Registry login option should verify that the obtained dockerconfig credentials are for the same host. When the helmrepo URL and the URL in docker auth config don't match, the docker config store returns an empty auth config, instead of failing. This results in accepting empty username and password. The HelmRepo would appear to be ready in such situation because the creds are empty, no login is attempted. But when a HelmChart tries to use the login options, it'd fail. Signed-off-by: Sunny <darkowlzz@protonmail.com> |
||
|---|---|---|
| .github/workflows | ||
| api | ||
| config | ||
| controllers | ||
| docs | ||
| hack | ||
| internal | ||
| pkg | ||
| tests/fuzz | ||
| .dockerignore | ||
| .gitignore | ||
| .goreleaser.yaml | ||
| ATTRIBUTIONS.md | ||
| CHANGELOG.md | ||
| CODE_OF_CONDUCT.md | ||
| DCO | ||
| DEVELOPMENT.md | ||
| Dockerfile | ||
| LICENSE | ||
| MAINTAINERS | ||
| Makefile | ||
| PROJECT | ||
| README.md | ||
| go.mod | ||
| go.sum | ||
| main.go | ||
README.md
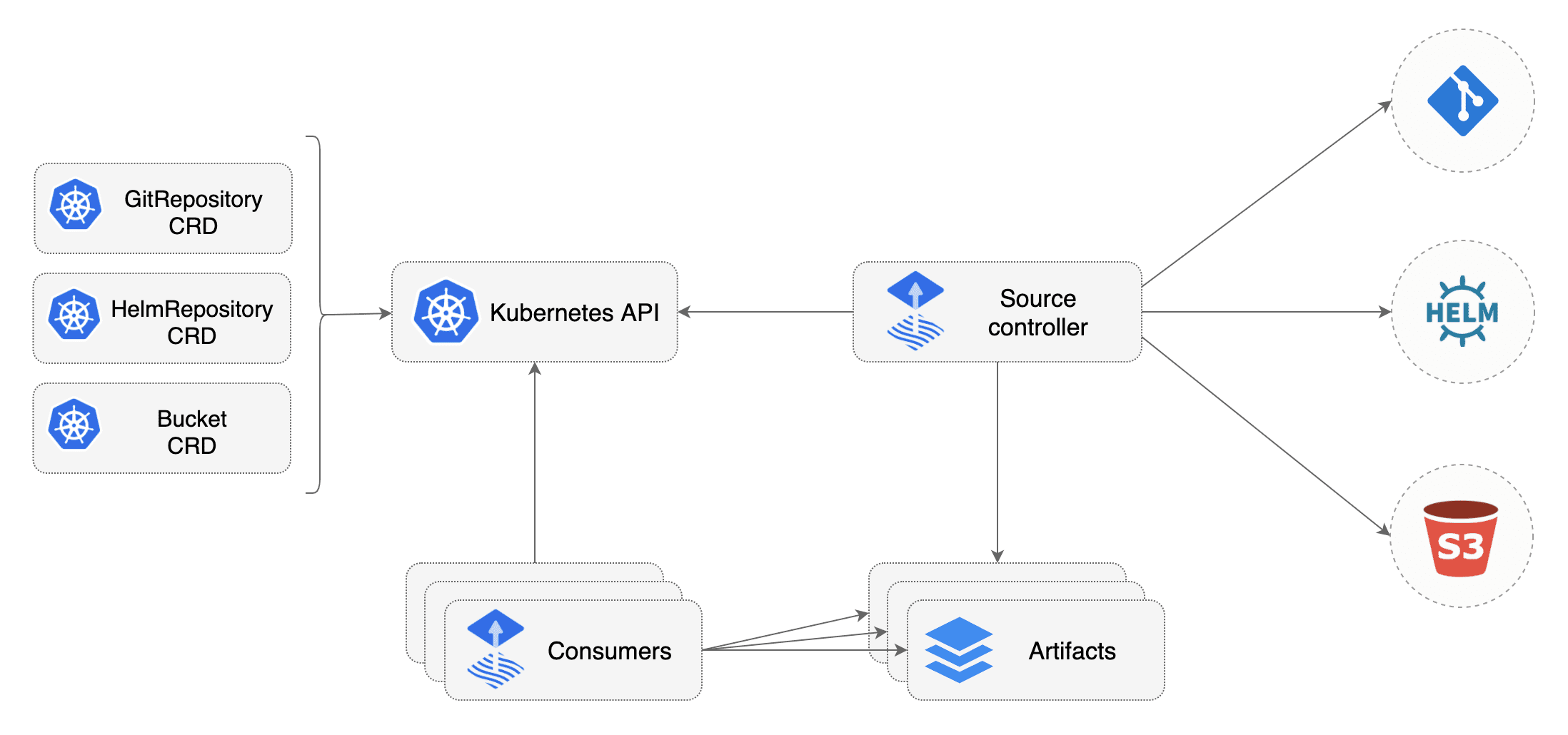
Source controller
The source-controller is a Kubernetes operator, specialised in artifacts acquisition from external sources such as Git, Helm repositories and S3 buckets. The source-controller implements the source.toolkit.fluxcd.io API and is a core component of the GitOps toolkit.
Features:
- authenticates to sources (SSH, user/password, API token)
- validates source authenticity (PGP)
- detects source changes based on update policies (semver)
- fetches resources on-demand and on-a-schedule
- packages the fetched resources into a well-known format (tar.gz, yaml)
- makes the artifacts addressable by their source identifier (sha, version, ts)
- makes the artifacts available in-cluster to interested 3rd parties
- notifies interested 3rd parties of source changes and availability (status conditions, events, hooks)
- reacts to Git push and Helm chart upload events (via notification-controller)