cluster
|
flux bootstrap git --url=ssh://git@ssh.dev.azure.com/v3/<org>/<project>/<repository> --private-key-file=<path/to/rsa-sha2-private.key> --ssh-hostkey-algos=rsa-sha2-512,rsa-sha2-256 --path=clusters/my-cluster
|
||||||
|
|
||||||
|
# Run bootstrap for a Git repository on Oracle VBS
|
||||||
|
flux bootstrap git --url=https://repository_url.git --with-bearer-token=true --password=<PAT> --path=clusters/my-cluster
|
||||||
`,
|
`,
|
||||||
RunE: bootstrapGitCmdRun,
|
RunE: bootstrapGitCmdRun,
|
||||||
}
|
}
|
||||||
|
|
@ -78,6 +82,7 @@ type gitFlags struct {
|
||||||
password string
|
password string
|
||||||
silent bool
|
silent bool
|
||||||
insecureHttpAllowed bool
|
insecureHttpAllowed bool
|
||||||
|
withBearerToken bool
|
||||||
}
|
}
|
||||||
|
|
||||||
const (
|
const (
|
||||||
|
|
@ -94,11 +99,16 @@ func init() {
|
||||||
bootstrapGitCmd.Flags().StringVarP(&gitArgs.password, "password", "p", "", "basic authentication password")
|
bootstrapGitCmd.Flags().StringVarP(&gitArgs.password, "password", "p", "", "basic authentication password")
|
||||||
bootstrapGitCmd.Flags().BoolVarP(&gitArgs.silent, "silent", "s", false, "assumes the deploy key is already setup, skips confirmation")
|
bootstrapGitCmd.Flags().BoolVarP(&gitArgs.silent, "silent", "s", false, "assumes the deploy key is already setup, skips confirmation")
|
||||||
bootstrapGitCmd.Flags().BoolVar(&gitArgs.insecureHttpAllowed, "allow-insecure-http", false, "allows insecure HTTP connections")
|
bootstrapGitCmd.Flags().BoolVar(&gitArgs.insecureHttpAllowed, "allow-insecure-http", false, "allows insecure HTTP connections")
|
||||||
|
bootstrapGitCmd.Flags().BoolVar(&gitArgs.withBearerToken, "with-bearer-token", false, "use password as bearer token for Authorization header")
|
||||||
|
|
||||||
bootstrapCmd.AddCommand(bootstrapGitCmd)
|
bootstrapCmd.AddCommand(bootstrapGitCmd)
|
||||||
}
|
}
|
||||||
|
|
||||||
func bootstrapGitCmdRun(cmd *cobra.Command, args []string) error {
|
func bootstrapGitCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
|
if gitArgs.withBearerToken {
|
||||||
|
bootstrapArgs.tokenAuth = true
|
||||||
|
}
|
||||||
|
|
||||||
gitPassword := os.Getenv(gitPasswordEnvVar)
|
gitPassword := os.Getenv(gitPasswordEnvVar)
|
||||||
if gitPassword != "" && gitArgs.password == "" {
|
if gitPassword != "" && gitArgs.password == "" {
|
||||||
gitArgs.password = gitPassword
|
gitArgs.password = gitPassword
|
||||||
|
|
@ -201,6 +211,7 @@ func bootstrapGitCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
Namespace: *kubeconfigArgs.Namespace,
|
Namespace: *kubeconfigArgs.Namespace,
|
||||||
Components: bootstrapComponents(),
|
Components: bootstrapComponents(),
|
||||||
Registry: bootstrapArgs.registry,
|
Registry: bootstrapArgs.registry,
|
||||||
|
RegistryCredential: bootstrapArgs.registryCredential,
|
||||||
ImagePullSecret: bootstrapArgs.imagePullSecret,
|
ImagePullSecret: bootstrapArgs.imagePullSecret,
|
||||||
WatchAllNamespaces: bootstrapArgs.watchAllNamespaces,
|
WatchAllNamespaces: bootstrapArgs.watchAllNamespaces,
|
||||||
NetworkPolicy: bootstrapArgs.networkPolicy,
|
NetworkPolicy: bootstrapArgs.networkPolicy,
|
||||||
|
|
@ -223,10 +234,16 @@ func bootstrapGitCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
TargetPath: gitArgs.path.String(),
|
TargetPath: gitArgs.path.String(),
|
||||||
ManifestFile: sourcesecret.MakeDefaultOptions().ManifestFile,
|
ManifestFile: sourcesecret.MakeDefaultOptions().ManifestFile,
|
||||||
}
|
}
|
||||||
|
|
||||||
if bootstrapArgs.tokenAuth {
|
if bootstrapArgs.tokenAuth {
|
||||||
secretOpts.Username = gitArgs.username
|
if gitArgs.withBearerToken {
|
||||||
secretOpts.Password = gitArgs.password
|
secretOpts.BearerToken = gitArgs.password
|
||||||
secretOpts.CAFile = caBundle
|
} else {
|
||||||
|
secretOpts.Username = gitArgs.username
|
||||||
|
secretOpts.Password = gitArgs.password
|
||||||
|
}
|
||||||
|
|
||||||
|
secretOpts.CACrt = caBundle
|
||||||
|
|
||||||
// Remove port of the given host when not syncing over HTTP/S to not assume port for protocol
|
// Remove port of the given host when not syncing over HTTP/S to not assume port for protocol
|
||||||
// This _might_ be overwritten later on by e.g. --ssh-hostname
|
// This _might_ be overwritten later on by e.g. --ssh-hostname
|
||||||
|
|
@ -318,18 +335,28 @@ func getAuthOpts(u *url.URL, caBundle []byte) (*git.AuthOptions, error) {
|
||||||
if !gitArgs.insecureHttpAllowed {
|
if !gitArgs.insecureHttpAllowed {
|
||||||
return nil, fmt.Errorf("scheme http is insecure, pass --allow-insecure-http=true to allow it")
|
return nil, fmt.Errorf("scheme http is insecure, pass --allow-insecure-http=true to allow it")
|
||||||
}
|
}
|
||||||
return &git.AuthOptions{
|
httpAuth := git.AuthOptions{
|
||||||
Transport: git.HTTP,
|
Transport: git.HTTP,
|
||||||
Username: gitArgs.username,
|
}
|
||||||
Password: gitArgs.password,
|
if gitArgs.withBearerToken {
|
||||||
}, nil
|
httpAuth.BearerToken = gitArgs.password
|
||||||
|
} else {
|
||||||
|
httpAuth.Username = gitArgs.username
|
||||||
|
httpAuth.Password = gitArgs.password
|
||||||
|
}
|
||||||
|
return &httpAuth, nil
|
||||||
case "https":
|
case "https":
|
||||||
return &git.AuthOptions{
|
httpsAuth := git.AuthOptions{
|
||||||
Transport: git.HTTPS,
|
Transport: git.HTTPS,
|
||||||
Username: gitArgs.username,
|
|
||||||
Password: gitArgs.password,
|
|
||||||
CAFile: caBundle,
|
CAFile: caBundle,
|
||||||
}, nil
|
}
|
||||||
|
if gitArgs.withBearerToken {
|
||||||
|
httpsAuth.BearerToken = gitArgs.password
|
||||||
|
} else {
|
||||||
|
httpsAuth.Username = gitArgs.username
|
||||||
|
httpsAuth.Password = gitArgs.password
|
||||||
|
}
|
||||||
|
return &httpsAuth, nil
|
||||||
case "ssh":
|
case "ssh":
|
||||||
authOpts := &git.AuthOptions{
|
authOpts := &git.AuthOptions{
|
||||||
Transport: git.SSH,
|
Transport: git.SSH,
|
||||||
|
|
|
||||||
|
|
@ -184,6 +184,7 @@ func bootstrapGiteaCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
Namespace: *kubeconfigArgs.Namespace,
|
Namespace: *kubeconfigArgs.Namespace,
|
||||||
Components: bootstrapComponents(),
|
Components: bootstrapComponents(),
|
||||||
Registry: bootstrapArgs.registry,
|
Registry: bootstrapArgs.registry,
|
||||||
|
RegistryCredential: bootstrapArgs.registryCredential,
|
||||||
ImagePullSecret: bootstrapArgs.imagePullSecret,
|
ImagePullSecret: bootstrapArgs.imagePullSecret,
|
||||||
WatchAllNamespaces: bootstrapArgs.watchAllNamespaces,
|
WatchAllNamespaces: bootstrapArgs.watchAllNamespaces,
|
||||||
NetworkPolicy: bootstrapArgs.networkPolicy,
|
NetworkPolicy: bootstrapArgs.networkPolicy,
|
||||||
|
|
@ -209,7 +210,7 @@ func bootstrapGiteaCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
if bootstrapArgs.tokenAuth {
|
if bootstrapArgs.tokenAuth {
|
||||||
secretOpts.Username = "git"
|
secretOpts.Username = "git"
|
||||||
secretOpts.Password = gtToken
|
secretOpts.Password = gtToken
|
||||||
secretOpts.CAFile = caBundle
|
secretOpts.CACrt = caBundle
|
||||||
} else {
|
} else {
|
||||||
secretOpts.PrivateKeyAlgorithm = sourcesecret.PrivateKeyAlgorithm(bootstrapArgs.keyAlgorithm)
|
secretOpts.PrivateKeyAlgorithm = sourcesecret.PrivateKeyAlgorithm(bootstrapArgs.keyAlgorithm)
|
||||||
secretOpts.RSAKeyBits = int(bootstrapArgs.keyRSABits)
|
secretOpts.RSAKeyBits = int(bootstrapArgs.keyRSABits)
|
||||||
|
|
|
||||||
|
|
@ -191,6 +191,7 @@ func bootstrapGitHubCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
Namespace: *kubeconfigArgs.Namespace,
|
Namespace: *kubeconfigArgs.Namespace,
|
||||||
Components: bootstrapComponents(),
|
Components: bootstrapComponents(),
|
||||||
Registry: bootstrapArgs.registry,
|
Registry: bootstrapArgs.registry,
|
||||||
|
RegistryCredential: bootstrapArgs.registryCredential,
|
||||||
ImagePullSecret: bootstrapArgs.imagePullSecret,
|
ImagePullSecret: bootstrapArgs.imagePullSecret,
|
||||||
WatchAllNamespaces: bootstrapArgs.watchAllNamespaces,
|
WatchAllNamespaces: bootstrapArgs.watchAllNamespaces,
|
||||||
NetworkPolicy: bootstrapArgs.networkPolicy,
|
NetworkPolicy: bootstrapArgs.networkPolicy,
|
||||||
|
|
@ -216,7 +217,7 @@ func bootstrapGitHubCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
if bootstrapArgs.tokenAuth {
|
if bootstrapArgs.tokenAuth {
|
||||||
secretOpts.Username = "git"
|
secretOpts.Username = "git"
|
||||||
secretOpts.Password = ghToken
|
secretOpts.Password = ghToken
|
||||||
secretOpts.CAFile = caBundle
|
secretOpts.CACrt = caBundle
|
||||||
} else {
|
} else {
|
||||||
secretOpts.PrivateKeyAlgorithm = sourcesecret.PrivateKeyAlgorithm(bootstrapArgs.keyAlgorithm)
|
secretOpts.PrivateKeyAlgorithm = sourcesecret.PrivateKeyAlgorithm(bootstrapArgs.keyAlgorithm)
|
||||||
secretOpts.RSAKeyBits = int(bootstrapArgs.keyRSABits)
|
secretOpts.RSAKeyBits = int(bootstrapArgs.keyRSABits)
|
||||||
|
|
|
||||||
|
|
@ -24,6 +24,7 @@ import (
|
||||||
"strings"
|
"strings"
|
||||||
"time"
|
"time"
|
||||||
|
|
||||||
|
"github.com/fluxcd/go-git-providers/gitprovider"
|
||||||
"github.com/fluxcd/pkg/git"
|
"github.com/fluxcd/pkg/git"
|
||||||
"github.com/fluxcd/pkg/git/gogit"
|
"github.com/fluxcd/pkg/git/gogit"
|
||||||
"github.com/spf13/cobra"
|
"github.com/spf13/cobra"
|
||||||
|
|
@ -41,7 +42,7 @@ import (
|
||||||
var bootstrapGitLabCmd = &cobra.Command{
|
var bootstrapGitLabCmd = &cobra.Command{
|
||||||
Use: "gitlab",
|
Use: "gitlab",
|
||||||
Short: "Deploy Flux on a cluster connected to a GitLab repository",
|
Short: "Deploy Flux on a cluster connected to a GitLab repository",
|
||||||
Long: `The bootstrap gitlab command creates the GitLab repository if it doesn't exists and
|
Long: `The bootstrap gitlab command creates the GitLab repository if it doesn't exist and
|
||||||
commits the Flux manifests to the specified branch.
|
commits the Flux manifests to the specified branch.
|
||||||
Then it configures the target cluster to synchronize with that repository.
|
Then it configures the target cluster to synchronize with that repository.
|
||||||
If the Flux components are present on the cluster,
|
If the Flux components are present on the cluster,
|
||||||
|
|
@ -58,14 +59,14 @@ the bootstrap command will perform an upgrade if needed.`,
|
||||||
# Run bootstrap for a repository path
|
# Run bootstrap for a repository path
|
||||||
flux bootstrap gitlab --owner=<group> --repository=<repository name> --path=dev-cluster
|
flux bootstrap gitlab --owner=<group> --repository=<repository name> --path=dev-cluster
|
||||||
|
|
||||||
# Run bootstrap for a public repository on a personal account
|
# Run bootstrap for a public repository
|
||||||
flux bootstrap gitlab --owner=<user> --repository=<repository name> --private=false --personal --token-auth
|
flux bootstrap gitlab --owner=<group> --repository=<repository name> --visibility=public --token-auth
|
||||||
|
|
||||||
# Run bootstrap for a private repository hosted on a GitLab server
|
# Run bootstrap for a private repository hosted on a GitLab server
|
||||||
flux bootstrap gitlab --owner=<group> --repository=<repository name> --hostname=<domain> --token-auth
|
flux bootstrap gitlab --owner=<group> --repository=<repository name> --hostname=<gitlab_url> --token-auth
|
||||||
|
|
||||||
# Run bootstrap for an existing repository with a branch named main
|
# Run bootstrap for an existing repository with a branch named main
|
||||||
flux bootstrap gitlab --owner=<organization> --repository=<repository name> --branch=main --token-auth
|
flux bootstrap gitlab --owner=<group> --repository=<repository name> --branch=main --token-auth
|
||||||
|
|
||||||
# Run bootstrap for a private repository using Deploy Token authentication
|
# Run bootstrap for a private repository using Deploy Token authentication
|
||||||
flux bootstrap gitlab --owner=<group> --repository=<repository name> --deploy-token-auth
|
flux bootstrap gitlab --owner=<group> --repository=<repository name> --deploy-token-auth
|
||||||
|
|
@ -85,6 +86,7 @@ type gitlabFlags struct {
|
||||||
repository string
|
repository string
|
||||||
interval time.Duration
|
interval time.Duration
|
||||||
personal bool
|
personal bool
|
||||||
|
visibility flags.GitLabVisibility
|
||||||
private bool
|
private bool
|
||||||
hostname string
|
hostname string
|
||||||
path flags.SafeRelativePath
|
path flags.SafeRelativePath
|
||||||
|
|
@ -94,7 +96,13 @@ type gitlabFlags struct {
|
||||||
deployTokenAuth bool
|
deployTokenAuth bool
|
||||||
}
|
}
|
||||||
|
|
||||||
var gitlabArgs gitlabFlags
|
func NewGitlabFlags() gitlabFlags {
|
||||||
|
return gitlabFlags{
|
||||||
|
visibility: flags.GitLabVisibility(gitprovider.RepositoryVisibilityPrivate),
|
||||||
|
}
|
||||||
|
}
|
||||||
|
|
||||||
|
var gitlabArgs = NewGitlabFlags()
|
||||||
|
|
||||||
func init() {
|
func init() {
|
||||||
bootstrapGitLabCmd.Flags().StringVar(&gitlabArgs.owner, "owner", "", "GitLab user or group name")
|
bootstrapGitLabCmd.Flags().StringVar(&gitlabArgs.owner, "owner", "", "GitLab user or group name")
|
||||||
|
|
@ -102,6 +110,8 @@ func init() {
|
||||||
bootstrapGitLabCmd.Flags().StringSliceVar(&gitlabArgs.teams, "team", []string{}, "GitLab teams to be given maintainer access (also accepts comma-separated values)")
|
bootstrapGitLabCmd.Flags().StringSliceVar(&gitlabArgs.teams, "team", []string{}, "GitLab teams to be given maintainer access (also accepts comma-separated values)")
|
||||||
bootstrapGitLabCmd.Flags().BoolVar(&gitlabArgs.personal, "personal", false, "if true, the owner is assumed to be a GitLab user; otherwise a group")
|
bootstrapGitLabCmd.Flags().BoolVar(&gitlabArgs.personal, "personal", false, "if true, the owner is assumed to be a GitLab user; otherwise a group")
|
||||||
bootstrapGitLabCmd.Flags().BoolVar(&gitlabArgs.private, "private", true, "if true, the repository is setup or configured as private")
|
bootstrapGitLabCmd.Flags().BoolVar(&gitlabArgs.private, "private", true, "if true, the repository is setup or configured as private")
|
||||||
|
bootstrapGitLabCmd.Flags().MarkDeprecated("private", "use --visibility instead")
|
||||||
|
bootstrapGitLabCmd.Flags().Var(&gitlabArgs.visibility, "visibility", gitlabArgs.visibility.Description())
|
||||||
bootstrapGitLabCmd.Flags().DurationVar(&gitlabArgs.interval, "interval", time.Minute, "sync interval")
|
bootstrapGitLabCmd.Flags().DurationVar(&gitlabArgs.interval, "interval", time.Minute, "sync interval")
|
||||||
bootstrapGitLabCmd.Flags().StringVar(&gitlabArgs.hostname, "hostname", glDefaultDomain, "GitLab hostname")
|
bootstrapGitLabCmd.Flags().StringVar(&gitlabArgs.hostname, "hostname", glDefaultDomain, "GitLab hostname")
|
||||||
bootstrapGitLabCmd.Flags().Var(&gitlabArgs.path, "path", "path relative to the repository root, when specified the cluster sync will be scoped to this path")
|
bootstrapGitLabCmd.Flags().Var(&gitlabArgs.path, "path", "path relative to the repository root, when specified the cluster sync will be scoped to this path")
|
||||||
|
|
@ -133,6 +143,11 @@ func bootstrapGitLabCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
return fmt.Errorf("--token-auth and --deploy-token-auth cannot be set both.")
|
return fmt.Errorf("--token-auth and --deploy-token-auth cannot be set both.")
|
||||||
}
|
}
|
||||||
|
|
||||||
|
if !gitlabArgs.private {
|
||||||
|
gitlabArgs.visibility.Set(string(gitprovider.RepositoryVisibilityPublic))
|
||||||
|
cmd.Println("Using visibility public as --private=false")
|
||||||
|
}
|
||||||
|
|
||||||
if err := bootstrapValidate(); err != nil {
|
if err := bootstrapValidate(); err != nil {
|
||||||
return err
|
return err
|
||||||
}
|
}
|
||||||
|
|
@ -216,6 +231,7 @@ func bootstrapGitLabCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
Namespace: *kubeconfigArgs.Namespace,
|
Namespace: *kubeconfigArgs.Namespace,
|
||||||
Components: bootstrapComponents(),
|
Components: bootstrapComponents(),
|
||||||
Registry: bootstrapArgs.registry,
|
Registry: bootstrapArgs.registry,
|
||||||
|
RegistryCredential: bootstrapArgs.registryCredential,
|
||||||
ImagePullSecret: bootstrapArgs.imagePullSecret,
|
ImagePullSecret: bootstrapArgs.imagePullSecret,
|
||||||
WatchAllNamespaces: bootstrapArgs.watchAllNamespaces,
|
WatchAllNamespaces: bootstrapArgs.watchAllNamespaces,
|
||||||
NetworkPolicy: bootstrapArgs.networkPolicy,
|
NetworkPolicy: bootstrapArgs.networkPolicy,
|
||||||
|
|
@ -241,10 +257,10 @@ func bootstrapGitLabCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
if bootstrapArgs.tokenAuth {
|
if bootstrapArgs.tokenAuth {
|
||||||
secretOpts.Username = "git"
|
secretOpts.Username = "git"
|
||||||
secretOpts.Password = glToken
|
secretOpts.Password = glToken
|
||||||
secretOpts.CAFile = caBundle
|
secretOpts.CACrt = caBundle
|
||||||
} else if gitlabArgs.deployTokenAuth {
|
} else if gitlabArgs.deployTokenAuth {
|
||||||
// the actual deploy token will be reconciled later
|
// the actual deploy token will be reconciled later
|
||||||
secretOpts.CAFile = caBundle
|
secretOpts.CACrt = caBundle
|
||||||
} else {
|
} else {
|
||||||
keypair, err := sourcesecret.LoadKeyPairFromPath(bootstrapArgs.privateKeyFile, gitArgs.password)
|
keypair, err := sourcesecret.LoadKeyPairFromPath(bootstrapArgs.privateKeyFile, gitArgs.password)
|
||||||
if err != nil {
|
if err != nil {
|
||||||
|
|
@ -281,6 +297,7 @@ func bootstrapGitLabCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
// Bootstrap config
|
// Bootstrap config
|
||||||
bootstrapOpts := []bootstrap.GitProviderOption{
|
bootstrapOpts := []bootstrap.GitProviderOption{
|
||||||
bootstrap.WithProviderRepository(gitlabArgs.owner, gitlabArgs.repository, gitlabArgs.personal),
|
bootstrap.WithProviderRepository(gitlabArgs.owner, gitlabArgs.repository, gitlabArgs.personal),
|
||||||
|
bootstrap.WithProviderVisibility(gitlabArgs.visibility.String()),
|
||||||
bootstrap.WithBranch(bootstrapArgs.branch),
|
bootstrap.WithBranch(bootstrapArgs.branch),
|
||||||
bootstrap.WithBootstrapTransportType("https"),
|
bootstrap.WithBootstrapTransportType("https"),
|
||||||
bootstrap.WithSignature(bootstrapArgs.authorName, bootstrapArgs.authorEmail),
|
bootstrap.WithSignature(bootstrapArgs.authorName, bootstrapArgs.authorEmail),
|
||||||
|
|
@ -300,9 +317,6 @@ func bootstrapGitLabCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
if gitlabArgs.deployTokenAuth {
|
if gitlabArgs.deployTokenAuth {
|
||||||
bootstrapOpts = append(bootstrapOpts, bootstrap.WithDeployTokenAuth())
|
bootstrapOpts = append(bootstrapOpts, bootstrap.WithDeployTokenAuth())
|
||||||
}
|
}
|
||||||
if !gitlabArgs.private {
|
|
||||||
bootstrapOpts = append(bootstrapOpts, bootstrap.WithProviderRepositoryConfig("", "", "public"))
|
|
||||||
}
|
|
||||||
if gitlabArgs.reconcile {
|
if gitlabArgs.reconcile {
|
||||||
bootstrapOpts = append(bootstrapOpts, bootstrap.WithReconcile())
|
bootstrapOpts = append(bootstrapOpts, bootstrap.WithReconcile())
|
||||||
}
|
}
|
||||||
|
|
|
||||||
|
|
@ -26,15 +26,15 @@ import (
|
||||||
|
|
||||||
"github.com/spf13/cobra"
|
"github.com/spf13/cobra"
|
||||||
|
|
||||||
oci "github.com/fluxcd/pkg/oci/client"
|
"github.com/fluxcd/pkg/oci"
|
||||||
"github.com/fluxcd/pkg/sourceignore"
|
"github.com/fluxcd/pkg/sourceignore"
|
||||||
)
|
)
|
||||||
|
|
||||||
var buildArtifactCmd = &cobra.Command{
|
var buildArtifactCmd = &cobra.Command{
|
||||||
Use: "artifact",
|
Use: "artifact",
|
||||||
Short: "Build artifact",
|
Short: "Build artifact",
|
||||||
Long: withPreviewNote(`The build artifact command creates a tgz file with the manifests
|
Long: `The build artifact command creates a tgz file with the manifests
|
||||||
from the given directory or a single manifest file.`),
|
from the given directory or a single manifest file.`,
|
||||||
Example: ` # Build the given manifests directory into an artifact
|
Example: ` # Build the given manifests directory into an artifact
|
||||||
flux build artifact --path ./path/to/local/manifests --output ./path/to/artifact.tgz
|
flux build artifact --path ./path/to/local/manifests --output ./path/to/artifact.tgz
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -21,10 +21,10 @@ import (
|
||||||
"os"
|
"os"
|
||||||
"os/signal"
|
"os/signal"
|
||||||
|
|
||||||
"github.com/fluxcd/pkg/ssa"
|
|
||||||
"github.com/spf13/cobra"
|
"github.com/spf13/cobra"
|
||||||
|
|
||||||
kustomizev1 "github.com/fluxcd/kustomize-controller/api/v1"
|
kustomizev1 "github.com/fluxcd/kustomize-controller/api/v1"
|
||||||
|
ssautil "github.com/fluxcd/pkg/ssa/utils"
|
||||||
|
|
||||||
"github.com/fluxcd/flux2/v2/internal/build"
|
"github.com/fluxcd/flux2/v2/internal/build"
|
||||||
)
|
)
|
||||||
|
|
@ -53,7 +53,12 @@ flux build kustomization my-app --path ./path/to/local/manifests \
|
||||||
# Exclude files by providing a comma separated list of entries that follow the .gitignore pattern fromat.
|
# Exclude files by providing a comma separated list of entries that follow the .gitignore pattern fromat.
|
||||||
flux build kustomization my-app --path ./path/to/local/manifests \
|
flux build kustomization my-app --path ./path/to/local/manifests \
|
||||||
--kustomization-file ./path/to/local/my-app.yaml \
|
--kustomization-file ./path/to/local/my-app.yaml \
|
||||||
--ignore-paths "/to_ignore/**/*.yaml,ignore.yaml"`,
|
--ignore-paths "/to_ignore/**/*.yaml,ignore.yaml"
|
||||||
|
|
||||||
|
# Run recursively on all encountered Kustomizations
|
||||||
|
flux build kustomization my-app --path ./path/to/local/manifests \
|
||||||
|
--recursive \
|
||||||
|
--local-sources GitRepository/flux-system/my-repo=./path/to/local/git`,
|
||||||
ValidArgsFunction: resourceNamesCompletionFunc(kustomizev1.GroupVersion.WithKind(kustomizev1.KustomizationKind)),
|
ValidArgsFunction: resourceNamesCompletionFunc(kustomizev1.GroupVersion.WithKind(kustomizev1.KustomizationKind)),
|
||||||
RunE: buildKsCmdRun,
|
RunE: buildKsCmdRun,
|
||||||
}
|
}
|
||||||
|
|
@ -63,6 +68,9 @@ type buildKsFlags struct {
|
||||||
path string
|
path string
|
||||||
ignorePaths []string
|
ignorePaths []string
|
||||||
dryRun bool
|
dryRun bool
|
||||||
|
strictSubst bool
|
||||||
|
recursive bool
|
||||||
|
localSources map[string]string
|
||||||
}
|
}
|
||||||
|
|
||||||
var buildKsArgs buildKsFlags
|
var buildKsArgs buildKsFlags
|
||||||
|
|
@ -72,6 +80,10 @@ func init() {
|
||||||
buildKsCmd.Flags().StringVar(&buildKsArgs.kustomizationFile, "kustomization-file", "", "Path to the Flux Kustomization YAML file.")
|
buildKsCmd.Flags().StringVar(&buildKsArgs.kustomizationFile, "kustomization-file", "", "Path to the Flux Kustomization YAML file.")
|
||||||
buildKsCmd.Flags().StringSliceVar(&buildKsArgs.ignorePaths, "ignore-paths", nil, "set paths to ignore in .gitignore format")
|
buildKsCmd.Flags().StringSliceVar(&buildKsArgs.ignorePaths, "ignore-paths", nil, "set paths to ignore in .gitignore format")
|
||||||
buildKsCmd.Flags().BoolVar(&buildKsArgs.dryRun, "dry-run", false, "Dry run mode.")
|
buildKsCmd.Flags().BoolVar(&buildKsArgs.dryRun, "dry-run", false, "Dry run mode.")
|
||||||
|
buildKsCmd.Flags().BoolVar(&buildKsArgs.strictSubst, "strict-substitute", false,
|
||||||
|
"When enabled, the post build substitutions will fail if a var without a default value is declared in files but is missing from the input vars.")
|
||||||
|
buildKsCmd.Flags().BoolVarP(&buildKsArgs.recursive, "recursive", "r", false, "Recursively build Kustomizations")
|
||||||
|
buildKsCmd.Flags().StringToStringVar(&buildKsArgs.localSources, "local-sources", nil, "Comma-separated list of repositories in format: Kind/namespace/name=path")
|
||||||
buildCmd.AddCommand(buildKsCmd)
|
buildCmd.AddCommand(buildKsCmd)
|
||||||
}
|
}
|
||||||
|
|
||||||
|
|
@ -107,6 +119,9 @@ func buildKsCmdRun(cmd *cobra.Command, args []string) (err error) {
|
||||||
build.WithDryRun(buildKsArgs.dryRun),
|
build.WithDryRun(buildKsArgs.dryRun),
|
||||||
build.WithNamespace(*kubeconfigArgs.Namespace),
|
build.WithNamespace(*kubeconfigArgs.Namespace),
|
||||||
build.WithIgnore(buildKsArgs.ignorePaths),
|
build.WithIgnore(buildKsArgs.ignorePaths),
|
||||||
|
build.WithStrictSubstitute(buildKsArgs.strictSubst),
|
||||||
|
build.WithRecursive(buildKsArgs.recursive),
|
||||||
|
build.WithLocalSources(buildKsArgs.localSources),
|
||||||
)
|
)
|
||||||
} else {
|
} else {
|
||||||
builder, err = build.NewBuilder(name, buildKsArgs.path,
|
builder, err = build.NewBuilder(name, buildKsArgs.path,
|
||||||
|
|
@ -114,6 +129,9 @@ func buildKsCmdRun(cmd *cobra.Command, args []string) (err error) {
|
||||||
build.WithTimeout(rootArgs.timeout),
|
build.WithTimeout(rootArgs.timeout),
|
||||||
build.WithKustomizationFile(buildKsArgs.kustomizationFile),
|
build.WithKustomizationFile(buildKsArgs.kustomizationFile),
|
||||||
build.WithIgnore(buildKsArgs.ignorePaths),
|
build.WithIgnore(buildKsArgs.ignorePaths),
|
||||||
|
build.WithStrictSubstitute(buildKsArgs.strictSubst),
|
||||||
|
build.WithRecursive(buildKsArgs.recursive),
|
||||||
|
build.WithLocalSources(buildKsArgs.localSources),
|
||||||
)
|
)
|
||||||
}
|
}
|
||||||
|
|
||||||
|
|
@ -132,7 +150,7 @@ func buildKsCmdRun(cmd *cobra.Command, args []string) (err error) {
|
||||||
errChan <- err
|
errChan <- err
|
||||||
}
|
}
|
||||||
|
|
||||||
manifests, err := ssa.ObjectsToYAML(objects)
|
manifests, err := ssautil.ObjectsToYAML(objects)
|
||||||
if err != nil {
|
if err != nil {
|
||||||
errChan <- err
|
errChan <- err
|
||||||
}
|
}
|
||||||
|
|
|
||||||
|
|
@ -22,6 +22,7 @@ package main
|
||||||
import (
|
import (
|
||||||
"bytes"
|
"bytes"
|
||||||
"os"
|
"os"
|
||||||
|
"path/filepath"
|
||||||
"testing"
|
"testing"
|
||||||
"text/template"
|
"text/template"
|
||||||
)
|
)
|
||||||
|
|
@ -69,6 +70,12 @@ func TestBuildKustomization(t *testing.T) {
|
||||||
resultFile: "./testdata/build-kustomization/podinfo-with-ignore-result.yaml",
|
resultFile: "./testdata/build-kustomization/podinfo-with-ignore-result.yaml",
|
||||||
assertFunc: "assertGoldenTemplateFile",
|
assertFunc: "assertGoldenTemplateFile",
|
||||||
},
|
},
|
||||||
|
{
|
||||||
|
name: "build with recursive",
|
||||||
|
args: "build kustomization podinfo --path ./testdata/build-kustomization/podinfo-with-my-app --recursive --local-sources GitRepository/default/podinfo=./testdata/build-kustomization",
|
||||||
|
resultFile: "./testdata/build-kustomization/podinfo-with-my-app-result.yaml",
|
||||||
|
assertFunc: "assertGoldenTemplateFile",
|
||||||
|
},
|
||||||
}
|
}
|
||||||
|
|
||||||
tmpl := map[string]string{
|
tmpl := map[string]string{
|
||||||
|
|
@ -118,6 +125,8 @@ spec:
|
||||||
cluster_region: "eu-central-1"
|
cluster_region: "eu-central-1"
|
||||||
`
|
`
|
||||||
|
|
||||||
|
tmpFile := filepath.Join(t.TempDir(), "podinfo.yaml")
|
||||||
|
|
||||||
tests := []struct {
|
tests := []struct {
|
||||||
name string
|
name string
|
||||||
args string
|
args string
|
||||||
|
|
@ -132,28 +141,40 @@ spec:
|
||||||
},
|
},
|
||||||
{
|
{
|
||||||
name: "build podinfo",
|
name: "build podinfo",
|
||||||
args: "build kustomization podinfo --kustomization-file ./testdata/build-kustomization/podinfo.yaml --path ./testdata/build-kustomization/podinfo",
|
args: "build kustomization podinfo --kustomization-file " + tmpFile + " --path ./testdata/build-kustomization/podinfo",
|
||||||
resultFile: "./testdata/build-kustomization/podinfo-result.yaml",
|
resultFile: "./testdata/build-kustomization/podinfo-result.yaml",
|
||||||
assertFunc: "assertGoldenTemplateFile",
|
assertFunc: "assertGoldenTemplateFile",
|
||||||
},
|
},
|
||||||
{
|
{
|
||||||
name: "build podinfo without service",
|
name: "build podinfo without service",
|
||||||
args: "build kustomization podinfo --kustomization-file ./testdata/build-kustomization/podinfo.yaml --path ./testdata/build-kustomization/delete-service",
|
args: "build kustomization podinfo --kustomization-file " + tmpFile + " --path ./testdata/build-kustomization/delete-service",
|
||||||
resultFile: "./testdata/build-kustomization/podinfo-without-service-result.yaml",
|
resultFile: "./testdata/build-kustomization/podinfo-without-service-result.yaml",
|
||||||
assertFunc: "assertGoldenTemplateFile",
|
assertFunc: "assertGoldenTemplateFile",
|
||||||
},
|
},
|
||||||
{
|
{
|
||||||
name: "build deployment and configmap with var substitution",
|
name: "build deployment and configmap with var substitution",
|
||||||
args: "build kustomization podinfo --kustomization-file ./testdata/build-kustomization/podinfo.yaml --path ./testdata/build-kustomization/var-substitution",
|
args: "build kustomization podinfo --kustomization-file " + tmpFile + " --path ./testdata/build-kustomization/var-substitution",
|
||||||
resultFile: "./testdata/build-kustomization/podinfo-with-var-substitution-result.yaml",
|
resultFile: "./testdata/build-kustomization/podinfo-with-var-substitution-result.yaml",
|
||||||
assertFunc: "assertGoldenTemplateFile",
|
assertFunc: "assertGoldenTemplateFile",
|
||||||
},
|
},
|
||||||
{
|
{
|
||||||
name: "build deployment and configmap with var substitution in dry-run mode",
|
name: "build deployment and configmap with var substitution in dry-run mode",
|
||||||
args: "build kustomization podinfo --kustomization-file ./testdata/build-kustomization/podinfo.yaml --path ./testdata/build-kustomization/var-substitution --dry-run",
|
args: "build kustomization podinfo --kustomization-file " + tmpFile + " --path ./testdata/build-kustomization/var-substitution --dry-run",
|
||||||
resultFile: "./testdata/build-kustomization/podinfo-with-var-substitution-result.yaml",
|
resultFile: "./testdata/build-kustomization/podinfo-with-var-substitution-result.yaml",
|
||||||
assertFunc: "assertGoldenTemplateFile",
|
assertFunc: "assertGoldenTemplateFile",
|
||||||
},
|
},
|
||||||
|
{
|
||||||
|
name: "build with recursive",
|
||||||
|
args: "build kustomization podinfo --kustomization-file " + tmpFile + " --path ./testdata/build-kustomization/podinfo-with-my-app --recursive --local-sources GitRepository/default/podinfo=./testdata/build-kustomization",
|
||||||
|
resultFile: "./testdata/build-kustomization/podinfo-with-my-app-result.yaml",
|
||||||
|
assertFunc: "assertGoldenTemplateFile",
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "build with recursive in dry-run mode",
|
||||||
|
args: "build kustomization podinfo --kustomization-file " + tmpFile + " --path ./testdata/build-kustomization/podinfo-with-my-app --recursive --local-sources GitRepository/default/podinfo=./testdata/build-kustomization --dry-run",
|
||||||
|
resultFile: "./testdata/build-kustomization/podinfo-with-my-app-result.yaml",
|
||||||
|
assertFunc: "assertGoldenTemplateFile",
|
||||||
|
},
|
||||||
}
|
}
|
||||||
|
|
||||||
tmpl := map[string]string{
|
tmpl := map[string]string{
|
||||||
|
|
@ -161,8 +182,6 @@ spec:
|
||||||
}
|
}
|
||||||
setup(t, tmpl)
|
setup(t, tmpl)
|
||||||
|
|
||||||
testEnv.CreateObjectFile("./testdata/build-kustomization/podinfo-source.yaml", tmpl, t)
|
|
||||||
|
|
||||||
temp, err := template.New("podinfo").Parse(podinfo)
|
temp, err := template.New("podinfo").Parse(podinfo)
|
||||||
if err != nil {
|
if err != nil {
|
||||||
t.Fatal(err)
|
t.Fatal(err)
|
||||||
|
|
@ -174,11 +193,10 @@ spec:
|
||||||
t.Fatal(err)
|
t.Fatal(err)
|
||||||
}
|
}
|
||||||
|
|
||||||
err = os.WriteFile("./testdata/build-kustomization/podinfo.yaml", b.Bytes(), 0666)
|
err = os.WriteFile(tmpFile, b.Bytes(), 0666)
|
||||||
if err != nil {
|
if err != nil {
|
||||||
t.Fatal(err)
|
t.Fatal(err)
|
||||||
}
|
}
|
||||||
t.Cleanup(func() { _ = os.Remove("./testdata/build-kustomization/podinfo.yaml") })
|
|
||||||
|
|
||||||
for _, tt := range tests {
|
for _, tt := range tests {
|
||||||
t.Run(tt.name, func(t *testing.T) {
|
t.Run(tt.name, func(t *testing.T) {
|
||||||
|
|
|
||||||
|
|
@ -40,6 +40,7 @@ import (
|
||||||
|
|
||||||
var checkCmd = &cobra.Command{
|
var checkCmd = &cobra.Command{
|
||||||
Use: "check",
|
Use: "check",
|
||||||
|
Args: cobra.NoArgs,
|
||||||
Short: "Check requirements and installation",
|
Short: "Check requirements and installation",
|
||||||
Long: withPreviewNote(`The check command will perform a series of checks to validate that
|
Long: withPreviewNote(`The check command will perform a series of checks to validate that
|
||||||
the local environment is configured correctly and if the installed components are healthy.`),
|
the local environment is configured correctly and if the installed components are healthy.`),
|
||||||
|
|
@ -59,7 +60,7 @@ type checkFlags struct {
|
||||||
}
|
}
|
||||||
|
|
||||||
var kubernetesConstraints = []string{
|
var kubernetesConstraints = []string{
|
||||||
">=1.26.0-0",
|
">=1.31.0-0",
|
||||||
}
|
}
|
||||||
|
|
||||||
var checkArgs checkFlags
|
var checkArgs checkFlags
|
||||||
|
|
@ -216,7 +217,7 @@ func componentsCheck(ctx context.Context, kubeClient client.Client) bool {
|
||||||
}
|
}
|
||||||
}
|
}
|
||||||
for _, c := range d.Spec.Template.Spec.Containers {
|
for _, c := range d.Spec.Template.Spec.Containers {
|
||||||
logger.Actionf(c.Image)
|
logger.Actionf("%s", c.Image)
|
||||||
}
|
}
|
||||||
}
|
}
|
||||||
}
|
}
|
||||||
|
|
@ -237,7 +238,7 @@ func crdsCheck(ctx context.Context, kubeClient client.Client) bool {
|
||||||
for _, crd := range list.Items {
|
for _, crd := range list.Items {
|
||||||
versions := crd.Status.StoredVersions
|
versions := crd.Status.StoredVersions
|
||||||
if len(versions) > 0 {
|
if len(versions) > 0 {
|
||||||
logger.Successf(crd.Name + "/" + versions[len(versions)-1])
|
logger.Successf("%s", crd.Name+"/"+versions[len(versions)-1])
|
||||||
} else {
|
} else {
|
||||||
ok = false
|
ok = false
|
||||||
logger.Failuref("no stored versions for %s", crd.Name)
|
logger.Failuref("no stored versions for %s", crd.Name)
|
||||||
|
|
|
||||||
|
|
@ -29,7 +29,7 @@ import (
|
||||||
"sigs.k8s.io/controller-runtime/pkg/client/fake"
|
"sigs.k8s.io/controller-runtime/pkg/client/fake"
|
||||||
|
|
||||||
kustomizev1 "github.com/fluxcd/kustomize-controller/api/v1"
|
kustomizev1 "github.com/fluxcd/kustomize-controller/api/v1"
|
||||||
"github.com/fluxcd/pkg/ssa"
|
ssautil "github.com/fluxcd/pkg/ssa/utils"
|
||||||
)
|
)
|
||||||
|
|
||||||
func Test_getFluxClusterInfo(t *testing.T) {
|
func Test_getFluxClusterInfo(t *testing.T) {
|
||||||
|
|
@ -37,7 +37,7 @@ func Test_getFluxClusterInfo(t *testing.T) {
|
||||||
f, err := os.Open("./testdata/cluster_info/gitrepositories.yaml")
|
f, err := os.Open("./testdata/cluster_info/gitrepositories.yaml")
|
||||||
g.Expect(err).To(BeNil())
|
g.Expect(err).To(BeNil())
|
||||||
|
|
||||||
objs, err := ssa.ReadObjects(f)
|
objs, err := ssautil.ReadObjects(f)
|
||||||
g.Expect(err).To(Not(HaveOccurred()))
|
g.Expect(err).To(Not(HaveOccurred()))
|
||||||
gitrepo := objs[0]
|
gitrepo := objs[0]
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -125,7 +125,7 @@ func (names apiType) upsertAndWait(object upsertWaitable, mutate func() error) e
|
||||||
logger.Generatef("generating %s", names.kind)
|
logger.Generatef("generating %s", names.kind)
|
||||||
logger.Actionf("applying %s", names.kind)
|
logger.Actionf("applying %s", names.kind)
|
||||||
|
|
||||||
namespacedName, err := imageRepositoryType.upsert(ctx, kubeClient, object, mutate)
|
namespacedName, err := names.upsert(ctx, kubeClient, object, mutate)
|
||||||
if err != nil {
|
if err != nil {
|
||||||
return err
|
return err
|
||||||
}
|
}
|
||||||
|
|
|
||||||
|
|
@ -1,5 +1,5 @@
|
||||||
/*
|
/*
|
||||||
Copyright 2020 The Flux authors
|
Copyright 2024 The Flux authors
|
||||||
|
|
||||||
Licensed under the Apache License, Version 2.0 (the "License");
|
Licensed under the Apache License, Version 2.0 (the "License");
|
||||||
you may not use this file except in compliance with the License.
|
you may not use this file except in compliance with the License.
|
||||||
|
|
@ -24,12 +24,6 @@ import (
|
||||||
"strings"
|
"strings"
|
||||||
"time"
|
"time"
|
||||||
|
|
||||||
"github.com/fluxcd/pkg/apis/meta"
|
|
||||||
"github.com/fluxcd/pkg/runtime/transform"
|
|
||||||
|
|
||||||
"github.com/fluxcd/flux2/v2/internal/flags"
|
|
||||||
"github.com/fluxcd/flux2/v2/internal/utils"
|
|
||||||
|
|
||||||
"github.com/spf13/cobra"
|
"github.com/spf13/cobra"
|
||||||
apiextensionsv1 "k8s.io/apiextensions-apiserver/pkg/apis/apiextensions/v1"
|
apiextensionsv1 "k8s.io/apiextensions-apiserver/pkg/apis/apiextensions/v1"
|
||||||
"k8s.io/apimachinery/pkg/api/errors"
|
"k8s.io/apimachinery/pkg/api/errors"
|
||||||
|
|
@ -39,14 +33,20 @@ import (
|
||||||
"sigs.k8s.io/controller-runtime/pkg/client"
|
"sigs.k8s.io/controller-runtime/pkg/client"
|
||||||
"sigs.k8s.io/yaml"
|
"sigs.k8s.io/yaml"
|
||||||
|
|
||||||
helmv2 "github.com/fluxcd/helm-controller/api/v2beta2"
|
helmv2 "github.com/fluxcd/helm-controller/api/v2"
|
||||||
|
"github.com/fluxcd/pkg/apis/meta"
|
||||||
|
"github.com/fluxcd/pkg/runtime/transform"
|
||||||
|
sourcev1 "github.com/fluxcd/source-controller/api/v1"
|
||||||
|
|
||||||
|
"github.com/fluxcd/flux2/v2/internal/flags"
|
||||||
|
"github.com/fluxcd/flux2/v2/internal/utils"
|
||||||
)
|
)
|
||||||
|
|
||||||
var createHelmReleaseCmd = &cobra.Command{
|
var createHelmReleaseCmd = &cobra.Command{
|
||||||
Use: "helmrelease [name]",
|
Use: "helmrelease [name]",
|
||||||
Aliases: []string{"hr"},
|
Aliases: []string{"hr"},
|
||||||
Short: "Create or update a HelmRelease resource",
|
Short: "Create or update a HelmRelease resource",
|
||||||
Long: withPreviewNote(`The helmrelease create command generates a HelmRelease resource for a given HelmRepository source.`),
|
Long: `The helmrelease create command generates a HelmRelease resource for a given HelmRepository source.`,
|
||||||
Example: ` # Create a HelmRelease with a chart from a HelmRepository source
|
Example: ` # Create a HelmRelease with a chart from a HelmRepository source
|
||||||
flux create hr podinfo \
|
flux create hr podinfo \
|
||||||
--interval=10m \
|
--interval=10m \
|
||||||
|
|
@ -105,7 +105,17 @@ var createHelmReleaseCmd = &cobra.Command{
|
||||||
--source=HelmRepository/podinfo \
|
--source=HelmRepository/podinfo \
|
||||||
--chart=podinfo \
|
--chart=podinfo \
|
||||||
--values=./values.yaml \
|
--values=./values.yaml \
|
||||||
--export > podinfo-release.yaml`,
|
--export > podinfo-release.yaml
|
||||||
|
|
||||||
|
# Create a HelmRelease using a chart from a HelmChart resource
|
||||||
|
flux create hr podinfo \
|
||||||
|
--namespace=default \
|
||||||
|
--chart-ref=HelmChart/podinfo.flux-system \
|
||||||
|
|
||||||
|
# Create a HelmRelease using a chart from an OCIRepository resource
|
||||||
|
flux create hr podinfo \
|
||||||
|
--namespace=default \
|
||||||
|
--chart-ref=OCIRepository/podinfo.flux-system`,
|
||||||
RunE: createHelmReleaseCmdRun,
|
RunE: createHelmReleaseCmdRun,
|
||||||
}
|
}
|
||||||
|
|
||||||
|
|
@ -115,6 +125,7 @@ type helmReleaseFlags struct {
|
||||||
dependsOn []string
|
dependsOn []string
|
||||||
chart string
|
chart string
|
||||||
chartVersion string
|
chartVersion string
|
||||||
|
chartRef string
|
||||||
targetNamespace string
|
targetNamespace string
|
||||||
createNamespace bool
|
createNamespace bool
|
||||||
valuesFiles []string
|
valuesFiles []string
|
||||||
|
|
@ -130,6 +141,8 @@ var helmReleaseArgs helmReleaseFlags
|
||||||
|
|
||||||
var supportedHelmReleaseValuesFromKinds = []string{"Secret", "ConfigMap"}
|
var supportedHelmReleaseValuesFromKinds = []string{"Secret", "ConfigMap"}
|
||||||
|
|
||||||
|
var supportedHelmReleaseReferenceKinds = []string{sourcev1.OCIRepositoryKind, sourcev1.HelmChartKind}
|
||||||
|
|
||||||
func init() {
|
func init() {
|
||||||
createHelmReleaseCmd.Flags().StringVar(&helmReleaseArgs.name, "release-name", "", "name used for the Helm release, defaults to a composition of '[<target-namespace>-]<HelmRelease-name>'")
|
createHelmReleaseCmd.Flags().StringVar(&helmReleaseArgs.name, "release-name", "", "name used for the Helm release, defaults to a composition of '[<target-namespace>-]<HelmRelease-name>'")
|
||||||
createHelmReleaseCmd.Flags().Var(&helmReleaseArgs.source, "source", helmReleaseArgs.source.Description())
|
createHelmReleaseCmd.Flags().Var(&helmReleaseArgs.source, "source", helmReleaseArgs.source.Description())
|
||||||
|
|
@ -145,14 +158,15 @@ func init() {
|
||||||
createHelmReleaseCmd.Flags().StringSliceVar(&helmReleaseArgs.valuesFrom, "values-from", nil, "a Kubernetes object reference that contains the values.yaml data key in the format '<kind>/<name>', where kind must be one of: (Secret,ConfigMap)")
|
createHelmReleaseCmd.Flags().StringSliceVar(&helmReleaseArgs.valuesFrom, "values-from", nil, "a Kubernetes object reference that contains the values.yaml data key in the format '<kind>/<name>', where kind must be one of: (Secret,ConfigMap)")
|
||||||
createHelmReleaseCmd.Flags().Var(&helmReleaseArgs.crds, "crds", helmReleaseArgs.crds.Description())
|
createHelmReleaseCmd.Flags().Var(&helmReleaseArgs.crds, "crds", helmReleaseArgs.crds.Description())
|
||||||
createHelmReleaseCmd.Flags().StringVar(&helmReleaseArgs.kubeConfigSecretRef, "kubeconfig-secret-ref", "", "the name of the Kubernetes Secret that contains a key with the kubeconfig file for connecting to a remote cluster")
|
createHelmReleaseCmd.Flags().StringVar(&helmReleaseArgs.kubeConfigSecretRef, "kubeconfig-secret-ref", "", "the name of the Kubernetes Secret that contains a key with the kubeconfig file for connecting to a remote cluster")
|
||||||
|
createHelmReleaseCmd.Flags().StringVar(&helmReleaseArgs.chartRef, "chart-ref", "", "the name of the HelmChart resource to use as source for the HelmRelease, in the format '<kind>/<name>.<namespace>', where kind must be one of: (OCIRepository,HelmChart)")
|
||||||
createCmd.AddCommand(createHelmReleaseCmd)
|
createCmd.AddCommand(createHelmReleaseCmd)
|
||||||
}
|
}
|
||||||
|
|
||||||
func createHelmReleaseCmdRun(cmd *cobra.Command, args []string) error {
|
func createHelmReleaseCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
name := args[0]
|
name := args[0]
|
||||||
|
|
||||||
if helmReleaseArgs.chart == "" {
|
if helmReleaseArgs.chart == "" && helmReleaseArgs.chartRef == "" {
|
||||||
return fmt.Errorf("chart name or path is required")
|
return fmt.Errorf("chart or chart-ref is required")
|
||||||
}
|
}
|
||||||
|
|
||||||
sourceLabels, err := parseLabels()
|
sourceLabels, err := parseLabels()
|
||||||
|
|
@ -182,37 +196,50 @@ func createHelmReleaseCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
Duration: createArgs.interval,
|
Duration: createArgs.interval,
|
||||||
},
|
},
|
||||||
TargetNamespace: helmReleaseArgs.targetNamespace,
|
TargetNamespace: helmReleaseArgs.targetNamespace,
|
||||||
|
Suspend: false,
|
||||||
Chart: helmv2.HelmChartTemplate{
|
|
||||||
Spec: helmv2.HelmChartTemplateSpec{
|
|
||||||
Chart: helmReleaseArgs.chart,
|
|
||||||
Version: helmReleaseArgs.chartVersion,
|
|
||||||
SourceRef: helmv2.CrossNamespaceObjectReference{
|
|
||||||
Kind: helmReleaseArgs.source.Kind,
|
|
||||||
Name: helmReleaseArgs.source.Name,
|
|
||||||
Namespace: helmReleaseArgs.source.Namespace,
|
|
||||||
},
|
|
||||||
ReconcileStrategy: helmReleaseArgs.reconcileStrategy,
|
|
||||||
},
|
|
||||||
},
|
|
||||||
Suspend: false,
|
|
||||||
},
|
},
|
||||||
}
|
}
|
||||||
|
|
||||||
|
switch {
|
||||||
|
case helmReleaseArgs.chart != "":
|
||||||
|
helmRelease.Spec.Chart = &helmv2.HelmChartTemplate{
|
||||||
|
Spec: helmv2.HelmChartTemplateSpec{
|
||||||
|
Chart: helmReleaseArgs.chart,
|
||||||
|
Version: helmReleaseArgs.chartVersion,
|
||||||
|
SourceRef: helmv2.CrossNamespaceObjectReference{
|
||||||
|
Kind: helmReleaseArgs.source.Kind,
|
||||||
|
Name: helmReleaseArgs.source.Name,
|
||||||
|
Namespace: helmReleaseArgs.source.Namespace,
|
||||||
|
},
|
||||||
|
ReconcileStrategy: helmReleaseArgs.reconcileStrategy,
|
||||||
|
},
|
||||||
|
}
|
||||||
|
if helmReleaseArgs.chartInterval != 0 {
|
||||||
|
helmRelease.Spec.Chart.Spec.Interval = &metav1.Duration{
|
||||||
|
Duration: helmReleaseArgs.chartInterval,
|
||||||
|
}
|
||||||
|
}
|
||||||
|
case helmReleaseArgs.chartRef != "":
|
||||||
|
kind, name, ns := utils.ParseObjectKindNameNamespace(helmReleaseArgs.chartRef)
|
||||||
|
if kind != sourcev1.HelmChartKind && kind != sourcev1.OCIRepositoryKind {
|
||||||
|
return fmt.Errorf("chart reference kind '%s' is not supported, must be one of: %s",
|
||||||
|
kind, strings.Join(supportedHelmReleaseReferenceKinds, ", "))
|
||||||
|
}
|
||||||
|
helmRelease.Spec.ChartRef = &helmv2.CrossNamespaceSourceReference{
|
||||||
|
Kind: kind,
|
||||||
|
Name: name,
|
||||||
|
Namespace: ns,
|
||||||
|
}
|
||||||
|
}
|
||||||
|
|
||||||
if helmReleaseArgs.kubeConfigSecretRef != "" {
|
if helmReleaseArgs.kubeConfigSecretRef != "" {
|
||||||
helmRelease.Spec.KubeConfig = &meta.KubeConfigReference{
|
helmRelease.Spec.KubeConfig = &meta.KubeConfigReference{
|
||||||
SecretRef: meta.SecretKeyReference{
|
SecretRef: &meta.SecretKeyReference{
|
||||||
Name: helmReleaseArgs.kubeConfigSecretRef,
|
Name: helmReleaseArgs.kubeConfigSecretRef,
|
||||||
},
|
},
|
||||||
}
|
}
|
||||||
}
|
}
|
||||||
|
|
||||||
if helmReleaseArgs.chartInterval != 0 {
|
|
||||||
helmRelease.Spec.Chart.Spec.Interval = &metav1.Duration{
|
|
||||||
Duration: helmReleaseArgs.chartInterval,
|
|
||||||
}
|
|
||||||
}
|
|
||||||
|
|
||||||
if helmReleaseArgs.createNamespace {
|
if helmReleaseArgs.createNamespace {
|
||||||
if helmRelease.Spec.Install == nil {
|
if helmRelease.Spec.Install == nil {
|
||||||
helmRelease.Spec.Install = &helmv2.Install{}
|
helmRelease.Spec.Install = &helmv2.Install{}
|
||||||
|
|
@ -309,7 +336,7 @@ func createHelmReleaseCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
}
|
}
|
||||||
logger.Successf("HelmRelease %s is ready", name)
|
logger.Successf("HelmRelease %s is ready", name)
|
||||||
|
|
||||||
logger.Successf("applied revision %s", helmRelease.Status.LastAppliedRevision)
|
logger.Successf("applied revision %s", getHelmReleaseRevision(helmRelease))
|
||||||
return nil
|
return nil
|
||||||
}
|
}
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -0,0 +1,86 @@
|
||||||
|
//go:build unit
|
||||||
|
// +build unit
|
||||||
|
|
||||||
|
/*
|
||||||
|
Copyright 2024 The Flux authors
|
||||||
|
|
||||||
|
Licensed under the Apache License, Version 2.0 (the "License");
|
||||||
|
you may not use this file except in compliance with the License.
|
||||||
|
You may obtain a copy of the License at
|
||||||
|
|
||||||
|
http://www.apache.org/licenses/LICENSE-2.0
|
||||||
|
|
||||||
|
Unless required by applicable law or agreed to in writing, software
|
||||||
|
distributed under the License is distributed on an "AS IS" BASIS,
|
||||||
|
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||||
|
See the License for the specific language governing permissions and
|
||||||
|
limitations under the License.
|
||||||
|
*/
|
||||||
|
|
||||||
|
package main
|
||||||
|
|
||||||
|
import "testing"
|
||||||
|
|
||||||
|
func TestCreateHelmRelease(t *testing.T) {
|
||||||
|
tmpl := map[string]string{
|
||||||
|
"fluxns": allocateNamespace("flux-system"),
|
||||||
|
}
|
||||||
|
setupHRSource(t, tmpl)
|
||||||
|
|
||||||
|
tests := []struct {
|
||||||
|
name string
|
||||||
|
args string
|
||||||
|
assert assertFunc
|
||||||
|
}{
|
||||||
|
{
|
||||||
|
name: "missing name",
|
||||||
|
args: "create helmrelease --export",
|
||||||
|
assert: assertError("name is required"),
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "missing chart template and chartRef",
|
||||||
|
args: "create helmrelease podinfo --export",
|
||||||
|
assert: assertError("chart or chart-ref is required"),
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "unknown source kind",
|
||||||
|
args: "create helmrelease podinfo --source foobar/podinfo --chart podinfo --export",
|
||||||
|
assert: assertError(`invalid argument "foobar/podinfo" for "--source" flag: source kind 'foobar' is not supported, must be one of: HelmRepository, GitRepository, Bucket`),
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "unknown chart reference kind",
|
||||||
|
args: "create helmrelease podinfo --chart-ref foobar/podinfo --export",
|
||||||
|
assert: assertError(`chart reference kind 'foobar' is not supported, must be one of: OCIRepository, HelmChart`),
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "basic helmrelease",
|
||||||
|
args: "create helmrelease podinfo --source Helmrepository/podinfo --chart podinfo --interval=1m0s --export",
|
||||||
|
assert: assertGoldenTemplateFile("testdata/create_hr/basic.yaml", tmpl),
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "chart with OCIRepository source",
|
||||||
|
args: "create helmrelease podinfo --chart-ref OCIRepository/podinfo --interval=1m0s --export",
|
||||||
|
assert: assertGoldenTemplateFile("testdata/create_hr/or_basic.yaml", tmpl),
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "chart with HelmChart source",
|
||||||
|
args: "create helmrelease podinfo --chart-ref HelmChart/podinfo --interval=1m0s --export",
|
||||||
|
assert: assertGoldenTemplateFile("testdata/create_hr/hc_basic.yaml", tmpl),
|
||||||
|
},
|
||||||
|
}
|
||||||
|
|
||||||
|
for _, tt := range tests {
|
||||||
|
t.Run(tt.name, func(t *testing.T) {
|
||||||
|
cmd := cmdTestCase{
|
||||||
|
args: tt.args + " -n " + tmpl["fluxns"],
|
||||||
|
assert: tt.assert,
|
||||||
|
}
|
||||||
|
cmd.runTestCmd(t)
|
||||||
|
})
|
||||||
|
}
|
||||||
|
}
|
||||||
|
|
||||||
|
func setupHRSource(t *testing.T, tmpl map[string]string) {
|
||||||
|
t.Helper()
|
||||||
|
testEnv.CreateObjectFile("./testdata/create_hr/setup-source.yaml", tmpl, t)
|
||||||
|
}
|
||||||
|
|
@ -20,6 +20,7 @@ import (
|
||||||
"fmt"
|
"fmt"
|
||||||
"regexp/syntax"
|
"regexp/syntax"
|
||||||
"strings"
|
"strings"
|
||||||
|
"time"
|
||||||
"unicode"
|
"unicode"
|
||||||
"unicode/utf8"
|
"unicode/utf8"
|
||||||
|
|
||||||
|
|
@ -34,12 +35,12 @@ import (
|
||||||
var createImagePolicyCmd = &cobra.Command{
|
var createImagePolicyCmd = &cobra.Command{
|
||||||
Use: "policy [name]",
|
Use: "policy [name]",
|
||||||
Short: "Create or update an ImagePolicy object",
|
Short: "Create or update an ImagePolicy object",
|
||||||
Long: withPreviewNote(`The create image policy command generates an ImagePolicy resource.
|
Long: `The create image policy command generates an ImagePolicy resource.
|
||||||
An ImagePolicy object calculates a "latest image" given an image
|
An ImagePolicy object calculates a "latest image" given an image
|
||||||
repository and a policy, e.g., semver.
|
repository and a policy, e.g., semver.
|
||||||
|
|
||||||
The image that sorts highest according to the policy is recorded in
|
The image that sorts highest according to the policy is recorded in
|
||||||
the status of the object.`),
|
the status of the object.`,
|
||||||
Example: ` # Create an ImagePolicy to select the latest stable release
|
Example: ` # Create an ImagePolicy to select the latest stable release
|
||||||
flux create image policy podinfo \
|
flux create image policy podinfo \
|
||||||
--image-ref=podinfo \
|
--image-ref=podinfo \
|
||||||
|
|
@ -60,6 +61,8 @@ type imagePolicyFlags struct {
|
||||||
numeric string
|
numeric string
|
||||||
filterRegex string
|
filterRegex string
|
||||||
filterExtract string
|
filterExtract string
|
||||||
|
reflectDigest string
|
||||||
|
interval time.Duration
|
||||||
}
|
}
|
||||||
|
|
||||||
var imagePolicyArgs = imagePolicyFlags{}
|
var imagePolicyArgs = imagePolicyFlags{}
|
||||||
|
|
@ -72,6 +75,8 @@ func init() {
|
||||||
flags.StringVar(&imagePolicyArgs.numeric, "select-numeric", "", "use numeric sorting to select image; either \"asc\" meaning select the last, or \"desc\" meaning select the first")
|
flags.StringVar(&imagePolicyArgs.numeric, "select-numeric", "", "use numeric sorting to select image; either \"asc\" meaning select the last, or \"desc\" meaning select the first")
|
||||||
flags.StringVar(&imagePolicyArgs.filterRegex, "filter-regex", "", "regular expression pattern used to filter the image tags")
|
flags.StringVar(&imagePolicyArgs.filterRegex, "filter-regex", "", "regular expression pattern used to filter the image tags")
|
||||||
flags.StringVar(&imagePolicyArgs.filterExtract, "filter-extract", "", "replacement pattern (using capture groups from --filter-regex) to use for sorting")
|
flags.StringVar(&imagePolicyArgs.filterExtract, "filter-extract", "", "replacement pattern (using capture groups from --filter-regex) to use for sorting")
|
||||||
|
flags.StringVar(&imagePolicyArgs.reflectDigest, "reflect-digest", "", "the digest reflection policy to use when observing latest image tags (one of 'Never', 'IfNotPresent', 'Never')")
|
||||||
|
flags.DurationVar(&imagePolicyArgs.interval, "interval", 0, "the interval at which to check for new image digests when the policy is set to 'Always'")
|
||||||
|
|
||||||
createImageCmd.AddCommand(createImagePolicyCmd)
|
createImageCmd.AddCommand(createImagePolicyCmd)
|
||||||
}
|
}
|
||||||
|
|
@ -153,6 +158,20 @@ func createImagePolicyRun(cmd *cobra.Command, args []string) error {
|
||||||
return fmt.Errorf("cannot specify --filter-extract without specifying --filter-regex")
|
return fmt.Errorf("cannot specify --filter-extract without specifying --filter-regex")
|
||||||
}
|
}
|
||||||
|
|
||||||
|
if p := imagev1.ReflectionPolicy(imagePolicyArgs.reflectDigest); p != "" {
|
||||||
|
if p != imagev1.ReflectNever && p != imagev1.ReflectIfNotPresent && p != imagev1.ReflectAlways {
|
||||||
|
return fmt.Errorf("invalid value for --reflect-digest, must be one of 'Never', 'IfNotPresent', 'Always'")
|
||||||
|
}
|
||||||
|
policy.Spec.DigestReflectionPolicy = p
|
||||||
|
}
|
||||||
|
|
||||||
|
if imagePolicyArgs.interval != 0 {
|
||||||
|
if imagePolicyArgs.reflectDigest != string(imagev1.ReflectAlways) {
|
||||||
|
return fmt.Errorf("the --interval flag can only be used with the 'Always' digest reflection policy, use --reflect-digest=Always")
|
||||||
|
}
|
||||||
|
policy.Spec.Interval = &metav1.Duration{Duration: imagePolicyArgs.interval}
|
||||||
|
}
|
||||||
|
|
||||||
if createArgs.export {
|
if createArgs.export {
|
||||||
return printExport(exportImagePolicy(&policy))
|
return printExport(exportImagePolicy(&policy))
|
||||||
}
|
}
|
||||||
|
|
|
||||||
|
|
@ -32,8 +32,8 @@ import (
|
||||||
var createImageRepositoryCmd = &cobra.Command{
|
var createImageRepositoryCmd = &cobra.Command{
|
||||||
Use: "repository [name]",
|
Use: "repository [name]",
|
||||||
Short: "Create or update an ImageRepository object",
|
Short: "Create or update an ImageRepository object",
|
||||||
Long: withPreviewNote(`The create image repository command generates an ImageRepository resource.
|
Long: `The create image repository command generates an ImageRepository resource.
|
||||||
An ImageRepository object specifies an image repository to scan.`),
|
An ImageRepository object specifies an image repository to scan.`,
|
||||||
Example: ` # Create an ImageRepository object to scan the alpine image repository:
|
Example: ` # Create an ImageRepository object to scan the alpine image repository:
|
||||||
flux create image repository alpine-repo --image alpine --interval 20m
|
flux create image repository alpine-repo --image alpine --interval 20m
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -22,16 +22,16 @@ import (
|
||||||
"github.com/spf13/cobra"
|
"github.com/spf13/cobra"
|
||||||
metav1 "k8s.io/apimachinery/pkg/apis/meta/v1"
|
metav1 "k8s.io/apimachinery/pkg/apis/meta/v1"
|
||||||
|
|
||||||
autov1 "github.com/fluxcd/image-automation-controller/api/v1beta1"
|
autov1 "github.com/fluxcd/image-automation-controller/api/v1beta2"
|
||||||
sourcev1 "github.com/fluxcd/source-controller/api/v1"
|
sourcev1 "github.com/fluxcd/source-controller/api/v1"
|
||||||
)
|
)
|
||||||
|
|
||||||
var createImageUpdateCmd = &cobra.Command{
|
var createImageUpdateCmd = &cobra.Command{
|
||||||
Use: "update [name]",
|
Use: "update [name]",
|
||||||
Short: "Create or update an ImageUpdateAutomation object",
|
Short: "Create or update an ImageUpdateAutomation object",
|
||||||
Long: withPreviewNote(`The create image update command generates an ImageUpdateAutomation resource.
|
Long: `The create image update command generates an ImageUpdateAutomation resource.
|
||||||
An ImageUpdateAutomation object specifies an automated update to images
|
An ImageUpdateAutomation object specifies an automated update to images
|
||||||
mentioned in YAMLs in a git repository.`),
|
mentioned in YAMLs in a git repository.`,
|
||||||
Example: ` # Configure image updates for the main repository created by flux bootstrap
|
Example: ` # Configure image updates for the main repository created by flux bootstrap
|
||||||
flux create image update flux-system \
|
flux create image update flux-system \
|
||||||
--git-repo-ref=flux-system \
|
--git-repo-ref=flux-system \
|
||||||
|
|
|
||||||
|
|
@ -29,7 +29,7 @@ import (
|
||||||
"k8s.io/apimachinery/pkg/util/wait"
|
"k8s.io/apimachinery/pkg/util/wait"
|
||||||
"sigs.k8s.io/controller-runtime/pkg/client"
|
"sigs.k8s.io/controller-runtime/pkg/client"
|
||||||
|
|
||||||
helmv2 "github.com/fluxcd/helm-controller/api/v2beta2"
|
helmv2 "github.com/fluxcd/helm-controller/api/v2"
|
||||||
kustomizev1 "github.com/fluxcd/kustomize-controller/api/v1"
|
kustomizev1 "github.com/fluxcd/kustomize-controller/api/v1"
|
||||||
"github.com/fluxcd/pkg/apis/meta"
|
"github.com/fluxcd/pkg/apis/meta"
|
||||||
|
|
||||||
|
|
@ -171,7 +171,7 @@ func createKsCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
|
|
||||||
if kustomizationArgs.kubeConfigSecretRef != "" {
|
if kustomizationArgs.kubeConfigSecretRef != "" {
|
||||||
kustomization.Spec.KubeConfig = &meta.KubeConfigReference{
|
kustomization.Spec.KubeConfig = &meta.KubeConfigReference{
|
||||||
SecretRef: meta.SecretKeyReference{
|
SecretRef: &meta.SecretKeyReference{
|
||||||
Name: kustomizationArgs.kubeConfigSecretRef,
|
Name: kustomizationArgs.kubeConfigSecretRef,
|
||||||
},
|
},
|
||||||
}
|
}
|
||||||
|
|
|
||||||
|
|
@ -87,7 +87,6 @@ type secretGitFlags struct {
|
||||||
keyAlgorithm flags.PublicKeyAlgorithm
|
keyAlgorithm flags.PublicKeyAlgorithm
|
||||||
rsaBits flags.RSAKeyBits
|
rsaBits flags.RSAKeyBits
|
||||||
ecdsaCurve flags.ECDSACurve
|
ecdsaCurve flags.ECDSACurve
|
||||||
caFile string
|
|
||||||
caCrtFile string
|
caCrtFile string
|
||||||
privateKeyFile string
|
privateKeyFile string
|
||||||
bearerToken string
|
bearerToken string
|
||||||
|
|
@ -102,8 +101,7 @@ func init() {
|
||||||
createSecretGitCmd.Flags().Var(&secretGitArgs.keyAlgorithm, "ssh-key-algorithm", secretGitArgs.keyAlgorithm.Description())
|
createSecretGitCmd.Flags().Var(&secretGitArgs.keyAlgorithm, "ssh-key-algorithm", secretGitArgs.keyAlgorithm.Description())
|
||||||
createSecretGitCmd.Flags().Var(&secretGitArgs.rsaBits, "ssh-rsa-bits", secretGitArgs.rsaBits.Description())
|
createSecretGitCmd.Flags().Var(&secretGitArgs.rsaBits, "ssh-rsa-bits", secretGitArgs.rsaBits.Description())
|
||||||
createSecretGitCmd.Flags().Var(&secretGitArgs.ecdsaCurve, "ssh-ecdsa-curve", secretGitArgs.ecdsaCurve.Description())
|
createSecretGitCmd.Flags().Var(&secretGitArgs.ecdsaCurve, "ssh-ecdsa-curve", secretGitArgs.ecdsaCurve.Description())
|
||||||
createSecretGitCmd.Flags().StringVar(&secretGitArgs.caFile, "ca-file", "", "path to TLS CA file used for validating self-signed certificates")
|
createSecretGitCmd.Flags().StringVar(&secretGitArgs.caCrtFile, "ca-crt-file", "", "path to TLS CA certificate file used for validating self-signed certificates")
|
||||||
createSecretGitCmd.Flags().StringVar(&secretGitArgs.caCrtFile, "ca-crt-file", "", "path to TLS CA certificate file used for validating self-signed certificates; takes precedence over --ca-file")
|
|
||||||
createSecretGitCmd.Flags().StringVar(&secretGitArgs.privateKeyFile, "private-key-file", "", "path to a passwordless private key file used for authenticating to the Git SSH server")
|
createSecretGitCmd.Flags().StringVar(&secretGitArgs.privateKeyFile, "private-key-file", "", "path to a passwordless private key file used for authenticating to the Git SSH server")
|
||||||
createSecretGitCmd.Flags().StringVar(&secretGitArgs.bearerToken, "bearer-token", "", "bearer authentication token")
|
createSecretGitCmd.Flags().StringVar(&secretGitArgs.bearerToken, "bearer-token", "", "bearer authentication token")
|
||||||
|
|
||||||
|
|
@ -169,17 +167,12 @@ func createSecretGitCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
if err != nil {
|
if err != nil {
|
||||||
return fmt.Errorf("unable to read TLS CA file: %w", err)
|
return fmt.Errorf("unable to read TLS CA file: %w", err)
|
||||||
}
|
}
|
||||||
} else if secretGitArgs.caFile != "" {
|
|
||||||
opts.CAFile, err = os.ReadFile(secretGitArgs.caFile)
|
|
||||||
if err != nil {
|
|
||||||
return fmt.Errorf("unable to read TLS CA file: %w", err)
|
|
||||||
}
|
|
||||||
}
|
}
|
||||||
default:
|
default:
|
||||||
return fmt.Errorf("git URL scheme '%s' not supported, can be: ssh, http and https", u.Scheme)
|
return fmt.Errorf("git URL scheme '%s' not supported, can be: ssh, http and https", u.Scheme)
|
||||||
}
|
}
|
||||||
|
|
||||||
secret, err := sourcesecret.Generate(opts)
|
secret, err := sourcesecret.GenerateGit(opts)
|
||||||
if err != nil {
|
if err != nil {
|
||||||
return err
|
return err
|
||||||
}
|
}
|
||||||
|
|
|
||||||
|
|
@ -0,0 +1,128 @@
|
||||||
|
/*
|
||||||
|
Copyright 2024 The Flux authors
|
||||||
|
|
||||||
|
Licensed under the Apache License, Version 2.0 (the "License");
|
||||||
|
you may not use this file except in compliance with the License.
|
||||||
|
You may obtain a copy of the License at
|
||||||
|
|
||||||
|
http://www.apache.org/licenses/LICENSE-2.0
|
||||||
|
|
||||||
|
Unless required by applicable law or agreed to in writing, software
|
||||||
|
distributed under the License is distributed on an "AS IS" BASIS,
|
||||||
|
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||||
|
See the License for the specific language governing permissions and
|
||||||
|
limitations under the License.
|
||||||
|
*/
|
||||||
|
|
||||||
|
package main
|
||||||
|
|
||||||
|
import (
|
||||||
|
"context"
|
||||||
|
"fmt"
|
||||||
|
"os"
|
||||||
|
|
||||||
|
"github.com/fluxcd/flux2/v2/internal/utils"
|
||||||
|
"github.com/fluxcd/flux2/v2/pkg/manifestgen/sourcesecret"
|
||||||
|
"github.com/spf13/cobra"
|
||||||
|
corev1 "k8s.io/api/core/v1"
|
||||||
|
"sigs.k8s.io/yaml"
|
||||||
|
)
|
||||||
|
|
||||||
|
var createSecretGitHubAppCmd = &cobra.Command{
|
||||||
|
Use: "githubapp [name]",
|
||||||
|
Short: "Create or update a github app secret",
|
||||||
|
Long: withPreviewNote(`The create secret githubapp command generates a Kubernetes secret that can be used for GitRepository authentication with github app`),
|
||||||
|
Example: ` # Create a githubapp authentication secret on disk and encrypt it with Mozilla SOPS
|
||||||
|
flux create secret githubapp podinfo-auth \
|
||||||
|
--app-id="1" \
|
||||||
|
--app-installation-id="2" \
|
||||||
|
--app-private-key=./private-key-file.pem \
|
||||||
|
--export > githubapp-auth.yaml
|
||||||
|
|
||||||
|
sops --encrypt --encrypted-regex '^(data|stringData)$' \
|
||||||
|
--in-place githubapp-auth.yaml
|
||||||
|
`,
|
||||||
|
RunE: createSecretGitHubAppCmdRun,
|
||||||
|
}
|
||||||
|
|
||||||
|
type secretGitHubAppFlags struct {
|
||||||
|
appID string
|
||||||
|
appInstallationID string
|
||||||
|
privateKeyFile string
|
||||||
|
baseURL string
|
||||||
|
}
|
||||||
|
|
||||||
|
var secretGitHubAppArgs = secretGitHubAppFlags{}
|
||||||
|
|
||||||
|
func init() {
|
||||||
|
createSecretGitHubAppCmd.Flags().StringVar(&secretGitHubAppArgs.appID, "app-id", "", "github app ID")
|
||||||
|
createSecretGitHubAppCmd.Flags().StringVar(&secretGitHubAppArgs.appInstallationID, "app-installation-id", "", "github app installation ID")
|
||||||
|
createSecretGitHubAppCmd.Flags().StringVar(&secretGitHubAppArgs.privateKeyFile, "app-private-key", "", "github app private key file path")
|
||||||
|
createSecretGitHubAppCmd.Flags().StringVar(&secretGitHubAppArgs.baseURL, "app-base-url", "", "github app base URL")
|
||||||
|
|
||||||
|
createSecretCmd.AddCommand(createSecretGitHubAppCmd)
|
||||||
|
}
|
||||||
|
|
||||||
|
func createSecretGitHubAppCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
|
if len(args) < 1 {
|
||||||
|
return fmt.Errorf("name is required")
|
||||||
|
}
|
||||||
|
|
||||||
|
secretName := args[0]
|
||||||
|
|
||||||
|
if secretGitHubAppArgs.appID == "" {
|
||||||
|
return fmt.Errorf("--app-id is required")
|
||||||
|
}
|
||||||
|
|
||||||
|
if secretGitHubAppArgs.appInstallationID == "" {
|
||||||
|
return fmt.Errorf("--app-installation-id is required")
|
||||||
|
}
|
||||||
|
|
||||||
|
if secretGitHubAppArgs.privateKeyFile == "" {
|
||||||
|
return fmt.Errorf("--app-private-key is required")
|
||||||
|
}
|
||||||
|
|
||||||
|
privateKey, err := os.ReadFile(secretGitHubAppArgs.privateKeyFile)
|
||||||
|
if err != nil {
|
||||||
|
return fmt.Errorf("unable to read private key file: %w", err)
|
||||||
|
}
|
||||||
|
|
||||||
|
opts := sourcesecret.Options{
|
||||||
|
Name: secretName,
|
||||||
|
Namespace: *kubeconfigArgs.Namespace,
|
||||||
|
GitHubAppID: secretGitHubAppArgs.appID,
|
||||||
|
GitHubAppInstallationID: secretGitHubAppArgs.appInstallationID,
|
||||||
|
GitHubAppPrivateKey: string(privateKey),
|
||||||
|
}
|
||||||
|
|
||||||
|
if secretGitHubAppArgs.baseURL != "" {
|
||||||
|
opts.GitHubAppBaseURL = secretGitHubAppArgs.baseURL
|
||||||
|
}
|
||||||
|
|
||||||
|
secret, err := sourcesecret.GenerateGitHubApp(opts)
|
||||||
|
if err != nil {
|
||||||
|
return err
|
||||||
|
}
|
||||||
|
|
||||||
|
if createArgs.export {
|
||||||
|
rootCmd.Println(secret.Content)
|
||||||
|
return nil
|
||||||
|
}
|
||||||
|
|
||||||
|
ctx, cancel := context.WithTimeout(context.Background(), rootArgs.timeout)
|
||||||
|
defer cancel()
|
||||||
|
kubeClient, err := utils.KubeClient(kubeconfigArgs, kubeclientOptions)
|
||||||
|
if err != nil {
|
||||||
|
return err
|
||||||
|
}
|
||||||
|
var s corev1.Secret
|
||||||
|
if err := yaml.Unmarshal([]byte(secret.Content), &s); err != nil {
|
||||||
|
return err
|
||||||
|
}
|
||||||
|
if err := upsertSecret(ctx, kubeClient, s); err != nil {
|
||||||
|
return err
|
||||||
|
}
|
||||||
|
|
||||||
|
logger.Actionf("githubapp secret '%s' created in '%s' namespace", secretName, *kubeconfigArgs.Namespace)
|
||||||
|
return nil
|
||||||
|
}
|
||||||
|
|
@ -0,0 +1,74 @@
|
||||||
|
/*
|
||||||
|
Copyright 2022 The Flux authors
|
||||||
|
|
||||||
|
Licensed under the Apache License, Version 2.0 (the "License");
|
||||||
|
you may not use this file except in compliance with the License.
|
||||||
|
You may obtain a copy of the License at
|
||||||
|
|
||||||
|
http://www.apache.org/licenses/LICENSE-2.0
|
||||||
|
|
||||||
|
Unless required by applicable law or agreed to in writing, software
|
||||||
|
distributed under the License is distributed on an "AS IS" BASIS,
|
||||||
|
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||||
|
See the License for the specific language governing permissions and
|
||||||
|
limitations under the License.
|
||||||
|
*/
|
||||||
|
|
||||||
|
package main
|
||||||
|
|
||||||
|
import (
|
||||||
|
"testing"
|
||||||
|
)
|
||||||
|
|
||||||
|
func TestCreateSecretGitHubApp(t *testing.T) {
|
||||||
|
tests := []struct {
|
||||||
|
name string
|
||||||
|
args string
|
||||||
|
assert assertFunc
|
||||||
|
}{
|
||||||
|
{
|
||||||
|
name: "create githubapp secret with missing name",
|
||||||
|
args: "create secret githubapp",
|
||||||
|
assert: assertError("name is required"),
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "create githubapp secret with missing app-id",
|
||||||
|
args: "create secret githubapp appinfo",
|
||||||
|
assert: assertError("--app-id is required"),
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "create githubapp secret with missing appInstallationID",
|
||||||
|
args: "create secret githubapp appinfo --app-id 1",
|
||||||
|
assert: assertError("--app-installation-id is required"),
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "create githubapp secret with missing private key file",
|
||||||
|
args: "create secret githubapp appinfo --app-id 1 --app-installation-id 2",
|
||||||
|
assert: assertError("--app-private-key is required"),
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "create githubapp secret with private key file that does not exist",
|
||||||
|
args: "create secret githubapp appinfo --app-id 1 --app-installation-id 2 --app-private-key pk.pem",
|
||||||
|
assert: assertError("unable to read private key file: open pk.pem: no such file or directory"),
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "create githubapp secret with app info",
|
||||||
|
args: "create secret githubapp appinfo --namespace my-namespace --app-id 1 --app-installation-id 2 --app-private-key ./testdata/create_secret/githubapp/test-private-key.pem --export",
|
||||||
|
assert: assertGoldenFile("testdata/create_secret/githubapp/secret.yaml"),
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "create githubapp secret with appinfo and base url",
|
||||||
|
args: "create secret githubapp appinfo --namespace my-namespace --app-id 1 --app-installation-id 2 --app-private-key ./testdata/create_secret/githubapp/test-private-key.pem --app-base-url www.example.com/api/v3 --export",
|
||||||
|
assert: assertGoldenFile("testdata/create_secret/githubapp/secret-with-baseurl.yaml"),
|
||||||
|
},
|
||||||
|
}
|
||||||
|
for _, tt := range tests {
|
||||||
|
t.Run(tt.name, func(t *testing.T) {
|
||||||
|
cmd := cmdTestCase{
|
||||||
|
args: tt.args,
|
||||||
|
assert: tt.assert,
|
||||||
|
}
|
||||||
|
cmd.runTestCmd(t)
|
||||||
|
})
|
||||||
|
}
|
||||||
|
}
|
||||||
|
|
@ -32,7 +32,7 @@ import (
|
||||||
var createSecretHelmCmd = &cobra.Command{
|
var createSecretHelmCmd = &cobra.Command{
|
||||||
Use: "helm [name]",
|
Use: "helm [name]",
|
||||||
Short: "Create or update a Kubernetes secret for Helm repository authentication",
|
Short: "Create or update a Kubernetes secret for Helm repository authentication",
|
||||||
Long: withPreviewNote(`The create secret helm command generates a Kubernetes secret with basic authentication credentials.`),
|
Long: `The create secret helm command generates a Kubernetes secret with basic authentication credentials.`,
|
||||||
Example: ` # Create a Helm authentication secret on disk and encrypt it with Mozilla SOPS
|
Example: ` # Create a Helm authentication secret on disk and encrypt it with Mozilla SOPS
|
||||||
flux create secret helm repo-auth \
|
flux create secret helm repo-auth \
|
||||||
--namespace=my-namespace \
|
--namespace=my-namespace \
|
||||||
|
|
@ -58,12 +58,9 @@ func init() {
|
||||||
flags := createSecretHelmCmd.Flags()
|
flags := createSecretHelmCmd.Flags()
|
||||||
flags.StringVarP(&secretHelmArgs.username, "username", "u", "", "basic authentication username")
|
flags.StringVarP(&secretHelmArgs.username, "username", "u", "", "basic authentication username")
|
||||||
flags.StringVarP(&secretHelmArgs.password, "password", "p", "", "basic authentication password")
|
flags.StringVarP(&secretHelmArgs.password, "password", "p", "", "basic authentication password")
|
||||||
|
flags.StringVar(&secretHelmArgs.tlsCrtFile, "tls-crt-file", "", "TLS authentication cert file path")
|
||||||
initSecretDeprecatedTLSFlags(flags, &secretHelmArgs.secretTLSFlags)
|
flags.StringVar(&secretHelmArgs.tlsKeyFile, "tls-key-file", "", "TLS authentication key file path")
|
||||||
deprecationMsg := "please use the command `flux create secret tls` to generate TLS secrets"
|
flags.StringVar(&secretHelmArgs.caCrtFile, "ca-crt-file", "", "TLS authentication CA file path")
|
||||||
flags.MarkDeprecated("cert-file", deprecationMsg)
|
|
||||||
flags.MarkDeprecated("key-file", deprecationMsg)
|
|
||||||
flags.MarkDeprecated("ca-file", deprecationMsg)
|
|
||||||
|
|
||||||
createSecretCmd.AddCommand(createSecretHelmCmd)
|
createSecretCmd.AddCommand(createSecretHelmCmd)
|
||||||
}
|
}
|
||||||
|
|
@ -77,20 +74,22 @@ func createSecretHelmCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
}
|
}
|
||||||
|
|
||||||
caBundle := []byte{}
|
caBundle := []byte{}
|
||||||
if secretHelmArgs.caFile != "" {
|
if secretHelmArgs.caCrtFile != "" {
|
||||||
var err error
|
var err error
|
||||||
caBundle, err = os.ReadFile(secretHelmArgs.caFile)
|
caBundle, err = os.ReadFile(secretHelmArgs.caCrtFile)
|
||||||
if err != nil {
|
if err != nil {
|
||||||
return fmt.Errorf("unable to read TLS CA file: %w", err)
|
return fmt.Errorf("unable to read TLS CA file: %w", err)
|
||||||
}
|
}
|
||||||
}
|
}
|
||||||
|
|
||||||
var certFile, keyFile []byte
|
var certFile, keyFile []byte
|
||||||
if secretHelmArgs.certFile != "" && secretHelmArgs.keyFile != "" {
|
if secretHelmArgs.tlsCrtFile != "" {
|
||||||
if certFile, err = os.ReadFile(secretHelmArgs.certFile); err != nil {
|
if certFile, err = os.ReadFile(secretHelmArgs.tlsCrtFile); err != nil {
|
||||||
return fmt.Errorf("failed to read cert file: %w", err)
|
return fmt.Errorf("failed to read cert file: %w", err)
|
||||||
}
|
}
|
||||||
if keyFile, err = os.ReadFile(secretHelmArgs.keyFile); err != nil {
|
}
|
||||||
|
if secretHelmArgs.tlsKeyFile != "" {
|
||||||
|
if keyFile, err = os.ReadFile(secretHelmArgs.tlsKeyFile); err != nil {
|
||||||
return fmt.Errorf("failed to read key file: %w", err)
|
return fmt.Errorf("failed to read key file: %w", err)
|
||||||
}
|
}
|
||||||
}
|
}
|
||||||
|
|
@ -101,11 +100,11 @@ func createSecretHelmCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
Labels: labels,
|
Labels: labels,
|
||||||
Username: secretHelmArgs.username,
|
Username: secretHelmArgs.username,
|
||||||
Password: secretHelmArgs.password,
|
Password: secretHelmArgs.password,
|
||||||
CAFile: caBundle,
|
CACrt: caBundle,
|
||||||
CertFile: certFile,
|
TLSCrt: certFile,
|
||||||
KeyFile: keyFile,
|
TLSKey: keyFile,
|
||||||
}
|
}
|
||||||
secret, err := sourcesecret.Generate(opts)
|
secret, err := sourcesecret.GenerateHelm(opts)
|
||||||
if err != nil {
|
if err != nil {
|
||||||
return err
|
return err
|
||||||
}
|
}
|
||||||
|
|
|
||||||
|
|
@ -0,0 +1,161 @@
|
||||||
|
/*
|
||||||
|
Copyright 2024 The Flux authors
|
||||||
|
|
||||||
|
Licensed under the Apache License, Version 2.0 (the "License");
|
||||||
|
you may not use this file except in compliance with the License.
|
||||||
|
You may obtain a copy of the License at
|
||||||
|
|
||||||
|
http://www.apache.org/licenses/LICENSE-2.0
|
||||||
|
|
||||||
|
Unless required by applicable law or agreed to in writing, software
|
||||||
|
distributed under the License is distributed on an "AS IS" BASIS,
|
||||||
|
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||||
|
See the License for the specific language governing permissions and
|
||||||
|
limitations under the License.
|
||||||
|
*/
|
||||||
|
|
||||||
|
package main
|
||||||
|
|
||||||
|
import (
|
||||||
|
"context"
|
||||||
|
"encoding/json"
|
||||||
|
"errors"
|
||||||
|
"fmt"
|
||||||
|
"os"
|
||||||
|
"path/filepath"
|
||||||
|
"strings"
|
||||||
|
|
||||||
|
"github.com/fluxcd/flux2/v2/internal/utils"
|
||||||
|
"github.com/fluxcd/flux2/v2/pkg/manifestgen/sourcesecret"
|
||||||
|
"github.com/notaryproject/notation-go/verifier/trustpolicy"
|
||||||
|
"github.com/spf13/cobra"
|
||||||
|
corev1 "k8s.io/api/core/v1"
|
||||||
|
"sigs.k8s.io/yaml"
|
||||||
|
)
|
||||||
|
|
||||||
|
var createSecretNotationCmd = &cobra.Command{
|
||||||
|
Use: "notation [name]",
|
||||||
|
Short: "Create or update a Kubernetes secret for verifications of artifacts signed by Notation",
|
||||||
|
Long: withPreviewNote(`The create secret notation command generates a Kubernetes secret with root ca certificates and trust policy.`),
|
||||||
|
Example: ` # Create a Notation configuration secret on disk and encrypt it with Mozilla SOPS
|
||||||
|
flux create secret notation my-notation-cert \
|
||||||
|
--namespace=my-namespace \
|
||||||
|
--trust-policy-file=./my-trust-policy.json \
|
||||||
|
--ca-cert-file=./my-cert.crt \
|
||||||
|
--export > my-notation-cert.yaml
|
||||||
|
|
||||||
|
sops --encrypt --encrypted-regex '^(data|stringData)$' \
|
||||||
|
--in-place my-notation-cert.yaml`,
|
||||||
|
|
||||||
|
RunE: createSecretNotationCmdRun,
|
||||||
|
}
|
||||||
|
|
||||||
|
type secretNotationFlags struct {
|
||||||
|
trustPolicyFile string
|
||||||
|
caCrtFile []string
|
||||||
|
}
|
||||||
|
|
||||||
|
var secretNotationArgs secretNotationFlags
|
||||||
|
|
||||||
|
func init() {
|
||||||
|
createSecretNotationCmd.Flags().StringVar(&secretNotationArgs.trustPolicyFile, "trust-policy-file", "", "notation trust policy file path")
|
||||||
|
createSecretNotationCmd.Flags().StringSliceVar(&secretNotationArgs.caCrtFile, "ca-cert-file", []string{}, "root ca cert file path")
|
||||||
|
|
||||||
|
createSecretCmd.AddCommand(createSecretNotationCmd)
|
||||||
|
}
|
||||||
|
|
||||||
|
func createSecretNotationCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
|
if len(args) < 1 {
|
||||||
|
return fmt.Errorf("name is required")
|
||||||
|
}
|
||||||
|
|
||||||
|
if secretNotationArgs.caCrtFile == nil || len(secretNotationArgs.caCrtFile) == 0 {
|
||||||
|
return fmt.Errorf("--ca-cert-file is required")
|
||||||
|
}
|
||||||
|
|
||||||
|
if secretNotationArgs.trustPolicyFile == "" {
|
||||||
|
return fmt.Errorf("--trust-policy-file is required")
|
||||||
|
}
|
||||||
|
|
||||||
|
name := args[0]
|
||||||
|
|
||||||
|
labels, err := parseLabels()
|
||||||
|
if err != nil {
|
||||||
|
return err
|
||||||
|
}
|
||||||
|
|
||||||
|
policy, err := os.ReadFile(secretNotationArgs.trustPolicyFile)
|
||||||
|
if err != nil {
|
||||||
|
return fmt.Errorf("unable to read trust policy file: %w", err)
|
||||||
|
}
|
||||||
|
|
||||||
|
var doc trustpolicy.Document
|
||||||
|
|
||||||
|
if err := json.Unmarshal(policy, &doc); err != nil {
|
||||||
|
return fmt.Errorf("failed to unmarshal trust policy %s: %w", secretNotationArgs.trustPolicyFile, err)
|
||||||
|
}
|
||||||
|
|
||||||
|
if err := doc.Validate(); err != nil {
|
||||||
|
return fmt.Errorf("invalid trust policy: %w", err)
|
||||||
|
}
|
||||||
|
|
||||||
|
var (
|
||||||
|
caCerts []sourcesecret.VerificationCrt
|
||||||
|
fileErr error
|
||||||
|
)
|
||||||
|
for _, caCrtFile := range secretNotationArgs.caCrtFile {
|
||||||
|
fileName := filepath.Base(caCrtFile)
|
||||||
|
if !strings.HasSuffix(fileName, ".crt") && !strings.HasSuffix(fileName, ".pem") {
|
||||||
|
fileErr = errors.Join(fileErr, fmt.Errorf("%s must end with either .crt or .pem", fileName))
|
||||||
|
continue
|
||||||
|
}
|
||||||
|
caBundle, err := os.ReadFile(caCrtFile)
|
||||||
|
if err != nil {
|
||||||
|
fileErr = errors.Join(fileErr, fmt.Errorf("unable to read TLS CA file: %w", err))
|
||||||
|
continue
|
||||||
|
}
|
||||||
|
caCerts = append(caCerts, sourcesecret.VerificationCrt{Name: fileName, CACrt: caBundle})
|
||||||
|
}
|
||||||
|
|
||||||
|
if fileErr != nil {
|
||||||
|
return fileErr
|
||||||
|
}
|
||||||
|
|
||||||
|
if len(caCerts) == 0 {
|
||||||
|
return fmt.Errorf("no CA certs found")
|
||||||
|
}
|
||||||
|
|
||||||
|
opts := sourcesecret.Options{
|
||||||
|
Name: name,
|
||||||
|
Namespace: *kubeconfigArgs.Namespace,
|
||||||
|
Labels: labels,
|
||||||
|
VerificationCrts: caCerts,
|
||||||
|
TrustPolicy: policy,
|
||||||
|
}
|
||||||
|
secret, err := sourcesecret.GenerateNotation(opts)
|
||||||
|
if err != nil {
|
||||||
|
return err
|
||||||
|
}
|
||||||
|
|
||||||
|
if createArgs.export {
|
||||||
|
rootCmd.Println(secret.Content)
|
||||||
|
return nil
|
||||||
|
}
|
||||||
|
|
||||||
|
ctx, cancel := context.WithTimeout(context.Background(), rootArgs.timeout)
|
||||||
|
defer cancel()
|
||||||
|
kubeClient, err := utils.KubeClient(kubeconfigArgs, kubeclientOptions)
|
||||||
|
if err != nil {
|
||||||
|
return err
|
||||||
|
}
|
||||||
|
var s corev1.Secret
|
||||||
|
if err := yaml.Unmarshal([]byte(secret.Content), &s); err != nil {
|
||||||
|
return err
|
||||||
|
}
|
||||||
|
if err := upsertSecret(ctx, kubeClient, s); err != nil {
|
||||||
|
return err
|
||||||
|
}
|
||||||
|
|
||||||
|
logger.Actionf("notation configuration secret '%s' created in '%s' namespace", name, *kubeconfigArgs.Namespace)
|
||||||
|
return nil
|
||||||
|
}
|
||||||
|
|
@ -0,0 +1,124 @@
|
||||||
|
/*
|
||||||
|
Copyright 2024 The Flux authors
|
||||||
|
|
||||||
|
Licensed under the Apache License, Version 2.0 (the "License");
|
||||||
|
you may not use this file except in compliance with the License.
|
||||||
|
You may obtain a copy of the License at
|
||||||
|
|
||||||
|
http://www.apache.org/licenses/LICENSE-2.0
|
||||||
|
|
||||||
|
Unless required by applicable law or agreed to in writing, software
|
||||||
|
distributed under the License is distributed on an "AS IS" BASIS,
|
||||||
|
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||||
|
See the License for the specific language governing permissions and
|
||||||
|
limitations under the License.
|
||||||
|
*/
|
||||||
|
|
||||||
|
package main
|
||||||
|
|
||||||
|
import (
|
||||||
|
"fmt"
|
||||||
|
"os"
|
||||||
|
"path/filepath"
|
||||||
|
"testing"
|
||||||
|
)
|
||||||
|
|
||||||
|
const (
|
||||||
|
trustPolicy = "./testdata/create_secret/notation/test-trust-policy.json"
|
||||||
|
invalidTrustPolicy = "./testdata/create_secret/notation/invalid-trust-policy.json"
|
||||||
|
invalidJson = "./testdata/create_secret/notation/invalid.json"
|
||||||
|
testCertFolder = "./testdata/create_secret/notation"
|
||||||
|
)
|
||||||
|
|
||||||
|
func TestCreateNotationSecret(t *testing.T) {
|
||||||
|
crt, err := os.Create(filepath.Join(t.TempDir(), "ca.crt"))
|
||||||
|
if err != nil {
|
||||||
|
t.Fatal("could not create ca.crt file")
|
||||||
|
}
|
||||||
|
|
||||||
|
pem, err := os.Create(filepath.Join(t.TempDir(), "ca.pem"))
|
||||||
|
if err != nil {
|
||||||
|
t.Fatal("could not create ca.pem file")
|
||||||
|
}
|
||||||
|
|
||||||
|
invalidCert, err := os.Create(filepath.Join(t.TempDir(), "ca.p12"))
|
||||||
|
if err != nil {
|
||||||
|
t.Fatal("could not create ca.p12 file")
|
||||||
|
}
|
||||||
|
|
||||||
|
_, err = crt.Write([]byte("ca-data-crt"))
|
||||||
|
if err != nil {
|
||||||
|
t.Fatal("could not write to crt certificate file")
|
||||||
|
}
|
||||||
|
|
||||||
|
_, err = pem.Write([]byte("ca-data-pem"))
|
||||||
|
if err != nil {
|
||||||
|
t.Fatal("could not write to pem certificate file")
|
||||||
|
}
|
||||||
|
|
||||||
|
tests := []struct {
|
||||||
|
name string
|
||||||
|
args string
|
||||||
|
assert assertFunc
|
||||||
|
}{
|
||||||
|
{
|
||||||
|
name: "no args",
|
||||||
|
args: "create secret notation",
|
||||||
|
assert: assertError("name is required"),
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "no trust policy",
|
||||||
|
args: fmt.Sprintf("create secret notation notation-config --ca-cert-file=%s", testCertFolder),
|
||||||
|
assert: assertError("--trust-policy-file is required"),
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "no cert",
|
||||||
|
args: fmt.Sprintf("create secret notation notation-config --trust-policy-file=%s", trustPolicy),
|
||||||
|
assert: assertError("--ca-cert-file is required"),
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "non pem and crt cert",
|
||||||
|
args: fmt.Sprintf("create secret notation notation-config --ca-cert-file=%s --trust-policy-file=%s", invalidCert.Name(), trustPolicy),
|
||||||
|
assert: assertError("ca.p12 must end with either .crt or .pem"),
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "invalid trust policy",
|
||||||
|
args: fmt.Sprintf("create secret notation notation-config --ca-cert-file=%s --trust-policy-file=%s", t.TempDir(), invalidTrustPolicy),
|
||||||
|
assert: assertError("invalid trust policy: trust policy: a trust policy statement is missing a name, every statement requires a name"),
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "invalid trust policy json",
|
||||||
|
args: fmt.Sprintf("create secret notation notation-config --ca-cert-file=%s --trust-policy-file=%s", t.TempDir(), invalidJson),
|
||||||
|
assert: assertError(fmt.Sprintf("failed to unmarshal trust policy %s: json: cannot unmarshal string into Go value of type trustpolicy.Document", invalidJson)),
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "crt secret",
|
||||||
|
args: fmt.Sprintf("create secret notation notation-config --ca-cert-file=%s --trust-policy-file=%s --namespace=my-namespace --export", crt.Name(), trustPolicy),
|
||||||
|
assert: assertGoldenFile("./testdata/create_secret/notation/secret-ca-crt.yaml"),
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "pem secret",
|
||||||
|
args: fmt.Sprintf("create secret notation notation-config --ca-cert-file=%s --trust-policy-file=%s --namespace=my-namespace --export", pem.Name(), trustPolicy),
|
||||||
|
assert: assertGoldenFile("./testdata/create_secret/notation/secret-ca-pem.yaml"),
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "multi secret",
|
||||||
|
args: fmt.Sprintf("create secret notation notation-config --ca-cert-file=%s --ca-cert-file=%s --trust-policy-file=%s --namespace=my-namespace --export", crt.Name(), pem.Name(), trustPolicy),
|
||||||
|
assert: assertGoldenFile("./testdata/create_secret/notation/secret-ca-multi.yaml"),
|
||||||
|
},
|
||||||
|
}
|
||||||
|
|
||||||
|
for _, tt := range tests {
|
||||||
|
t.Run(tt.name, func(t *testing.T) {
|
||||||
|
defer func() {
|
||||||
|
secretNotationArgs = secretNotationFlags{}
|
||||||
|
}()
|
||||||
|
|
||||||
|
cmd := cmdTestCase{
|
||||||
|
args: tt.args,
|
||||||
|
assert: tt.assert,
|
||||||
|
}
|
||||||
|
cmd.runTestCmd(t)
|
||||||
|
})
|
||||||
|
}
|
||||||
|
}
|
||||||
|
|
@ -92,7 +92,7 @@ func createSecretOCICmdRun(cmd *cobra.Command, args []string) error {
|
||||||
Username: secretOCIArgs.username,
|
Username: secretOCIArgs.username,
|
||||||
}
|
}
|
||||||
|
|
||||||
secret, err := sourcesecret.Generate(opts)
|
secret, err := sourcesecret.GenerateOCI(opts)
|
||||||
if err != nil {
|
if err != nil {
|
||||||
return err
|
return err
|
||||||
}
|
}
|
||||||
|
|
|
||||||
|
|
@ -0,0 +1,112 @@
|
||||||
|
/*
|
||||||
|
Copyright 2024 The Flux authors
|
||||||
|
|
||||||
|
Licensed under the Apache License, Version 2.0 (the "License");
|
||||||
|
you may not use this file except in compliance with the License.
|
||||||
|
You may obtain a copy of the License at
|
||||||
|
|
||||||
|
http://www.apache.org/licenses/LICENSE-2.0
|
||||||
|
|
||||||
|
Unless required by applicable law or agreed to in writing, software
|
||||||
|
distributed under the License is distributed on an "AS IS" BASIS,
|
||||||
|
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||||
|
See the License for the specific language governing permissions and
|
||||||
|
limitations under the License.
|
||||||
|
*/
|
||||||
|
|
||||||
|
package main
|
||||||
|
|
||||||
|
import (
|
||||||
|
"context"
|
||||||
|
"errors"
|
||||||
|
|
||||||
|
"github.com/spf13/cobra"
|
||||||
|
corev1 "k8s.io/api/core/v1"
|
||||||
|
"sigs.k8s.io/yaml"
|
||||||
|
|
||||||
|
"github.com/fluxcd/flux2/v2/internal/utils"
|
||||||
|
"github.com/fluxcd/flux2/v2/pkg/manifestgen/sourcesecret"
|
||||||
|
)
|
||||||
|
|
||||||
|
var createSecretProxyCmd = &cobra.Command{
|
||||||
|
Use: "proxy [name]",
|
||||||
|
Short: "Create or update a Kubernetes secret for proxy authentication",
|
||||||
|
Long: `The create secret proxy command generates a Kubernetes secret with the
|
||||||
|
proxy address and the basic authentication credentials.`,
|
||||||
|
Example: ` # Create a proxy secret on disk and encrypt it with SOPS
|
||||||
|
flux create secret proxy my-proxy \
|
||||||
|
--namespace=my-namespace \
|
||||||
|
--address=https://my-proxy.com \
|
||||||
|
--username=my-username \
|
||||||
|
--password=my-password \
|
||||||
|
--export > proxy.yaml
|
||||||
|
|
||||||
|
sops --encrypt --encrypted-regex '^(data|stringData)$' \
|
||||||
|
--in-place proxy.yaml`,
|
||||||
|
|
||||||
|
RunE: createSecretProxyCmdRun,
|
||||||
|
}
|
||||||
|
|
||||||
|
type secretProxyFlags struct {
|
||||||
|
address string
|
||||||
|
username string
|
||||||
|
password string
|
||||||
|
}
|
||||||
|
|
||||||
|
var secretProxyArgs secretProxyFlags
|
||||||
|
|
||||||
|
func init() {
|
||||||
|
createSecretProxyCmd.Flags().StringVar(&secretProxyArgs.address, "address", "", "proxy address")
|
||||||
|
createSecretProxyCmd.Flags().StringVarP(&secretProxyArgs.username, "username", "u", "", "basic authentication username")
|
||||||
|
createSecretProxyCmd.Flags().StringVarP(&secretProxyArgs.password, "password", "p", "", "basic authentication password")
|
||||||
|
|
||||||
|
createSecretCmd.AddCommand(createSecretProxyCmd)
|
||||||
|
}
|
||||||
|
|
||||||
|
func createSecretProxyCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
|
name := args[0]
|
||||||
|
|
||||||
|
labels, err := parseLabels()
|
||||||
|
if err != nil {
|
||||||
|
return err
|
||||||
|
}
|
||||||
|
|
||||||
|
if secretProxyArgs.address == "" {
|
||||||
|
return errors.New("address is required")
|
||||||
|
}
|
||||||
|
|
||||||
|
opts := sourcesecret.Options{
|
||||||
|
Name: name,
|
||||||
|
Namespace: *kubeconfigArgs.Namespace,
|
||||||
|
Labels: labels,
|
||||||
|
Address: secretProxyArgs.address,
|
||||||
|
Username: secretProxyArgs.username,
|
||||||
|
Password: secretProxyArgs.password,
|
||||||
|
}
|
||||||
|
secret, err := sourcesecret.GenerateProxy(opts)
|
||||||
|
if err != nil {
|
||||||
|
return err
|
||||||
|
}
|
||||||
|
|
||||||
|
if createArgs.export {
|
||||||
|
rootCmd.Println(secret.Content)
|
||||||
|
return nil
|
||||||
|
}
|
||||||
|
|
||||||
|
ctx, cancel := context.WithTimeout(context.Background(), rootArgs.timeout)
|
||||||
|
defer cancel()
|
||||||
|
kubeClient, err := utils.KubeClient(kubeconfigArgs, kubeclientOptions)
|
||||||
|
if err != nil {
|
||||||
|
return err
|
||||||
|
}
|
||||||
|
var s corev1.Secret
|
||||||
|
if err := yaml.Unmarshal([]byte(secret.Content), &s); err != nil {
|
||||||
|
return err
|
||||||
|
}
|
||||||
|
if err := upsertSecret(ctx, kubeClient, s); err != nil {
|
||||||
|
return err
|
||||||
|
}
|
||||||
|
|
||||||
|
logger.Actionf("proxy secret '%s' created in '%s' namespace", name, *kubeconfigArgs.Namespace)
|
||||||
|
return nil
|
||||||
|
}
|
||||||
|
|
@ -0,0 +1,47 @@
|
||||||
|
/*
|
||||||
|
Copyright 2024 The Flux authors
|
||||||
|
|
||||||
|
Licensed under the Apache License, Version 2.0 (the "License");
|
||||||
|
you may not use this file except in compliance with the License.
|
||||||
|
You may obtain a copy of the License at
|
||||||
|
|
||||||
|
http://www.apache.org/licenses/LICENSE-2.0
|
||||||
|
|
||||||
|
Unless required by applicable law or agreed to in writing, software
|
||||||
|
distributed under the License is distributed on an "AS IS" BASIS,
|
||||||
|
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||||
|
See the License for the specific language governing permissions and
|
||||||
|
limitations under the License.
|
||||||
|
*/
|
||||||
|
|
||||||
|
package main
|
||||||
|
|
||||||
|
import (
|
||||||
|
"testing"
|
||||||
|
)
|
||||||
|
|
||||||
|
func TestCreateProxySecret(t *testing.T) {
|
||||||
|
tests := []struct {
|
||||||
|
name string
|
||||||
|
args string
|
||||||
|
assert assertFunc
|
||||||
|
}{
|
||||||
|
{
|
||||||
|
args: "create secret proxy proxy-secret",
|
||||||
|
assert: assertError("address is required"),
|
||||||
|
},
|
||||||
|
{
|
||||||
|
args: "create secret proxy proxy-secret --address=https://my-proxy.com --username=my-username --password=my-password --namespace=my-namespace --export",
|
||||||
|
assert: assertGoldenFile("testdata/create_secret/proxy/secret-proxy.yaml"),
|
||||||
|
},
|
||||||
|
}
|
||||||
|
for _, tt := range tests {
|
||||||
|
t.Run(tt.name, func(t *testing.T) {
|
||||||
|
cmd := cmdTestCase{
|
||||||
|
args: tt.args,
|
||||||
|
assert: tt.assert,
|
||||||
|
}
|
||||||
|
cmd.runTestCmd(t)
|
||||||
|
})
|
||||||
|
}
|
||||||
|
}
|
||||||
|
|
@ -22,7 +22,6 @@ import (
|
||||||
"os"
|
"os"
|
||||||
|
|
||||||
"github.com/spf13/cobra"
|
"github.com/spf13/cobra"
|
||||||
"github.com/spf13/pflag"
|
|
||||||
corev1 "k8s.io/api/core/v1"
|
corev1 "k8s.io/api/core/v1"
|
||||||
"sigs.k8s.io/yaml"
|
"sigs.k8s.io/yaml"
|
||||||
|
|
||||||
|
|
@ -33,8 +32,8 @@ import (
|
||||||
var createSecretTLSCmd = &cobra.Command{
|
var createSecretTLSCmd = &cobra.Command{
|
||||||
Use: "tls [name]",
|
Use: "tls [name]",
|
||||||
Short: "Create or update a Kubernetes secret with TLS certificates",
|
Short: "Create or update a Kubernetes secret with TLS certificates",
|
||||||
Long: withPreviewNote(`The create secret tls command generates a Kubernetes secret with certificates for use with TLS.`),
|
Long: `The create secret tls command generates a Kubernetes secret with certificates for use with TLS.`,
|
||||||
Example: ` # Create a TLS secret on disk and encrypt it with Mozilla SOPS.
|
Example: ` # Create a TLS secret on disk and encrypt it with SOPS.
|
||||||
# Files are expected to be PEM-encoded.
|
# Files are expected to be PEM-encoded.
|
||||||
flux create secret tls certs \
|
flux create secret tls certs \
|
||||||
--namespace=my-namespace \
|
--namespace=my-namespace \
|
||||||
|
|
@ -49,9 +48,6 @@ var createSecretTLSCmd = &cobra.Command{
|
||||||
}
|
}
|
||||||
|
|
||||||
type secretTLSFlags struct {
|
type secretTLSFlags struct {
|
||||||
certFile string
|
|
||||||
keyFile string
|
|
||||||
caFile string
|
|
||||||
caCrtFile string
|
caCrtFile string
|
||||||
tlsKeyFile string
|
tlsKeyFile string
|
||||||
tlsCrtFile string
|
tlsCrtFile string
|
||||||
|
|
@ -59,26 +55,10 @@ type secretTLSFlags struct {
|
||||||
|
|
||||||
var secretTLSArgs secretTLSFlags
|
var secretTLSArgs secretTLSFlags
|
||||||
|
|
||||||
func initSecretDeprecatedTLSFlags(flags *pflag.FlagSet, args *secretTLSFlags) {
|
|
||||||
flags.StringVar(&args.certFile, "cert-file", "", "TLS authentication cert file path")
|
|
||||||
flags.StringVar(&args.keyFile, "key-file", "", "TLS authentication key file path")
|
|
||||||
flags.StringVar(&args.caFile, "ca-file", "", "TLS authentication CA file path")
|
|
||||||
}
|
|
||||||
|
|
||||||
func initSecretTLSFlags(flags *pflag.FlagSet, args *secretTLSFlags) {
|
|
||||||
flags.StringVar(&args.tlsCrtFile, "tls-crt-file", "", "TLS authentication cert file path")
|
|
||||||
flags.StringVar(&args.tlsKeyFile, "tls-key-file", "", "TLS authentication key file path")
|
|
||||||
flags.StringVar(&args.caCrtFile, "ca-crt-file", "", "TLS authentication CA file path")
|
|
||||||
}
|
|
||||||
|
|
||||||
func init() {
|
func init() {
|
||||||
flags := createSecretTLSCmd.Flags()
|
createSecretTLSCmd.Flags().StringVar(&secretTLSArgs.tlsCrtFile, "tls-crt-file", "", "TLS authentication cert file path")
|
||||||
initSecretDeprecatedTLSFlags(flags, &secretTLSArgs)
|
createSecretTLSCmd.Flags().StringVar(&secretTLSArgs.tlsKeyFile, "tls-key-file", "", "TLS authentication key file path")
|
||||||
initSecretTLSFlags(flags, &secretTLSArgs)
|
createSecretTLSCmd.Flags().StringVar(&secretTLSArgs.caCrtFile, "ca-crt-file", "", "TLS authentication CA file path")
|
||||||
|
|
||||||
flags.MarkDeprecated("cert-file", "please use --tls-crt-file instead")
|
|
||||||
flags.MarkDeprecated("key-file", "please use --tls-key-file instead")
|
|
||||||
flags.MarkDeprecated("ca-file", "please use --ca-crt-file instead")
|
|
||||||
|
|
||||||
createSecretCmd.AddCommand(createSecretTLSCmd)
|
createSecretCmd.AddCommand(createSecretTLSCmd)
|
||||||
}
|
}
|
||||||
|
|
@ -102,30 +82,20 @@ func createSecretTLSCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
if err != nil {
|
if err != nil {
|
||||||
return fmt.Errorf("unable to read TLS CA file: %w", err)
|
return fmt.Errorf("unable to read TLS CA file: %w", err)
|
||||||
}
|
}
|
||||||
} else if secretTLSArgs.caFile != "" {
|
|
||||||
opts.CAFile, err = os.ReadFile(secretTLSArgs.caFile)
|
|
||||||
if err != nil {
|
|
||||||
return fmt.Errorf("unable to read TLS CA file: %w", err)
|
|
||||||
}
|
|
||||||
}
|
}
|
||||||
|
|
||||||
if secretTLSArgs.tlsCrtFile != "" && secretTLSArgs.tlsKeyFile != "" {
|
if secretTLSArgs.tlsCrtFile != "" {
|
||||||
if opts.TLSCrt, err = os.ReadFile(secretTLSArgs.tlsCrtFile); err != nil {
|
if opts.TLSCrt, err = os.ReadFile(secretTLSArgs.tlsCrtFile); err != nil {
|
||||||
return fmt.Errorf("failed to read cert file: %w", err)
|
return fmt.Errorf("failed to read cert file: %w", err)
|
||||||
}
|
}
|
||||||
|
}
|
||||||
|
if secretTLSArgs.tlsKeyFile != "" {
|
||||||
if opts.TLSKey, err = os.ReadFile(secretTLSArgs.tlsKeyFile); err != nil {
|
if opts.TLSKey, err = os.ReadFile(secretTLSArgs.tlsKeyFile); err != nil {
|
||||||
return fmt.Errorf("failed to read key file: %w", err)
|
return fmt.Errorf("failed to read key file: %w", err)
|
||||||
}
|
}
|
||||||
} else if secretTLSArgs.certFile != "" && secretTLSArgs.keyFile != "" {
|
|
||||||
if opts.CertFile, err = os.ReadFile(secretTLSArgs.certFile); err != nil {
|
|
||||||
return fmt.Errorf("failed to read cert file: %w", err)
|
|
||||||
}
|
|
||||||
if opts.KeyFile, err = os.ReadFile(secretTLSArgs.keyFile); err != nil {
|
|
||||||
return fmt.Errorf("failed to read key file: %w", err)
|
|
||||||
}
|
|
||||||
}
|
}
|
||||||
|
|
||||||
secret, err := sourcesecret.Generate(opts)
|
secret, err := sourcesecret.GenerateTLS(opts)
|
||||||
if err != nil {
|
if err != nil {
|
||||||
return err
|
return err
|
||||||
}
|
}
|
||||||
|
|
|
||||||
|
|
@ -18,10 +18,6 @@ func TestCreateTlsSecret(t *testing.T) {
|
||||||
args: "create secret tls certs --namespace=my-namespace --tls-crt-file=./testdata/create_secret/tls/test-cert.pem --tls-key-file=./testdata/create_secret/tls/test-key.pem --ca-crt-file=./testdata/create_secret/tls/test-ca.pem --export",
|
args: "create secret tls certs --namespace=my-namespace --tls-crt-file=./testdata/create_secret/tls/test-cert.pem --tls-key-file=./testdata/create_secret/tls/test-key.pem --ca-crt-file=./testdata/create_secret/tls/test-ca.pem --export",
|
||||||
assert: assertGoldenFile("testdata/create_secret/tls/secret-tls.yaml"),
|
assert: assertGoldenFile("testdata/create_secret/tls/secret-tls.yaml"),
|
||||||
},
|
},
|
||||||
{
|
|
||||||
args: "create secret tls certs --namespace=my-namespace --cert-file=./testdata/create_secret/tls/test-cert.pem --key-file=./testdata/create_secret/tls/test-key.pem --ca-file=./testdata/create_secret/tls/test-ca.pem --export",
|
|
||||||
assert: assertGoldenFile("testdata/create_secret/tls/deprecated-secret-tls.yaml"),
|
|
||||||
},
|
|
||||||
}
|
}
|
||||||
for _, tt := range tests {
|
for _, tt := range tests {
|
||||||
t.Run(tt.name, func(t *testing.T) {
|
t.Run(tt.name, func(t *testing.T) {
|
||||||
|
|
|
||||||
|
|
@ -32,7 +32,7 @@ import (
|
||||||
|
|
||||||
"github.com/fluxcd/pkg/apis/meta"
|
"github.com/fluxcd/pkg/apis/meta"
|
||||||
|
|
||||||
sourcev1 "github.com/fluxcd/source-controller/api/v1beta2"
|
sourcev1 "github.com/fluxcd/source-controller/api/v1"
|
||||||
|
|
||||||
"github.com/fluxcd/flux2/v2/internal/flags"
|
"github.com/fluxcd/flux2/v2/internal/flags"
|
||||||
"github.com/fluxcd/flux2/v2/internal/utils"
|
"github.com/fluxcd/flux2/v2/internal/utils"
|
||||||
|
|
@ -41,8 +41,8 @@ import (
|
||||||
var createSourceBucketCmd = &cobra.Command{
|
var createSourceBucketCmd = &cobra.Command{
|
||||||
Use: "bucket [name]",
|
Use: "bucket [name]",
|
||||||
Short: "Create or update a Bucket source",
|
Short: "Create or update a Bucket source",
|
||||||
Long: withPreviewNote(`The create source bucket command generates a Bucket resource and waits for it to be downloaded.
|
Long: `The create source bucket command generates a Bucket resource and waits for it to be downloaded.
|
||||||
For Buckets with static authentication, the credentials are stored in a Kubernetes secret.`),
|
For Buckets with static authentication, the credentials are stored in a Kubernetes secret.`,
|
||||||
Example: ` # Create a source for a Bucket using static authentication
|
Example: ` # Create a source for a Bucket using static authentication
|
||||||
flux create source bucket podinfo \
|
flux create source bucket podinfo \
|
||||||
--bucket-name=podinfo \
|
--bucket-name=podinfo \
|
||||||
|
|
@ -63,15 +63,16 @@ For Buckets with static authentication, the credentials are stored in a Kubernet
|
||||||
}
|
}
|
||||||
|
|
||||||
type sourceBucketFlags struct {
|
type sourceBucketFlags struct {
|
||||||
name string
|
name string
|
||||||
provider flags.SourceBucketProvider
|
provider flags.SourceBucketProvider
|
||||||
endpoint string
|
endpoint string
|
||||||
accessKey string
|
accessKey string
|
||||||
secretKey string
|
secretKey string
|
||||||
region string
|
region string
|
||||||
insecure bool
|
insecure bool
|
||||||
secretRef string
|
secretRef string
|
||||||
ignorePaths []string
|
proxySecretRef string
|
||||||
|
ignorePaths []string
|
||||||
}
|
}
|
||||||
|
|
||||||
var sourceBucketArgs = newSourceBucketFlags()
|
var sourceBucketArgs = newSourceBucketFlags()
|
||||||
|
|
@ -85,6 +86,7 @@ func init() {
|
||||||
createSourceBucketCmd.Flags().StringVar(&sourceBucketArgs.region, "region", "", "the bucket region")
|
createSourceBucketCmd.Flags().StringVar(&sourceBucketArgs.region, "region", "", "the bucket region")
|
||||||
createSourceBucketCmd.Flags().BoolVar(&sourceBucketArgs.insecure, "insecure", false, "for when connecting to a non-TLS S3 HTTP endpoint")
|
createSourceBucketCmd.Flags().BoolVar(&sourceBucketArgs.insecure, "insecure", false, "for when connecting to a non-TLS S3 HTTP endpoint")
|
||||||
createSourceBucketCmd.Flags().StringVar(&sourceBucketArgs.secretRef, "secret-ref", "", "the name of an existing secret containing credentials")
|
createSourceBucketCmd.Flags().StringVar(&sourceBucketArgs.secretRef, "secret-ref", "", "the name of an existing secret containing credentials")
|
||||||
|
createSourceBucketCmd.Flags().StringVar(&sourceBucketArgs.proxySecretRef, "proxy-secret-ref", "", "the name of an existing secret containing the proxy address and credentials")
|
||||||
createSourceBucketCmd.Flags().StringSliceVar(&sourceBucketArgs.ignorePaths, "ignore-paths", nil, "set paths to ignore in bucket resource (can specify multiple paths with commas: path1,path2)")
|
createSourceBucketCmd.Flags().StringSliceVar(&sourceBucketArgs.ignorePaths, "ignore-paths", nil, "set paths to ignore in bucket resource (can specify multiple paths with commas: path1,path2)")
|
||||||
|
|
||||||
createSourceCmd.AddCommand(createSourceBucketCmd)
|
createSourceCmd.AddCommand(createSourceBucketCmd)
|
||||||
|
|
@ -92,7 +94,7 @@ func init() {
|
||||||
|
|
||||||
func newSourceBucketFlags() sourceBucketFlags {
|
func newSourceBucketFlags() sourceBucketFlags {
|
||||||
return sourceBucketFlags{
|
return sourceBucketFlags{
|
||||||
provider: flags.SourceBucketProvider(sourcev1.GenericBucketProvider),
|
provider: flags.SourceBucketProvider(sourcev1.BucketProviderGeneric),
|
||||||
}
|
}
|
||||||
}
|
}
|
||||||
|
|
||||||
|
|
@ -153,6 +155,12 @@ func createSourceBucketCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
}
|
}
|
||||||
}
|
}
|
||||||
|
|
||||||
|
if sourceBucketArgs.proxySecretRef != "" {
|
||||||
|
bucket.Spec.ProxySecretRef = &meta.LocalObjectReference{
|
||||||
|
Name: sourceBucketArgs.proxySecretRef,
|
||||||
|
}
|
||||||
|
}
|
||||||
|
|
||||||
if createArgs.export {
|
if createArgs.export {
|
||||||
return printExport(exportBucket(bucket))
|
return printExport(exportBucket(bucket))
|
||||||
}
|
}
|
||||||
|
|
|
||||||
|
|
@ -0,0 +1,217 @@
|
||||||
|
/*
|
||||||
|
Copyright 2024 The Flux authors
|
||||||
|
|
||||||
|
Licensed under the Apache License, Version 2.0 (the "License");
|
||||||
|
you may not use this file except in compliance with the License.
|
||||||
|
You may obtain a copy of the License at
|
||||||
|
|
||||||
|
http://www.apache.org/licenses/LICENSE-2.0
|
||||||
|
|
||||||
|
Unless required by applicable law or agreed to in writing, software
|
||||||
|
distributed under the License is distributed on an "AS IS" BASIS,
|
||||||
|
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||||
|
See the License for the specific language governing permissions and
|
||||||
|
limitations under the License.
|
||||||
|
*/
|
||||||
|
|
||||||
|
package main
|
||||||
|
|
||||||
|
import (
|
||||||
|
"context"
|
||||||
|
"fmt"
|
||||||
|
|
||||||
|
"github.com/spf13/cobra"
|
||||||
|
"k8s.io/apimachinery/pkg/api/errors"
|
||||||
|
metav1 "k8s.io/apimachinery/pkg/apis/meta/v1"
|
||||||
|
"k8s.io/apimachinery/pkg/types"
|
||||||
|
"k8s.io/apimachinery/pkg/util/wait"
|
||||||
|
"sigs.k8s.io/controller-runtime/pkg/client"
|
||||||
|
|
||||||
|
"github.com/fluxcd/pkg/apis/meta"
|
||||||
|
sourcev1 "github.com/fluxcd/source-controller/api/v1"
|
||||||
|
|
||||||
|
"github.com/fluxcd/flux2/v2/internal/flags"
|
||||||
|
"github.com/fluxcd/flux2/v2/internal/utils"
|
||||||
|
)
|
||||||
|
|
||||||
|
var createSourceChartCmd = &cobra.Command{
|
||||||
|
Use: "chart [name]",
|
||||||
|
Short: "Create or update a HelmChart source",
|
||||||
|
Long: `The create source chart command generates a HelmChart resource and waits for the chart to be available.`,
|
||||||
|
Example: ` # Create a source for a chart residing in a HelmRepository
|
||||||
|
flux create source chart podinfo \
|
||||||
|
--source=HelmRepository/podinfo \
|
||||||
|
--chart=podinfo \
|
||||||
|
--chart-version=6.x
|
||||||
|
|
||||||
|
# Create a source for a chart residing in a Git repository
|
||||||
|
flux create source chart podinfo \
|
||||||
|
--source=GitRepository/podinfo \
|
||||||
|
--chart=./charts/podinfo
|
||||||
|
|
||||||
|
# Create a source for a chart residing in a S3 Bucket
|
||||||
|
flux create source chart podinfo \
|
||||||
|
--source=Bucket/podinfo \
|
||||||
|
--chart=./charts/podinfo
|
||||||
|
|
||||||
|
# Create a source for a chart from OCI and verify its signature
|
||||||
|
flux create source chart podinfo \
|
||||||
|
--source HelmRepository/podinfo \
|
||||||
|
--chart podinfo \
|
||||||
|
--chart-version=6.6.2 \
|
||||||
|
--verify-provider=cosign \
|
||||||
|
--verify-issuer=https://token.actions.githubusercontent.com \
|
||||||
|
--verify-subject=https://github.com/stefanprodan/podinfo/.github/workflows/release.yml@refs/tags/6.6.2`,
|
||||||
|
RunE: createSourceChartCmdRun,
|
||||||
|
}
|
||||||
|
|
||||||
|
type sourceChartFlags struct {
|
||||||
|
chart string
|
||||||
|
chartVersion string
|
||||||
|
source flags.LocalHelmChartSource
|
||||||
|
reconcileStrategy string
|
||||||
|
verifyProvider flags.SourceOCIVerifyProvider
|
||||||
|
verifySecretRef string
|
||||||
|
verifyOIDCIssuer string
|
||||||
|
verifySubject string
|
||||||
|
}
|
||||||
|
|
||||||
|
var sourceChartArgs sourceChartFlags
|
||||||
|
|
||||||
|
func init() {
|
||||||
|
createSourceChartCmd.Flags().StringVar(&sourceChartArgs.chart, "chart", "", "Helm chart name or path")
|
||||||
|
createSourceChartCmd.Flags().StringVar(&sourceChartArgs.chartVersion, "chart-version", "", "Helm chart version, accepts a semver range (ignored for charts from GitRepository sources)")
|
||||||
|
createSourceChartCmd.Flags().Var(&sourceChartArgs.source, "source", sourceChartArgs.source.Description())
|
||||||
|
createSourceChartCmd.Flags().StringVar(&sourceChartArgs.reconcileStrategy, "reconcile-strategy", "ChartVersion", "the reconcile strategy for helm chart (accepted values: Revision and ChartRevision)")
|
||||||
|
createSourceChartCmd.Flags().Var(&sourceChartArgs.verifyProvider, "verify-provider", sourceOCIRepositoryArgs.verifyProvider.Description())
|
||||||
|
createSourceChartCmd.Flags().StringVar(&sourceChartArgs.verifySecretRef, "verify-secret-ref", "", "the name of a secret to use for signature verification")
|
||||||
|
createSourceChartCmd.Flags().StringVar(&sourceChartArgs.verifySubject, "verify-subject", "", "regular expression to use for the OIDC subject during signature verification")
|
||||||
|
createSourceChartCmd.Flags().StringVar(&sourceChartArgs.verifyOIDCIssuer, "verify-issuer", "", "regular expression to use for the OIDC issuer during signature verification")
|
||||||
|
|
||||||
|
createSourceCmd.AddCommand(createSourceChartCmd)
|
||||||
|
}
|
||||||
|
|
||||||
|
func createSourceChartCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
|
name := args[0]
|
||||||
|
|
||||||
|
if sourceChartArgs.source.Kind == "" || sourceChartArgs.source.Name == "" {
|
||||||
|
return fmt.Errorf("chart source is required")
|
||||||
|
}
|
||||||
|
|
||||||
|
if sourceChartArgs.chart == "" {
|
||||||
|
return fmt.Errorf("chart name or path is required")
|
||||||
|
}
|
||||||
|
|
||||||
|
logger.Generatef("generating HelmChart source")
|
||||||
|
|
||||||
|
sourceLabels, err := parseLabels()
|
||||||
|
if err != nil {
|
||||||
|
return err
|
||||||
|
}
|
||||||
|
|
||||||
|
helmChart := &sourcev1.HelmChart{
|
||||||
|
ObjectMeta: metav1.ObjectMeta{
|
||||||
|
Name: name,
|
||||||
|
Namespace: *kubeconfigArgs.Namespace,
|
||||||
|
Labels: sourceLabels,
|
||||||
|
},
|
||||||
|
Spec: sourcev1.HelmChartSpec{
|
||||||
|
Chart: sourceChartArgs.chart,
|
||||||
|
Version: sourceChartArgs.chartVersion,
|
||||||
|
Interval: metav1.Duration{
|
||||||
|
Duration: createArgs.interval,
|
||||||
|
},
|
||||||
|
ReconcileStrategy: sourceChartArgs.reconcileStrategy,
|
||||||
|
SourceRef: sourcev1.LocalHelmChartSourceReference{
|
||||||
|
Kind: sourceChartArgs.source.Kind,
|
||||||
|
Name: sourceChartArgs.source.Name,
|
||||||
|
},
|
||||||
|
},
|
||||||
|
}
|
||||||
|
|
||||||
|
if provider := sourceChartArgs.verifyProvider.String(); provider != "" {
|
||||||
|
helmChart.Spec.Verify = &sourcev1.OCIRepositoryVerification{
|
||||||
|
Provider: provider,
|
||||||
|
}
|
||||||
|
if secretName := sourceChartArgs.verifySecretRef; secretName != "" {
|
||||||
|
helmChart.Spec.Verify.SecretRef = &meta.LocalObjectReference{
|
||||||
|
Name: secretName,
|
||||||
|
}
|
||||||
|
}
|
||||||
|
verifyIssuer := sourceChartArgs.verifyOIDCIssuer
|
||||||
|
verifySubject := sourceChartArgs.verifySubject
|
||||||
|
if verifyIssuer != "" || verifySubject != "" {
|
||||||
|
helmChart.Spec.Verify.MatchOIDCIdentity = []sourcev1.OIDCIdentityMatch{{
|
||||||
|
Issuer: verifyIssuer,
|
||||||
|
Subject: verifySubject,
|
||||||
|
}}
|
||||||
|
}
|
||||||
|
} else if sourceChartArgs.verifySecretRef != "" {
|
||||||
|
return fmt.Errorf("a verification provider must be specified when a secret is specified")
|
||||||
|
} else if sourceChartArgs.verifyOIDCIssuer != "" || sourceOCIRepositoryArgs.verifySubject != "" {
|
||||||
|
return fmt.Errorf("a verification provider must be specified when OIDC issuer/subject is specified")
|
||||||
|
}
|
||||||
|
|
||||||
|
if createArgs.export {
|
||||||
|
return printExport(exportHelmChart(helmChart))
|
||||||
|
}
|
||||||
|
|
||||||
|
logger.Actionf("applying HelmChart source")
|
||||||
|
|
||||||
|
ctx, cancel := context.WithTimeout(context.Background(), rootArgs.timeout)
|
||||||
|
defer cancel()
|
||||||
|
|
||||||
|
kubeClient, err := utils.KubeClient(kubeconfigArgs, kubeclientOptions)
|
||||||
|
if err != nil {
|
||||||
|
return err
|
||||||
|
}
|
||||||
|
|
||||||
|
namespacedName, err := upsertHelmChart(ctx, kubeClient, helmChart)
|
||||||
|
if err != nil {
|
||||||
|
return err
|
||||||
|
}
|
||||||
|
|
||||||
|
logger.Waitingf("waiting for HelmChart source reconciliation")
|
||||||
|
readyConditionFunc := isObjectReadyConditionFunc(kubeClient, namespacedName, helmChart)
|
||||||
|
if err := wait.PollUntilContextTimeout(ctx, rootArgs.pollInterval, rootArgs.timeout, true, readyConditionFunc); err != nil {
|
||||||
|
return err
|
||||||
|
}
|
||||||
|
logger.Successf("HelmChart source reconciliation completed")
|
||||||
|
|
||||||
|
if helmChart.Status.Artifact == nil {
|
||||||
|
return fmt.Errorf("HelmChart source reconciliation completed but no artifact was found")
|
||||||
|
}
|
||||||
|
logger.Successf("fetched revision: %s", helmChart.Status.Artifact.Revision)
|
||||||
|
return nil
|
||||||
|
}
|
||||||
|
|
||||||
|
func upsertHelmChart(ctx context.Context, kubeClient client.Client,
|
||||||
|
helmChart *sourcev1.HelmChart) (types.NamespacedName, error) {
|
||||||
|
namespacedName := types.NamespacedName{
|
||||||
|
Namespace: helmChart.GetNamespace(),
|
||||||
|
Name: helmChart.GetName(),
|
||||||
|
}
|
||||||
|
|
||||||
|
var existing sourcev1.HelmChart
|
||||||
|
err := kubeClient.Get(ctx, namespacedName, &existing)
|
||||||
|
if err != nil {
|
||||||
|
if errors.IsNotFound(err) {
|
||||||
|
if err := kubeClient.Create(ctx, helmChart); err != nil {
|
||||||
|
return namespacedName, err
|
||||||
|
} else {
|
||||||
|
logger.Successf("source created")
|
||||||
|
return namespacedName, nil
|
||||||
|
}
|
||||||
|
}
|
||||||
|
return namespacedName, err
|
||||||
|
}
|
||||||
|
|
||||||
|
existing.Labels = helmChart.Labels
|
||||||
|
existing.Spec = helmChart.Spec
|
||||||
|
if err := kubeClient.Update(ctx, &existing); err != nil {
|
||||||
|
return namespacedName, err
|
||||||
|
}
|
||||||
|
helmChart = &existing
|
||||||
|
logger.Successf("source updated")
|
||||||
|
return namespacedName, nil
|
||||||
|
}
|
||||||
|
|
@ -0,0 +1,91 @@
|
||||||
|
//go:build unit
|
||||||
|
// +build unit
|
||||||
|
|
||||||
|
/*
|
||||||
|
Copyright 2024 The Flux authors
|
||||||
|
|
||||||
|
Licensed under the Apache License, Version 2.0 (the "License");
|
||||||
|
you may not use this file except in compliance with the License.
|
||||||
|
You may obtain a copy of the License at
|
||||||
|
|
||||||
|
http://www.apache.org/licenses/LICENSE-2.0
|
||||||
|
|
||||||
|
Unless required by applicable law or agreed to in writing, software
|
||||||
|
distributed under the License is distributed on an "AS IS" BASIS,
|
||||||
|
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||||
|
See the License for the specific language governing permissions and
|
||||||
|
limitations under the License.
|
||||||
|
*/
|
||||||
|
|
||||||
|
package main
|
||||||
|
|
||||||
|
import "testing"
|
||||||
|
|
||||||
|
func TestCreateSourceChart(t *testing.T) {
|
||||||
|
tmpl := map[string]string{
|
||||||
|
"fluxns": allocateNamespace("flux-system"),
|
||||||
|
}
|
||||||
|
setupSourceChart(t, tmpl)
|
||||||
|
|
||||||
|
tests := []struct {
|
||||||
|
name string
|
||||||
|
args string
|
||||||
|
assert assertFunc
|
||||||
|
}{
|
||||||
|
{
|
||||||
|
name: "missing name",
|
||||||
|
args: "create source chart --export",
|
||||||
|
assert: assertError("name is required"),
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "missing source reference",
|
||||||
|
args: "create source chart podinfo --export ",
|
||||||
|
assert: assertError("chart source is required"),
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "missing chart name",
|
||||||
|
args: "create source chart podinfo --source helmrepository/podinfo --export",
|
||||||
|
assert: assertError("chart name or path is required"),
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "unknown source kind",
|
||||||
|
args: "create source chart podinfo --source foobar/podinfo --export",
|
||||||
|
assert: assertError(`invalid argument "foobar/podinfo" for "--source" flag: source kind 'foobar' is not supported, must be one of: HelmRepository, GitRepository, Bucket`),
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "basic chart",
|
||||||
|
args: "create source chart podinfo --source helmrepository/podinfo --chart podinfo --export",
|
||||||
|
assert: assertGoldenTemplateFile("testdata/create_source_chart/basic.yaml", tmpl),
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "chart with basic signature verification",
|
||||||
|
args: "create source chart podinfo --source helmrepository/podinfo --chart podinfo --verify-provider cosign --export",
|
||||||
|
assert: assertGoldenTemplateFile("testdata/create_source_chart/verify_basic.yaml", tmpl),
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "unknown signature verification provider",
|
||||||
|
args: "create source chart podinfo --source helmrepository/podinfo --chart podinfo --verify-provider foobar --export",
|
||||||
|
assert: assertError(`invalid argument "foobar" for "--verify-provider" flag: source OCI verify provider 'foobar' is not supported, must be one of: cosign`),
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "chart with complete signature verification",
|
||||||
|
args: "create source chart podinfo --source helmrepository/podinfo --chart podinfo --verify-provider cosign --verify-issuer foo --verify-subject bar --export",
|
||||||
|
assert: assertGoldenTemplateFile("testdata/create_source_chart/verify_complete.yaml", tmpl),
|
||||||
|
},
|
||||||
|
}
|
||||||
|
|
||||||
|
for _, tt := range tests {
|
||||||
|
t.Run(tt.name, func(t *testing.T) {
|
||||||
|
cmd := cmdTestCase{
|
||||||
|
args: tt.args + " -n " + tmpl["fluxns"],
|
||||||
|
assert: tt.assert,
|
||||||
|
}
|
||||||
|
cmd.runTestCmd(t)
|
||||||
|
})
|
||||||
|
}
|
||||||
|
}
|
||||||
|
|
||||||
|
func setupSourceChart(t *testing.T, tmpl map[string]string) {
|
||||||
|
t.Helper()
|
||||||
|
testEnv.CreateObjectFile("./testdata/create_source_chart/setup-source.yaml", tmpl, t)
|
||||||
|
}
|
||||||
|
|
@ -44,23 +44,26 @@ import (
|
||||||
)
|
)
|
||||||
|
|
||||||
type sourceGitFlags struct {
|
type sourceGitFlags struct {
|
||||||
url string
|
url string
|
||||||
branch string
|
branch string
|
||||||
tag string
|
tag string
|
||||||
semver string
|
semver string
|
||||||
refName string
|
refName string
|
||||||
commit string
|
commit string
|
||||||
username string
|
username string
|
||||||
password string
|
password string
|
||||||
keyAlgorithm flags.PublicKeyAlgorithm
|
keyAlgorithm flags.PublicKeyAlgorithm
|
||||||
keyRSABits flags.RSAKeyBits
|
keyRSABits flags.RSAKeyBits
|
||||||
keyECDSACurve flags.ECDSACurve
|
keyECDSACurve flags.ECDSACurve
|
||||||
secretRef string
|
secretRef string
|
||||||
caFile string
|
proxySecretRef string
|
||||||
privateKeyFile string
|
provider flags.SourceGitProvider
|
||||||
recurseSubmodules bool
|
caFile string
|
||||||
silent bool
|
privateKeyFile string
|
||||||
ignorePaths []string
|
recurseSubmodules bool
|
||||||
|
silent bool
|
||||||
|
ignorePaths []string
|
||||||
|
sparseCheckoutPaths []string
|
||||||
}
|
}
|
||||||
|
|
||||||
var createSourceGitCmd = &cobra.Command{
|
var createSourceGitCmd = &cobra.Command{
|
||||||
|
|
@ -119,7 +122,13 @@ For private Git repositories, the basic authentication credentials are stored in
|
||||||
--url=https://github.com/stefanprodan/podinfo \
|
--url=https://github.com/stefanprodan/podinfo \
|
||||||
--branch=master \
|
--branch=master \
|
||||||
--username=username \
|
--username=username \
|
||||||
--password=password`,
|
--password=password
|
||||||
|
|
||||||
|
# Create a source for a Git repository using azure provider
|
||||||
|
flux create source git podinfo \
|
||||||
|
--url=https://dev.azure.com/foo/bar/_git/podinfo \
|
||||||
|
--branch=master \
|
||||||
|
--provider=azure`,
|
||||||
RunE: createSourceGitCmdRun,
|
RunE: createSourceGitCmdRun,
|
||||||
}
|
}
|
||||||
|
|
||||||
|
|
@ -130,20 +139,23 @@ func init() {
|
||||||
createSourceGitCmd.Flags().StringVar(&sourceGitArgs.branch, "branch", "", "git branch")
|
createSourceGitCmd.Flags().StringVar(&sourceGitArgs.branch, "branch", "", "git branch")
|
||||||
createSourceGitCmd.Flags().StringVar(&sourceGitArgs.tag, "tag", "", "git tag")
|
createSourceGitCmd.Flags().StringVar(&sourceGitArgs.tag, "tag", "", "git tag")
|
||||||
createSourceGitCmd.Flags().StringVar(&sourceGitArgs.semver, "tag-semver", "", "git tag semver range")
|
createSourceGitCmd.Flags().StringVar(&sourceGitArgs.semver, "tag-semver", "", "git tag semver range")
|
||||||
createSourceGitCmd.Flags().StringVar(&sourceGitArgs.refName, "ref-name", "", " git reference name")
|
createSourceGitCmd.Flags().StringVar(&sourceGitArgs.refName, "ref-name", "", "git reference name")
|
||||||
createSourceGitCmd.Flags().StringVar(&sourceGitArgs.commit, "commit", "", "git commit")
|
createSourceGitCmd.Flags().StringVar(&sourceGitArgs.commit, "commit", "", "git commit")
|
||||||
createSourceGitCmd.Flags().StringVarP(&sourceGitArgs.username, "username", "u", "", "basic authentication username")
|
createSourceGitCmd.Flags().StringVarP(&sourceGitArgs.username, "username", "u", "", "basic authentication username")
|
||||||
createSourceGitCmd.Flags().StringVarP(&sourceGitArgs.password, "password", "p", "", "basic authentication password")
|
createSourceGitCmd.Flags().StringVarP(&sourceGitArgs.password, "password", "p", "", "basic authentication password")
|
||||||
createSourceGitCmd.Flags().Var(&sourceGitArgs.keyAlgorithm, "ssh-key-algorithm", sourceGitArgs.keyAlgorithm.Description())
|
createSourceGitCmd.Flags().Var(&sourceGitArgs.keyAlgorithm, "ssh-key-algorithm", sourceGitArgs.keyAlgorithm.Description())
|
||||||
createSourceGitCmd.Flags().Var(&sourceGitArgs.keyRSABits, "ssh-rsa-bits", sourceGitArgs.keyRSABits.Description())
|
createSourceGitCmd.Flags().Var(&sourceGitArgs.keyRSABits, "ssh-rsa-bits", sourceGitArgs.keyRSABits.Description())
|
||||||
createSourceGitCmd.Flags().Var(&sourceGitArgs.keyECDSACurve, "ssh-ecdsa-curve", sourceGitArgs.keyECDSACurve.Description())
|
createSourceGitCmd.Flags().Var(&sourceGitArgs.keyECDSACurve, "ssh-ecdsa-curve", sourceGitArgs.keyECDSACurve.Description())
|
||||||
createSourceGitCmd.Flags().StringVar(&sourceGitArgs.secretRef, "secret-ref", "", "the name of an existing secret containing SSH or basic credentials")
|
createSourceGitCmd.Flags().StringVar(&sourceGitArgs.secretRef, "secret-ref", "", "the name of an existing secret containing SSH or basic credentials or github app authentication")
|
||||||
|
createSourceGitCmd.Flags().StringVar(&sourceGitArgs.proxySecretRef, "proxy-secret-ref", "", "the name of an existing secret containing the proxy address and credentials")
|
||||||
|
createSourceGitCmd.Flags().Var(&sourceGitArgs.provider, "provider", sourceGitArgs.provider.Description())
|
||||||
createSourceGitCmd.Flags().StringVar(&sourceGitArgs.caFile, "ca-file", "", "path to TLS CA file used for validating self-signed certificates")
|
createSourceGitCmd.Flags().StringVar(&sourceGitArgs.caFile, "ca-file", "", "path to TLS CA file used for validating self-signed certificates")
|
||||||
createSourceGitCmd.Flags().StringVar(&sourceGitArgs.privateKeyFile, "private-key-file", "", "path to a passwordless private key file used for authenticating to the Git SSH server")
|
createSourceGitCmd.Flags().StringVar(&sourceGitArgs.privateKeyFile, "private-key-file", "", "path to a passwordless private key file used for authenticating to the Git SSH server")
|
||||||
createSourceGitCmd.Flags().BoolVar(&sourceGitArgs.recurseSubmodules, "recurse-submodules", false,
|
createSourceGitCmd.Flags().BoolVar(&sourceGitArgs.recurseSubmodules, "recurse-submodules", false,
|
||||||
"when enabled, configures the GitRepository source to initialize and include Git submodules in the artifact it produces")
|
"when enabled, configures the GitRepository source to initialize and include Git submodules in the artifact it produces")
|
||||||
createSourceGitCmd.Flags().BoolVarP(&sourceGitArgs.silent, "silent", "s", false, "assumes the deploy key is already setup, skips confirmation")
|
createSourceGitCmd.Flags().BoolVarP(&sourceGitArgs.silent, "silent", "s", false, "assumes the deploy key is already setup, skips confirmation")
|
||||||
createSourceGitCmd.Flags().StringSliceVar(&sourceGitArgs.ignorePaths, "ignore-paths", nil, "set paths to ignore in git resource (can specify multiple paths with commas: path1,path2)")
|
createSourceGitCmd.Flags().StringSliceVar(&sourceGitArgs.ignorePaths, "ignore-paths", nil, "set paths to ignore in git resource (can specify multiple paths with commas: path1,path2)")
|
||||||
|
createSourceGitCmd.Flags().StringSliceVar(&sourceGitArgs.sparseCheckoutPaths, "sparse-checkout-paths", nil, "set paths to sparse checkout in git resource (can specify multiple paths with commas: path1,path2)")
|
||||||
|
|
||||||
createSourceCmd.AddCommand(createSourceGitCmd)
|
createSourceCmd.AddCommand(createSourceGitCmd)
|
||||||
}
|
}
|
||||||
|
|
@ -210,6 +222,7 @@ func createSourceGitCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
RecurseSubmodules: sourceGitArgs.recurseSubmodules,
|
RecurseSubmodules: sourceGitArgs.recurseSubmodules,
|
||||||
Reference: &sourcev1.GitRepositoryRef{},
|
Reference: &sourcev1.GitRepositoryRef{},
|
||||||
Ignore: ignorePaths,
|
Ignore: ignorePaths,
|
||||||
|
SparseCheckout: sourceGitArgs.sparseCheckoutPaths,
|
||||||
},
|
},
|
||||||
}
|
}
|
||||||
|
|
||||||
|
|
@ -236,6 +249,16 @@ func createSourceGitCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
}
|
}
|
||||||
}
|
}
|
||||||
|
|
||||||
|
if sourceGitArgs.proxySecretRef != "" {
|
||||||
|
gitRepository.Spec.ProxySecretRef = &meta.LocalObjectReference{
|
||||||
|
Name: sourceGitArgs.proxySecretRef,
|
||||||
|
}
|
||||||
|
}
|
||||||
|
|
||||||
|
if provider := sourceGitArgs.provider.String(); provider != "" {
|
||||||
|
gitRepository.Spec.Provider = provider
|
||||||
|
}
|
||||||
|
|
||||||
if createArgs.export {
|
if createArgs.export {
|
||||||
return printExport(exportGit(&gitRepository))
|
return printExport(exportGit(&gitRepository))
|
||||||
}
|
}
|
||||||
|
|
@ -273,7 +296,7 @@ func createSourceGitCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
if err != nil {
|
if err != nil {
|
||||||
return fmt.Errorf("unable to read TLS CA file: %w", err)
|
return fmt.Errorf("unable to read TLS CA file: %w", err)
|
||||||
}
|
}
|
||||||
secretOpts.CAFile = caBundle
|
secretOpts.CACrt = caBundle
|
||||||
}
|
}
|
||||||
secretOpts.Username = sourceGitArgs.username
|
secretOpts.Username = sourceGitArgs.username
|
||||||
secretOpts.Password = sourceGitArgs.password
|
secretOpts.Password = sourceGitArgs.password
|
||||||
|
|
@ -282,7 +305,7 @@ func createSourceGitCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
secretOpts.Username = sourceGitArgs.username
|
secretOpts.Username = sourceGitArgs.username
|
||||||
secretOpts.Password = sourceGitArgs.password
|
secretOpts.Password = sourceGitArgs.password
|
||||||
}
|
}
|
||||||
secret, err := sourcesecret.Generate(secretOpts)
|
secret, err := sourcesecret.GenerateGit(secretOpts)
|
||||||
if err != nil {
|
if err != nil {
|
||||||
return err
|
return err
|
||||||
}
|
}
|
||||||
|
|
|
||||||
|
|
@ -87,7 +87,7 @@ func (r *reconciler) conditionFunc() (bool, error) {
|
||||||
}
|
}
|
||||||
|
|
||||||
func TestCreateSourceGitExport(t *testing.T) {
|
func TestCreateSourceGitExport(t *testing.T) {
|
||||||
var command = "create source git podinfo --url=https://github.com/stefanprodan/podinfo --branch=master --ignore-paths .cosign,non-existent-dir/ -n default --interval 1m --export --timeout=" + testTimeout.String()
|
var command = "create source git podinfo --url=https://github.com/stefanprodan/podinfo --branch=master --sparse-checkout-paths .cosign,non-existent-dir/ --ignore-paths .cosign,non-existent-dir/ -n default --interval 1m --export --timeout=" + testTimeout.String()
|
||||||
|
|
||||||
cases := []struct {
|
cases := []struct {
|
||||||
name string
|
name string
|
||||||
|
|
@ -134,6 +134,36 @@ func TestCreateSourceGitExport(t *testing.T) {
|
||||||
args: "create source git podinfo --namespace=flux-system --url=https://github.com/stefanprodan/podinfo --branch=test --interval=1m0s --export",
|
args: "create source git podinfo --namespace=flux-system --url=https://github.com/stefanprodan/podinfo --branch=test --interval=1m0s --export",
|
||||||
assert: assertGoldenFile("testdata/create_source_git/source-git-branch.yaml"),
|
assert: assertGoldenFile("testdata/create_source_git/source-git-branch.yaml"),
|
||||||
},
|
},
|
||||||
|
{
|
||||||
|
name: "source with generic provider",
|
||||||
|
args: "create source git podinfo --namespace=flux-system --url=https://github.com/stefanprodan/podinfo --provider generic --branch=test --interval=1m0s --export",
|
||||||
|
assert: assertGoldenFile("testdata/create_source_git/source-git-provider-generic.yaml"),
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "source with azure provider",
|
||||||
|
args: "create source git podinfo --namespace=flux-system --url=https://dev.azure.com/foo/bar/_git/podinfo --provider azure --branch=test --interval=1m0s --export",
|
||||||
|
assert: assertGoldenFile("testdata/create_source_git/source-git-provider-azure.yaml"),
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "source with github provider",
|
||||||
|
args: "create source git podinfo --namespace=flux-system --url=https://github.com/stefanprodan/podinfo --provider github --branch=test --interval=1m0s --secret-ref appinfo --export",
|
||||||
|
assert: assertGoldenFile("testdata/create_source_git/source-git-provider-github.yaml"),
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "source with invalid provider",
|
||||||
|
args: "create source git podinfo --namespace=flux-system --url=https://dev.azure.com/foo/bar/_git/podinfo --provider dummy --branch=test --interval=1m0s --export",
|
||||||
|
assert: assertError("invalid argument \"dummy\" for \"--provider\" flag: source Git provider 'dummy' is not supported, must be one of: generic|azure|github"),
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "source with empty provider",
|
||||||
|
args: "create source git podinfo --namespace=flux-system --url=https://dev.azure.com/foo/bar/_git/podinfo --provider \"\" --branch=test --interval=1m0s --export",
|
||||||
|
assert: assertError("invalid argument \"\" for \"--provider\" flag: no source Git provider given, please specify the Git provider name"),
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "source with no provider",
|
||||||
|
args: "create source git podinfo --namespace=flux-system --url=https://dev.azure.com/foo/bar/_git/podinfo --branch=test --interval=1m0s --export --provider",
|
||||||
|
assert: assertError("flag needs an argument: --provider"),
|
||||||
|
},
|
||||||
}
|
}
|
||||||
for _, tc := range cases {
|
for _, tc := range cases {
|
||||||
t.Run(tc.name, func(t *testing.T) {
|
t.Run(tc.name, func(t *testing.T) {
|
||||||
|
|
|
||||||
|
|
@ -22,7 +22,6 @@ import (
|
||||||
"net/url"
|
"net/url"
|
||||||
"os"
|
"os"
|
||||||
|
|
||||||
"github.com/fluxcd/pkg/apis/meta"
|
|
||||||
"github.com/spf13/cobra"
|
"github.com/spf13/cobra"
|
||||||
corev1 "k8s.io/api/core/v1"
|
corev1 "k8s.io/api/core/v1"
|
||||||
"k8s.io/apimachinery/pkg/api/errors"
|
"k8s.io/apimachinery/pkg/api/errors"
|
||||||
|
|
@ -32,7 +31,8 @@ import (
|
||||||
"sigs.k8s.io/controller-runtime/pkg/client"
|
"sigs.k8s.io/controller-runtime/pkg/client"
|
||||||
"sigs.k8s.io/yaml"
|
"sigs.k8s.io/yaml"
|
||||||
|
|
||||||
sourcev1 "github.com/fluxcd/source-controller/api/v1beta2"
|
"github.com/fluxcd/pkg/apis/meta"
|
||||||
|
sourcev1 "github.com/fluxcd/source-controller/api/v1"
|
||||||
|
|
||||||
"github.com/fluxcd/flux2/v2/internal/utils"
|
"github.com/fluxcd/flux2/v2/internal/utils"
|
||||||
"github.com/fluxcd/flux2/v2/pkg/manifestgen/sourcesecret"
|
"github.com/fluxcd/flux2/v2/pkg/manifestgen/sourcesecret"
|
||||||
|
|
@ -41,8 +41,8 @@ import (
|
||||||
var createSourceHelmCmd = &cobra.Command{
|
var createSourceHelmCmd = &cobra.Command{
|
||||||
Use: "helm [name]",
|
Use: "helm [name]",
|
||||||
Short: "Create or update a HelmRepository source",
|
Short: "Create or update a HelmRepository source",
|
||||||
Long: withPreviewNote(`The create source helm command generates a HelmRepository resource and waits for it to fetch the index.
|
Long: `The create source helm command generates a HelmRepository resource and waits for it to fetch the index.
|
||||||
For private Helm repositories, the basic authentication credentials are stored in a Kubernetes secret.`),
|
For private Helm repositories, the basic authentication credentials are stored in a Kubernetes secret.`,
|
||||||
Example: ` # Create a source for an HTTPS public Helm repository
|
Example: ` # Create a source for an HTTPS public Helm repository
|
||||||
flux create source helm podinfo \
|
flux create source helm podinfo \
|
||||||
--url=https://stefanprodan.github.io/podinfo \
|
--url=https://stefanprodan.github.io/podinfo \
|
||||||
|
|
@ -197,12 +197,12 @@ func createSourceHelmCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
Namespace: *kubeconfigArgs.Namespace,
|
Namespace: *kubeconfigArgs.Namespace,
|
||||||
Username: sourceHelmArgs.username,
|
Username: sourceHelmArgs.username,
|
||||||
Password: sourceHelmArgs.password,
|
Password: sourceHelmArgs.password,
|
||||||
CAFile: caBundle,
|
CACrt: caBundle,
|
||||||
CertFile: certFile,
|
TLSCrt: certFile,
|
||||||
KeyFile: keyFile,
|
TLSKey: keyFile,
|
||||||
ManifestFile: sourcesecret.MakeDefaultOptions().ManifestFile,
|
ManifestFile: sourcesecret.MakeDefaultOptions().ManifestFile,
|
||||||
}
|
}
|
||||||
secret, err := sourcesecret.Generate(secretOpts)
|
secret, err := sourcesecret.GenerateHelm(secretOpts)
|
||||||
if err != nil {
|
if err != nil {
|
||||||
return err
|
return err
|
||||||
}
|
}
|
||||||
|
|
|
||||||
|
|
@ -29,8 +29,7 @@ import (
|
||||||
"sigs.k8s.io/controller-runtime/pkg/client"
|
"sigs.k8s.io/controller-runtime/pkg/client"
|
||||||
|
|
||||||
"github.com/fluxcd/pkg/apis/meta"
|
"github.com/fluxcd/pkg/apis/meta"
|
||||||
|
sourcev1 "github.com/fluxcd/source-controller/api/v1"
|
||||||
sourcev1 "github.com/fluxcd/source-controller/api/v1beta2"
|
|
||||||
|
|
||||||
"github.com/fluxcd/flux2/v2/internal/flags"
|
"github.com/fluxcd/flux2/v2/internal/flags"
|
||||||
"github.com/fluxcd/flux2/v2/internal/utils"
|
"github.com/fluxcd/flux2/v2/internal/utils"
|
||||||
|
|
@ -43,25 +42,37 @@ var createSourceOCIRepositoryCmd = &cobra.Command{
|
||||||
Example: ` # Create an OCIRepository for a public container image
|
Example: ` # Create an OCIRepository for a public container image
|
||||||
flux create source oci podinfo \
|
flux create source oci podinfo \
|
||||||
--url=oci://ghcr.io/stefanprodan/manifests/podinfo \
|
--url=oci://ghcr.io/stefanprodan/manifests/podinfo \
|
||||||
--tag=6.1.6 \
|
--tag=6.6.2 \
|
||||||
--interval=10m
|
--interval=10m
|
||||||
|
|
||||||
|
# Create an OCIRepository with OIDC signature verification
|
||||||
|
flux create source oci podinfo \
|
||||||
|
--url=oci://ghcr.io/stefanprodan/manifests/podinfo \
|
||||||
|
--tag=6.6.2 \
|
||||||
|
--interval=10m \
|
||||||
|
--verify-provider=cosign \
|
||||||
|
--verify-subject="^https://github.com/stefanprodan/podinfo/.github/workflows/release.yml@refs/tags/6.6.2$" \
|
||||||
|
--verify-issuer="^https://token.actions.githubusercontent.com$"
|
||||||
`,
|
`,
|
||||||
RunE: createSourceOCIRepositoryCmdRun,
|
RunE: createSourceOCIRepositoryCmdRun,
|
||||||
}
|
}
|
||||||
|
|
||||||
type sourceOCIRepositoryFlags struct {
|
type sourceOCIRepositoryFlags struct {
|
||||||
url string
|
url string
|
||||||
tag string
|
tag string
|
||||||
semver string
|
semver string
|
||||||
digest string
|
digest string
|
||||||
secretRef string
|
secretRef string
|
||||||
serviceAccount string
|
proxySecretRef string
|
||||||
certSecretRef string
|
serviceAccount string
|
||||||
verifyProvider flags.SourceOCIVerifyProvider
|
certSecretRef string
|
||||||
verifySecretRef string
|
verifyProvider flags.SourceOCIVerifyProvider
|
||||||
ignorePaths []string
|
verifySecretRef string
|
||||||
provider flags.SourceOCIProvider
|
verifyOIDCIssuer string
|
||||||
insecure bool
|
verifySubject string
|
||||||
|
ignorePaths []string
|
||||||
|
provider flags.SourceOCIProvider
|
||||||
|
insecure bool
|
||||||
}
|
}
|
||||||
|
|
||||||
var sourceOCIRepositoryArgs = newSourceOCIFlags()
|
var sourceOCIRepositoryArgs = newSourceOCIFlags()
|
||||||
|
|
@ -79,10 +90,13 @@ func init() {
|
||||||
createSourceOCIRepositoryCmd.Flags().StringVar(&sourceOCIRepositoryArgs.semver, "tag-semver", "", "the OCI artifact tag semver range")
|
createSourceOCIRepositoryCmd.Flags().StringVar(&sourceOCIRepositoryArgs.semver, "tag-semver", "", "the OCI artifact tag semver range")
|
||||||
createSourceOCIRepositoryCmd.Flags().StringVar(&sourceOCIRepositoryArgs.digest, "digest", "", "the OCI artifact digest")
|
createSourceOCIRepositoryCmd.Flags().StringVar(&sourceOCIRepositoryArgs.digest, "digest", "", "the OCI artifact digest")
|
||||||
createSourceOCIRepositoryCmd.Flags().StringVar(&sourceOCIRepositoryArgs.secretRef, "secret-ref", "", "the name of the Kubernetes image pull secret (type 'kubernetes.io/dockerconfigjson')")
|
createSourceOCIRepositoryCmd.Flags().StringVar(&sourceOCIRepositoryArgs.secretRef, "secret-ref", "", "the name of the Kubernetes image pull secret (type 'kubernetes.io/dockerconfigjson')")
|
||||||
|
createSourceOCIRepositoryCmd.Flags().StringVar(&sourceOCIRepositoryArgs.proxySecretRef, "proxy-secret-ref", "", "the name of an existing secret containing the proxy address and credentials")
|
||||||
createSourceOCIRepositoryCmd.Flags().StringVar(&sourceOCIRepositoryArgs.serviceAccount, "service-account", "", "the name of the Kubernetes service account that refers to an image pull secret")
|
createSourceOCIRepositoryCmd.Flags().StringVar(&sourceOCIRepositoryArgs.serviceAccount, "service-account", "", "the name of the Kubernetes service account that refers to an image pull secret")
|
||||||
createSourceOCIRepositoryCmd.Flags().StringVar(&sourceOCIRepositoryArgs.certSecretRef, "cert-ref", "", "the name of a secret to use for TLS certificates")
|
createSourceOCIRepositoryCmd.Flags().StringVar(&sourceOCIRepositoryArgs.certSecretRef, "cert-ref", "", "the name of a secret to use for TLS certificates")
|
||||||
createSourceOCIRepositoryCmd.Flags().Var(&sourceOCIRepositoryArgs.verifyProvider, "verify-provider", sourceOCIRepositoryArgs.verifyProvider.Description())
|
createSourceOCIRepositoryCmd.Flags().Var(&sourceOCIRepositoryArgs.verifyProvider, "verify-provider", sourceOCIRepositoryArgs.verifyProvider.Description())
|
||||||
createSourceOCIRepositoryCmd.Flags().StringVar(&sourceOCIRepositoryArgs.verifySecretRef, "verify-secret-ref", "", "the name of a secret to use for signature verification")
|
createSourceOCIRepositoryCmd.Flags().StringVar(&sourceOCIRepositoryArgs.verifySecretRef, "verify-secret-ref", "", "the name of a secret to use for signature verification")
|
||||||
|
createSourceOCIRepositoryCmd.Flags().StringVar(&sourceOCIRepositoryArgs.verifySubject, "verify-subject", "", "regular expression to use for the OIDC subject during signature verification")
|
||||||
|
createSourceOCIRepositoryCmd.Flags().StringVar(&sourceOCIRepositoryArgs.verifyOIDCIssuer, "verify-issuer", "", "regular expression to use for the OIDC issuer during signature verification")
|
||||||
createSourceOCIRepositoryCmd.Flags().StringSliceVar(&sourceOCIRepositoryArgs.ignorePaths, "ignore-paths", nil, "set paths to ignore resources (can specify multiple paths with commas: path1,path2)")
|
createSourceOCIRepositoryCmd.Flags().StringSliceVar(&sourceOCIRepositoryArgs.ignorePaths, "ignore-paths", nil, "set paths to ignore resources (can specify multiple paths with commas: path1,path2)")
|
||||||
createSourceOCIRepositoryCmd.Flags().BoolVar(&sourceOCIRepositoryArgs.insecure, "insecure", false, "for when connecting to a non-TLS registries over plain HTTP")
|
createSourceOCIRepositoryCmd.Flags().BoolVar(&sourceOCIRepositoryArgs.insecure, "insecure", false, "for when connecting to a non-TLS registries over plain HTTP")
|
||||||
|
|
||||||
|
|
@ -153,6 +167,12 @@ func createSourceOCIRepositoryCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
}
|
}
|
||||||
}
|
}
|
||||||
|
|
||||||
|
if secretName := sourceOCIRepositoryArgs.proxySecretRef; secretName != "" {
|
||||||
|
repository.Spec.ProxySecretRef = &meta.LocalObjectReference{
|
||||||
|
Name: secretName,
|
||||||
|
}
|
||||||
|
}
|
||||||
|
|
||||||
if secretName := sourceOCIRepositoryArgs.certSecretRef; secretName != "" {
|
if secretName := sourceOCIRepositoryArgs.certSecretRef; secretName != "" {
|
||||||
repository.Spec.CertSecretRef = &meta.LocalObjectReference{
|
repository.Spec.CertSecretRef = &meta.LocalObjectReference{
|
||||||
Name: secretName,
|
Name: secretName,
|
||||||
|
|
@ -168,8 +188,18 @@ func createSourceOCIRepositoryCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
Name: secretName,
|
Name: secretName,
|
||||||
}
|
}
|
||||||
}
|
}
|
||||||
|
verifyIssuer := sourceOCIRepositoryArgs.verifyOIDCIssuer
|
||||||
|
verifySubject := sourceOCIRepositoryArgs.verifySubject
|
||||||
|
if verifyIssuer != "" || verifySubject != "" {
|
||||||
|
repository.Spec.Verify.MatchOIDCIdentity = []sourcev1.OIDCIdentityMatch{{
|
||||||
|
Issuer: verifyIssuer,
|
||||||
|
Subject: verifySubject,
|
||||||
|
}}
|
||||||
|
}
|
||||||
} else if sourceOCIRepositoryArgs.verifySecretRef != "" {
|
} else if sourceOCIRepositoryArgs.verifySecretRef != "" {
|
||||||
return fmt.Errorf("a verification provider must be specified when a secret is specified")
|
return fmt.Errorf("a verification provider must be specified when a secret is specified")
|
||||||
|
} else if sourceOCIRepositoryArgs.verifyOIDCIssuer != "" || sourceOCIRepositoryArgs.verifySubject != "" {
|
||||||
|
return fmt.Errorf("a verification provider must be specified when OIDC issuer/subject is specified")
|
||||||
}
|
}
|
||||||
|
|
||||||
if createArgs.export {
|
if createArgs.export {
|
||||||
|
|
|
||||||
|
|
@ -37,10 +37,35 @@ func TestCreateSourceOCI(t *testing.T) {
|
||||||
assertFunc: assertError("url is required"),
|
assertFunc: assertError("url is required"),
|
||||||
},
|
},
|
||||||
{
|
{
|
||||||
name: "verify provider not specified",
|
name: "verify secret specified but provider missing",
|
||||||
args: "create source oci podinfo --url=oci://ghcr.io/stefanprodan/manifests/podinfo --tag=6.3.5 --verify-secret-ref=cosign-pub",
|
args: "create source oci podinfo --url=oci://ghcr.io/stefanprodan/manifests/podinfo --tag=6.3.5 --verify-secret-ref=cosign-pub",
|
||||||
assertFunc: assertError("a verification provider must be specified when a secret is specified"),
|
assertFunc: assertError("a verification provider must be specified when a secret is specified"),
|
||||||
},
|
},
|
||||||
|
{
|
||||||
|
name: "verify issuer specified but provider missing",
|
||||||
|
args: "create source oci podinfo --url=oci://ghcr.io/stefanprodan/manifests/podinfo --tag=6.3.5 --verify-issuer=github.com",
|
||||||
|
assertFunc: assertError("a verification provider must be specified when OIDC issuer/subject is specified"),
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "verify identity specified but provider missing",
|
||||||
|
args: "create source oci podinfo --url=oci://ghcr.io/stefanprodan/manifests/podinfo --tag=6.3.5 --verify-subject=developer",
|
||||||
|
assertFunc: assertError("a verification provider must be specified when OIDC issuer/subject is specified"),
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "verify issuer specified but subject missing",
|
||||||
|
args: "create source oci podinfo --url=oci://ghcr.io/stefanprodan/manifests/podinfo --tag=6.3.5 --verify-issuer=github --verify-provider=cosign --export",
|
||||||
|
assertFunc: assertGoldenFile("./testdata/oci/export_with_issuer.golden"),
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "all verify fields set",
|
||||||
|
args: "create source oci podinfo --url=oci://ghcr.io/stefanprodan/manifests/podinfo --tag=6.3.5 --verify-issuer=github verify-subject=stefanprodan --verify-provider=cosign --export",
|
||||||
|
assertFunc: assertGoldenFile("./testdata/oci/export_with_issuer.golden"),
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "verify subject specified but issuer missing",
|
||||||
|
args: "create source oci podinfo --url=oci://ghcr.io/stefanprodan/manifests/podinfo --tag=6.3.5 --verify-subject=stefanprodan --verify-provider=cosign --export",
|
||||||
|
assertFunc: assertGoldenFile("./testdata/oci/export_with_subject.golden"),
|
||||||
|
},
|
||||||
{
|
{
|
||||||
name: "export manifest",
|
name: "export manifest",
|
||||||
args: "create source oci podinfo --url=oci://ghcr.io/stefanprodan/manifests/podinfo --tag=6.3.5 --interval 10m --export",
|
args: "create source oci podinfo --url=oci://ghcr.io/stefanprodan/manifests/podinfo --tag=6.3.5 --interval 10m --export",
|
||||||
|
|
|
||||||
|
|
@ -59,6 +59,7 @@ const (
|
||||||
type tenantFlags struct {
|
type tenantFlags struct {
|
||||||
namespaces []string
|
namespaces []string
|
||||||
clusterRole string
|
clusterRole string
|
||||||
|
account string
|
||||||
}
|
}
|
||||||
|
|
||||||
var tenantArgs tenantFlags
|
var tenantArgs tenantFlags
|
||||||
|
|
@ -66,6 +67,7 @@ var tenantArgs tenantFlags
|
||||||
func init() {
|
func init() {
|
||||||
createTenantCmd.Flags().StringSliceVar(&tenantArgs.namespaces, "with-namespace", nil, "namespace belonging to this tenant")
|
createTenantCmd.Flags().StringSliceVar(&tenantArgs.namespaces, "with-namespace", nil, "namespace belonging to this tenant")
|
||||||
createTenantCmd.Flags().StringVar(&tenantArgs.clusterRole, "cluster-role", "cluster-admin", "cluster role of the tenant role binding")
|
createTenantCmd.Flags().StringVar(&tenantArgs.clusterRole, "cluster-role", "cluster-admin", "cluster role of the tenant role binding")
|
||||||
|
createTenantCmd.Flags().StringVar(&tenantArgs.account, "with-service-account", "", "service account belonging to this tenant")
|
||||||
createCmd.AddCommand(createTenantCmd)
|
createCmd.AddCommand(createTenantCmd)
|
||||||
}
|
}
|
||||||
|
|
||||||
|
|
@ -107,9 +109,17 @@ func createTenantCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
}
|
}
|
||||||
namespaces = append(namespaces, namespace)
|
namespaces = append(namespaces, namespace)
|
||||||
|
|
||||||
|
accountName := tenant
|
||||||
|
if tenantArgs.account != "" {
|
||||||
|
accountName = tenantArgs.account
|
||||||
|
}
|
||||||
|
if err := validation.IsQualifiedName(accountName); len(err) > 0 {
|
||||||
|
return fmt.Errorf("invalid service-account name '%s': %v", accountName, err)
|
||||||
|
}
|
||||||
|
|
||||||
account := corev1.ServiceAccount{
|
account := corev1.ServiceAccount{
|
||||||
ObjectMeta: metav1.ObjectMeta{
|
ObjectMeta: metav1.ObjectMeta{
|
||||||
Name: tenant,
|
Name: accountName,
|
||||||
Namespace: ns,
|
Namespace: ns,
|
||||||
Labels: objLabels,
|
Labels: objLabels,
|
||||||
},
|
},
|
||||||
|
|
@ -131,7 +141,7 @@ func createTenantCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
},
|
},
|
||||||
{
|
{
|
||||||
Kind: "ServiceAccount",
|
Kind: "ServiceAccount",
|
||||||
Name: tenant,
|
Name: accountName,
|
||||||
Namespace: ns,
|
Namespace: ns,
|
||||||
},
|
},
|
||||||
},
|
},
|
||||||
|
|
@ -283,9 +293,9 @@ func exportTenant(namespace corev1.Namespace, account corev1.ServiceAccount, rol
|
||||||
return err
|
return err
|
||||||
}
|
}
|
||||||
|
|
||||||
fmt.Println("---")
|
rootCmd.Println("---")
|
||||||
data = bytes.Replace(data, []byte("spec: {}\n"), []byte(""), 1)
|
data = bytes.Replace(data, []byte("spec: {}\n"), []byte(""), 1)
|
||||||
fmt.Println(resourceToString(data))
|
rootCmd.Println(resourceToString(data))
|
||||||
|
|
||||||
account.TypeMeta = metav1.TypeMeta{
|
account.TypeMeta = metav1.TypeMeta{
|
||||||
APIVersion: "v1",
|
APIVersion: "v1",
|
||||||
|
|
@ -296,9 +306,9 @@ func exportTenant(namespace corev1.Namespace, account corev1.ServiceAccount, rol
|
||||||
return err
|
return err
|
||||||
}
|
}
|
||||||
|
|
||||||
fmt.Println("---")
|
rootCmd.Println("---")
|
||||||
data = bytes.Replace(data, []byte("spec: {}\n"), []byte(""), 1)
|
data = bytes.Replace(data, []byte("spec: {}\n"), []byte(""), 1)
|
||||||
fmt.Println(resourceToString(data))
|
rootCmd.Println(resourceToString(data))
|
||||||
|
|
||||||
roleBinding.TypeMeta = metav1.TypeMeta{
|
roleBinding.TypeMeta = metav1.TypeMeta{
|
||||||
APIVersion: "rbac.authorization.k8s.io/v1",
|
APIVersion: "rbac.authorization.k8s.io/v1",
|
||||||
|
|
@ -309,8 +319,8 @@ func exportTenant(namespace corev1.Namespace, account corev1.ServiceAccount, rol
|
||||||
return err
|
return err
|
||||||
}
|
}
|
||||||
|
|
||||||
fmt.Println("---")
|
rootCmd.Println("---")
|
||||||
fmt.Println(resourceToString(data))
|
rootCmd.Println(resourceToString(data))
|
||||||
|
|
||||||
return nil
|
return nil
|
||||||
}
|
}
|
||||||
|
|
|
||||||
|
|
@ -0,0 +1,68 @@
|
||||||
|
//go:build e2e
|
||||||
|
// +build e2e
|
||||||
|
|
||||||
|
/*
|
||||||
|
Copyright 2025 The Flux authors
|
||||||
|
|
||||||
|
Licensed under the Apache License, Version 2.0 (the "License");
|
||||||
|
you may not use this file except in compliance with the License.
|
||||||
|
You may obtain a copy of the License at
|
||||||
|
|
||||||
|
http://www.apache.org/licenses/LICENSE-2.0
|
||||||
|
|
||||||
|
Unless required by applicable law or agreed to in writing, software
|
||||||
|
distributed under the License is distributed on an "AS IS" BASIS,
|
||||||
|
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||||
|
See the License for the specific language governing permissions and
|
||||||
|
limitations under the License.
|
||||||
|
*/
|
||||||
|
|
||||||
|
package main
|
||||||
|
|
||||||
|
import (
|
||||||
|
"testing"
|
||||||
|
)
|
||||||
|
|
||||||
|
func TestCreateTenant(t *testing.T) {
|
||||||
|
tests := []struct {
|
||||||
|
name string
|
||||||
|
args string
|
||||||
|
assert assertFunc
|
||||||
|
}{
|
||||||
|
{
|
||||||
|
name: "no args",
|
||||||
|
args: "create tenant",
|
||||||
|
assert: assertError("name is required"),
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "no namespace",
|
||||||
|
args: "create tenant dev-team --cluster-role=cluster-admin",
|
||||||
|
assert: assertError("with-namespace is required"),
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "basic tenant",
|
||||||
|
args: "create tenant dev-team --with-namespace=apps --cluster-role=cluster-admin --export",
|
||||||
|
assert: assertGoldenFile("./testdata/create_tenant/tenant-basic.yaml"),
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "tenant with custom serviceaccount",
|
||||||
|
args: "create tenant dev-team --with-namespace=apps --cluster-role=cluster-admin --with-service-account=flux-tenant --export",
|
||||||
|
assert: assertGoldenFile("./testdata/create_tenant/tenant-with-service-account.yaml"),
|
||||||
|
},
|
||||||
|
{
|
||||||
|
name: "tenant with custom cluster role",
|
||||||
|
args: "create tenant dev-team --with-namespace=apps --cluster-role=custom-role --export",
|
||||||
|
assert: assertGoldenFile("./testdata/create_tenant/tenant-with-cluster-role.yaml"),
|
||||||
|
},
|
||||||
|
}
|
||||||
|
|
||||||
|
for _, tt := range tests {
|
||||||
|
t.Run(tt.name, func(t *testing.T) {
|
||||||
|
cmd := cmdTestCase{
|
||||||
|
args: tt.args,
|
||||||
|
assert: tt.assert,
|
||||||
|
}
|
||||||
|
cmd.runTestCmd(t)
|
||||||
|
})
|
||||||
|
}
|
||||||
|
}
|
||||||
|
|
@ -0,0 +1,31 @@
|
||||||
|
/*
|
||||||
|
Copyright 2024 The Flux authors
|
||||||
|
|
||||||
|
Licensed under the Apache License, Version 2.0 (the "License");
|
||||||
|
you may not use this file except in compliance with the License.
|
||||||
|
You may obtain a copy of the License at
|
||||||
|
|
||||||
|
http://www.apache.org/licenses/LICENSE-2.0
|
||||||
|
|
||||||
|
Unless required by applicable law or agreed to in writing, software
|
||||||
|
distributed under the License is distributed on an "AS IS" BASIS,
|
||||||
|
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||||
|
See the License for the specific language governing permissions and
|
||||||
|
limitations under the License.
|
||||||
|
*/
|
||||||
|
|
||||||
|
package main
|
||||||
|
|
||||||
|
import (
|
||||||
|
"github.com/spf13/cobra"
|
||||||
|
)
|
||||||
|
|
||||||
|
var debugCmd = &cobra.Command{
|
||||||
|
Use: "debug",
|
||||||
|
Short: "Debug a flux resource",
|
||||||
|
Long: `The debug command can be used to troubleshoot failing resource reconciliations.`,
|
||||||
|
}
|
||||||
|
|
||||||
|
func init() {
|
||||||
|
rootCmd.AddCommand(debugCmd)
|
||||||
|
}
|
||||||
|
|
@ -0,0 +1,113 @@
|
||||||
|
/*
|
||||||
|
Copyright 2024 The Flux authors
|
||||||
|
|
||||||
|
Licensed under the Apache License, Version 2.0 (the "License");
|
||||||
|
you may not use this file except in compliance with the License.
|
||||||
|
You may obtain a copy of the License at
|
||||||
|
|
||||||
|
http://www.apache.org/licenses/LICENSE-2.0
|
||||||
|
|
||||||
|
Unless required by applicable law or agreed to in writing, software
|
||||||
|
distributed under the License is distributed on an "AS IS" BASIS,
|
||||||
|
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||||
|
See the License for the specific language governing permissions and
|
||||||
|
limitations under the License.
|
||||||
|
*/
|
||||||
|
|
||||||
|
package main
|
||||||
|
|
||||||
|
import (
|
||||||
|
"context"
|
||||||
|
"fmt"
|
||||||
|
|
||||||
|
helmv2 "github.com/fluxcd/helm-controller/api/v2"
|
||||||
|
"github.com/fluxcd/pkg/chartutil"
|
||||||
|
"github.com/go-logr/logr"
|
||||||
|
"github.com/spf13/cobra"
|
||||||
|
"k8s.io/apimachinery/pkg/types"
|
||||||
|
"sigs.k8s.io/yaml"
|
||||||
|
|
||||||
|
"github.com/fluxcd/flux2/v2/internal/utils"
|
||||||
|
)
|
||||||
|
|
||||||
|
var debugHelmReleaseCmd = &cobra.Command{
|
||||||
|
Use: "helmrelease [name]",
|
||||||
|
Aliases: []string{"hr"},
|
||||||
|
Short: "Debug a HelmRelease resource",
|
||||||
|
Long: withPreviewNote(`The debug helmrelease command can be used to troubleshoot failing Helm release reconciliations.
|
||||||
|
WARNING: This command will print sensitive information if Kubernetes Secrets are referenced in the HelmRelease .spec.valuesFrom field.`),
|
||||||
|
Example: ` # Print the status of a Helm release
|
||||||
|
flux debug hr podinfo --show-status
|
||||||
|
|
||||||
|
# Export the final values of a Helm release composed from referred ConfigMaps and Secrets
|
||||||
|
flux debug hr podinfo --show-values > values.yaml`,
|
||||||
|
RunE: debugHelmReleaseCmdRun,
|
||||||
|
Args: cobra.ExactArgs(1),
|
||||||
|
ValidArgsFunction: resourceNamesCompletionFunc(helmv2.GroupVersion.WithKind(helmv2.HelmReleaseKind)),
|
||||||
|
}
|
||||||
|
|
||||||
|
type debugHelmReleaseFlags struct {
|
||||||
|
showStatus bool
|
||||||
|
showValues bool
|
||||||
|
}
|
||||||
|
|
||||||
|
var debugHelmReleaseArgs debugHelmReleaseFlags
|
||||||
|
|
||||||
|
func init() {
|
||||||
|
debugHelmReleaseCmd.Flags().BoolVar(&debugHelmReleaseArgs.showStatus, "show-status", false, "print the status of the Helm release")
|
||||||
|
debugHelmReleaseCmd.Flags().BoolVar(&debugHelmReleaseArgs.showValues, "show-values", false, "print the final values of the Helm release")
|
||||||
|
debugCmd.AddCommand(debugHelmReleaseCmd)
|
||||||
|
}
|
||||||
|
|
||||||
|
func debugHelmReleaseCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
|
name := args[0]
|
||||||
|
|
||||||
|
if (!debugHelmReleaseArgs.showStatus && !debugHelmReleaseArgs.showValues) ||
|
||||||
|
(debugHelmReleaseArgs.showStatus && debugHelmReleaseArgs.showValues) {
|
||||||
|
return fmt.Errorf("either --show-status or --show-values must be set")
|
||||||
|
}
|
||||||
|
|
||||||
|
ctx, cancel := context.WithTimeout(context.Background(), rootArgs.timeout)
|
||||||
|
defer cancel()
|
||||||
|
|
||||||
|
kubeClient, err := utils.KubeClient(kubeconfigArgs, kubeclientOptions)
|
||||||
|
if err != nil {
|
||||||
|
return err
|
||||||
|
}
|
||||||
|
|
||||||
|
hr := &helmv2.HelmRelease{}
|
||||||
|
hrName := types.NamespacedName{Namespace: *kubeconfigArgs.Namespace, Name: name}
|
||||||
|
if err := kubeClient.Get(ctx, hrName, hr); err != nil {
|
||||||
|
return err
|
||||||
|
}
|
||||||
|
|
||||||
|
if debugHelmReleaseArgs.showStatus {
|
||||||
|
status, err := yaml.Marshal(hr.Status)
|
||||||
|
if err != nil {
|
||||||
|
return err
|
||||||
|
}
|
||||||
|
rootCmd.Println("# Status documentation: https://fluxcd.io/flux/components/helm/helmreleases/#helmrelease-status")
|
||||||
|
rootCmd.Print(string(status))
|
||||||
|
return nil
|
||||||
|
}
|
||||||
|
|
||||||
|
if debugHelmReleaseArgs.showValues {
|
||||||
|
finalValues, err := chartutil.ChartValuesFromReferences(ctx,
|
||||||
|
logr.Discard(),
|
||||||
|
kubeClient,
|
||||||
|
hr.GetNamespace(),
|
||||||
|
hr.GetValues(),
|
||||||
|
hr.Spec.ValuesFrom...)
|
||||||
|
if err != nil {
|
||||||
|
return err
|
||||||
|
}
|
||||||
|
|
||||||
|
values, err := yaml.Marshal(finalValues)
|
||||||
|
if err != nil {
|
||||||
|
return err
|
||||||
|
}
|
||||||
|
rootCmd.Print(string(values))
|
||||||
|
}
|
||||||
|
|
||||||
|
return nil
|
||||||
|
}
|
||||||
|
|
@ -0,0 +1,71 @@
|
||||||
|
//go:build unit
|
||||||
|
// +build unit
|
||||||
|
|
||||||
|
/*
|
||||||
|
Copyright 2024 The Flux authors
|
||||||
|
|
||||||
|
Licensed under the Apache License, Version 2.0 (the "License");
|
||||||
|
you may not use this file except in compliance with the License.
|
||||||
|
You may obtain a copy of the License at
|
||||||
|
|
||||||
|
http://www.apache.org/licenses/LICENSE-2.0
|
||||||
|
|
||||||
|
Unless required by applicable law or agreed to in writing, software
|
||||||
|
distributed under the License is distributed on an "AS IS" BASIS,
|
||||||
|
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||||
|
See the License for the specific language governing permissions and
|
||||||
|
limitations under the License.
|
||||||
|
*/
|
||||||
|
|
||||||
|
package main
|
||||||
|
|
||||||
|
import (
|
||||||
|
"testing"
|
||||||
|
)
|
||||||
|
|
||||||
|
func TestDebugHelmRelease(t *testing.T) {
|
||||||
|
namespace := allocateNamespace("debug")
|
||||||
|
|
||||||
|
objectFile := "testdata/debug_helmrelease/objects.yaml"
|
||||||
|
tmpl := map[string]string{
|
||||||
|
"fluxns": namespace,
|
||||||
|
}
|
||||||
|
testEnv.CreateObjectFile(objectFile, tmpl, t)
|
||||||
|
|
||||||
|
cases := []struct {
|
||||||
|
name string
|
||||||
|
arg string
|
||||||
|
goldenFile string
|
||||||
|
tmpl map[string]string
|
||||||
|
}{
|
||||||
|
{
|
||||||
|
"debug status",
|
||||||
|
"debug helmrelease test-values-inline --show-status --show-values=false",
|
||||||
|
"testdata/debug_helmrelease/status.golden.yaml",
|
||||||
|
tmpl,
|
||||||
|
},
|
||||||
|
{
|
||||||
|
"debug values",
|
||||||
|
"debug helmrelease test-values-inline --show-values --show-status=false",
|
||||||
|
"testdata/debug_helmrelease/values-inline.golden.yaml",
|
||||||
|
tmpl,
|
||||||
|
},
|
||||||
|
{
|
||||||
|
"debug values from",
|
||||||
|
"debug helmrelease test-values-from --show-values --show-status=false",
|
||||||
|
"testdata/debug_helmrelease/values-from.golden.yaml",
|
||||||
|
tmpl,
|
||||||
|
},
|
||||||
|
}
|
||||||
|
|
||||||
|
for _, tt := range cases {
|
||||||
|
t.Run(tt.name, func(t *testing.T) {
|
||||||
|
cmd := cmdTestCase{
|
||||||
|
args: tt.arg + " -n=" + namespace,
|
||||||
|
assert: assertGoldenTemplateFile(tt.goldenFile, tmpl),
|
||||||
|
}
|
||||||
|
|
||||||
|
cmd.runTestCmd(t)
|
||||||
|
})
|
||||||
|
}
|
||||||
|
}
|
||||||
|
|
@ -0,0 +1,134 @@
|
||||||
|
/*
|
||||||
|
Copyright 2024 The Flux authors
|
||||||
|
|
||||||
|
Licensed under the Apache License, Version 2.0 (the "License");
|
||||||
|
you may not use this file except in compliance with the License.
|
||||||
|
You may obtain a copy of the License at
|
||||||
|
|
||||||
|
http://www.apache.org/licenses/LICENSE-2.0
|
||||||
|
|
||||||
|
Unless required by applicable law or agreed to in writing, software
|
||||||
|
distributed under the License is distributed on an "AS IS" BASIS,
|
||||||
|
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||||
|
See the License for the specific language governing permissions and
|
||||||
|
limitations under the License.
|
||||||
|
*/
|
||||||
|
|
||||||
|
package main
|
||||||
|
|
||||||
|
import (
|
||||||
|
"context"
|
||||||
|
"errors"
|
||||||
|
"fmt"
|
||||||
|
"sort"
|
||||||
|
"strings"
|
||||||
|
|
||||||
|
kustomizev1 "github.com/fluxcd/kustomize-controller/api/v1"
|
||||||
|
"github.com/fluxcd/pkg/kustomize"
|
||||||
|
"github.com/spf13/cobra"
|
||||||
|
"k8s.io/apimachinery/pkg/apis/meta/v1/unstructured"
|
||||||
|
"k8s.io/apimachinery/pkg/runtime"
|
||||||
|
"k8s.io/apimachinery/pkg/types"
|
||||||
|
"sigs.k8s.io/yaml"
|
||||||
|
|
||||||
|
"github.com/fluxcd/flux2/v2/internal/utils"
|
||||||
|
)
|
||||||
|
|
||||||
|
var debugKustomizationCmd = &cobra.Command{
|
||||||
|
Use: "kustomization [name]",
|
||||||
|
Aliases: []string{"ks"},
|
||||||
|
Short: "Debug a Flux Kustomization resource",
|
||||||
|
Long: withPreviewNote(`The debug kustomization command can be used to troubleshoot failing Flux Kustomization reconciliations.
|
||||||
|
WARNING: This command will print sensitive information if Kubernetes Secrets are referenced in the Kustomization .spec.postBuild.substituteFrom field.`),
|
||||||
|
Example: ` # Print the status of a Flux Kustomization
|
||||||
|
flux debug ks podinfo --show-status
|
||||||
|
|
||||||
|
# Export the final variables used for post-build substitutions composed from referred ConfigMaps and Secrets
|
||||||
|
flux debug ks podinfo --show-vars > vars.env`,
|
||||||
|
RunE: debugKustomizationCmdRun,
|
||||||
|
Args: cobra.ExactArgs(1),
|
||||||
|
ValidArgsFunction: resourceNamesCompletionFunc(kustomizev1.GroupVersion.WithKind(kustomizev1.KustomizationKind)),
|
||||||
|
}
|
||||||
|
|
||||||
|
type debugKustomizationFlags struct {
|
||||||
|
showStatus bool
|
||||||
|
showVars bool
|
||||||
|
}
|
||||||
|
|
||||||
|
var debugKustomizationArgs debugKustomizationFlags
|
||||||
|
|
||||||
|
func init() {
|
||||||
|
debugKustomizationCmd.Flags().BoolVar(&debugKustomizationArgs.showStatus, "show-status", false, "print the status of the Flux Kustomization")
|
||||||
|
debugKustomizationCmd.Flags().BoolVar(&debugKustomizationArgs.showVars, "show-vars", false, "print the final vars of the Flux Kustomization in dot env format")
|
||||||
|
debugCmd.AddCommand(debugKustomizationCmd)
|
||||||
|
}
|
||||||
|
|
||||||
|
func debugKustomizationCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
|
name := args[0]
|
||||||
|
|
||||||
|
if (!debugKustomizationArgs.showStatus && !debugKustomizationArgs.showVars) ||
|
||||||
|
(debugKustomizationArgs.showStatus && debugKustomizationArgs.showVars) {
|
||||||
|
return fmt.Errorf("either --show-status or --show-vars must be set")
|
||||||
|
}
|
||||||
|
|
||||||
|
ctx, cancel := context.WithTimeout(context.Background(), rootArgs.timeout)
|
||||||
|
defer cancel()
|
||||||
|
|
||||||
|
kubeClient, err := utils.KubeClient(kubeconfigArgs, kubeclientOptions)
|
||||||
|
if err != nil {
|
||||||
|
return err
|
||||||
|
}
|
||||||
|
|
||||||
|
ks := &kustomizev1.Kustomization{}
|
||||||
|
ksName := types.NamespacedName{Namespace: *kubeconfigArgs.Namespace, Name: name}
|
||||||
|
if err := kubeClient.Get(ctx, ksName, ks); err != nil {
|
||||||
|
return err
|
||||||
|
}
|
||||||
|
|
||||||
|
if debugKustomizationArgs.showStatus {
|
||||||
|
status, err := yaml.Marshal(ks.Status)
|
||||||
|
if err != nil {
|
||||||
|
return err
|
||||||
|
}
|
||||||
|
rootCmd.Println("# Status documentation: https://fluxcd.io/flux/components/kustomize/kustomizations/#kustomization-status")
|
||||||
|
rootCmd.Print(string(status))
|
||||||
|
return nil
|
||||||
|
}
|
||||||
|
|
||||||
|
if debugKustomizationArgs.showVars {
|
||||||
|
if ks.Spec.PostBuild == nil {
|
||||||
|
return errors.New("no post build substitutions found")
|
||||||
|
}
|
||||||
|
|
||||||
|
ksObj, err := runtime.DefaultUnstructuredConverter.ToUnstructured(ks)
|
||||||
|
if err != nil {
|
||||||
|
return err
|
||||||
|
}
|
||||||
|
|
||||||
|
finalVars, err := kustomize.LoadVariables(ctx, kubeClient, unstructured.Unstructured{Object: ksObj})
|
||||||
|
if err != nil {
|
||||||
|
return err
|
||||||
|
}
|
||||||
|
|
||||||
|
if len(ks.Spec.PostBuild.Substitute) > 0 {
|
||||||
|
for k, v := range ks.Spec.PostBuild.Substitute {
|
||||||
|
// Remove new lines from the values as they are not supported.
|
||||||
|
// Replicates the controller behavior from
|
||||||
|
// https://github.com/fluxcd/pkg/blob/main/kustomize/kustomize_varsub.go
|
||||||
|
finalVars[k] = strings.ReplaceAll(v, "\n", "")
|
||||||
|
}
|
||||||
|
}
|
||||||
|
|
||||||
|
keys := make([]string, 0, len(finalVars))
|
||||||
|
for k := range finalVars {
|
||||||
|
keys = append(keys, k)
|
||||||
|
}
|
||||||
|
sort.Strings(keys)
|
||||||
|
|
||||||
|
for _, k := range keys {
|
||||||
|
rootCmd.Println(k + "=" + finalVars[k])
|
||||||
|
}
|
||||||
|
}
|
||||||
|
|
||||||
|
return nil
|
||||||
|
}
|
||||||
|
|
@ -0,0 +1,71 @@
|
||||||
|
//go:build unit
|
||||||
|
// +build unit
|
||||||
|
|
||||||
|
/*
|
||||||
|
Copyright 2024 The Flux authors
|
||||||
|
|
||||||
|
Licensed under the Apache License, Version 2.0 (the "License");
|
||||||
|
you may not use this file except in compliance with the License.
|
||||||
|
You may obtain a copy of the License at
|
||||||
|
|
||||||
|
http://www.apache.org/licenses/LICENSE-2.0
|
||||||
|
|
||||||
|
Unless required by applicable law or agreed to in writing, software
|
||||||
|
distributed under the License is distributed on an "AS IS" BASIS,
|
||||||
|
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||||
|
See the License for the specific language governing permissions and
|
||||||
|
limitations under the License.
|
||||||
|
*/
|
||||||
|
|
||||||
|
package main
|
||||||
|
|
||||||
|
import (
|
||||||
|
"testing"
|
||||||
|
)
|
||||||
|
|
||||||
|
func TestDebugKustomization(t *testing.T) {
|
||||||
|
namespace := allocateNamespace("debug")
|
||||||
|
|
||||||
|
objectFile := "testdata/debug_kustomization/objects.yaml"
|
||||||
|
tmpl := map[string]string{
|
||||||
|
"fluxns": namespace,
|
||||||
|
}
|
||||||
|
testEnv.CreateObjectFile(objectFile, tmpl, t)
|
||||||
|
|
||||||
|
cases := []struct {
|
||||||
|
name string
|
||||||
|
arg string
|
||||||
|
goldenFile string
|
||||||
|
tmpl map[string]string
|
||||||
|
}{
|
||||||
|
{
|
||||||
|
"debug status",
|
||||||
|
"debug ks test --show-status --show-vars=false",
|
||||||
|
"testdata/debug_kustomization/status.golden.yaml",
|
||||||
|
tmpl,
|
||||||
|
},
|
||||||
|
{
|
||||||
|
"debug vars",
|
||||||
|
"debug ks test --show-vars --show-status=false",
|
||||||
|
"testdata/debug_kustomization/vars.golden.env",
|
||||||
|
tmpl,
|
||||||
|
},
|
||||||
|
{
|
||||||
|
"debug vars from",
|
||||||
|
"debug ks test-from --show-vars --show-status=false",
|
||||||
|
"testdata/debug_kustomization/vars-from.golden.env",
|
||||||
|
tmpl,
|
||||||
|
},
|
||||||
|
}
|
||||||
|
|
||||||
|
for _, tt := range cases {
|
||||||
|
t.Run(tt.name, func(t *testing.T) {
|
||||||
|
cmd := cmdTestCase{
|
||||||
|
args: tt.arg + " -n=" + namespace,
|
||||||
|
assert: assertGoldenTemplateFile(tt.goldenFile, tmpl),
|
||||||
|
}
|
||||||
|
|
||||||
|
cmd.runTestCmd(t)
|
||||||
|
})
|
||||||
|
}
|
||||||
|
}
|
||||||
|
|
@ -1,5 +1,5 @@
|
||||||
/*
|
/*
|
||||||
Copyright 2020 The Flux authors
|
Copyright 2024 The Flux authors
|
||||||
|
|
||||||
Licensed under the Apache License, Version 2.0 (the "License");
|
Licensed under the Apache License, Version 2.0 (the "License");
|
||||||
you may not use this file except in compliance with the License.
|
you may not use this file except in compliance with the License.
|
||||||
|
|
@ -19,14 +19,14 @@ package main
|
||||||
import (
|
import (
|
||||||
"github.com/spf13/cobra"
|
"github.com/spf13/cobra"
|
||||||
|
|
||||||
helmv2 "github.com/fluxcd/helm-controller/api/v2beta2"
|
helmv2 "github.com/fluxcd/helm-controller/api/v2"
|
||||||
)
|
)
|
||||||
|
|
||||||
var deleteHelmReleaseCmd = &cobra.Command{
|
var deleteHelmReleaseCmd = &cobra.Command{
|
||||||
Use: "helmrelease [name]",
|
Use: "helmrelease [name]",
|
||||||
Aliases: []string{"hr"},
|
Aliases: []string{"hr"},
|
||||||
Short: "Delete a HelmRelease resource",
|
Short: "Delete a HelmRelease resource",
|
||||||
Long: withPreviewNote("The delete helmrelease command removes the given HelmRelease from the cluster."),
|
Long: "The delete helmrelease command removes the given HelmRelease from the cluster.",
|
||||||
Example: ` # Delete a Helm release and the Kubernetes resources created by it
|
Example: ` # Delete a Helm release and the Kubernetes resources created by it
|
||||||
flux delete hr podinfo`,
|
flux delete hr podinfo`,
|
||||||
ValidArgsFunction: resourceNamesCompletionFunc(helmv2.GroupVersion.WithKind(helmv2.HelmReleaseKind)),
|
ValidArgsFunction: resourceNamesCompletionFunc(helmv2.GroupVersion.WithKind(helmv2.HelmReleaseKind)),
|
||||||
|
|
|
||||||
|
|
@ -25,7 +25,7 @@ import (
|
||||||
var deleteImagePolicyCmd = &cobra.Command{
|
var deleteImagePolicyCmd = &cobra.Command{
|
||||||
Use: "policy [name]",
|
Use: "policy [name]",
|
||||||
Short: "Delete an ImagePolicy object",
|
Short: "Delete an ImagePolicy object",
|
||||||
Long: withPreviewNote(`The delete image policy command deletes the given ImagePolicy from the cluster.`),
|
Long: `The delete image policy command deletes the given ImagePolicy from the cluster.`,
|
||||||
Example: ` # Delete an image policy
|
Example: ` # Delete an image policy
|
||||||
flux delete image policy alpine3.x`,
|
flux delete image policy alpine3.x`,
|
||||||
ValidArgsFunction: resourceNamesCompletionFunc(imagev1.GroupVersion.WithKind(imagev1.ImagePolicyKind)),
|
ValidArgsFunction: resourceNamesCompletionFunc(imagev1.GroupVersion.WithKind(imagev1.ImagePolicyKind)),
|
||||||
|
|
|
||||||
|
|
@ -25,7 +25,7 @@ import (
|
||||||
var deleteImageRepositoryCmd = &cobra.Command{
|
var deleteImageRepositoryCmd = &cobra.Command{
|
||||||
Use: "repository [name]",
|
Use: "repository [name]",
|
||||||
Short: "Delete an ImageRepository object",
|
Short: "Delete an ImageRepository object",
|
||||||
Long: withPreviewNote("The delete image repository command deletes the given ImageRepository from the cluster."),
|
Long: "The delete image repository command deletes the given ImageRepository from the cluster.",
|
||||||
Example: ` # Delete an image repository
|
Example: ` # Delete an image repository
|
||||||
flux delete image repository alpine`,
|
flux delete image repository alpine`,
|
||||||
ValidArgsFunction: resourceNamesCompletionFunc(imagev1.GroupVersion.WithKind(imagev1.ImageRepositoryKind)),
|
ValidArgsFunction: resourceNamesCompletionFunc(imagev1.GroupVersion.WithKind(imagev1.ImageRepositoryKind)),
|
||||||
|
|
|
||||||
|
|
@ -19,13 +19,13 @@ package main
|
||||||
import (
|
import (
|
||||||
"github.com/spf13/cobra"
|
"github.com/spf13/cobra"
|
||||||
|
|
||||||
autov1 "github.com/fluxcd/image-automation-controller/api/v1beta1"
|
autov1 "github.com/fluxcd/image-automation-controller/api/v1beta2"
|
||||||
)
|
)
|
||||||
|
|
||||||
var deleteImageUpdateCmd = &cobra.Command{
|
var deleteImageUpdateCmd = &cobra.Command{
|
||||||
Use: "update [name]",
|
Use: "update [name]",
|
||||||
Short: "Delete an ImageUpdateAutomation object",
|
Short: "Delete an ImageUpdateAutomation object",
|
||||||
Long: withPreviewNote(`The delete image update command deletes the given ImageUpdateAutomation from the cluster.`),
|
Long: `The delete image update command deletes the given ImageUpdateAutomation from the cluster.`,
|
||||||
Example: ` # Delete an image update automation
|
Example: ` # Delete an image update automation
|
||||||
flux delete image update latest-images`,
|
flux delete image update latest-images`,
|
||||||
ValidArgsFunction: resourceNamesCompletionFunc(autov1.GroupVersion.WithKind(autov1.ImageUpdateAutomationKind)),
|
ValidArgsFunction: resourceNamesCompletionFunc(autov1.GroupVersion.WithKind(autov1.ImageUpdateAutomationKind)),
|
||||||
|
|
|
||||||
|
|
@ -19,13 +19,13 @@ package main
|
||||||
import (
|
import (
|
||||||
"github.com/spf13/cobra"
|
"github.com/spf13/cobra"
|
||||||
|
|
||||||
sourcev1 "github.com/fluxcd/source-controller/api/v1beta2"
|
sourcev1 "github.com/fluxcd/source-controller/api/v1"
|
||||||
)
|
)
|
||||||
|
|
||||||
var deleteSourceBucketCmd = &cobra.Command{
|
var deleteSourceBucketCmd = &cobra.Command{
|
||||||
Use: "bucket [name]",
|
Use: "bucket [name]",
|
||||||
Short: "Delete a Bucket source",
|
Short: "Delete a Bucket source",
|
||||||
Long: withPreviewNote("The delete source bucket command deletes the given Bucket from the cluster."),
|
Long: "The delete source bucket command deletes the given Bucket from the cluster.",
|
||||||
Example: ` # Delete a Bucket source
|
Example: ` # Delete a Bucket source
|
||||||
flux delete source bucket podinfo`,
|
flux delete source bucket podinfo`,
|
||||||
ValidArgsFunction: resourceNamesCompletionFunc(sourcev1.GroupVersion.WithKind(sourcev1.BucketKind)),
|
ValidArgsFunction: resourceNamesCompletionFunc(sourcev1.GroupVersion.WithKind(sourcev1.BucketKind)),
|
||||||
|
|
|
||||||
|
|
@ -0,0 +1,40 @@
|
||||||
|
/*
|
||||||
|
Copyright 2024 The Flux authors
|
||||||
|
|
||||||
|
Licensed under the Apache License, Version 2.0 (the "License");
|
||||||
|
you may not use this file except in compliance with the License.
|
||||||
|
You may obtain a copy of the License at
|
||||||
|
|
||||||
|
http://www.apache.org/licenses/LICENSE-2.0
|
||||||
|
|
||||||
|
Unless required by applicable law or agreed to in writing, software
|
||||||
|
distributed under the License is distributed on an "AS IS" BASIS,
|
||||||
|
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||||
|
See the License for the specific language governing permissions and
|
||||||
|
limitations under the License.
|
||||||
|
*/
|
||||||
|
|
||||||
|
package main
|
||||||
|
|
||||||
|
import (
|
||||||
|
"github.com/spf13/cobra"
|
||||||
|
|
||||||
|
sourcev1 "github.com/fluxcd/source-controller/api/v1"
|
||||||
|
)
|
||||||
|
|
||||||
|
var deleteSourceChartCmd = &cobra.Command{
|
||||||
|
Use: "chart [name]",
|
||||||
|
Short: "Delete a HelmChart source",
|
||||||
|
Long: "The delete source chart command deletes the given HelmChart from the cluster.",
|
||||||
|
Example: ` # Delete a HelmChart
|
||||||
|
flux delete source chart podinfo`,
|
||||||
|
ValidArgsFunction: resourceNamesCompletionFunc(sourcev1.GroupVersion.WithKind(sourcev1.HelmChartKind)),
|
||||||
|
RunE: deleteCommand{
|
||||||
|
apiType: helmChartType,
|
||||||
|
object: universalAdapter{&sourcev1.HelmChart{}},
|
||||||
|
}.run,
|
||||||
|
}
|
||||||
|
|
||||||
|
func init() {
|
||||||
|
deleteSourceCmd.AddCommand(deleteSourceChartCmd)
|
||||||
|
}
|
||||||
|
|
@ -19,13 +19,13 @@ package main
|
||||||
import (
|
import (
|
||||||
"github.com/spf13/cobra"
|
"github.com/spf13/cobra"
|
||||||
|
|
||||||
sourcev1 "github.com/fluxcd/source-controller/api/v1beta2"
|
sourcev1 "github.com/fluxcd/source-controller/api/v1"
|
||||||
)
|
)
|
||||||
|
|
||||||
var deleteSourceHelmCmd = &cobra.Command{
|
var deleteSourceHelmCmd = &cobra.Command{
|
||||||
Use: "helm [name]",
|
Use: "helm [name]",
|
||||||
Short: "Delete a HelmRepository source",
|
Short: "Delete a HelmRepository source",
|
||||||
Long: withPreviewNote("The delete source helm command deletes the given HelmRepository from the cluster."),
|
Long: "The delete source helm command deletes the given HelmRepository from the cluster.",
|
||||||
Example: ` # Delete a Helm repository
|
Example: ` # Delete a Helm repository
|
||||||
flux delete source helm podinfo`,
|
flux delete source helm podinfo`,
|
||||||
ValidArgsFunction: resourceNamesCompletionFunc(sourcev1.GroupVersion.WithKind(sourcev1.HelmRepositoryKind)),
|
ValidArgsFunction: resourceNamesCompletionFunc(sourcev1.GroupVersion.WithKind(sourcev1.HelmRepositoryKind)),
|
||||||
|
|
|
||||||
|
|
@ -19,7 +19,7 @@ package main
|
||||||
import (
|
import (
|
||||||
"github.com/spf13/cobra"
|
"github.com/spf13/cobra"
|
||||||
|
|
||||||
sourcev1 "github.com/fluxcd/source-controller/api/v1beta2"
|
sourcev1 "github.com/fluxcd/source-controller/api/v1"
|
||||||
)
|
)
|
||||||
|
|
||||||
var deleteSourceOCIRepositoryCmd = &cobra.Command{
|
var deleteSourceOCIRepositoryCmd = &cobra.Command{
|
||||||
|
|
|
||||||
|
|
@ -21,8 +21,9 @@ import (
|
||||||
"fmt"
|
"fmt"
|
||||||
"os"
|
"os"
|
||||||
|
|
||||||
oci "github.com/fluxcd/pkg/oci/client"
|
"github.com/fluxcd/pkg/oci"
|
||||||
sourcev1 "github.com/fluxcd/source-controller/api/v1beta2"
|
sourcev1 "github.com/fluxcd/source-controller/api/v1"
|
||||||
|
"github.com/google/go-containerregistry/pkg/crane"
|
||||||
"github.com/spf13/cobra"
|
"github.com/spf13/cobra"
|
||||||
|
|
||||||
"github.com/fluxcd/flux2/v2/internal/flags"
|
"github.com/fluxcd/flux2/v2/internal/flags"
|
||||||
|
|
@ -31,7 +32,7 @@ import (
|
||||||
var diffArtifactCmd = &cobra.Command{
|
var diffArtifactCmd = &cobra.Command{
|
||||||
Use: "artifact",
|
Use: "artifact",
|
||||||
Short: "Diff Artifact",
|
Short: "Diff Artifact",
|
||||||
Long: withPreviewNote(`The diff artifact command computes the diff between the remote OCI artifact and a local directory or file`),
|
Long: `The diff artifact command computes the diff between the remote OCI artifact and a local directory or file`,
|
||||||
Example: `# Check if local files differ from remote
|
Example: `# Check if local files differ from remote
|
||||||
flux diff artifact oci://ghcr.io/stefanprodan/manifests:podinfo:6.2.0 --path=./kustomize`,
|
flux diff artifact oci://ghcr.io/stefanprodan/manifests:podinfo:6.2.0 --path=./kustomize`,
|
||||||
RunE: diffArtifactCmdRun,
|
RunE: diffArtifactCmdRun,
|
||||||
|
|
@ -42,6 +43,7 @@ type diffArtifactFlags struct {
|
||||||
creds string
|
creds string
|
||||||
provider flags.SourceOCIProvider
|
provider flags.SourceOCIProvider
|
||||||
ignorePaths []string
|
ignorePaths []string
|
||||||
|
insecure bool
|
||||||
}
|
}
|
||||||
|
|
||||||
var diffArtifactArgs = newDiffArtifactArgs()
|
var diffArtifactArgs = newDiffArtifactArgs()
|
||||||
|
|
@ -57,6 +59,7 @@ func init() {
|
||||||
diffArtifactCmd.Flags().StringVar(&diffArtifactArgs.creds, "creds", "", "credentials for OCI registry in the format <username>[:<password>] if --provider is generic")
|
diffArtifactCmd.Flags().StringVar(&diffArtifactArgs.creds, "creds", "", "credentials for OCI registry in the format <username>[:<password>] if --provider is generic")
|
||||||
diffArtifactCmd.Flags().Var(&diffArtifactArgs.provider, "provider", sourceOCIRepositoryArgs.provider.Description())
|
diffArtifactCmd.Flags().Var(&diffArtifactArgs.provider, "provider", sourceOCIRepositoryArgs.provider.Description())
|
||||||
diffArtifactCmd.Flags().StringSliceVar(&diffArtifactArgs.ignorePaths, "ignore-paths", excludeOCI, "set paths to ignore in .gitignore format")
|
diffArtifactCmd.Flags().StringSliceVar(&diffArtifactArgs.ignorePaths, "ignore-paths", excludeOCI, "set paths to ignore in .gitignore format")
|
||||||
|
diffArtifactCmd.Flags().BoolVar(&diffArtifactArgs.insecure, "insecure-registry", false, "allows the remote artifact to be pulled without TLS")
|
||||||
diffCmd.AddCommand(diffArtifactCmd)
|
diffCmd.AddCommand(diffArtifactCmd)
|
||||||
}
|
}
|
||||||
|
|
||||||
|
|
@ -82,7 +85,22 @@ func diffArtifactCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
ctx, cancel := context.WithTimeout(context.Background(), rootArgs.timeout)
|
ctx, cancel := context.WithTimeout(context.Background(), rootArgs.timeout)
|
||||||
defer cancel()
|
defer cancel()
|
||||||
|
|
||||||
ociClient := oci.NewClient(oci.DefaultOptions())
|
opts := oci.DefaultOptions()
|
||||||
|
|
||||||
|
if diffArtifactArgs.insecure {
|
||||||
|
opts = append(opts, crane.Insecure)
|
||||||
|
}
|
||||||
|
|
||||||
|
if diffArtifactArgs.provider.String() != sourcev1.GenericOCIProvider {
|
||||||
|
logger.Actionf("logging in to registry with provider credentials")
|
||||||
|
opt, err := loginWithProvider(ctx, url, diffArtifactArgs.provider.String())
|
||||||
|
if err != nil {
|
||||||
|
return fmt.Errorf("error during login with provider: %w", err)
|
||||||
|
}
|
||||||
|
opts = append(opts, opt)
|
||||||
|
}
|
||||||
|
|
||||||
|
ociClient := oci.NewClient(opts)
|
||||||
|
|
||||||
if diffArtifactArgs.provider.String() == sourcev1.GenericOCIProvider && diffArtifactArgs.creds != "" {
|
if diffArtifactArgs.provider.String() == sourcev1.GenericOCIProvider && diffArtifactArgs.creds != "" {
|
||||||
logger.Actionf("logging in to registry with credentials")
|
logger.Actionf("logging in to registry with credentials")
|
||||||
|
|
@ -91,18 +109,6 @@ func diffArtifactCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
}
|
}
|
||||||
}
|
}
|
||||||
|
|
||||||
if diffArtifactArgs.provider.String() != sourcev1.GenericOCIProvider {
|
|
||||||
logger.Actionf("logging in to registry with provider credentials")
|
|
||||||
ociProvider, err := diffArtifactArgs.provider.ToOCIProvider()
|
|
||||||
if err != nil {
|
|
||||||
return fmt.Errorf("provider not supported: %w", err)
|
|
||||||
}
|
|
||||||
|
|
||||||
if err := ociClient.LoginWithProvider(ctx, url, ociProvider); err != nil {
|
|
||||||
return fmt.Errorf("error during login with provider: %w", err)
|
|
||||||
}
|
|
||||||
}
|
|
||||||
|
|
||||||
if err := ociClient.Diff(ctx, url, diffArtifactArgs.path, diffArtifactArgs.ignorePaths); err != nil {
|
if err := ociClient.Diff(ctx, url, diffArtifactArgs.path, diffArtifactArgs.ignorePaths); err != nil {
|
||||||
return err
|
return err
|
||||||
}
|
}
|
||||||
|
|
|
||||||
|
|
@ -96,7 +96,7 @@ func TestDiffArtifact(t *testing.T) {
|
||||||
tt.url = fmt.Sprintf(tt.url, dockerReg)
|
tt.url = fmt.Sprintf(tt.url, dockerReg)
|
||||||
_, err := executeCommand("push artifact " + tt.url + " --path=" + tt.pushFile + " --source=test --revision=test")
|
_, err := executeCommand("push artifact " + tt.url + " --path=" + tt.pushFile + " --source=test --revision=test")
|
||||||
if err != nil {
|
if err != nil {
|
||||||
t.Fatalf(fmt.Errorf("failed to push image: %w", err).Error())
|
t.Fatal(fmt.Errorf("failed to push image: %w", err).Error())
|
||||||
}
|
}
|
||||||
|
|
||||||
cmd := cmdTestCase{
|
cmd := cmdTestCase{
|
||||||
|
|
|
||||||
|
|
@ -23,8 +23,9 @@ import (
|
||||||
|
|
||||||
"github.com/spf13/cobra"
|
"github.com/spf13/cobra"
|
||||||
|
|
||||||
"github.com/fluxcd/flux2/v2/internal/build"
|
|
||||||
kustomizev1 "github.com/fluxcd/kustomize-controller/api/v1"
|
kustomizev1 "github.com/fluxcd/kustomize-controller/api/v1"
|
||||||
|
|
||||||
|
"github.com/fluxcd/flux2/v2/internal/build"
|
||||||
)
|
)
|
||||||
|
|
||||||
var diffKsCmd = &cobra.Command{
|
var diffKsCmd = &cobra.Command{
|
||||||
|
|
@ -43,7 +44,12 @@ flux diff kustomization my-app --path ./path/to/local/manifests \
|
||||||
# Exclude files by providing a comma separated list of entries that follow the .gitignore pattern fromat.
|
# Exclude files by providing a comma separated list of entries that follow the .gitignore pattern fromat.
|
||||||
flux diff kustomization my-app --path ./path/to/local/manifests \
|
flux diff kustomization my-app --path ./path/to/local/manifests \
|
||||||
--kustomization-file ./path/to/local/my-app.yaml \
|
--kustomization-file ./path/to/local/my-app.yaml \
|
||||||
--ignore-paths "/to_ignore/**/*.yaml,ignore.yaml"`,
|
--ignore-paths "/to_ignore/**/*.yaml,ignore.yaml"
|
||||||
|
|
||||||
|
# Run recursively on all encountered Kustomizations
|
||||||
|
flux diff kustomization my-app --path ./path/to/local/manifests \
|
||||||
|
--recursive \
|
||||||
|
--local-sources GitRepository/flux-system/my-repo=./path/to/local/git`,
|
||||||
ValidArgsFunction: resourceNamesCompletionFunc(kustomizev1.GroupVersion.WithKind(kustomizev1.KustomizationKind)),
|
ValidArgsFunction: resourceNamesCompletionFunc(kustomizev1.GroupVersion.WithKind(kustomizev1.KustomizationKind)),
|
||||||
RunE: diffKsCmdRun,
|
RunE: diffKsCmdRun,
|
||||||
}
|
}
|
||||||
|
|
@ -53,6 +59,9 @@ type diffKsFlags struct {
|
||||||
path string
|
path string
|
||||||
ignorePaths []string
|
ignorePaths []string
|
||||||
progressBar bool
|
progressBar bool
|
||||||
|
strictSubst bool
|
||||||
|
recursive bool
|
||||||
|
localSources map[string]string
|
||||||
}
|
}
|
||||||
|
|
||||||
var diffKsArgs diffKsFlags
|
var diffKsArgs diffKsFlags
|
||||||
|
|
@ -62,6 +71,10 @@ func init() {
|
||||||
diffKsCmd.Flags().BoolVar(&diffKsArgs.progressBar, "progress-bar", true, "Boolean to set the progress bar. The default value is true.")
|
diffKsCmd.Flags().BoolVar(&diffKsArgs.progressBar, "progress-bar", true, "Boolean to set the progress bar. The default value is true.")
|
||||||
diffKsCmd.Flags().StringSliceVar(&diffKsArgs.ignorePaths, "ignore-paths", nil, "set paths to ignore in .gitignore format")
|
diffKsCmd.Flags().StringSliceVar(&diffKsArgs.ignorePaths, "ignore-paths", nil, "set paths to ignore in .gitignore format")
|
||||||
diffKsCmd.Flags().StringVar(&diffKsArgs.kustomizationFile, "kustomization-file", "", "Path to the Flux Kustomization YAML file.")
|
diffKsCmd.Flags().StringVar(&diffKsArgs.kustomizationFile, "kustomization-file", "", "Path to the Flux Kustomization YAML file.")
|
||||||
|
diffKsCmd.Flags().BoolVar(&diffKsArgs.strictSubst, "strict-substitute", false,
|
||||||
|
"When enabled, the post build substitutions will fail if a var without a default value is declared in files but is missing from the input vars.")
|
||||||
|
diffKsCmd.Flags().BoolVarP(&diffKsArgs.recursive, "recursive", "r", false, "Recursively diff Kustomizations")
|
||||||
|
diffKsCmd.Flags().StringToStringVar(&diffKsArgs.localSources, "local-sources", nil, "Comma-separated list of repositories in format: Kind/namespace/name=path")
|
||||||
diffCmd.AddCommand(diffKsCmd)
|
diffCmd.AddCommand(diffKsCmd)
|
||||||
}
|
}
|
||||||
|
|
||||||
|
|
@ -96,6 +109,10 @@ func diffKsCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
build.WithKustomizationFile(diffKsArgs.kustomizationFile),
|
build.WithKustomizationFile(diffKsArgs.kustomizationFile),
|
||||||
build.WithProgressBar(),
|
build.WithProgressBar(),
|
||||||
build.WithIgnore(diffKsArgs.ignorePaths),
|
build.WithIgnore(diffKsArgs.ignorePaths),
|
||||||
|
build.WithStrictSubstitute(diffKsArgs.strictSubst),
|
||||||
|
build.WithRecursive(diffKsArgs.recursive),
|
||||||
|
build.WithLocalSources(diffKsArgs.localSources),
|
||||||
|
build.WithSingleKustomization(),
|
||||||
)
|
)
|
||||||
} else {
|
} else {
|
||||||
builder, err = build.NewBuilder(name, diffKsArgs.path,
|
builder, err = build.NewBuilder(name, diffKsArgs.path,
|
||||||
|
|
@ -103,6 +120,10 @@ func diffKsCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
build.WithTimeout(rootArgs.timeout),
|
build.WithTimeout(rootArgs.timeout),
|
||||||
build.WithKustomizationFile(diffKsArgs.kustomizationFile),
|
build.WithKustomizationFile(diffKsArgs.kustomizationFile),
|
||||||
build.WithIgnore(diffKsArgs.ignorePaths),
|
build.WithIgnore(diffKsArgs.ignorePaths),
|
||||||
|
build.WithStrictSubstitute(diffKsArgs.strictSubst),
|
||||||
|
build.WithRecursive(diffKsArgs.recursive),
|
||||||
|
build.WithLocalSources(diffKsArgs.localSources),
|
||||||
|
build.WithSingleKustomization(),
|
||||||
)
|
)
|
||||||
}
|
}
|
||||||
|
|
||||||
|
|
@ -132,6 +153,12 @@ func diffKsCmdRun(cmd *cobra.Command, args []string) error {
|
||||||
|
|
||||||
select {
|
select {
|
||||||
case <-sigc:
|
case <-sigc:
|
||||||
|
if diffKsArgs.progressBar {
|
||||||
|
err := builder.StopSpinner()
|
||||||
|
if err != nil {
|
||||||
|
return err
|
||||||
|
}
|
||||||
|
}
|
||||||
fmt.Println("Build cancelled... exiting.")
|
fmt.Println("Build cancelled... exiting.")
|
||||||
return builder.Cancel()
|
return builder.Cancel()
|
||||||
case err := <-errChan:
|
case err := <-errChan:
|
||||||
|
|
|
||||||
|
|
@ -27,6 +27,7 @@ import (
|
||||||
|
|
||||||
"github.com/fluxcd/flux2/v2/internal/build"
|
"github.com/fluxcd/flux2/v2/internal/build"
|
||||||
"github.com/fluxcd/pkg/ssa"
|
"github.com/fluxcd/pkg/ssa"
|
||||||
|
"github.com/fluxcd/pkg/ssa/normalize"
|
||||||
"k8s.io/apimachinery/pkg/apis/meta/v1/unstructured"
|
"k8s.io/apimachinery/pkg/apis/meta/v1/unstructured"
|
||||||
)
|
)
|
||||||
|
|
||||||
|
|
@ -97,6 +98,12 @@ func TestDiffKustomization(t *testing.T) {
|
||||||
objectFile: "",
|
objectFile: "",
|
||||||
assert: assertGoldenFile("./testdata/diff-kustomization/nothing-is-deployed.golden"),
|
assert: assertGoldenFile("./testdata/diff-kustomization/nothing-is-deployed.golden"),
|
||||||
},
|
},
|
||||||
|
{
|
||||||
|
name: "diff with recursive",
|
||||||
|
args: "diff kustomization podinfo --path ./testdata/build-kustomization/podinfo-with-my-app --progress-bar=false --recursive --local-sources GitRepository/default/podinfo=./testdata/build-kustomization",
|
||||||
|
objectFile: "./testdata/diff-kustomization/my-app.yaml",
|
||||||
|
assert: assertGoldenFile("./testdata/diff-kustomization/diff-with-recursive.golden"),
|
||||||
|
},
|
||||||
}
|
}
|
||||||
|
|
||||||
tmpl := map[string]string{
|
tmpl := map[string]string{
|
||||||
|
|
@ -145,7 +152,7 @@ func createObjectFromFile(objectFile string, templateValues map[string]string, t
|
||||||
t.Fatalf("Error decoding yaml file '%s': %v", objectFile, err)
|
t.Fatalf("Error decoding yaml file '%s': %v", objectFile, err)
|
||||||
}
|
}
|
||||||
|
|
||||||
if err := ssa.SetNativeKindsDefaults(clientObjects); err != nil {
|
if err := normalize.UnstructuredList(clientObjects); err != nil {
|
||||||
t.Fatalf("Error setting native kinds defaults for '%s': %v", objectFile, err)
|
t.Fatalf("Error setting native kinds defaults for '%s': %v", objectFile, err)
|
||||||
}
|
}
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -0,0 +1,74 @@
|
||||||
|
/*
|
||||||
|
Copyright 2024 The Flux authors
|
||||||
|
|
||||||
|
Licensed under the Apache License, Version 2.0 (the "License");
|
||||||
|
you may not use this file except in compliance with the License.
|
||||||
|
You may obtain a copy of the License at
|
||||||
|
|
||||||
|
http://www.apache.org/licenses/LICENSE-2.0
|
||||||
|
|
||||||
|
Unless required by applicable law or agreed to in writing, software
|
||||||
|
distributed under the License is distributed on an "AS IS" BASIS,
|
||||||
|
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||||
|
See the License for the specific language governing permissions and
|
||||||
|
limitations under the License.
|
||||||
|
*/
|
||||||
|
|
||||||
|
package main
|
||||||
|
|
||||||
|
import (
|
||||||
|
"bufio"
|
||||||
|
"fmt"
|
||||||
|
|
||||||
|
"github.com/fluxcd/pkg/envsubst"
|
||||||
|
"github.com/spf13/cobra"
|
||||||
|
)
|
||||||
|
|
||||||
|
var envsubstCmd = &cobra.Command{
|
||||||
|
Use: "envsubst",
|
||||||
|
Args: cobra.NoArgs,
|
||||||
|
Short: "envsubst substitutes the values of environment variables",
|
||||||
|
Long: withPreviewNote(`The envsubst command substitutes the values of environment variables
|
||||||
|
in the string piped as standard input and writes the result to the standard output. This command can be used
|
||||||
|
to replicate the behavior of the Flux Kustomization post-build substitutions.`),
|
||||||
|
Example: ` # Run env var substitutions on the kustomization build output
|
||||||
|
export cluster_region=eu-central-1
|
||||||
|
kustomize build . | flux envsubst
|
||||||
|
|
||||||
|
# Run env var substitutions and error out if a variable is not set
|
||||||
|
kustomize build . | flux envsubst --strict
|
||||||
|
`,
|
||||||
|
RunE: runEnvsubstCmd,
|
||||||
|
}
|
||||||
|
|
||||||
|
type envsubstFlags struct {
|
||||||
|
strict bool
|
||||||
|
}
|
||||||
|
|
||||||
|
var envsubstArgs envsubstFlags
|
||||||
|
|
||||||
|
func init() {
|
||||||
|
envsubstCmd.Flags().BoolVar(&envsubstArgs.strict, "strict", false,
|
||||||
|
"fail if a variable without a default value is declared in the input but is missing from the environment")
|
||||||
|
rootCmd.AddCommand(envsubstCmd)
|
||||||
|
}
|
||||||
|
|
||||||
|
func runEnvsubstCmd(cmd *cobra.Command, args []string) error {
|
||||||
|
stdin := bufio.NewScanner(rootCmd.InOrStdin())
|
||||||
|
stdout := bufio.NewWriter(rootCmd.OutOrStdout())
|
||||||
|
for stdin.Scan() {
|
||||||
|
line, err := envsubst.EvalEnv(stdin.Text(), envsubstArgs.strict)
|
||||||
|
if err != nil {
|
||||||
|
return err
|
||||||
|
}
|
||||||
|
_, err = fmt.Fprintln(stdout, line)
|
||||||
|
if err != nil {
|
||||||
|
return err
|
||||||
|
}
|
||||||
|
err = stdout.Flush()
|
||||||
|
if err != nil {
|
||||||
|
return err
|
||||||
|
}
|
||||||
|
}
|
||||||
|
return nil
|
||||||
|
}
|
||||||
|
|
@ -0,0 +1,50 @@
|
||||||
|
/*
|
||||||
|
Copyright 2024 The Flux authors
|
||||||
|
|
||||||
|
Licensed under the Apache License, Version 2.0 (the "License");
|
||||||
|
you may not use this file except in compliance with the License.
|
||||||
|
You may obtain a copy of the License at
|
||||||
|
|
||||||
|
http://www.apache.org/licenses/LICENSE-2.0
|
||||||
|
|
||||||
|
Unless required by applicable law or agreed to in writing, software
|
||||||
|
distributed under the License is distributed on an "AS IS" BASIS,
|
||||||
|
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||||
|
See the License for the specific language governing permissions and
|
||||||
|
limitations under the License.
|
||||||
|
*/
|
||||||
|
|
||||||
|
package main
|
||||||
|
|
||||||
|
import (
|
||||||
|
"bytes"
|
||||||
|
"os"
|
||||||
|
"testing"
|
||||||
|
|
||||||
|
. "github.com/onsi/gomega"
|
||||||
|
)
|
||||||
|
|
||||||
|
func TestEnvsubst(t *testing.T) {
|
||||||
|
g := NewWithT(t)
|
||||||
|
input, err := os.ReadFile("testdata/envsubst/file.yaml")
|
||||||
|
g.Expect(err).NotTo(HaveOccurred())
|
||||||
|
|
||||||
|
t.Setenv("REPO_NAME", "test")
|
||||||
|
|
||||||
|
output, err := executeCommandWithIn("envsubst", bytes.NewReader(input))
|
||||||
|
g.Expect(err).NotTo(HaveOccurred())
|
||||||
|
|
||||||
|
expected, err := os.ReadFile("testdata/envsubst/file.gold")
|
||||||
|
g.Expect(err).NotTo(HaveOccurred())
|
||||||
|
g.Expect(output).To(Equal(string(expected)))
|
||||||
|
}
|
||||||
|
|
||||||
|
func TestEnvsubst_Strinct(t *testing.T) {
|
||||||
|
g := NewWithT(t)
|
||||||
|
input, err := os.ReadFile("testdata/envsubst/file.yaml")
|
||||||
|
g.Expect(err).NotTo(HaveOccurred())
|
||||||
|
|
||||||
|
_, err = executeCommandWithIn("envsubst --strict", bytes.NewReader(input))
|
||||||
|
g.Expect(err).To(HaveOccurred())
|
||||||
|
g.Expect(err.Error()).To(ContainSubstring("variable not set (strict mode)"))
|
||||||
|
}
|
||||||
|
|
@ -39,14 +39,13 @@ import (
|
||||||
cmdutil "k8s.io/kubectl/pkg/cmd/util"
|
cmdutil "k8s.io/kubectl/pkg/cmd/util"
|
||||||
"sigs.k8s.io/controller-runtime/pkg/client"
|
"sigs.k8s.io/controller-runtime/pkg/client"
|
||||||
|
|
||||||
helmv2 "github.com/fluxcd/helm-controller/api/v2beta2"
|
helmv2 "github.com/fluxcd/helm-controller/api/v2"
|
||||||
autov1 "github.com/fluxcd/image-automation-controller/api/v1beta1"
|
autov1 "github.com/fluxcd/image-automation-controller/api/v1beta2"
|
||||||
imagev1 "github.com/fluxcd/image-reflector-controller/api/v1beta2"
|
imagev1 "github.com/fluxcd/image-reflector-controller/api/v1beta2"
|
||||||
kustomizev1 "github.com/fluxcd/kustomize-controller/api/v1"
|
kustomizev1 "github.com/fluxcd/kustomize-controller/api/v1"
|
||||||
notificationv1 "github.com/fluxcd/notification-controller/api/v1"
|
notificationv1 "github.com/fluxcd/notification-controller/api/v1"
|
||||||
notificationv1b3 "github.com/fluxcd/notification-controller/api/v1beta3"
|
notificationv1b3 "github.com/fluxcd/notification-controller/api/v1beta3"
|
||||||
sourcev1 "github.com/fluxcd/source-controller/api/v1"
|
sourcev1 "github.com/fluxcd/source-controller/api/v1"
|
||||||
sourcev1b2 "github.com/fluxcd/source-controller/api/v1beta2"
|
|
||||||
|
|
||||||
"github.com/fluxcd/flux2/v2/internal/utils"
|
"github.com/fluxcd/flux2/v2/internal/utils"
|
||||||
"github.com/fluxcd/flux2/v2/pkg/printers"
|
"github.com/fluxcd/flux2/v2/pkg/printers"
|
||||||
|
|
@ -422,7 +421,7 @@ var fluxKindMap = refMap{
|
||||||
gvk: helmv2.GroupVersion.WithKind(helmv2.HelmReleaseKind),
|
gvk: helmv2.GroupVersion.WithKind(helmv2.HelmReleaseKind),
|
||||||
crossNamespaced: true,
|
crossNamespaced: true,
|
||||||
otherRefs: func(namespace, name string) []string {
|
otherRefs: func(namespace, name string) []string {
|
||||||
return []string{fmt.Sprintf("%s/%s-%s", sourcev1b2.HelmChartKind, namespace, name)}
|
return []string{fmt.Sprintf("%s/%s-%s", sourcev1.HelmChartKind, namespace, name)}
|
||||||
},
|
},
|
||||||
field: []string{"spec", "chart", "spec", "sourceRef"},
|
field: []string{"spec", "chart", "spec", "sourceRef"},
|
||||||
},
|
},
|
||||||
|
|
@ -440,15 +439,15 @@ var fluxKindMap = refMap{
|
||||||
crossNamespaced: true,
|
crossNamespaced: true,
|
||||||
field: []string{"spec", "imageRepositoryRef"},
|
field: []string{"spec", "imageRepositoryRef"},
|
||||||
},
|
},
|
||||||
sourcev1b2.HelmChartKind: {
|
sourcev1.HelmChartKind: {
|
||||||
gvk: sourcev1b2.GroupVersion.WithKind(sourcev1b2.HelmChartKind),
|
gvk: sourcev1.GroupVersion.WithKind(sourcev1.HelmChartKind),
|
||||||
crossNamespaced: true,
|
crossNamespaced: true,
|
||||||
field: []string{"spec", "sourceRef"},
|
field: []string{"spec", "sourceRef"},
|
||||||
},
|
},
|
||||||
sourcev1.GitRepositoryKind: {gvk: sourcev1.GroupVersion.WithKind(sourcev1.GitRepositoryKind)},
|
sourcev1.GitRepositoryKind: {gvk: sourcev1.GroupVersion.WithKind(sourcev1.GitRepositoryKind)},
|
||||||
sourcev1b2.OCIRepositoryKind: {gvk: sourcev1b2.GroupVersion.WithKind(sourcev1b2.OCIRepositoryKind)},
|
sourcev1.OCIRepositoryKind: {gvk: sourcev1.GroupVersion.WithKind(sourcev1.OCIRepositoryKind)},
|
||||||
sourcev1b2.BucketKind: {gvk: sourcev1b2.GroupVersion.WithKind(sourcev1b2.BucketKind)},
|
sourcev1.BucketKind: {gvk: sourcev1.GroupVersion.WithKind(sourcev1.BucketKind)},
|
||||||
sourcev1b2.HelmRepositoryKind: {gvk: sourcev1b2.GroupVersion.WithKind(sourcev1b2.HelmRepositoryKind)},
|
sourcev1.HelmRepositoryKind: {gvk: sourcev1.GroupVersion.WithKind(sourcev1.HelmRepositoryKind)},
|
||||||
autov1.ImageUpdateAutomationKind: {gvk: autov1.GroupVersion.WithKind(autov1.ImageUpdateAutomationKind)},
|
autov1.ImageUpdateAutomationKind: {gvk: autov1.GroupVersion.WithKind(autov1.ImageUpdateAutomationKind)},
|
||||||
imagev1.ImageRepositoryKind: {gvk: imagev1.GroupVersion.WithKind(imagev1.ImageRepositoryKind)},
|
imagev1.ImageRepositoryKind: {gvk: imagev1.GroupVersion.WithKind(imagev1.ImageRepositoryKind)},
|
||||||
}
|
}
|
||||||
|
|
|
||||||
|
|
@ -31,7 +31,7 @@ import (
|
||||||
"sigs.k8s.io/controller-runtime/pkg/client/fake"
|
"sigs.k8s.io/controller-runtime/pkg/client/fake"
|
||||||
|
|
||||||
eventv1 "github.com/fluxcd/pkg/apis/event/v1beta1"
|
eventv1 "github.com/fluxcd/pkg/apis/event/v1beta1"
|
||||||
"github.com/fluxcd/pkg/ssa"
|
ssautil "github.com/fluxcd/pkg/ssa/utils"
|
||||||
|
|
||||||
"github.com/fluxcd/flux2/v2/internal/utils"
|
"github.com/fluxcd/flux2/v2/internal/utils"
|
||||||
)
|
)
|
||||||
|
|
@ -78,7 +78,7 @@ spec:
|
||||||
timeout: 1m0s
|
timeout: 1m0s
|
||||||
url: ssh://git@github.com/example/repo
|
url: ssh://git@github.com/example/repo
|
||||||
---
|
---
|
||||||
apiVersion: helm.toolkit.fluxcd.io/v2beta2
|
apiVersion: helm.toolkit.fluxcd.io/v2
|
||||||
kind: HelmRelease
|
kind: HelmRelease
|
||||||
metadata:
|
metadata:
|
||||||
name: podinfo
|
name: podinfo
|
||||||
|
|
@ -95,7 +95,7 @@ spec:
|
||||||
version: '*'
|
version: '*'
|
||||||
interval: 5m0s
|
interval: 5m0s
|
||||||
---
|
---
|
||||||
apiVersion: source.toolkit.fluxcd.io/v1beta2
|
apiVersion: source.toolkit.fluxcd.io/v1
|
||||||
kind: HelmRepository
|
kind: HelmRepository
|
||||||
metadata:
|
metadata:
|
||||||
name: podinfo
|
name: podinfo
|
||||||
|
|
@ -104,7 +104,7 @@ spec:
|
||||||
interval: 1m0s
|
interval: 1m0s
|
||||||
url: https://stefanprodan.github.io/podinfo
|
url: https://stefanprodan.github.io/podinfo
|
||||||
---
|
---
|
||||||
apiVersion: source.toolkit.fluxcd.io/v1beta2
|
apiVersion: source.toolkit.fluxcd.io/v1
|
||||||
kind: HelmChart
|
kind: HelmChart
|
||||||
metadata:
|
metadata:
|
||||||
name: default-podinfo
|
name: default-podinfo
|
||||||
|
|
@ -160,7 +160,7 @@ metadata:
|
||||||
|
|
||||||
func Test_getObjectRef(t *testing.T) {
|
func Test_getObjectRef(t *testing.T) {
|
||||||
g := NewWithT(t)
|
g := NewWithT(t)
|
||||||
objs, err := ssa.ReadObjects(strings.NewReader(objects))
|
objs, err := ssautil.ReadObjects(strings.NewReader(objects))
|
||||||
g.Expect(err).To(Not(HaveOccurred()))
|
g.Expect(err).To(Not(HaveOccurred()))
|
||||||
|
|
||||||
builder := fake.NewClientBuilder().WithScheme(utils.NewScheme())
|
builder := fake.NewClientBuilder().WithScheme(utils.NewScheme())
|
||||||
|
|
@ -244,7 +244,7 @@ func Test_getObjectRef(t *testing.T) {
|
||||||
|
|
||||||
func Test_getRows(t *testing.T) {
|
func Test_getRows(t *testing.T) {
|
||||||
g := NewWithT(t)
|
g := NewWithT(t)
|
||||||
objs, err := ssa.ReadObjects(strings.NewReader(objects))
|
objs, err := ssautil.ReadObjects(strings.NewReader(objects))
|
||||||
g.Expect(err).To(Not(HaveOccurred()))
|
g.Expect(err).To(Not(HaveOccurred()))
|
||||||
|
|
||||||
builder := fake.NewClientBuilder().WithScheme(utils.NewScheme())
|
builder := fake.NewClientBuilder().WithScheme(utils.NewScheme())
|
||||||
|
|
|
||||||
|
|
@ -1,5 +1,5 @@
|
||||||
/*
|
/*
|
||||||
Copyright 2020 The Flux authors
|
Copyright 2024 The Flux authors
|
||||||
|
|
||||||
Licensed under the Apache License, Version 2.0 (the "License");
|
Licensed under the Apache License, Version 2.0 (the "License");
|
||||||
you may not use this file except in compliance with the License.
|
you may not use this file except in compliance with the License.
|
||||||
|
|
@ -20,14 +20,14 @@ import (
|
||||||
"github.com/spf13/cobra"
|
"github.com/spf13/cobra"
|
||||||
metav1 "k8s.io/apimachinery/pkg/apis/meta/v1"
|
metav1 "k8s.io/apimachinery/pkg/apis/meta/v1"
|
||||||
|
|
||||||
helmv2 "github.com/fluxcd/helm-controller/api/v2beta2"
|
helmv2 "github.com/fluxcd/helm-controller/api/v2"
|
||||||
)
|
)
|
||||||
|
|
||||||
var exportHelmReleaseCmd = &cobra.Command{
|
var exportHelmReleaseCmd = &cobra.Command{
|
||||||
Use: "helmrelease [name]",
|
Use: "helmrelease [name]",
|
||||||
Aliases: []string{"hr"},
|
Aliases: []string{"hr"},
|
||||||
Short: "Export HelmRelease resources in YAML format",
|
Short: "Export HelmRelease resources in YAML format",
|
||||||
Long: withPreviewNote("The export helmrelease command exports one or all HelmRelease resources in YAML format."),
|
Long: "The export helmrelease command exports one or all HelmRelease resources in YAML format.",
|
||||||
Example: ` # Export all HelmRelease resources
|
Example: ` # Export all HelmRelease resources
|
||||||
flux export helmrelease --all > kustomizations.yaml
|
flux export helmrelease --all > kustomizations.yaml
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -26,7 +26,7 @@ import (
|
||||||
var exportImagePolicyCmd = &cobra.Command{
|
var exportImagePolicyCmd = &cobra.Command{
|
||||||
Use: "policy [name]",
|
Use: "policy [name]",
|
||||||
Short: "Export ImagePolicy resources in YAML format",
|
Short: "Export ImagePolicy resources in YAML format",
|
||||||
Long: withPreviewNote("The export image policy command exports one or all ImagePolicy resources in YAML format."),
|
Long: "The export image policy command exports one or all ImagePolicy resources in YAML format.",
|
||||||
Example: ` # Export all ImagePolicy resources
|
Example: ` # Export all ImagePolicy resources
|
||||||
flux export image policy --all > image-policies.yaml
|
flux export image policy --all > image-policies.yaml
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -26,7 +26,7 @@ import (
|
||||||
var exportImageRepositoryCmd = &cobra.Command{
|
var exportImageRepositoryCmd = &cobra.Command{
|
||||||
Use: "repository [name]",
|
Use: "repository [name]",
|
||||||
Short: "Export ImageRepository resources in YAML format",
|
Short: "Export ImageRepository resources in YAML format",
|
||||||
Long: withPreviewNote("The export image repository command exports one or all ImageRepository resources in YAML format."),
|
Long: "The export image repository command exports one or all ImageRepository resources in YAML format.",
|
||||||
Example: ` # Export all ImageRepository resources
|
Example: ` # Export all ImageRepository resources
|
||||||
flux export image repository --all > image-repositories.yaml
|
flux export image repository --all > image-repositories.yaml
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -20,13 +20,13 @@ import (
|
||||||
"github.com/spf13/cobra"
|
"github.com/spf13/cobra"
|
||||||
metav1 "k8s.io/apimachinery/pkg/apis/meta/v1"
|
metav1 "k8s.io/apimachinery/pkg/apis/meta/v1"
|
||||||
|
|
||||||
autov1 "github.com/fluxcd/image-automation-controller/api/v1beta1"
|
autov1 "github.com/fluxcd/image-automation-controller/api/v1beta2"
|
||||||
)
|
)
|
||||||
|
|
||||||
var exportImageUpdateCmd = &cobra.Command{
|
var exportImageUpdateCmd = &cobra.Command{
|
||||||
Use: "update [name]",
|
Use: "update [name]",
|
||||||
Short: "Export ImageUpdateAutomation resources in YAML format",
|
Short: "Export ImageUpdateAutomation resources in YAML format",
|
||||||
Long: withPreviewNote("The export image update command exports one or all ImageUpdateAutomation resources in YAML format."),
|
Long: "The export image update command exports one or all ImageUpdateAutomation resources in YAML format.",
|
||||||
Example: ` # Export all ImageUpdateAutomation resources
|
Example: ` # Export all ImageUpdateAutomation resources
|
||||||
flux export image update --all > updates.yaml
|
flux export image update --all > updates.yaml
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -21,13 +21,13 @@ import (
|
||||||
metav1 "k8s.io/apimachinery/pkg/apis/meta/v1"
|
metav1 "k8s.io/apimachinery/pkg/apis/meta/v1"
|
||||||
"k8s.io/apimachinery/pkg/types"
|
"k8s.io/apimachinery/pkg/types"
|
||||||
|
|
||||||
sourcev1 "github.com/fluxcd/source-controller/api/v1beta2"
|
sourcev1 "github.com/fluxcd/source-controller/api/v1"
|
||||||
)
|
)
|
||||||
|
|
||||||
var exportSourceBucketCmd = &cobra.Command{
|
var exportSourceBucketCmd = &cobra.Command{
|
||||||
Use: "bucket [name]",
|
Use: "bucket [name]",
|
||||||
Short: "Export Bucket sources in YAML format",
|
Short: "Export Bucket sources in YAML format",
|
||||||
Long: withPreviewNote("The export source git command exports one or all Bucket sources in YAML format."),
|
Long: "The export source git command exports one or all Bucket sources in YAML format.",
|
||||||
Example: ` # Export all Bucket sources
|
Example: ` # Export all Bucket sources
|
||||||
flux export source bucket --all > sources.yaml
|
flux export source bucket --all > sources.yaml
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -0,0 +1,67 @@
|
||||||
|
/*
|
||||||
|
Copyright 2024 The Flux authors
|
||||||
|
|
||||||
|
Licensed under the Apache License, Version 2.0 (the "License");
|
||||||
|
you may not use this file except in compliance with the License.
|
||||||
|
You may obtain a copy of the License at
|
||||||
|
|
||||||
|
http://www.apache.org/licenses/LICENSE-2.0
|
||||||
|
|
||||||
|
Unless required by applicable law or agreed to in writing, software
|
||||||
|
distributed under the License is distributed on an "AS IS" BASIS,
|
||||||
|
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||||
|
See the License for the specific language governing permissions and
|
||||||
|
limitations under the License.
|
||||||
|
*/
|
||||||
|
|
||||||
|
package main
|
||||||
|
|
||||||
|
import (
|
||||||
|
"github.com/spf13/cobra"
|
||||||
|
metav1 "k8s.io/apimachinery/pkg/apis/meta/v1"
|
||||||
|
|
||||||
|
sourcev1 "github.com/fluxcd/source-controller/api/v1"
|
||||||
|
)
|
||||||
|
|
||||||
|
var exportSourceChartCmd = &cobra.Command{
|
||||||
|
Use: "chart [name]",
|
||||||
|
Short: "Export HelmChart sources in YAML format",
|
||||||
|
Long: withPreviewNote("The export source chart command exports one or all HelmChart sources in YAML format."),
|
||||||
|
Example: ` # Export all chart sources
|
||||||
|
flux export source chart --all > sources.yaml`,
|
||||||
|
ValidArgsFunction: resourceNamesCompletionFunc(sourcev1.GroupVersion.WithKind(sourcev1.HelmChartKind)),
|
||||||
|
RunE: exportCommand{
|
||||||
|
list: helmChartListAdapter{&sourcev1.HelmChartList{}},
|
||||||
|
object: helmChartAdapter{&sourcev1.HelmChart{}},
|
||||||
|
}.run,
|
||||||
|
}
|
||||||
|
|
||||||
|
func init() {
|
||||||
|
exportSourceCmd.AddCommand(exportSourceChartCmd)
|
||||||
|
}
|
||||||
|
|
||||||
|
func exportHelmChart(source *sourcev1.HelmChart) interface{} {
|
||||||
|
gvk := sourcev1.GroupVersion.WithKind(sourcev1.HelmChartKind)
|
||||||
|
export := sourcev1.HelmChart{
|
||||||
|
TypeMeta: metav1.TypeMeta{
|
||||||
|
Kind: gvk.Kind,
|
||||||
|
APIVersion: gvk.GroupVersion().String(),
|
||||||
|
},
|
||||||
|
ObjectMeta: metav1.ObjectMeta{
|
||||||
|
Name: source.Name,
|
||||||
|
Namespace: source.Namespace,
|
||||||
|
Labels: source.Labels,
|
||||||
|
Annotations: source.Annotations,
|
||||||
|
},
|
||||||
|
Spec: source.Spec,
|
||||||
|
}
|
||||||
|
return export
|
||||||
|
}
|
||||||
|
|
||||||
|
func (ex helmChartAdapter) export() interface{} {
|
||||||
|
return exportHelmChart(ex.HelmChart)
|
||||||
|
}
|
||||||
|
|
||||||
|
func (ex helmChartListAdapter) exportItem(i int) interface{} {
|
||||||
|
return exportHelmChart(&ex.HelmChartList.Items[i])
|
||||||
|
}
|
||||||
|
|
@ -21,13 +21,13 @@ import (
|
||||||
metav1 "k8s.io/apimachinery/pkg/apis/meta/v1"
|
metav1 "k8s.io/apimachinery/pkg/apis/meta/v1"
|
||||||
"k8s.io/apimachinery/pkg/types"
|
"k8s.io/apimachinery/pkg/types"
|
||||||
|
|
||||||
sourcev1 "github.com/fluxcd/source-controller/api/v1beta2"
|
sourcev1 "github.com/fluxcd/source-controller/api/v1"
|
||||||
)
|
)
|
||||||
|
|
||||||
var exportSourceHelmCmd = &cobra.Command{
|
var exportSourceHelmCmd = &cobra.Command{
|
||||||
Use: "helm [name]",
|
Use: "helm [name]",
|
||||||
Short: "Export HelmRepository sources in YAML format",
|
Short: "Export HelmRepository sources in YAML format",
|
||||||
Long: withPreviewNote("The export source git command exports one or all HelmRepository sources in YAML format."),
|
Long: "The export source git command exports one or all HelmRepository sources in YAML format.",
|
||||||
Example: ` # Export all HelmRepository sources
|
Example: ` # Export all HelmRepository sources
|
||||||
flux export source helm --all > sources.yaml
|
flux export source helm --all > sources.yaml
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -21,7 +21,7 @@ import (
|
||||||
metav1 "k8s.io/apimachinery/pkg/apis/meta/v1"
|
metav1 "k8s.io/apimachinery/pkg/apis/meta/v1"
|
||||||
"k8s.io/apimachinery/pkg/types"
|
"k8s.io/apimachinery/pkg/types"
|
||||||
|
|
||||||
sourcev1 "github.com/fluxcd/source-controller/api/v1beta2"
|
sourcev1 "github.com/fluxcd/source-controller/api/v1"
|
||||||
)
|
)
|
||||||
|
|
||||||
var exportSourceOCIRepositoryCmd = &cobra.Command{
|
var exportSourceOCIRepositoryCmd = &cobra.Command{
|
||||||
|
|
|
||||||
|
|
@ -1,6 +1,22 @@
|
||||||
//go:build unit
|
//go:build unit
|
||||||
// +build unit
|
// +build unit
|
||||||
|
|
||||||
|
/*
|
||||||
|
Copyright 2024 The Flux authors
|
||||||
|
|
||||||
|
Licensed under the Apache License, Version 2.0 (the "License");
|
||||||
|
you may not use this file except in compliance with the License.
|
||||||
|
You may obtain a copy of the License at
|
||||||
|
|
||||||
|
http://www.apache.org/licenses/LICENSE-2.0
|
||||||
|
|
||||||
|
Unless required by applicable law or agreed to in writing, software
|
||||||
|
distributed under the License is distributed on an "AS IS" BASIS,
|
||||||
|
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
|
||||||
|
See the License for the specific language governing permissions and
|
||||||
|
limitations under the License.
|
||||||
|
*/
|
||||||
|
|
||||||
package main
|
package main
|
||||||
|
|
||||||
import (
|
import (
|
||||||
|
|
@ -58,6 +74,12 @@ func TestExport(t *testing.T) {
|
||||||
"testdata/export/git-repo.yaml",
|
"testdata/export/git-repo.yaml",
|
||||||
tmpl,
|
tmpl,
|
||||||
},
|
},
|
||||||
|
{
|
||||||
|
"source chart",
|
||||||
|
"export source chart flux-system",
|
||||||
|
"testdata/export/helm-chart.yaml",
|
||||||
|
tmpl,
|
||||||
|
},
|
||||||
{
|
{
|
||||||
"source helm",
|
"source helm",
|
||||||
"export source helm flux-system",
|
"export source helm flux-system",
|
||||||
|
|
|
||||||
|
|
@ -18,7 +18,6 @@ package main
|
||||||
|
|
||||||
import (
|
import (
|
||||||
"context"
|
"context"
|
||||||
"errors"
|
|
||||||
"fmt"
|
"fmt"
|
||||||
"os"
|
"os"
|
||||||
"strings"
|
"strings"
|
||||||
|
|
@ -28,7 +27,6 @@ import (
|
||||||
metav1 "k8s.io/apimachinery/pkg/apis/meta/v1"
|
metav1 "k8s.io/apimachinery/pkg/apis/meta/v1"
|
||||||
"k8s.io/apimachinery/pkg/runtime"
|
"k8s.io/apimachinery/pkg/runtime"
|
||||||
"k8s.io/apimachinery/pkg/watch"
|
"k8s.io/apimachinery/pkg/watch"
|
||||||
"k8s.io/client-go/discovery"
|
|
||||||
watchtools "k8s.io/client-go/tools/watch"
|
watchtools "k8s.io/client-go/tools/watch"
|
||||||
"sigs.k8s.io/controller-runtime/pkg/client"
|
"sigs.k8s.io/controller-runtime/pkg/client"
|
||||||
|
|
||||||
|
|
@ -178,8 +176,7 @@ func (get getCommand) run(cmd *cobra.Command, args []string) error {
|
||||||
|
|
||||||
err = kubeClient.List(ctx, get.list.asClientList(), listOpts...)
|
err = kubeClient.List(ctx, get.list.asClientList(), listOpts...)
|
||||||
if err != nil {
|
if err != nil {
|
||||||
var discErr *discovery.ErrGroupDiscoveryFailed
|
if getAll && apimeta.IsNoMatchError(err) {
|
||||||
if getAll && (strings.Contains(err.Error(), "no matches for kind") || errors.As(err, &discErr)) {
|
|
||||||
return nil
|
return nil
|
||||||
}
|
}
|
||||||
return err
|
return err
|
||||||
|
|
@ -187,13 +184,13 @@ func (get getCommand) run(cmd *cobra.Command, args []string) error {
|
||||||
|
|
||||||
if get.list.len() == 0 {
|
if get.list.len() == 0 {
|
||||||
if len(args) > 0 {
|
if len(args) > 0 {
|
||||||
logger.Failuref("%s object '%s' not found in %s namespace",
|
return fmt.Errorf("%s object '%s' not found in %s namespace",
|
||||||
get.kind,
|
get.kind,
|
||||||
args[0],
|
args[0],
|
||||||
namespaceNameOrAny(getArgs.allNamespaces, *kubeconfigArgs.Namespace),
|
namespaceNameOrAny(getArgs.allNamespaces, *kubeconfigArgs.Namespace),
|
||||||
)
|
)
|
||||||
} else if !getAll {
|
} else if !getAll {
|
||||||
logger.Failuref("no %s objects found in %s namespace",
|
return fmt.Errorf("no %s objects found in %s namespace",
|
||||||
get.kind,
|
get.kind,
|
||||||
namespaceNameOrAny(getArgs.allNamespaces, *kubeconfigArgs.Namespace),
|
namespaceNameOrAny(getArgs.allNamespaces, *kubeconfigArgs.Namespace),
|
||||||
)
|
)
|
||||||
|
|
|
||||||
|
|
@ -17,11 +17,10 @@ limitations under the License.
|
||||||
package main
|
package main
|
||||||
|
|
||||||
import (
|
import (
|
||||||
"strings"
|
|
||||||
|
|
||||||
"github.com/spf13/cobra"
|
"github.com/spf13/cobra"
|
||||||
|
apimeta "k8s.io/apimachinery/pkg/api/meta"
|
||||||
|
|
||||||
helmv2 "github.com/fluxcd/helm-controller/api/v2beta2"
|
helmv2 "github.com/fluxcd/helm-controller/api/v2"
|
||||||
kustomizev1 "github.com/fluxcd/kustomize-controller/api/v1"
|
kustomizev1 "github.com/fluxcd/kustomize-controller/api/v1"
|
||||||
notificationv1 "github.com/fluxcd/notification-controller/api/v1"
|
notificationv1 "github.com/fluxcd/notification-controller/api/v1"
|
||||||
notificationv1b3 "github.com/fluxcd/notification-controller/api/v1beta3"
|
notificationv1b3 "github.com/fluxcd/notification-controller/api/v1beta3"
|
||||||
|
|
@ -87,8 +86,8 @@ var getAllCmd = &cobra.Command{
|
||||||
}
|
}
|
||||||
|
|
||||||
func logError(err error) {
|
func logError(err error) {
|
||||||
if !strings.Contains(err.Error(), "no matches for kind") {
|
if !apimeta.IsNoMatchError(err) {
|
||||||
logger.Failuref(err.Error())
|
logger.Failuref("%s", err.Error())
|
||||||
}
|
}
|
||||||
}
|
}
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -1,5 +1,5 @@
|
||||||
/*
|
/*
|
||||||
Copyright 2020 The Flux authors
|
Copyright 2024 The Flux authors
|
||||||
|
|
||||||
Licensed under the Apache License, Version 2.0 (the "License");
|
Licensed under the Apache License, Version 2.0 (the "License");
|
||||||
you may not use this file except in compliance with the License.
|
you may not use this file except in compliance with the License.
|
||||||
|
|
@ -25,14 +25,14 @@ import (
|
||||||
"golang.org/x/text/language"
|
"golang.org/x/text/language"
|
||||||
"k8s.io/apimachinery/pkg/runtime"
|
"k8s.io/apimachinery/pkg/runtime"
|
||||||
|
|
||||||
helmv2 "github.com/fluxcd/helm-controller/api/v2beta2"
|
helmv2 "github.com/fluxcd/helm-controller/api/v2"
|
||||||
)
|
)
|
||||||
|
|
||||||
var getHelmReleaseCmd = &cobra.Command{
|
var getHelmReleaseCmd = &cobra.Command{
|
||||||
Use: "helmreleases",
|
Use: "helmreleases",
|
||||||
Aliases: []string{"hr", "helmrelease"},
|
Aliases: []string{"hr", "helmrelease"},
|
||||||
Short: "Get HelmRelease statuses",
|
Short: "Get HelmRelease statuses",
|
||||||
Long: withPreviewNote("The get helmreleases command prints the statuses of the resources."),
|
Long: "The get helmreleases command prints the statuses of the resources.",
|
||||||
Example: ` # List all Helm releases and their status
|
Example: ` # List all Helm releases and their status
|
||||||
flux get helmreleases`,
|
flux get helmreleases`,
|
||||||
ValidArgsFunction: resourceNamesCompletionFunc(helmv2.GroupVersion.WithKind(helmv2.HelmReleaseKind)),
|
ValidArgsFunction: resourceNamesCompletionFunc(helmv2.GroupVersion.WithKind(helmv2.HelmReleaseKind)),
|
||||||
|
|
@ -72,9 +72,16 @@ func init() {
|
||||||
getCmd.AddCommand(getHelmReleaseCmd)
|
getCmd.AddCommand(getHelmReleaseCmd)
|
||||||
}
|
}
|
||||||
|
|
||||||
|
func getHelmReleaseRevision(helmRelease helmv2.HelmRelease) string {
|
||||||
|
if helmRelease.Status.History != nil && len(helmRelease.Status.History) > 0 {
|
||||||
|
return helmRelease.Status.History[0].ChartVersion
|
||||||
|
}
|
||||||
|
return helmRelease.Status.LastAttemptedRevision
|
||||||
|
}
|
||||||
|
|
||||||
func (a helmReleaseListAdapter) summariseItem(i int, includeNamespace bool, includeKind bool) []string {
|
func (a helmReleaseListAdapter) summariseItem(i int, includeNamespace bool, includeKind bool) []string {
|
||||||
item := a.Items[i]
|
item := a.Items[i]
|
||||||
revision := item.Status.LastAppliedRevision
|
revision := getHelmReleaseRevision(item)
|
||||||
status, msg := statusAndMessage(item.Status.Conditions)
|
status, msg := statusAndMessage(item.Status.Conditions)
|
||||||
return append(nameColumns(&item, includeNamespace, includeKind),
|
return append(nameColumns(&item, includeNamespace, includeKind),
|
||||||
revision, cases.Title(language.English).String(strconv.FormatBool(item.Spec.Suspend)), status, msg)
|
revision, cases.Title(language.English).String(strconv.FormatBool(item.Spec.Suspend)), status, msg)
|
||||||
|
|
|
||||||
|
|
@ -19,14 +19,14 @@ package main
|
||||||
import (
|
import (
|
||||||
"github.com/spf13/cobra"
|
"github.com/spf13/cobra"
|
||||||
|
|
||||||
autov1 "github.com/fluxcd/image-automation-controller/api/v1beta1"
|
autov1 "github.com/fluxcd/image-automation-controller/api/v1beta2"
|
||||||
imagev1 "github.com/fluxcd/image-reflector-controller/api/v1beta2"
|
imagev1 "github.com/fluxcd/image-reflector-controller/api/v1beta2"
|
||||||
)
|
)
|
||||||
|
|
||||||
var getImageAllCmd = &cobra.Command{
|
var getImageAllCmd = &cobra.Command{
|
||||||
Use: "all",
|
Use: "all",
|
||||||
Short: "Get all image statuses",
|
Short: "Get all image statuses",
|
||||||
Long: withPreviewNote("The get image sub-commands print the statuses of all image objects."),
|
Long: "The get image sub-commands print the statuses of all image objects.",
|
||||||
Example: ` # List all image objects in a namespace
|
Example: ` # List all image objects in a namespace
|
||||||
flux get images all --namespace=flux-system
|
flux get images all --namespace=flux-system
|
||||||
|
|
||||||
|
|
@ -55,7 +55,7 @@ var getImageAllCmd = &cobra.Command{
|
||||||
|
|
||||||
for _, c := range allImageCmd {
|
for _, c := range allImageCmd {
|
||||||
if err := c.run(cmd, args); err != nil {
|
if err := c.run(cmd, args); err != nil {
|
||||||
logger.Failuref(err.Error())
|
logger.Failuref("%s", err.Error())
|
||||||
}
|
}
|
||||||
}
|
}
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -28,7 +28,7 @@ import (
|
||||||
var getImagePolicyCmd = &cobra.Command{
|
var getImagePolicyCmd = &cobra.Command{
|
||||||
Use: "policy",
|
Use: "policy",
|
||||||
Short: "Get ImagePolicy status",
|
Short: "Get ImagePolicy status",
|
||||||
Long: withPreviewNote("The get image policy command prints the status of ImagePolicy objects."),
|
Long: "The get image policy command prints the status of ImagePolicy objects.",
|
||||||
Example: ` # List all image policies and their status
|
Example: ` # List all image policies and their status
|
||||||
flux get image policy
|
flux get image policy
|
||||||
|
|
||||||
|
|
|
||||||
|
|
@ -32,7 +32,7 @@ import (
|
||||||
var getImageRepositoryCmd = &cobra.Command{
|
var getImageRepositoryCmd = &cobra.Command{
|
||||||
Use: "repository",
|
Use: "repository",
|
||||||
Short: "Get ImageRepository status",
|
Short: "Get ImageRepository status",
|
||||||
Long: withPreviewNote("The get image repository command prints the status of ImageRepository objects."),
|
Long: "The get image repository command prints the status of ImageRepository objects.",
|
||||||
Example: ` # List all image repositories and their status
|
Example: ` # List all image repositories and their status
|
||||||
flux get image repository
|
flux get image repository
|
||||||
|
|
||||||
|
|
|
||||||
Some files were not shown because too many files have changed in this diff Show More
Loading…
Reference in New Issue