Compare commits
No commits in common. "main" and "jaeger-operator-2.14.0" have entirely different histories.
main
...
jaeger-ope
|
|
@ -1,4 +0,0 @@
|
|||
# https://docs.github.com/en/github/creating-cloning-and-archiving-repositories/about-code-owners
|
||||
|
||||
/charts/jaeger/ @dvonthenen @mikelorant @naseemkullah @pavelnikolov
|
||||
/charts/jaeger-operator/ @batazor @cpanato
|
||||
|
|
@ -1,16 +0,0 @@
|
|||
#### What this PR does
|
||||
|
||||
#### Which issue this PR fixes
|
||||
|
||||
*(optional, in `fixes #<issue number>(, fixes #<issue_number>, ...)` format,
|
||||
will close that issue when PR gets merged)*
|
||||
|
||||
- fixes #
|
||||
|
||||
#### Checklist
|
||||
|
||||
- [ ] [DCO](https://github.com/jaegertracing/helm-charts/blob/main/CONTRIBUTING.md#sign-off-your-work) signed
|
||||
- [ ] Commits are [GPG signed](https://docs.github.com/en/github/authenticating-to-github/about-commit-signature-verification)
|
||||
- [ ] Chart Version bumped
|
||||
- [ ] Title of the PR starts with chart name (`[jaeger]` or `[jaeger-operator]`)
|
||||
- [ ] README.md has been updated to match version/contain new values
|
||||
|
|
@ -1,51 +0,0 @@
|
|||
name: Prepare K8s for Helm tests
|
||||
runs:
|
||||
using: "composite"
|
||||
steps:
|
||||
- name: Set up Helm
|
||||
uses: azure/setup-helm@v4
|
||||
with:
|
||||
version: v3.14.4
|
||||
|
||||
# Python is required because `ct lint` runs Yamale (https://github.com/23andMe/Yamale) and
|
||||
# yamllint (https://github.com/adrienverge/yamllint) which require Python
|
||||
- name: Set up Python
|
||||
uses: actions/setup-python@v4
|
||||
with:
|
||||
python-version: '3.11'
|
||||
|
||||
- name: Set up chart-testing
|
||||
uses: helm/chart-testing-action@v2.6.1
|
||||
with:
|
||||
version: v3.10.1
|
||||
|
||||
- name: Create kind cluster
|
||||
uses: helm/kind-action@v1.9.0
|
||||
|
||||
- name: Install kubectl
|
||||
uses: azure/setup-kubectl@v4.0.0
|
||||
with:
|
||||
version: 'v1.28.8'
|
||||
id: install
|
||||
|
||||
- name: Set up cert-manager
|
||||
shell: bash
|
||||
run: |
|
||||
kubectl apply -f https://raw.githubusercontent.com/kubernetes/ingress-nginx/main/deploy/static/provider/kind/deploy.yaml --namespace ingress-nginx
|
||||
kubectl label node --all ingress-ready=true
|
||||
kubectl describe pod --selector=app.kubernetes.io/component=controller -n ingress-nginx
|
||||
kubectl wait --namespace ingress-nginx --for=condition=ready pod --selector=app.kubernetes.io/component=controller --timeout=5m
|
||||
kubectl apply --validate=false -f https://github.com/jetstack/cert-manager/releases/download/v1.6.1/cert-manager.yaml
|
||||
|
||||
- name: Set up cmctl
|
||||
shell: bash
|
||||
run: |
|
||||
curl -sSL -o cmctl.tar.gz https://github.com/cert-manager/cert-manager/releases/download/v1.6.1/cmctl-linux-amd64.tar.gz
|
||||
tar xzf cmctl.tar.gz
|
||||
sudo mv cmctl /usr/local/bin
|
||||
cmctl version
|
||||
|
||||
- name: Check if cert-manager is up
|
||||
shell: bash
|
||||
run: |
|
||||
cmctl check api --wait=5m
|
||||
|
|
@ -3,87 +3,26 @@ name: Lint and Test Charts
|
|||
on: pull_request
|
||||
|
||||
jobs:
|
||||
lint:
|
||||
lint-test:
|
||||
runs-on: ubuntu-latest
|
||||
steps:
|
||||
- uses: actions/checkout@v2
|
||||
with:
|
||||
fetch-depth: 0
|
||||
|
||||
- name: Set up Helm
|
||||
uses: azure/setup-helm@v4
|
||||
with:
|
||||
version: v3.14.4
|
||||
|
||||
# Python is required because `ct lint` runs Yamale (https://github.com/23andMe/Yamale) and
|
||||
# yamllint (https://github.com/adrienverge/yamllint) which require Python
|
||||
- name: Set up Python
|
||||
uses: actions/setup-python@v4
|
||||
with:
|
||||
python-version: '3.11'
|
||||
|
||||
- name: Set up chart-testing
|
||||
uses: helm/chart-testing-action@v2.6.1
|
||||
with:
|
||||
version: v3.10.1
|
||||
|
||||
- name: Run chart-testing (list-changed)
|
||||
id: list-changed
|
||||
run: |
|
||||
changed=$(ct list-changed --config ct.yaml)
|
||||
if [[ -n "$changed" ]]; then
|
||||
echo "::set-output name=changed::true"
|
||||
fi
|
||||
- name: Checkout
|
||||
uses: actions/checkout@v1
|
||||
|
||||
- name: Run chart-testing (lint)
|
||||
run: ct lint --config ct.yaml
|
||||
|
||||
test-with-cassandra:
|
||||
runs-on: ubuntu-latest
|
||||
steps:
|
||||
- uses: actions/checkout@v2
|
||||
id: lint
|
||||
uses: helm/chart-testing-action@v1.0.0-alpha.3
|
||||
with:
|
||||
fetch-depth: 0
|
||||
command: lint
|
||||
|
||||
- uses: ./.github/actions/prepare-k8s
|
||||
|
||||
- name: Run cassandra-chart-testing (install)
|
||||
run: ct install --config ct.yaml
|
||||
test-with-allInOne:
|
||||
runs-on: ubuntu-latest
|
||||
steps:
|
||||
- uses: actions/checkout@v2
|
||||
- name: Create kind cluster
|
||||
uses: helm/kind-action@v1.0.0-alpha.3
|
||||
with:
|
||||
fetch-depth: 0
|
||||
installLocalPathProvisioner: true
|
||||
# Only build a kind cluster if there are chart changes to test.
|
||||
if: steps.lint.outputs.changed == 'true'
|
||||
|
||||
- uses: ./.github/actions/prepare-k8s
|
||||
|
||||
- name: Run allInOne-chart-testing (install)
|
||||
run: |
|
||||
ct install --config ct.yaml --helm-extra-set-args "
|
||||
--set provisionDataStore.cassandra=false
|
||||
--set storage.type=memory
|
||||
--set allInOne.enabled=true
|
||||
--set agent.enabled=false
|
||||
--set collector.enabled=false
|
||||
--set query.enabled=false"
|
||||
test-with-elasticsearch:
|
||||
runs-on: ubuntu-latest
|
||||
steps:
|
||||
- uses: actions/checkout@v2
|
||||
with:
|
||||
fetch-depth: 0
|
||||
|
||||
- uses: ./.github/actions/prepare-k8s
|
||||
|
||||
- name: Run elasticsearch-chart-testing (install)
|
||||
run: |
|
||||
ct install --config ct.yaml --helm-extra-set-args "
|
||||
--set provisionDataStore.cassandra=false
|
||||
--set provisionDataStore.elasticsearch=true
|
||||
--set storage.type=elasticsearch
|
||||
--set elasticsearch.master.masterOnly=false
|
||||
--set elasticsearch.master.replicaCount=1
|
||||
--set elasticsearch.data.replicaCount=0
|
||||
--set elasticsearch.coordinating.replicaCount=0
|
||||
--set elasticsearch.ingest.replicaCount=0"
|
||||
- name: Run chart-testing (install)
|
||||
uses: helm/chart-testing-action@v1.0.0-alpha.3
|
||||
with:
|
||||
command: install
|
||||
|
|
|
|||
|
|
@ -3,34 +3,35 @@ name: Release Charts
|
|||
on:
|
||||
push:
|
||||
branches:
|
||||
- main
|
||||
- master
|
||||
|
||||
jobs:
|
||||
release:
|
||||
runs-on: ubuntu-latest
|
||||
steps:
|
||||
- name: Checkout
|
||||
uses: actions/checkout@v2
|
||||
with:
|
||||
fetch-depth: 0
|
||||
uses: actions/checkout@v1
|
||||
|
||||
- name: Configure Git
|
||||
run: |
|
||||
git config user.name "$GITHUB_ACTOR"
|
||||
git config user.email "$GITHUB_ACTOR@users.noreply.github.com"
|
||||
|
||||
# See https://github.com/helm/chart-releaser-action/issues/6
|
||||
- name: Install Helm
|
||||
uses: azure/setup-helm@v1
|
||||
with:
|
||||
version: v3.4.1
|
||||
run: |
|
||||
curl -sSLo get_helm.sh https://raw.githubusercontent.com/helm/helm/master/scripts/get
|
||||
chmod 700 get_helm.sh
|
||||
./get_helm.sh
|
||||
helm init --client-only
|
||||
|
||||
- name: Add dependency chart repos
|
||||
run: |
|
||||
helm repo add incubator https://charts.helm.sh/incubator
|
||||
helm repo add stable https://kubernetes-charts.storage.googleapis.com/
|
||||
helm repo add incubator https://kubernetes-charts-incubator.storage.googleapis.com/
|
||||
helm repo add elastic https://helm.elastic.co
|
||||
helm repo add bitnami https://charts.bitnami.com/bitnami
|
||||
|
||||
- name: Run chart-releaser
|
||||
uses: helm/chart-releaser-action@v1.1.0
|
||||
uses: helm/chart-releaser-action@v1.0.0-alpha.2
|
||||
env:
|
||||
CR_TOKEN: "${{ secrets.GITHUB_TOKEN }}"
|
||||
CR_TOKEN: "${{ secrets.CR_TOKEN }}"
|
||||
|
|
|
|||
|
|
@ -1,4 +1,3 @@
|
|||
# Helm chart automated files
|
||||
/charts/*/charts
|
||||
/charts/*/requirements.lock
|
||||
/charts/*/*.tgz
|
||||
|
|
|
|||
|
|
@ -1,3 +1,3 @@
|
|||
## Community Code of Conduct
|
||||
|
||||
Jaeger follows the [CNCF Code of Conduct](https://github.com/cncf/foundation/blob/main/code-of-conduct.md).
|
||||
Jaeger follows the [CNCF Code of Conduct](https://github.com/cncf/foundation/blob/master/code-of-conduct.md).
|
||||
|
|
|
|||
|
|
@ -36,7 +36,7 @@ See `git help commit`:
|
|||
* Must pass [DCO check](#sign-off-your-work)
|
||||
* Must follow [Charts best practices](https://helm.sh/docs/topics/chart_best_practices/)
|
||||
* Must pass CI jobs for linting and installing changed charts with the [chart-testing](https://github.com/helm/chart-testing) tool
|
||||
* Any change to a chart requires a version bump following [semver](https://semver.org/) principles. See [Immutability](#immutability) and [Versioning](#versioning) below
|
||||
* Any change to a chart requires a version bump following [semver](https://semver.org/) principles. See [Immutability(#immutability) and [Versioning](#versioning) below
|
||||
|
||||
Once changes have been merged, the release job will automatically run to package and release changed charts.
|
||||
|
||||
|
|
|
|||
13
README.md
13
README.md
|
|
@ -1,15 +1,10 @@
|
|||
# Jaeger Helm Charts
|
||||
# Kubernetes Helm Charts for Jaeger backend
|
||||
|
||||
[](https://opensource.org/licenses/Apache-2.0)
|
||||
[](https://github.com/jaegertracing/helm-charts/actions)
|
||||
[](https://github.com/jaegertracing/helm-charts/actions)
|
||||
|
||||
This functionality is in beta and is subject to change. The code is provided as-is with no warranties. Beta features are not subject to the support SLA of official GA features.
|
||||
|
||||
# 🛑 If you are looking for Helm Chart for Jaeger-v2
|
||||
|
||||
it is located in the [v2 branch](https://github.com/jaegertracing/helm-charts/blob/v2/charts/jaeger/README-v2.md).
|
||||
|
||||
|
||||
## Usage
|
||||
|
||||
[Helm](https://helm.sh) must be installed to use the charts.
|
||||
|
|
@ -23,10 +18,6 @@ $ helm repo add jaegertracing https://jaegertracing.github.io/helm-charts
|
|||
|
||||
You can then run `helm search repo jaegertracing` to see the charts.
|
||||
|
||||
See additional documentation:
|
||||
* [Jaeger chart](./charts/jaeger)
|
||||
* [Jaeger Operator chart](./charts/jaeger-operator)
|
||||
|
||||
## Contributing
|
||||
|
||||
We'd love to have you contribute! Please refer to our [contribution guidelines](CONTRIBUTING.md) for details.
|
||||
|
|
|
|||
|
|
@ -1,37 +0,0 @@
|
|||
The following table shows the compatibility of `Jaeger Operator helm chart` with different components, in this particular case we shows Jaeger Operator, Kubernetes and Strimzi operator compatibility. Cert-manager installed or certificate for webhook service in a secret is required in version 2.29.0+ of the helm chart.
|
||||
|
||||
| Chart version | Jaeger Operator | Kubernetes | Strimzi Operator | Cert-Manager |
|
||||
|---------------------------|-----------------|-----------------|--------------------|--------------|
|
||||
| 2.57.0 | v1.61.x | v1.19 to v1.29 | v0.32 | v1.6.1+ |
|
||||
| 2.54.0 | v1.57.x | v1.19 to v1.29 | v0.32 | v1.6.1+ |
|
||||
| 2.50.0 | v1.52.x | v1.19 to v1.28 | v0.32 | v1.6.1+ |
|
||||
| 2.49.0 | v1.49.x | v1.19 to v1.28 | v0.32 | v1.6.1+ |
|
||||
| 2.47.0 | v1.47.x | v1.19 to v1.26 | v0.23 | v1.6.1+ |
|
||||
| 2.46.0 | v1.46.x | v1.19 to v1.26 | v0.23 | v1.6.1+ |
|
||||
| 2.45.0 | v1.45.x | v1.19 to v1.26 | v0.23 | v1.6.1+ |
|
||||
| 2.42.0 | v1.43.x | v1.19 to v1.26 | v0.23 | v1.6.1+ |
|
||||
| 2.41.0 | v1.42.x | v1.19 to v1.24 | v0.23 | v1.6.1+ |
|
||||
| (Missing) | | v1.19 to v1.23 | v0.23 | v1.6.1+ |
|
||||
| (Missing) | v1.41.x | v1.19 to v1.23 | v0.23 | v1.6.1+ |
|
||||
| (Missing) | v1.40.x | v1.19 to v1.23 | v0.23 | v1.6.1+ |
|
||||
| 2.37.0 | v1.39.x | v1.19 to v1.24 | v0.23 | v1.6.1+ |
|
||||
| 2.36.0 | v1.38.x | v1.19 to v1.24 | v0.23 | v1.6.1+ |
|
||||
| 2.35.0 | v1.37.x | v1.19 to v1.24 | v0.23 | v1.6.1+ |
|
||||
| 2.34.0 | v1.36.x | v1.19 to v1.24 | v0.23 | v1.6.1+ |
|
||||
| 2.33.0 | v1.35.x | v1.19 to v1.24 | v0.23 | v1.6.1+ |
|
||||
| 2.32.0(C), 2.32.1, 2.32.2 | v1.34.x | v1.19 to v1.24 | v0.23 | v1.6.1+ |
|
||||
| (Missing) | v1.33.x | v1.19 to v1.23 | v0.23 | v1.6.1+ |
|
||||
| 2.30.0(C), 2.31.0(C) | v1.32.x | v1.19 to v1.21 | v0.23 | v1.6.1+ |
|
||||
| 2.29.0(C) | v1.31.x | v1.19 to v1.21 | v0.23 | v1.6.1+ |
|
||||
| 2.28.0 | v1.30.x | v1.19 to v1.21 | v0.23 | |
|
||||
| 2.27.1 | v1.29.x | v1.19 to v1.21 | v0.23 | |
|
||||
| 2.27.0 | v1.28.x | v1.19 to v1.21 | v0.23 | |
|
||||
| 2.26.0 | v1.27.x | v1.19 to v1.21 | v0.23 | |
|
||||
| (Missing) | v1.26.x | v1.19 to v1.21 | v0.23 | |
|
||||
| (Missing) | v1.25.x | v1.19 to v1.21 | v0.23 | |
|
||||
| 2.23.0, 2.24.0, 2.25.0 | v1.24.x | v1.19 to v1.21 | v0.23 | |
|
||||
| (Missing) | v1.23.x | v1.19 to v1.21 | v0.19, v0.20 | |
|
||||
| 2.21.* | v1.22.x | v1.18 to v1.20 | v0.19 | |
|
||||
Legend:
|
||||
- `(C)` Chart is corrupted. Please do not use it, see [link](https://github.com/jaegertracing/helm-charts/issues/351) and [link](https://github.com/jaegertracing/helm-charts/issues/373)
|
||||
- `(Missing)` Missing chart version for specified Jaeger Operator version
|
||||
|
|
@ -1,12 +1,11 @@
|
|||
apiVersion: v1
|
||||
description: jaeger-operator Helm chart for Kubernetes
|
||||
name: jaeger-operator
|
||||
version: 2.57.0
|
||||
appVersion: 1.61.0
|
||||
version: 2.14.0
|
||||
appVersion: 1.17.0
|
||||
home: https://www.jaegertracing.io/
|
||||
icon: https://www.jaegertracing.io/img/jaeger-icon-reverse-color.svg
|
||||
sources:
|
||||
- https://github.com/jaegertracing/jaeger-operator
|
||||
source: https://github.com/jaegertracing/jaeger-operator
|
||||
maintainers:
|
||||
- email: ctadeu@gmail.com
|
||||
name: cpanato
|
||||
|
|
|
|||
|
|
@ -0,0 +1,6 @@
|
|||
approvers:
|
||||
- cpanato
|
||||
- batazor
|
||||
reviewers:
|
||||
- cpanato
|
||||
- batazor
|
||||
|
|
@ -14,13 +14,7 @@ This chart bootstraps a jaeger-operator deployment on a [Kubernetes](http://kube
|
|||
|
||||
## Prerequisites
|
||||
|
||||
- Kubernetes 1.19+
|
||||
- Helm 3
|
||||
- cert-manager 1.6.1+ installed, or certificate for webhook service in a secret
|
||||
|
||||
## Check compability matrix
|
||||
|
||||
See the compatibility matrix [here](./COMPATIBILITY.md).
|
||||
- Kubernetes 1.8+ with Beta APIs enabled
|
||||
|
||||
## Installing the Chart
|
||||
|
||||
|
|
@ -30,10 +24,10 @@ Add the Jaeger Tracing Helm repository:
|
|||
$ helm repo add jaegertracing https://jaegertracing.github.io/helm-charts
|
||||
```
|
||||
|
||||
To install the chart with the release name `my-release` in `observability` namespace:
|
||||
To install the chart with the release name `my-release`:
|
||||
|
||||
```console
|
||||
$ helm install my-release jaegertracing/jaeger-operator -n observability
|
||||
$ helm install --name my-release jaegertracing/jaeger-operator
|
||||
```
|
||||
|
||||
The command deploys jaeger-operator on the Kubernetes cluster in the default configuration. The [configuration](#configuration) section lists the parameters that can be configured during installation.
|
||||
|
|
@ -54,31 +48,24 @@ The command removes all the Kubernetes components associated with the chart and
|
|||
|
||||
The following table lists the configurable parameters of the jaeger-operator chart and their default values.
|
||||
|
||||
| Parameter | Description | Default |
|
||||
| :-------------------------- | :---------------------------------------------------------------------------------------------------------- |:--------------------------------|
|
||||
| `serviceExtraLabels` | Additional labels to jaeger-operator service | `{}` |
|
||||
| `extraLabels` | Additional labels to jaeger-operator deployment | `{}` |
|
||||
| `image.repository` | Controller container image repository | `jaegertracing/jaeger-operator` |
|
||||
| `image.tag` | Controller container image tag | `1.61.0` |
|
||||
| `image.pullPolicy` | Controller container image pull policy | `IfNotPresent` |
|
||||
| `jaeger.create` | Jaeger instance will be created | `false` |
|
||||
| `jaeger.spec` | Jaeger instance specification | `{}` |
|
||||
| `rbac.create` | All required roles and rolebindings will be created | `true` |
|
||||
| `serviceAccount.create` | Service account to use | `true` |
|
||||
| `rbac.pspEnabled` | Pod security policy for pod will be created and included in rbac role | `false` |
|
||||
| `rbac.clusterRole` | ClusterRole will be used by operator ServiceAccount | `false` |
|
||||
| `serviceAccount.name` | Service account name to use. If not set and create is true, a name is generated using the fullname template | `nil` |
|
||||
| `extraArgs` | Additional command line arguments arguments passed to the operator | `{}` |
|
||||
| `extraEnv` | Additional environment variables passed to the operator. For example: name: LOG-LEVEL value: debug | `[]` |
|
||||
| `replicaCount` | Desired number of operator pods | `1` |
|
||||
| `resources` | K8s pod resources | `None` |
|
||||
| `nodeSelector` | Node labels for pod assignment | `{}` |
|
||||
| `tolerations` | Toleration labels for pod assignment | `[]` |
|
||||
| `topologySpreadConstraints` | Topology Spread Constraints for pod assignment | `[]` |
|
||||
| `affinity` | Affinity settings for pod assignment | `{}` |
|
||||
| `securityContext` | Security context for pod | `{}` |
|
||||
| `containerSecurityContext` | Security context for the container | `{}` |
|
||||
| `priorityClassName` | Priority class name for the pod | `None` |
|
||||
| Parameter | Description | Default |
|
||||
| :---------------------- | :---------------------------------------------------------------------------------------------------------- | :------------------------------ |
|
||||
| `image.repository` | Controller container image repository | `jaegertracing/jaeger-operator` |
|
||||
| `image.tag` | Controller container image tag | `1.17.0` |
|
||||
| `image.pullPolicy` | Controller container image pull policy | `IfNotPresent` |
|
||||
| `jaeger.create` | Jaeger instance will be created | `false` |
|
||||
| `jaeger.spec` | Jaeger instance specification | `{}` |
|
||||
| `crd.install` | CustomResourceDefinition will be installed | `true` |
|
||||
| `rbac.create` | All required roles and rolebindings will be created | `true` |
|
||||
| `serviceAccount.create` | Service account to use | `true` |
|
||||
| `rbac.pspEnabled` | Pod security policy for pod will be created and included in rbac role | `false` |
|
||||
| `rbac.clusterRole` | ClusterRole will be used by operator ServiceAccount | `false` |
|
||||
| `serviceAccount.name` | Service account name to use. If not set and create is true, a name is generated using the fullname template | `nil` |
|
||||
| `resources` | K8s pod resources | `None` |
|
||||
| `nodeSelector` | Node labels for pod assignment | `{}` |
|
||||
| `tolerations` | Toleration labels for pod assignment | `[]` |
|
||||
| `affinity` | Affinity settings for pod assignment | `{}` |
|
||||
| `securityContext` | Security context for pod | `{}` |
|
||||
|
||||
Specify each parameter you'd like to override using a YAML file as described above in the [installation](#installing-the-chart) section.
|
||||
|
||||
|
|
@ -89,13 +76,6 @@ $ helm install jaegertracing/jaeger-operator --name my-release \
|
|||
--set rbac.create=false
|
||||
```
|
||||
|
||||
To install the chart without creating the CRDs (any files under `chart/crds`) make use of the `--skip-crds` flag. For example,
|
||||
|
||||
```console
|
||||
$ helm install jaegertracing/jaeger-operator --name my-release \
|
||||
--skip-crds
|
||||
```
|
||||
|
||||
## After the Helm Installation
|
||||
|
||||
### Creating a new Jaeger instance
|
||||
|
|
|
|||
File diff suppressed because it is too large
Load Diff
|
|
@ -2,7 +2,7 @@ jaeger-operator is installed.
|
|||
|
||||
|
||||
Check the jaeger-operator logs
|
||||
export POD=$(kubectl get pods -l app.kubernetes.io/instance={{ .Release.Name }} -l app.kubernetes.io/name=jaeger-operator --namespace {{ .Release.Namespace }} --output name)
|
||||
export POD=$(kubectl get pods-l app.kubernetes.io/instance={{ .Release.Name }} -lapp.kubernetes.io/name=jaeger-operator --namespace {{ .Release.Namespace }} --output name)
|
||||
kubectl logs $POD --namespace={{ .Release.Namespace }}
|
||||
|
||||
|
||||
|
|
|
|||
|
|
@ -45,5 +45,4 @@ Create chart name and version as used by the chart label.
|
|||
{{/* Generate basic labels */}}
|
||||
{{- define "jaeger-operator.labels" }}
|
||||
app.kubernetes.io/name: {{ include "jaeger-operator.name" . }}
|
||||
app.kubernetes.io/instance: {{ .Release.Name }}
|
||||
{{- end }}
|
||||
|
|
|
|||
|
|
@ -1,22 +0,0 @@
|
|||
{{- if .Values.certs.certificate.create }}
|
||||
apiVersion: cert-manager.io/v1
|
||||
kind: Certificate
|
||||
metadata:
|
||||
name: {{ default "jaeger-operator-service-cert" .Values.certs.certificate.secretName }}
|
||||
namespace: {{ .Release.Namespace }}
|
||||
spec:
|
||||
dnsNames:
|
||||
- "{{ default "jaeger-operator-webhook-service" .Values.webhooks.service.name }}.{{ .Release.Namespace }}.svc"
|
||||
- "{{ default "jaeger-operator-webhook-service" .Values.webhooks.service.name }}.{{ .Release.Namespace }}.svc.cluster.local"
|
||||
issuerRef:
|
||||
{{- if .Values.certs.issuer.create }}
|
||||
kind: Issuer
|
||||
{{- else }}
|
||||
kind: {{ .Values.certs.certificate.issuerKind }}
|
||||
{{- end }}
|
||||
name: {{ default "selfsigned-issuer" .Values.certs.issuer.name }}
|
||||
secretName: {{ default "jaeger-operator-service-cert" .Values.certs.certificate.secretName }}
|
||||
subject:
|
||||
organizationalUnits:
|
||||
- "{{ include "jaeger-operator.name" . }}"
|
||||
{{- end }}
|
||||
|
|
@ -0,0 +1,6 @@
|
|||
{{- if .Values.crd.install }}
|
||||
{{- range $path, $bytes := .Files.Glob "crds/*.yaml" }}
|
||||
{{ $.Files.Get $path }}
|
||||
---
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
|
@ -2,14 +2,10 @@ apiVersion: apps/v1
|
|||
kind: Deployment
|
||||
metadata:
|
||||
name: {{ include "jaeger-operator.fullname" . }}
|
||||
namespace: {{ .Release.Namespace }}
|
||||
labels:
|
||||
{{ include "jaeger-operator.labels" . | indent 4 }}
|
||||
{{- with .Values.extraLabels }}
|
||||
{{ . | toYaml | indent 4 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
replicas: {{ .Values.replicaCount }}
|
||||
replicas: 1
|
||||
selector:
|
||||
matchLabels:
|
||||
{{ include "jaeger-operator.labels" . | indent 6 }}
|
||||
|
|
@ -18,9 +14,6 @@ spec:
|
|||
name: {{ include "jaeger-operator.fullname" . }}
|
||||
labels:
|
||||
{{ include "jaeger-operator.labels" . | indent 8 }}
|
||||
{{- with .Values.extraLabels }}
|
||||
{{ . | toYaml | indent 8 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
{{- if .Values.serviceAccount.create }}
|
||||
serviceAccountName: {{ include "jaeger-operator.serviceAccountName" . }}
|
||||
|
|
@ -28,9 +21,6 @@ spec:
|
|||
{{- with .Values.securityContext }}
|
||||
securityContext:
|
||||
{{ toYaml . | indent 8 }}
|
||||
{{- end }}
|
||||
{{- if .Values.priorityClassName }}
|
||||
priorityClassName: {{ .Values.priorityClassName | quote }}
|
||||
{{- end }}
|
||||
{{- if and .Values.image.imagePullSecrets (not .Values.serviceAccount.create ) }}
|
||||
imagePullSecrets:
|
||||
|
|
@ -38,38 +28,14 @@ spec:
|
|||
- name: {{ . }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- if .Values.hostNetwork }}
|
||||
hostNetwork: {{ .Values.hostNetwork }}
|
||||
{{- end }}
|
||||
containers:
|
||||
- name: {{ include "jaeger-operator.fullname" . }}
|
||||
image: "{{ .Values.image.repository }}:{{ .Values.image.tag }}"
|
||||
imagePullPolicy: {{ .Values.image.pullPolicy }}
|
||||
ports:
|
||||
- containerPort: {{ .Values.metricsPort }}
|
||||
- containerPort: 8383
|
||||
name: metrics
|
||||
- containerPort: {{ .Values.webhooks.port }}
|
||||
name: webhook-server
|
||||
protocol: TCP
|
||||
volumeMounts:
|
||||
- mountPath: /tmp/k8s-webhook-server/serving-certs
|
||||
name: cert
|
||||
readOnly: true
|
||||
args:
|
||||
- start
|
||||
- {{ printf "--metrics-port=%v" .Values.metricsPort }}
|
||||
- {{ printf "--webhook-bind-port=%v" .Values.webhooks.port }}
|
||||
{{- $replicaCount := int .Values.replicaCount }}
|
||||
{{- if gt $replicaCount 1 }}
|
||||
- --leader-elect
|
||||
{{- end }}
|
||||
{{- range $key, $value := .Values.extraArgs }}
|
||||
{{- if $value }}
|
||||
- --{{ $key }}={{ $value }}
|
||||
{{- else }}
|
||||
- --{{ $key }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
args: ["start"]
|
||||
env:
|
||||
- name: WATCH_NAMESPACE
|
||||
{{- if .Values.rbac.clusterRole }}
|
||||
|
|
@ -89,20 +55,8 @@ spec:
|
|||
fieldPath: metadata.namespace
|
||||
- name: OPERATOR_NAME
|
||||
value: {{ include "jaeger-operator.fullname" . | quote }}
|
||||
{{- if .Values.extraEnv }}
|
||||
{{- toYaml .Values.extraEnv | nindent 12 }}
|
||||
{{- end }}
|
||||
resources:
|
||||
{{ toYaml .Values.resources | indent 12 }}
|
||||
{{- with .Values.containerSecurityContext }}
|
||||
securityContext:
|
||||
{{- toYaml . | nindent 12 }}
|
||||
{{- end }}
|
||||
volumes:
|
||||
- name: cert
|
||||
secret:
|
||||
defaultMode: 420
|
||||
secretName: {{ default "jaeger-operator-service-cert" .Values.certs.certificate.secretName }}
|
||||
{{- with .Values.nodeSelector }}
|
||||
nodeSelector:
|
||||
{{ toYaml . | indent 8 }}
|
||||
|
|
@ -113,9 +67,5 @@ spec:
|
|||
{{- end }}
|
||||
{{- with .Values.tolerations }}
|
||||
tolerations:
|
||||
{{ toYaml . | indent 8 }}
|
||||
{{- end }}
|
||||
{{- with .Values.topologySpreadConstraints }}
|
||||
topologySpreadConstraints:
|
||||
{{ toYaml . | indent 8 }}
|
||||
{{- end }}
|
||||
|
|
|
|||
|
|
@ -1,9 +0,0 @@
|
|||
{{- if .Values.certs.issuer.create }}
|
||||
apiVersion: cert-manager.io/v1
|
||||
kind: Issuer
|
||||
metadata:
|
||||
name: {{ default "selfsigned-issuer" .Values.certs.issuer.name }}
|
||||
namespace: {{ .Release.Namespace }}
|
||||
spec:
|
||||
selfSigned: {}
|
||||
{{- end }}
|
||||
|
|
@ -3,7 +3,6 @@ apiVersion: jaegertracing.io/v1
|
|||
kind: Jaeger
|
||||
metadata:
|
||||
name: {{ include "jaeger-operator.fullname" . }}-jaeger
|
||||
namespace: {{ default .Release.Namespace .Values.jaeger.namespace }}
|
||||
{{- with .Values.jaeger.spec }}
|
||||
spec:
|
||||
{{ toYaml . | indent 2}}
|
||||
|
|
|
|||
|
|
@ -1,57 +0,0 @@
|
|||
{{- if and (.Values.webhooks.mutatingWebhook.create) (.Values.webhooks.service.create) }}
|
||||
apiVersion: admissionregistration.k8s.io/v1
|
||||
kind: MutatingWebhookConfiguration
|
||||
metadata:
|
||||
annotations:
|
||||
cert-manager.io/inject-ca-from: {{ default .Release.Namespace .Values.certs.certificate.namespace }}/{{ default "jaeger-operator-service-cert" .Values.certs.certificate.secretName }}
|
||||
labels:
|
||||
{{ include "jaeger-operator.labels" . | indent 4 }}
|
||||
name: jaeger-operator-mutating-webhook-configuration
|
||||
webhooks:
|
||||
- admissionReviewVersions:
|
||||
- v1
|
||||
clientConfig:
|
||||
service:
|
||||
name: {{ default "jaeger-operator-webhook-service" .Values.webhooks.service.name }}
|
||||
namespace: {{ .Release.Namespace }}
|
||||
path: /mutate-v1-deployment
|
||||
failurePolicy: Ignore
|
||||
name: deployment.sidecar-injector.jaegertracing.io
|
||||
objectSelector:
|
||||
matchExpressions:
|
||||
- key: app.kubernetes.io/name
|
||||
operator: NotIn
|
||||
values:
|
||||
- {{ include "jaeger-operator.name" . }}
|
||||
rules:
|
||||
- apiGroups:
|
||||
- apps
|
||||
apiVersions:
|
||||
- v1
|
||||
operations:
|
||||
- CREATE
|
||||
- UPDATE
|
||||
resources:
|
||||
- deployments
|
||||
sideEffects: None
|
||||
- admissionReviewVersions:
|
||||
- v1
|
||||
clientConfig:
|
||||
service:
|
||||
name: {{ default "jaeger-operator-webhook-service" .Values.webhooks.service.name }}
|
||||
namespace: {{ .Release.Namespace }}
|
||||
path: /mutate-jaegertracing-io-v1-jaeger
|
||||
failurePolicy: Fail
|
||||
name: mjaeger.kb.io
|
||||
rules:
|
||||
- apiGroups:
|
||||
- jaegertracing.io
|
||||
apiVersions:
|
||||
- v1
|
||||
operations:
|
||||
- CREATE
|
||||
- UPDATE
|
||||
resources:
|
||||
- jaegers
|
||||
sideEffects: None
|
||||
{{- end }}
|
||||
|
|
@ -7,170 +7,90 @@ metadata:
|
|||
labels:
|
||||
{{ include "jaeger-operator.labels" . | indent 4 }}
|
||||
rules:
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- pods
|
||||
- services
|
||||
- endpoints
|
||||
- persistentvolumeclaims
|
||||
- events
|
||||
- configmaps
|
||||
- secrets
|
||||
- serviceaccounts
|
||||
verbs:
|
||||
- '*'
|
||||
- apiGroups:
|
||||
- apps
|
||||
resources:
|
||||
- daemonsets
|
||||
- deployments
|
||||
- daemonsets
|
||||
- replicasets
|
||||
- statefulsets
|
||||
verbs:
|
||||
- '*'
|
||||
- apiGroups:
|
||||
- monitoring.coreos.com
|
||||
resources:
|
||||
- servicemonitors
|
||||
verbs:
|
||||
- get
|
||||
- create
|
||||
- delete
|
||||
- get
|
||||
- list
|
||||
- patch
|
||||
- update
|
||||
- watch
|
||||
- apiGroups:
|
||||
- apps
|
||||
- io.jaegertracing
|
||||
resources:
|
||||
- deployments
|
||||
- '*'
|
||||
verbs:
|
||||
- create
|
||||
- delete
|
||||
- get
|
||||
- list
|
||||
- patch
|
||||
- update
|
||||
- watch
|
||||
- apiGroups:
|
||||
- apps
|
||||
resources:
|
||||
- deployments/status
|
||||
verbs:
|
||||
- get
|
||||
- patch
|
||||
- update
|
||||
- apiGroups:
|
||||
- autoscaling
|
||||
resources:
|
||||
- horizontalpodautoscalers
|
||||
verbs:
|
||||
- create
|
||||
- delete
|
||||
- get
|
||||
- list
|
||||
- patch
|
||||
- update
|
||||
- watch
|
||||
- apiGroups:
|
||||
- batch
|
||||
resources:
|
||||
- cronjobs
|
||||
- jobs
|
||||
verbs:
|
||||
- create
|
||||
- delete
|
||||
- get
|
||||
- list
|
||||
- patch
|
||||
- update
|
||||
- watch
|
||||
- apiGroups:
|
||||
- console.openshift.io
|
||||
resources:
|
||||
- consolelinks
|
||||
verbs:
|
||||
- create
|
||||
- delete
|
||||
- get
|
||||
- list
|
||||
- patch
|
||||
- update
|
||||
- watch
|
||||
- apiGroups:
|
||||
- coordination.k8s.io
|
||||
resources:
|
||||
- leases
|
||||
verbs:
|
||||
- create
|
||||
- get
|
||||
- list
|
||||
- update
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- configmaps
|
||||
- persistentvolumeclaims
|
||||
- pods
|
||||
- secrets
|
||||
- serviceaccounts
|
||||
- services
|
||||
- services/finalizers
|
||||
verbs:
|
||||
- create
|
||||
- delete
|
||||
- get
|
||||
- list
|
||||
- patch
|
||||
- update
|
||||
- watch
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- namespaces
|
||||
verbs:
|
||||
- create
|
||||
- delete
|
||||
- get
|
||||
- list
|
||||
- patch
|
||||
- update
|
||||
- watch
|
||||
- apiGroups:
|
||||
- ""
|
||||
resources:
|
||||
- namespaces/status
|
||||
verbs:
|
||||
- get
|
||||
- patch
|
||||
- update
|
||||
- '*'
|
||||
- apiGroups:
|
||||
- extensions
|
||||
resources:
|
||||
- replicasets
|
||||
- deployments
|
||||
- daemonsets
|
||||
- statefulsets
|
||||
- ingresses
|
||||
verbs:
|
||||
- create
|
||||
- delete
|
||||
- get
|
||||
- list
|
||||
- patch
|
||||
- update
|
||||
- watch
|
||||
- "*"
|
||||
- apiGroups:
|
||||
- image.openshift.io
|
||||
- batch
|
||||
resources:
|
||||
- imagestreams
|
||||
- jobs
|
||||
- cronjobs
|
||||
verbs:
|
||||
- get
|
||||
- list
|
||||
- watch
|
||||
- "*"
|
||||
- apiGroups:
|
||||
- route.openshift.io
|
||||
resources:
|
||||
- routes
|
||||
verbs:
|
||||
- "*"
|
||||
- apiGroups:
|
||||
- logging.openshift.io
|
||||
resources:
|
||||
- elasticsearches
|
||||
verbs:
|
||||
- '*'
|
||||
- apiGroups:
|
||||
- jaegertracing.io
|
||||
resources:
|
||||
- jaegers
|
||||
- '*'
|
||||
verbs:
|
||||
- create
|
||||
- delete
|
||||
- get
|
||||
- list
|
||||
- patch
|
||||
- update
|
||||
- watch
|
||||
- '*'
|
||||
- apiGroups:
|
||||
- jaegertracing.io
|
||||
- rbac.authorization.k8s.io
|
||||
resources:
|
||||
- jaegers/finalizers
|
||||
- clusterrolebindings
|
||||
verbs:
|
||||
- update
|
||||
- '*'
|
||||
- apiGroups:
|
||||
- jaegertracing.io
|
||||
- apps
|
||||
- extensions
|
||||
resourceNames:
|
||||
- jaeger-operator
|
||||
resources:
|
||||
- jaegers/status
|
||||
- deployments/finalizers
|
||||
verbs:
|
||||
- get
|
||||
- patch
|
||||
- update
|
||||
- apiGroups:
|
||||
- kafka.strimzi.io
|
||||
|
|
@ -178,92 +98,7 @@ rules:
|
|||
- kafkas
|
||||
- kafkausers
|
||||
verbs:
|
||||
- create
|
||||
- delete
|
||||
- get
|
||||
- list
|
||||
- patch
|
||||
- update
|
||||
- watch
|
||||
- apiGroups:
|
||||
- logging.openshift.io
|
||||
resources:
|
||||
- elasticsearch
|
||||
verbs:
|
||||
- create
|
||||
- delete
|
||||
- get
|
||||
- list
|
||||
- patch
|
||||
- update
|
||||
- watch
|
||||
- apiGroups:
|
||||
- logging.openshift.io
|
||||
resources:
|
||||
- elasticsearches
|
||||
verbs:
|
||||
- create
|
||||
- delete
|
||||
- get
|
||||
- list
|
||||
- patch
|
||||
- update
|
||||
- watch
|
||||
- apiGroups:
|
||||
- monitoring.coreos.com
|
||||
resources:
|
||||
- servicemonitors
|
||||
verbs:
|
||||
- create
|
||||
- delete
|
||||
- get
|
||||
- list
|
||||
- patch
|
||||
- update
|
||||
- watch
|
||||
- apiGroups:
|
||||
- networking.k8s.io
|
||||
resources:
|
||||
- ingresses
|
||||
verbs:
|
||||
- create
|
||||
- delete
|
||||
- get
|
||||
- list
|
||||
- patch
|
||||
- update
|
||||
- watch
|
||||
- apiGroups:
|
||||
- networking.k8s.io
|
||||
resources:
|
||||
- ingressclasses
|
||||
verbs:
|
||||
- list
|
||||
- watch
|
||||
- apiGroups:
|
||||
- rbac.authorization.k8s.io
|
||||
resources:
|
||||
- clusterrolebindings
|
||||
verbs:
|
||||
- create
|
||||
- delete
|
||||
- get
|
||||
- list
|
||||
- patch
|
||||
- update
|
||||
- watch
|
||||
- apiGroups:
|
||||
- route.openshift.io
|
||||
resources:
|
||||
- routes
|
||||
verbs:
|
||||
- create
|
||||
- delete
|
||||
- get
|
||||
- list
|
||||
- patch
|
||||
- update
|
||||
- watch
|
||||
- '*'
|
||||
{{- if .Values.rbac.pspEnabled }}
|
||||
- apiGroups: ['policy']
|
||||
resources: ['podsecuritypolicies']
|
||||
|
|
|
|||
|
|
@ -6,10 +6,6 @@ metadata:
|
|||
namespace: {{ .Release.Namespace }}
|
||||
labels:
|
||||
{{ include "jaeger-operator.labels" . | indent 4 }}
|
||||
{{- if .Values.serviceAccount.annotations }}
|
||||
annotations:
|
||||
{{ toYaml .Values.serviceAccount.annotations | indent 4 }}
|
||||
{{- end }}
|
||||
{{- if .Values.image.imagePullSecrets }}
|
||||
imagePullSecrets:
|
||||
{{- range .Values.image.imagePullSecrets }}
|
||||
|
|
|
|||
|
|
@ -2,47 +2,15 @@ apiVersion: v1
|
|||
kind: Service
|
||||
metadata:
|
||||
name: {{ include "jaeger-operator.fullname" . }}-metrics
|
||||
namespace: {{ .Release.Namespace }}
|
||||
labels:
|
||||
{{ include "jaeger-operator.labels" . | indent 4 }}
|
||||
{{- with .Values.serviceExtraLabels }}
|
||||
{{ . | toYaml | indent 4 }}
|
||||
{{- end }}
|
||||
{{- if .Values.service.annotations }}
|
||||
annotations:
|
||||
{{ toYaml .Values.service.annotations | indent 4 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
ports:
|
||||
- name: metrics
|
||||
port: {{ .Values.metricsPort }}
|
||||
port: 8383
|
||||
protocol: TCP
|
||||
targetPort: {{ .Values.metricsPort }}
|
||||
{{- if and (eq .Values.service.type "NodePort") (.Values.service.nodePort) }}
|
||||
nodePort: {{ .Values.service.nodePort }}
|
||||
{{- end }}
|
||||
targetPort: 8383
|
||||
selector:
|
||||
app.kubernetes.io/name: {{ include "jaeger-operator.name" . }}
|
||||
app.kubernetes.io/instance: {{ .Release.Name }}
|
||||
type: {{ .Values.service.type }}
|
||||
---
|
||||
{{- if .Values.webhooks.service.create }}
|
||||
apiVersion: v1
|
||||
kind: Service
|
||||
metadata:
|
||||
labels:
|
||||
{{ include "jaeger-operator.labels" . | indent 4 }}
|
||||
name: {{ default "jaeger-operator-webhook-service" .Values.webhooks.service.name }}
|
||||
namespace: {{ .Release.Namespace }}
|
||||
{{- if .Values.webhooks.service.annotations }}
|
||||
annotations:
|
||||
{{ toYaml .Values.webhooks.service.annotations | indent 4 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
ports:
|
||||
- port: 443
|
||||
protocol: TCP
|
||||
targetPort: {{ .Values.webhooks.port }}
|
||||
selector:
|
||||
{{ include "jaeger-operator.labels" . | indent 4 }}
|
||||
{{- end }}
|
||||
type: ClusterIP
|
||||
|
|
|
|||
|
|
@ -1,29 +0,0 @@
|
|||
{{- if and (.Values.webhooks.validatingWebhook.create) (.Values.webhooks.service.create) }}
|
||||
apiVersion: admissionregistration.k8s.io/v1
|
||||
kind: ValidatingWebhookConfiguration
|
||||
metadata:
|
||||
annotations:
|
||||
cert-manager.io/inject-ca-from: {{ default .Release.Namespace .Values.certs.certificate.namespace }}/{{ default "jaeger-operator-service-cert" .Values.certs.certificate.secretName }}
|
||||
name: jaeger-operator-validating-webhook-configuration
|
||||
webhooks:
|
||||
- admissionReviewVersions:
|
||||
- v1
|
||||
clientConfig:
|
||||
service:
|
||||
name: {{ default "jaeger-operator-webhook-service" .Values.webhooks.service.name }}
|
||||
namespace: {{ .Release.Namespace }}
|
||||
path: /validate-jaegertracing-io-v1-jaeger
|
||||
failurePolicy: Fail
|
||||
name: vjaeger.kb.io
|
||||
rules:
|
||||
- apiGroups:
|
||||
- jaegertracing.io
|
||||
apiVersions:
|
||||
- v1
|
||||
operations:
|
||||
- CREATE
|
||||
- UPDATE
|
||||
resources:
|
||||
- jaegers
|
||||
sideEffects: None
|
||||
{{- end }}
|
||||
|
|
@ -1,42 +1,18 @@
|
|||
# Default values for jaeger-operator.
|
||||
# This is a YAML-formatted file.
|
||||
# Declare variables to be passed into your templates.
|
||||
|
||||
image:
|
||||
repository: jaegertracing/jaeger-operator
|
||||
tag: 1.61.0
|
||||
tag: 1.17.0
|
||||
pullPolicy: IfNotPresent
|
||||
imagePullSecrets: []
|
||||
|
||||
certs:
|
||||
issuer:
|
||||
create: true
|
||||
name: ""
|
||||
certificate:
|
||||
create: true
|
||||
namespace: ""
|
||||
secretName: ""
|
||||
# Specify the cert-manager issuer kind to use an existing cert-manager
|
||||
# issuer; typically Issuer or ClusterIssuer
|
||||
# This field will be ignored if issuer.create is true
|
||||
issuerKind: Issuer
|
||||
|
||||
webhooks:
|
||||
mutatingWebhook:
|
||||
create: true
|
||||
validatingWebhook:
|
||||
create: true
|
||||
port: 9443
|
||||
service:
|
||||
annotations: {}
|
||||
create: true
|
||||
name: ""
|
||||
crd:
|
||||
install: true
|
||||
|
||||
jaeger:
|
||||
# Specifies whether Jaeger instance should be created
|
||||
create: false
|
||||
# namespace where Jaeger resource should be created default to .Release.Namespace
|
||||
namespace:
|
||||
spec: {}
|
||||
|
||||
rbac:
|
||||
|
|
@ -45,42 +21,12 @@ rbac:
|
|||
pspEnabled: false
|
||||
clusterRole: false
|
||||
|
||||
service:
|
||||
type: ClusterIP
|
||||
# Specify a specific node port when type is NodePort
|
||||
# nodePort: 32500
|
||||
# Annotations for service
|
||||
annotations: {}
|
||||
|
||||
serviceAccount:
|
||||
# Specifies whether a ServiceAccount should be created
|
||||
create: true
|
||||
# The name of the ServiceAccount to use.
|
||||
# If not set and create is true, a name is generated using the fullname template
|
||||
name:
|
||||
# Annotations for serviceAccount
|
||||
annotations: {}
|
||||
|
||||
extraArgs: {}
|
||||
# Specifies extra command line arguments arguments passed to the operator:
|
||||
# foo: bar
|
||||
|
||||
# Specifies extra environment variables passed to the operator:
|
||||
extraEnv: []
|
||||
# Specifies log-level for the operator:
|
||||
# - name: LOG-LEVEL
|
||||
# value: debug
|
||||
|
||||
serviceExtraLabels: {}
|
||||
# Specifies extra labels for the operator-metric service:
|
||||
# foo: bar
|
||||
|
||||
extraLabels: {}
|
||||
# Specifies extra labels for the operator deployment:
|
||||
# foo: bar
|
||||
|
||||
# Specifies desired number of operator pods
|
||||
replicaCount: 1
|
||||
|
||||
resources: {}
|
||||
# limits:
|
||||
|
|
@ -94,17 +40,6 @@ nodeSelector: {}
|
|||
|
||||
tolerations: []
|
||||
|
||||
topologySpreadConstraints: []
|
||||
|
||||
affinity: {}
|
||||
|
||||
securityContext: {}
|
||||
|
||||
containerSecurityContext: {}
|
||||
|
||||
priorityClassName:
|
||||
|
||||
# Specifies weather host network should be used
|
||||
hostNetwork: false
|
||||
|
||||
metricsPort: 8383
|
||||
|
|
|
|||
|
|
@ -1,15 +0,0 @@
|
|||
dependencies:
|
||||
- name: cassandra
|
||||
repository: https://charts.helm.sh/incubator
|
||||
version: 0.15.3
|
||||
- name: elasticsearch
|
||||
repository: https://charts.bitnami.com/bitnami
|
||||
version: 20.0.4
|
||||
- name: kafka
|
||||
repository: https://charts.bitnami.com/bitnami
|
||||
version: 26.6.2
|
||||
- name: common
|
||||
repository: https://charts.bitnami.com/bitnami
|
||||
version: 2.19.1
|
||||
digest: sha256:16dad4387f2b392d5034731f997518ff05b77909220ce45ee6dd69664942f2df
|
||||
generated: "2024-04-11T08:42:48.824851-04:00"
|
||||
|
|
@ -1,46 +1,23 @@
|
|||
apiVersion: v2
|
||||
appVersion: 1.53.0
|
||||
apiVersion: v1
|
||||
appVersion: 1.17.0
|
||||
description: A Jaeger Helm chart for Kubernetes
|
||||
name: jaeger
|
||||
type: application
|
||||
version: 3.4.1
|
||||
# CronJobs require v1.21
|
||||
kubeVersion: ">= 1.21-0"
|
||||
version: 0.20.0
|
||||
keywords:
|
||||
- jaeger
|
||||
- opentracing
|
||||
- tracing
|
||||
- instrumentation
|
||||
home: https://jaegertracing.io
|
||||
icon: https://www.jaegertracing.io/img/jaeger-icon-reverse-color.svg
|
||||
icon: https://camo.githubusercontent.com/afa87494e0753b4b1f5719a2f35aa5263859dffb/687474703a2f2f6a61656765722e72656164746865646f63732e696f2f656e2f6c61746573742f696d616765732f6a61656765722d766563746f722e737667
|
||||
sources:
|
||||
- https://hub.docker.com/u/jaegertracing/
|
||||
maintainers:
|
||||
- name: dvonthenen
|
||||
email: david.vonthenen@dell.com
|
||||
- name: mehta-ankit
|
||||
email: ankit.mehta@appian.com
|
||||
- name: mikelorant
|
||||
email: michael.lorant@fairfaxmedia.com.au
|
||||
- name: naseemkullah
|
||||
email: naseem@transit.app
|
||||
- name: pavelnikolov
|
||||
email: me@pavelnikolov.net
|
||||
- name: jkowall
|
||||
email: jkowall@kowall.net
|
||||
dependencies:
|
||||
- name: cassandra
|
||||
version: 0.15.3
|
||||
repository: https://charts.helm.sh/incubator
|
||||
condition: provisionDataStore.cassandra
|
||||
- name: elasticsearch
|
||||
version: 20.0.4
|
||||
repository: https://charts.bitnami.com/bitnami
|
||||
condition: provisionDataStore.elasticsearch
|
||||
- name: kafka
|
||||
version: 26.6.2
|
||||
repository: https://charts.bitnami.com/bitnami
|
||||
condition: provisionDataStore.kafka
|
||||
- name: common
|
||||
repository: https://charts.bitnami.com/bitnami
|
||||
version: 2.x.x
|
||||
email: pavel.nikolov@fairfaxmedia.com.au
|
||||
|
|
|
|||
|
|
@ -0,0 +1,10 @@
|
|||
approvers:
|
||||
- dvonthenen
|
||||
- mikelorant
|
||||
- naseemkullah
|
||||
- pavelnikolov
|
||||
reviewers:
|
||||
- dvonthenen
|
||||
- mikelorant
|
||||
- naseemkullah
|
||||
- pavelnikolov
|
||||
|
|
@ -14,7 +14,7 @@ Add the Jaeger Tracing Helm repository:
|
|||
helm repo add jaegertracing https://jaegertracing.github.io/helm-charts
|
||||
```
|
||||
|
||||
To install a release named `jaeger`:
|
||||
To install the chart with the release name `jaeger`, run the following command:
|
||||
|
||||
```bash
|
||||
helm install jaeger jaegertracing/jaeger
|
||||
|
|
@ -25,156 +25,27 @@ By default, the chart deploys the following:
|
|||
- Jaeger Agent DaemonSet
|
||||
- Jaeger Collector Deployment
|
||||
- Jaeger Query (UI) Deployment
|
||||
- Cassandra StatefulSet (subject to change!)
|
||||
- Cassandra StatefulSet
|
||||
|
||||
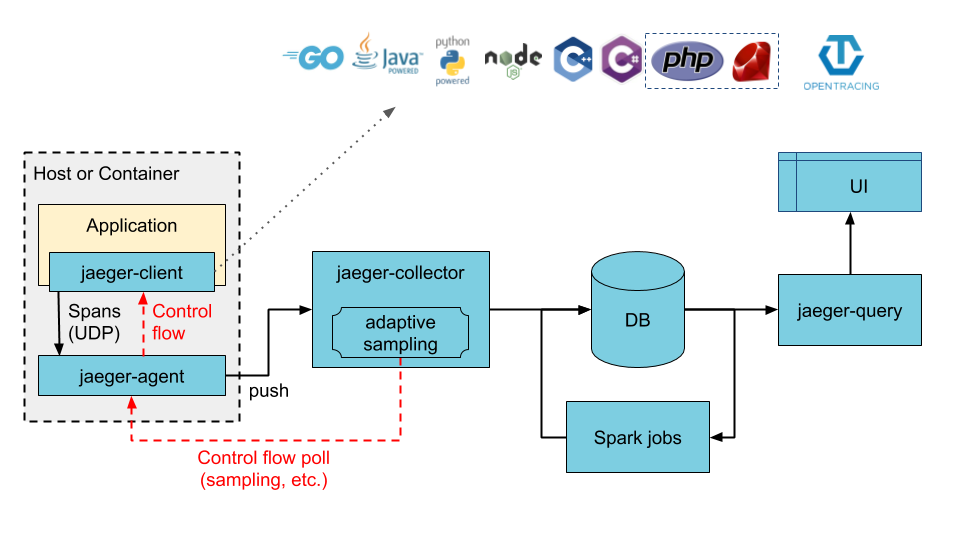
|
||||

|
||||
|
||||
## Configuration
|
||||
IMPORTANT NOTE: For testing purposes, the footprint for Cassandra can be reduced significantly in the event resources become constrained (such as running on your local laptop or in a Vagrant environment). You can override the resources required run running this command:
|
||||
|
||||
See [Customizing the Chart Before Installing](https://helm.sh/docs/intro/using_helm/#customizing-the-chart-before-installing). To see all configurable options with detailed comments, visit the chart's [values.yaml](https://github.com/jaegertracing/helm-charts/blob/master/charts/jaeger/values.yaml), or run these configuration commands:
|
||||
|
||||
```console
|
||||
$ helm show values jaegertracing/jaeger
|
||||
```
|
||||
|
||||
You may also `helm show values` on this chart's [dependencies](#dependencies) for additional options.
|
||||
|
||||
### Dependencies
|
||||
|
||||
If installing with a dependency such as Cassandra, Elasticsearch and/or Kafka
|
||||
their, values can be shown by running:
|
||||
|
||||
```console
|
||||
helm repo add elastic https://helm.elastic.co
|
||||
helm show values elastic/elasticsearch
|
||||
```
|
||||
|
||||
```console
|
||||
helm repo add incubator https://kubernetes-charts-incubator.storage.googleapis.com/
|
||||
helm show values incubator/cassandra
|
||||
```
|
||||
|
||||
```console
|
||||
helm repo add bitnami https://charts.bitnami.com/bitnami
|
||||
helm show values bitnami/kafka
|
||||
```
|
||||
|
||||
Please note, any dependency values must be nested within the key named after the
|
||||
chart, i.e. `elasticsearch`, `cassandra` and/or `kafka`.
|
||||
|
||||
## Storage
|
||||
|
||||
As per Jaeger documentation, for large scale production deployment the Jaeger
|
||||
team [recommends Elasticsearch backend over Cassandra](https://www.jaegertracing.io/docs/latest/faq/#what-is-the-recommended-storage-backend),
|
||||
as such the default backend may change in the future and **it is highly
|
||||
recommended to explicitly configure storage**.
|
||||
|
||||
If you are just starting out with a testing/demo setup, you can also use in-memory storage for a
|
||||
fast and easy setup experience using the [Jaeger All in One executable](https://www.jaegertracing.io/docs/1.29/getting-started/#all-in-one).
|
||||
|
||||
### Elasticsearch configuration
|
||||
|
||||
#### Elasticsearch Rollover
|
||||
|
||||
If using the [Elasticsearch
|
||||
Rollover](https://www.jaegertracing.io/docs/latest/deployment/#elasticsearch-rollover)
|
||||
feature, elasticsearch must already be present and so must be deployed
|
||||
separately from this chart, if not the rollover init hook won't be able to
|
||||
complete successfully.
|
||||
|
||||
#### Installing the Chart using a New ElasticSearch Cluster
|
||||
|
||||
To install the chart with the release name `jaeger` using a new ElasticSearch cluster instead of Cassandra (default), run the following command:
|
||||
|
||||
```console
|
||||
```bash
|
||||
helm install jaeger jaegertracing/jaeger \
|
||||
--set provisionDataStore.cassandra=false \
|
||||
--set provisionDataStore.elasticsearch=true \
|
||||
--set storage.type=elasticsearch
|
||||
--set cassandra.config.max_heap_size=1024M \
|
||||
--set cassandra.config.heap_new_size=256M \
|
||||
--set cassandra.resources.requests.memory=2048Mi \
|
||||
--set cassandra.resources.requests.cpu=0.4 \
|
||||
--set cassandra.resources.limits.memory=2048Mi \
|
||||
--set cassandra.resources.limits.cpu=0.4
|
||||
```
|
||||
|
||||
#### Installing the Chart using an Existing Elasticsearch Cluster
|
||||
|
||||
A release can be configured as follows to use an existing ElasticSearch cluster as it as the storage backend:
|
||||
|
||||
```console
|
||||
helm install jaeger jaegertracing/jaeger \
|
||||
--set provisionDataStore.cassandra=false \
|
||||
--set storage.type=elasticsearch \
|
||||
--set storage.elasticsearch.host=<HOST> \
|
||||
--set storage.elasticsearch.port=<PORT> \
|
||||
--set storage.elasticsearch.user=<USER> \
|
||||
--set storage.elasticsearch.password=<password>
|
||||
```
|
||||
|
||||
#### Installing the Chart using an Existing ElasticSearch Cluster with TLS
|
||||
|
||||
If you already have an existing running ElasticSearch cluster with TLS, you can configure the chart as follows to use it as your backing store:
|
||||
|
||||
Content of the `jaeger-values.yaml` file:
|
||||
|
||||
```YAML
|
||||
storage:
|
||||
type: elasticsearch
|
||||
elasticsearch:
|
||||
host: <HOST>
|
||||
port: <PORT>
|
||||
scheme: https
|
||||
user: <USER>
|
||||
password: <PASSWORD>
|
||||
provisionDataStore:
|
||||
cassandra: false
|
||||
elasticsearch: false
|
||||
query:
|
||||
cmdlineParams:
|
||||
es.tls.ca: "/tls/es.pem"
|
||||
extraConfigmapMounts:
|
||||
- name: jaeger-tls
|
||||
mountPath: /tls
|
||||
subPath: ""
|
||||
configMap: jaeger-tls
|
||||
readOnly: true
|
||||
collector:
|
||||
cmdlineParams:
|
||||
es.tls.ca: "/tls/es.pem"
|
||||
extraConfigmapMounts:
|
||||
- name: jaeger-tls
|
||||
mountPath: /tls
|
||||
subPath: ""
|
||||
configMap: jaeger-tls
|
||||
readOnly: true
|
||||
spark:
|
||||
enabled: true
|
||||
cmdlineParams:
|
||||
java.opts: "-Djavax.net.ssl.trustStore=/tls/trust.store -Djavax.net.ssl.trustStorePassword=changeit"
|
||||
extraConfigmapMounts:
|
||||
- name: jaeger-tls
|
||||
mountPath: /tls
|
||||
subPath: ""
|
||||
configMap: jaeger-tls
|
||||
readOnly: true
|
||||
|
||||
```
|
||||
|
||||
Generate configmap jaeger-tls:
|
||||
|
||||
```console
|
||||
keytool -import -trustcacerts -keystore trust.store -storepass changeit -alias es-root -file es.pem
|
||||
kubectl create configmap jaeger-tls --from-file=trust.store --from-file=es.pem
|
||||
```
|
||||
|
||||
```console
|
||||
helm install jaeger jaegertracing/jaeger --values jaeger-values.yaml
|
||||
```
|
||||
|
||||
### Cassandra configuration
|
||||
|
||||
#### Installing the Chart using an Existing Cassandra Cluster
|
||||
## Installing the Chart using an Existing Cassandra Cluster
|
||||
|
||||
If you already have an existing running Cassandra cluster, you can configure the chart as follows to use it as your backing store (make sure you replace `<HOST>`, `<PORT>`, etc with your values):
|
||||
|
||||
```console
|
||||
```bash
|
||||
helm install jaeger jaegertracing/jaeger \
|
||||
--set provisionDataStore.cassandra=false \
|
||||
--set storage.cassandra.host=<HOST> \
|
||||
|
|
@ -183,7 +54,7 @@ helm install jaeger jaegertracing/jaeger \
|
|||
--set storage.cassandra.password=<PASSWORD>
|
||||
```
|
||||
|
||||
#### Installing the Chart using an Existing Cassandra Cluster with TLS
|
||||
## Installing the Chart using an Existing Cassandra Cluster with TLS
|
||||
|
||||
If you already have an existing running Cassandra cluster with TLS, you can configure the chart as follows to use it as your backing store:
|
||||
|
||||
|
|
@ -233,220 +104,255 @@ data:
|
|||
|
||||
```
|
||||
|
||||
```console
|
||||
```bash
|
||||
kubectl apply -f jaeger-tls-cassandra-secret.yaml
|
||||
helm install jaeger jaegertracing/jaeger --values values.yaml
|
||||
```
|
||||
|
||||
### Ingester Configuration
|
||||
## Installing the Chart using a New ElasticSearch Cluster
|
||||
|
||||
#### Installing the Chart with Ingester enabled
|
||||
To install the chart with the release name `jaeger` using a new ElasticSearch cluster instead of Cassandra (default), run the following command:
|
||||
|
||||
```bash
|
||||
helm install jaeger jaegertracing/jaeger \
|
||||
--set provisionDataStore.cassandra=false \
|
||||
--set provisionDataStore.elasticsearch=true \
|
||||
--set storage.type=elasticsearch
|
||||
```
|
||||
|
||||
## Installing the Chart using an Existing Elasticsearch Cluster
|
||||
|
||||
A release can be configured as follows to use an existing ElasticSearch cluster as it as the storage backend:
|
||||
|
||||
```bash
|
||||
helm install jaeger jaegertracing/jaeger \
|
||||
--set provisionDataStore.cassandra=false \
|
||||
--set storage.type=elasticsearch \
|
||||
--set storage.elasticsearch.host=<HOST> \
|
||||
--set storage.elasticsearch.port=<PORT> \
|
||||
--set storage.elasticsearch.user=<USER> \
|
||||
--set storage.elasticsearch.password=<password>
|
||||
```
|
||||
|
||||
## Installing the Chart using an Existing ElasticSearch Cluster with TLS
|
||||
|
||||
If you already have an existing running ElasticSearch cluster with TLS, you can configure the chart as follows to use it as your backing store:
|
||||
|
||||
Content of the `jaeger-values.yaml` file:
|
||||
|
||||
```YAML
|
||||
storage:
|
||||
type: elasticsearch
|
||||
elasticsearch:
|
||||
host: <HOST>
|
||||
port: <PORT>
|
||||
scheme: https
|
||||
user: <USER>
|
||||
password: <PASSWORD>
|
||||
provisionDataStore:
|
||||
cassandra: false
|
||||
elasticsearch: false
|
||||
query:
|
||||
cmdlineParams:
|
||||
es.tls.ca: "/tls/es.pem"
|
||||
extraConfigmapMounts:
|
||||
- name: jaeger-tls
|
||||
mountPath: /tls
|
||||
subPath: ""
|
||||
configMap: jaeger-tls
|
||||
readOnly: true
|
||||
collector:
|
||||
cmdlineParams:
|
||||
es.tls.ca: "/tls/es.pem"
|
||||
extraConfigmapMounts:
|
||||
- name: jaeger-tls
|
||||
mountPath: /tls
|
||||
subPath: ""
|
||||
configMap: jaeger-tls
|
||||
readOnly: true
|
||||
spark:
|
||||
enabled: true
|
||||
cmdlineParams:
|
||||
java.opts: "-Djavax.net.ssl.trustStore=/tls/trust.store -Djavax.net.ssl.trustStorePassword=changeit"
|
||||
extraConfigmapMounts:
|
||||
- name: jaeger-tls
|
||||
mountPath: /tls
|
||||
subPath: ""
|
||||
configMap: jaeger-tls
|
||||
readOnly: true
|
||||
|
||||
```
|
||||
|
||||
Generate configmap jaeger-tls:
|
||||
```bash
|
||||
keytool -import -trustcacerts -keystore trust.store -storepass changeit -alias es-root -file es.pem
|
||||
kubectl create configmap jaeger-tls --from-file=trust.store --from-file=es.pem
|
||||
```
|
||||
|
||||
```bash
|
||||
helm install jaeger jaegertracing/jaeger --values jaeger-values.yaml
|
||||
```
|
||||
|
||||
## Installing the Chart with Ingester enabled
|
||||
|
||||
The architecture illustrated below can be achieved by enabling the ingester component. When enabled, Cassandra or Elasticsearch (depending on the configured values) now becomes the ingester's storage backend, whereas Kafka becomes the storage backend of the collector service.
|
||||
|
||||
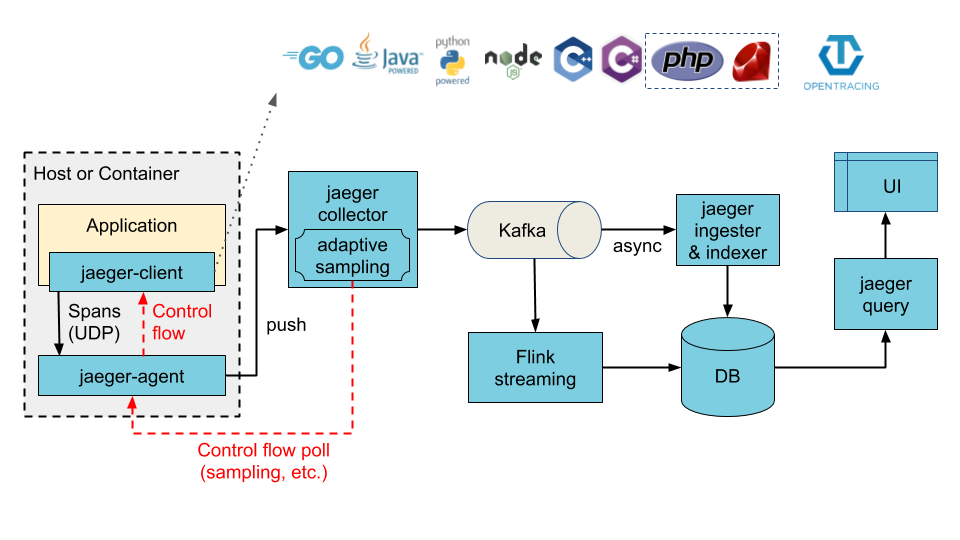
|
||||
|
||||
#### Installing the Chart with Ingester enabled using a New Kafka Cluster
|
||||
## Installing the Chart with Ingester enabled using a New Kafka Cluster
|
||||
|
||||
To provision a new Kafka cluster along with jaeger-ingester:
|
||||
|
||||
```console
|
||||
```bash
|
||||
helm install jaeger jaegertracing/jaeger \
|
||||
--set provisionDataStore.kafka=true \
|
||||
--set ingester.enabled=true
|
||||
```
|
||||
|
||||
#### Installing the Chart with Ingester using an existing Kafka Cluster
|
||||
## Installing the Chart with Ingester using an existing Kafka Cluster
|
||||
|
||||
You can use an existing Kafka cluster with jaeger too
|
||||
You can use an exisiting Kafka cluster with jaeger too
|
||||
|
||||
```console
|
||||
```bash
|
||||
helm install jaeger jaegertracing/jaeger \
|
||||
--set ingester.enabled=true \
|
||||
--set storage.kafka.brokers={<BROKER1:PORT>,<BROKER2:PORT>} \
|
||||
--set storage.kafka.topic=<TOPIC>
|
||||
```
|
||||
|
||||
### Other Storage Configuration
|
||||
## Configuration
|
||||
|
||||
If you are using grpc-plugin based storage, you can set environment
|
||||
variables that are needed by the plugin.
|
||||
The following table lists the configurable parameters of the Jaeger chart and their default values.
|
||||
|
||||
As as example if using the [jaeger-mongodb](https://github.com/mongodb-labs/jaeger-mongodb)
|
||||
plugin you can set the `MONGO_URL` as follows...
|
||||
| Parameter | Description | Default |
|
||||
|-----------|-------------|---------|
|
||||
| `<component>.nodeSelector` | Node selector | {} |
|
||||
| `<component>.tolerations` | Node tolerations | [] |
|
||||
| `<component.affinity` | Affinity | {} |
|
||||
| `<component>.podSecurityContext` | Pod security context | {} |
|
||||
| `<component>.securityContext` | Container security context | {} |
|
||||
| `<component>.serviceAccount.create` | Create service account | `true` |
|
||||
| `<component>.serviceAccount.name` | The name of the ServiceAccount to use. If not set and create is true, a name is generated using the fullname template | `` |
|
||||
| `agent.annotations` | Annotations for Agent | `nil` |
|
||||
| `agent.cmdlineParams` |Additional command line parameters| `nil` |
|
||||
| `agent.dnsPolicy` | Configure DNS policy for agents | `ClusterFirst` |
|
||||
| `agent.service.annotations` | Annotations for Agent SVC | `nil` |
|
||||
| `agent.service.binaryPort` | jaeger.thrift over binary thrift | `6832` |
|
||||
| `agent.service.compactPort` | jaeger.thrift over compact thrift| `6831` |
|
||||
| `agent.image` | Image for Jaeger Agent | `jaegertracing/jaeger-agent` |
|
||||
| `agent.podAnnotations` | Annotations for Agent pod | `nil` |
|
||||
| `agent.pullPolicy` | Agent image pullPolicy | `IfNotPresent` |
|
||||
| `agent.service.loadBalancerSourceRanges` | list of IP CIDRs allowed access to load balancer (if supported) | `[]` |
|
||||
| `agent.service.annotations` | Annotations for Agent SVC | `nil` |
|
||||
| `agent.service.binaryPort` | jaeger.thrift over binary thrift | `6832` |
|
||||
| `agent.service.compactPort` | jaeger.thrift over compact thrift | `6831` |
|
||||
| `agent.service.zipkinThriftPort` | zipkin.thrift over compact thrift | `5775` |
|
||||
| `agent.extraConfigmapMounts` | Additional agent configMap mounts | `[]` |
|
||||
| `agent.extraSecretMounts` | Additional agent secret mounts | `[]` |
|
||||
| `agent.useHostNetwork` | Enable hostNetwork for agents | `false` |
|
||||
| `collector.autoscaling.enabled` | Enable horizontal pod autoscaling | `false` |
|
||||
| `collector.autoscaling.minReplicas` | Minimum replicas | 2 |
|
||||
| `collector.autoscaling.maxReplicas` | Maximum replicas | 10 |
|
||||
| `collector.autoscaling.targetCPUUtilizationPercentage` | Target CPU utilization | 80 |
|
||||
| `collector.autoscaling.targetMemoryUtilizationPercentage` | Target memory utilization | `nil` |
|
||||
| `collector.cmdlineParams` | Additional command line parameters | `nil` |
|
||||
| `collector.podAnnotations` | Annotations for Collector pod | `nil` |
|
||||
| `collector.service.httpPort` | Client port for HTTP thrift | `14268` |
|
||||
| `collector.service.annotations` | Annotations for Collector SVC | `nil` |
|
||||
| `collector.image` | Image for jaeger collector | `jaegertracing/jaeger-collector` |
|
||||
| `collector.pullPolicy` | Collector image pullPolicy | `IfNotPresent` |
|
||||
| `collector.service.annotations` | Annotations for Collector SVC | `nil` |
|
||||
| `collector.service.httpPort` | Client port for HTTP thrift | `14268` |
|
||||
| `collector.service.loadBalancerSourceRanges` | list of IP CIDRs allowed access to load balancer (if supported) | `[]` |
|
||||
| `collector.service.tchannelPort` | Jaeger Agent port for thrift| `14267` |
|
||||
| `collector.service.type` | Service type | `ClusterIP` |
|
||||
| `collector.service.zipkinPort` | Zipkin port for JSON/thrift HTTP | `nil` |
|
||||
| `collector.extraConfigmapMounts` | Additional collector configMap mounts | `[]` |
|
||||
| `collector.extraSecretMounts` | Additional collector secret mounts | `[]` |
|
||||
| `collector.samplingConfig` | [Sampling strategies json file](https://www.jaegertracing.io/docs/latest/sampling/#collector-sampling-configuration) | `nil` |
|
||||
| `ingester.enabled` | Enable ingester component, collectors will write to Kafka | `false` |
|
||||
| `ingester.autoscaling.enabled` | Enable horizontal pod autoscaling | `false` |
|
||||
| `ingester.autoscaling.minReplicas` | Minimum replicas | 2 |
|
||||
| `ingester.autoscaling.maxReplicas` | Maximum replicas | 10 |
|
||||
| `ingester.autoscaling.targetCPUUtilizationPercentage` | Target CPU utilization | 80 |
|
||||
| `ingester.autoscaling.targetMemoryUtilizationPercentage` | Target memory utilization | `nil` |
|
||||
| `ingester.cmdlineParams` | Additional command line parameters | `nil` |
|
||||
| `ingester.podAnnotations` | Annotations for Ingester pod | `nil` |
|
||||
| `ingester.service.annotations` | Annotations for Ingester SVC | `nil` |
|
||||
| `ingester.image` | Image for jaeger Ingester | `jaegertracing/jaeger-ingester` |
|
||||
| `ingester.pullPolicy` | Ingester image pullPolicy | `IfNotPresent` |
|
||||
| `ingester.service.annotations` | Annotations for Ingester SVC | `nil` |
|
||||
| `ingester.service.loadBalancerSourceRanges` | list of IP CIDRs allowed access to load balancer (if supported) | `[]` |
|
||||
| `ingester.service.type` | Service type | `ClusterIP` |
|
||||
| `ingester.extraConfigmapMounts` | Additional Ingester configMap mounts | `[]` |
|
||||
| `ingester.extraSecretMounts` | Additional Ingester secret mounts | `[]` |
|
||||
| `fullnameOverride` | Override full name | `nil` |
|
||||
| `hotrod.enabled` | Enables the Hotrod demo app | `false` |
|
||||
| `hotrod.service.loadBalancerSourceRanges` | list of IP CIDRs allowed access to load balancer (if supported) | `[]` |
|
||||
| `nameOverride` | Override name| `nil` |
|
||||
| `provisionDataStore.cassandra` | Provision Cassandra Data Store| `true` |
|
||||
| `provisionDataStore.elasticsearch` | Provision Elasticsearch Data Store | `false` |
|
||||
| `provisionDataStore.kafka` | Provision Kafka Data Store | `false` |
|
||||
| `query.agentSidecar.enabled` | Enable agent sidecare for query deployment | `true` |
|
||||
| `query.service.annotations` | Annotations for Query SVC | `nil` |
|
||||
| `query.cmdlineParams` | Additional command line parameters | `nil` |
|
||||
| `query.image` | Image for Jaeger Query UI | `jaegertracing/jaeger-query` |
|
||||
| `query.ingress.enabled` | Allow external traffic access | `false` |
|
||||
| `query.ingress.annotations` | Configure annotations for Ingress | `{}` |
|
||||
| `query.ingress.hosts` | Configure host for Ingress | `nil` |
|
||||
| `query.ingress.tls` | Configure tls for Ingress | `nil` |
|
||||
| `query.podAnnotations` | Annotations for Query pod | `nil` |
|
||||
| `query.pullPolicy` | Query UI image pullPolicy | `IfNotPresent` |
|
||||
| `query.service.loadBalancerSourceRanges` | list of IP CIDRs allowed access to load balancer (if supported) | `[]` |
|
||||
| `query.service.port` | External accessible port | `80` |
|
||||
| `query.service.type` | Service type | `ClusterIP` |
|
||||
| `query.basePath` | Base path of Query UI, used for ingress as well (if it is enabled) | `/` |
|
||||
| `query.extraConfigmapMounts` | Additional query configMap mounts | `[]` |
|
||||
| `schema.annotations` | Annotations for the schema job| `nil` |
|
||||
| `schema.extraConfigmapMounts` | Additional cassandra schema job configMap mounts | `[]` |
|
||||
| `schema.image` | Image to setup cassandra schema | `jaegertracing/jaeger-cassandra-schema` |
|
||||
| `schema.mode` | Schema mode (prod or test) | `prod` |
|
||||
| `schema.pullPolicy` | Schema image pullPolicy | `IfNotPresent` |
|
||||
| `schema.activeDeadlineSeconds` | Deadline in seconds for cassandra schema creation job to complete | `120` |
|
||||
| `schema.traceTtl` | Time to live for trace data in seconds | `nil` |
|
||||
| `schema.keyspace` | Set explicit keyspace name | `nil` |
|
||||
| `schema.dependenciesTtl` | Time to live for dependencies data in seconds | `nil` |
|
||||
| `spark.enabled` | Enables the dependencies job| `false` |
|
||||
| `spark.image` | Image for the dependencies job| `jaegertracing/spark-dependencies` |
|
||||
| `spark.pullPolicy` | Image pull policy of the deps image | `Always` |
|
||||
| `spark.schedule` | Schedule of the cron job | `"49 23 * * *"` |
|
||||
| `spark.successfulJobsHistoryLimit` | Cron job successfulJobsHistoryLimit | `5` |
|
||||
| `spark.failedJobsHistoryLimit` | Cron job failedJobsHistoryLimit | `5` |
|
||||
| `spark.tag` | Tag of the dependencies job image | `latest` |
|
||||
| `spark.extraConfigmapMounts` | Additional spark configMap mounts | `[]` |
|
||||
| `spark.extraSecretMounts` | Additional spark secret mounts | `[]` |
|
||||
| `storage.cassandra.existingSecret` | Name of existing password secret object (for password authentication | `nil`
|
||||
| `storage.cassandra.host` | Provisioned cassandra host | `cassandra` |
|
||||
| `storage.cassandra.keyspace` | Schema name for cassandra | `jaeger_v1_test` |
|
||||
| `storage.cassandra.password` | Provisioned cassandra password (ignored if storage.cassandra.existingSecret set) | `password` |
|
||||
| `storage.cassandra.port` | Provisioned cassandra port | `9042` |
|
||||
| `storage.cassandra.tls.enabled` | Provisioned cassandra TLS connection enabled | `false` |
|
||||
| `storage.cassandra.tls.secretName` | Provisioned cassandra TLS connection existing secret name (possible keys in secret: `ca-cert.pem`, `client-key.pem`, `client-cert.pem`, `cqlshrc`, `commonName`) | `` |
|
||||
| `storage.cassandra.usePassword` | Use password | `true` |
|
||||
| `storage.cassandra.user` | Provisioned cassandra username | `user` |
|
||||
| `storage.elasticsearch.existingSecret` | Name of existing password secret object (for password authentication | `nil` |
|
||||
| `storage.elasticsearch.host` | Provisioned elasticsearch host| `elasticsearch` |
|
||||
| `storage.elasticsearch.password` | Provisioned elasticsearch password (ignored if storage.elasticsearch.existingSecret set | `changeme` |
|
||||
| `storage.elasticsearch.port` | Provisioned elasticsearch port| `9200` |
|
||||
| `storage.elasticsearch.scheme` | Provisioned elasticsearch scheme | `http` |
|
||||
| `storage.elasticsearch.usePassword` | Use password | `true` |
|
||||
| `storage.elasticsearch.user` | Provisioned elasticsearch user| `elastic` |
|
||||
| `storage.elasticsearch.indexPrefix` | Index Prefix for elasticsearch | `nil` |
|
||||
| `storage.elasticsearch.nodesWanOnly` | Only access specified es host | `false` |
|
||||
| `storage.kafka.brokers` | Broker List for Kafka with port | `kafka:9092` |
|
||||
| `storage.kafka.topic` | Topic name for Kafka | `jaeger_v1_test` |
|
||||
| `storage.type` | Storage type (ES or Cassandra)| `cassandra` |
|
||||
| `tag` | Image tag/version | `1.17.0` |
|
||||
|
||||
```YAML
|
||||
storage:
|
||||
type: grpc-plugin
|
||||
grpcPlugin:
|
||||
extraEnv:
|
||||
- name: MONGO_URL
|
||||
valueFrom:
|
||||
secretKeyRef:
|
||||
key: MONGO_URL
|
||||
name: jaeger-secrets
|
||||
```
|
||||
For more information about some of the tunable parameters that Cassandra provides, please visit the helm chart for [cassandra](https://github.com/kubernetes/charts/tree/master/incubator/cassandra) and the official [website](http://cassandra.apache.org/) at apache.org.
|
||||
|
||||
### All in One In-Memory Configuration
|
||||
For more information about some of the tunable parameters that Jaeger provides, please visit the official [Jaeger repo](https://github.com/uber/jaeger) at GitHub.com.
|
||||
|
||||
#### Installing the Chart using the All in One executable and in-memory storage
|
||||
### Pending enhancements
|
||||
|
||||
To install the chart with the release name `jaeger` using in-memory storage and the All in One
|
||||
executable, configure the chart as follows:
|
||||
|
||||
Content of the `values.yaml` file:
|
||||
|
||||
```yaml
|
||||
provisionDataStore:
|
||||
cassandra: false
|
||||
allInOne:
|
||||
enabled: true
|
||||
storage:
|
||||
type: memory
|
||||
agent:
|
||||
enabled: false
|
||||
collector:
|
||||
enabled: false
|
||||
query:
|
||||
enabled: false
|
||||
```
|
||||
|
||||
It's possible to specify resources, extra environment variables, and extra secrets for the all in one deployment:
|
||||
|
||||
```yaml
|
||||
allInOne:
|
||||
extraEnv:
|
||||
- name: QUERY_BASE_PATH
|
||||
value: /jaeger
|
||||
resources:
|
||||
limits:
|
||||
cpu: 500m
|
||||
memory: 512Mi
|
||||
requests:
|
||||
cpu: 256m
|
||||
memory: 128Mi
|
||||
extraSecretMounts:
|
||||
- name: jaeger-tls
|
||||
mountPath: /tls
|
||||
subPath: ""
|
||||
secretName: jaeger-tls
|
||||
readOnly: true
|
||||
```
|
||||
|
||||
```bash
|
||||
helm install jaeger jaegertracing/jaeger --values values.yaml
|
||||
```
|
||||
|
||||
## oAuth2 Sidecar
|
||||
If extra protection of the Jaeger UI is needed, then the oAuth2 sidecar can be enabled in the Jaeger Query. The oAuth2
|
||||
sidecar acts as a security proxy in front of the Jaeger Query service and enforces user authentication before reaching
|
||||
the Jaeger UI. This method can work with any valid provider including Keycloak, Azure, Google, GitHub, and more.
|
||||
|
||||
Offical docs [here](https://oauth2-proxy.github.io/oauth2-proxy/docs/behaviour)
|
||||
|
||||
Content of the `jaeger-values.yaml` file:
|
||||
|
||||
```YAML
|
||||
query:
|
||||
enabled: true
|
||||
oAuthSidecar:
|
||||
enabled: true
|
||||
resources: {}
|
||||
image:
|
||||
registry: quay.io
|
||||
repository: oauth2-proxy/oauth2-proxy
|
||||
tag: v7.6.0
|
||||
pullPolicy: IfNotPresent
|
||||
containerPort: 4180
|
||||
args:
|
||||
- --config
|
||||
- /etc/oauth2-proxy/oauth2-proxy.cfg
|
||||
- --client-secret
|
||||
- "$(client-secret)"
|
||||
extraEnv:
|
||||
- name: client-secret
|
||||
valueFrom:
|
||||
secretKeyRef:
|
||||
name: client-secret
|
||||
key: client-secret-key
|
||||
extraConfigmapMounts: []
|
||||
extraSecretMounts: []
|
||||
config: |-
|
||||
provider = "oidc"
|
||||
https_address = ":4180"
|
||||
upstreams = ["http://localhost:16686"]
|
||||
redirect_url = "https://jaeger-svc-domain/oauth2/callback"
|
||||
client_id = "jaeger-query"
|
||||
oidc_issuer_url = "https://keycloak-svc-domain/auth/realms/Default"
|
||||
cookie_secure = "true"
|
||||
cookie_secret = ""
|
||||
email_domains = "*"
|
||||
oidc_groups_claim = "groups"
|
||||
user_id_claim = "preferred_username"
|
||||
skip_provider_button = "true"
|
||||
```
|
||||
|
||||
## Installing extra kubernetes objects
|
||||
|
||||
If additional kubernetes objects need to be installed alongside this chart, set the `extraObjects` array to contain
|
||||
the yaml describing these objects. The values in the array are treated as a template to allow the use of variable
|
||||
substitution and function calls as in the example below.
|
||||
|
||||
Content of the `jaeger-values.yaml` file:
|
||||
|
||||
```YAML
|
||||
extraObjects:
|
||||
- apiVersion: rbac.authorization.k8s.io/v1
|
||||
kind: RoleBinding
|
||||
metadata:
|
||||
name: "{{ .Release.Name }}-someRoleBinding"
|
||||
roleRef:
|
||||
apiGroup: rbac.authorization.k8s.io
|
||||
kind: Role
|
||||
name: someRole
|
||||
subjects:
|
||||
- kind: ServiceAccount
|
||||
name: "{{ include \"jaeger.esLookback.serviceAccountName\" . }}"
|
||||
```
|
||||
|
||||
## Configuring the hotrod example application to send traces to the OpenTelemetry collector
|
||||
|
||||
If the `hotrod` example application is enabled it will export traces to Jaeger
|
||||
via the Jaeger exporter. To switch this to another collector and/or protocol,
|
||||
such as an OpenTelemetry OTLP Collector, see the example below.
|
||||
|
||||
The primary use case of sending the traces to the collector instead of directly
|
||||
to Jaeger is to verify traces can get back to Jaeger or another distributed
|
||||
tracing store and verify that pipeline with the pre-instrumented hotrod
|
||||
application.
|
||||
|
||||
**NOTE: This will not install or setup the OpenTelemetry collector. To setup an example OpenTelemetry Collector, see the [OpenTelemetry helm
|
||||
charts](https://github.com/open-telemetry/opentelemetry-helm-charts/tree/main/charts/opentelemetry-collector).**
|
||||
|
||||
Content of the `jaeger-values.yaml` file:
|
||||
|
||||
```YAML
|
||||
hotrod:
|
||||
enabled: true
|
||||
# Switch from the jaeger protocol to OTLP
|
||||
extraArgs:
|
||||
- --otel-exporter=otlp
|
||||
# Set the address of the OpenTelemetry collector endpoint
|
||||
extraEnv:
|
||||
- name: OTEL_EXPORTER_OTLP_ENDPOINT
|
||||
value: http://my-otel-collector-opentelemetry-collector:4318
|
||||
```
|
||||
|
||||
## Updating to Kafka to Kraft Mode
|
||||
|
||||
In the Kafka Helm Chart version 24.0.0 major refactors were done to support Kraft mode. More information can be found [here](https://github.com/bitnami/charts/tree/main/bitnami/kafka#to-2400).
|
||||
|
||||
#### Upgrading from Kraft mode
|
||||
|
||||
If you are upgrading from Kraft mode, follow the instructions [here](https://github.com/bitnami/charts/tree/main/bitnami/kafka#upgrading-from-zookeeper-mode).
|
||||
|
||||
#### Upgrading from Zookeeper mode
|
||||
|
||||
If you are upgrading from Zookeeper mode, follow the instructions [here](https://github.com/bitnami/charts/tree/main/bitnami/kafka#upgrading-from-zookeeper-mode).
|
||||
|
||||
After you complete the steps above, follow the instructions [here](https://github.com/bitnami/charts/tree/main/bitnami/kafka#migrating-from-zookeeper-early-access) to finally migrate from Zookeeper.
|
||||
- [ ] Sidecar deployment support
|
||||
|
|
|
|||
|
|
@ -0,0 +1,13 @@
|
|||
dependencies:
|
||||
- name: cassandra
|
||||
version: ^0.13.1
|
||||
repository: https://kubernetes-charts-incubator.storage.googleapis.com/
|
||||
condition: provisionDataStore.cassandra
|
||||
- name: elasticsearch
|
||||
version: ^7.5.1
|
||||
repository: https://helm.elastic.co
|
||||
condition: provisionDataStore.elasticsearch
|
||||
- name: kafka
|
||||
version: ^0.20.6
|
||||
repository: https://kubernetes-charts-incubator.storage.googleapis.com/
|
||||
condition: provisionDataStore.kafka
|
||||
|
|
@ -1,12 +1,3 @@
|
|||
|
||||
###################################################################
|
||||
### IMPORTANT: Ensure that storage is explicitly configured ###
|
||||
### Default storage options are subject to change. ###
|
||||
### ###
|
||||
### IMPORTANT: The use of <component>.env: {...} is deprecated. ###
|
||||
### Please use <component>.extraEnv: [] instead. ###
|
||||
###################################################################
|
||||
|
||||
You can log into the Jaeger Query UI here:
|
||||
|
||||
{{- if contains "NodePort" .Values.query.service.type }}
|
||||
|
|
|
|||
|
|
@ -56,9 +56,9 @@ Create the name of the cassandra schema service account to use
|
|||
*/}}
|
||||
{{- define "jaeger.cassandraSchema.serviceAccountName" -}}
|
||||
{{- if .Values.schema.serviceAccount.create -}}
|
||||
{{ default (printf "%s-cassandra-schema" (include "jaeger.fullname" .)) .Values.schema.serviceAccount.name }}
|
||||
{{ default (printf "%s-cassandra-schema" (include "jaeger.fullname" .)) .Values.schema.serviceAccount.name }}
|
||||
{{- else -}}
|
||||
{{ default "default" .Values.schema.serviceAccount.name }}
|
||||
{{ default "default" .Values.schema.serviceAccount.name }}
|
||||
{{- end -}}
|
||||
{{- end -}}
|
||||
|
||||
|
|
@ -67,42 +67,9 @@ Create the name of the spark service account to use
|
|||
*/}}
|
||||
{{- define "jaeger.spark.serviceAccountName" -}}
|
||||
{{- if .Values.spark.serviceAccount.create -}}
|
||||
{{ default (printf "%s-spark" (include "jaeger.fullname" .)) .Values.spark.serviceAccount.name }}
|
||||
{{ default (printf "%s-spark" (include "jaeger.fullname" .)) .Values.spark.serviceAccount.name }}
|
||||
{{- else -}}
|
||||
{{ default "default" .Values.spark.serviceAccount.name }}
|
||||
{{- end -}}
|
||||
{{- end -}}
|
||||
|
||||
{{/*
|
||||
Create the name of the esIndexCleaner service account to use
|
||||
*/}}
|
||||
{{- define "jaeger.esIndexCleaner.serviceAccountName" -}}
|
||||
{{- if .Values.esIndexCleaner.serviceAccount.create -}}
|
||||
{{ default (printf "%s-es-index-cleaner" (include "jaeger.fullname" .)) .Values.esIndexCleaner.serviceAccount.name }}
|
||||
{{- else -}}
|
||||
{{ default "default" .Values.esIndexCleaner.serviceAccount.name }}
|
||||
{{- end -}}
|
||||
{{- end -}}
|
||||
|
||||
{{/*
|
||||
Create the name of the esRollover service account to use
|
||||
*/}}
|
||||
{{- define "jaeger.esRollover.serviceAccountName" -}}
|
||||
{{- if .Values.esRollover.serviceAccount.create -}}
|
||||
{{ default (printf "%s-es-rollover" (include "jaeger.fullname" .)) .Values.esRollover.serviceAccount.name }}
|
||||
{{- else -}}
|
||||
{{ default "default" .Values.esRollover.serviceAccount.name }}
|
||||
{{- end -}}
|
||||
{{- end -}}
|
||||
|
||||
{{/*
|
||||
Create the name of the esLookback service account to use
|
||||
*/}}
|
||||
{{- define "jaeger.esLookback.serviceAccountName" -}}
|
||||
{{- if .Values.esLookback.serviceAccount.create -}}
|
||||
{{ default (printf "%s-es-lookback" (include "jaeger.fullname" .)) .Values.esLookback.serviceAccount.name }}
|
||||
{{- else -}}
|
||||
{{ default "default" .Values.esLookback.serviceAccount.name }}
|
||||
{{ default "default" .Values.spark.serviceAccount.name }}
|
||||
{{- end -}}
|
||||
{{- end -}}
|
||||
|
||||
|
|
@ -111,9 +78,9 @@ Create the name of the hotrod service account to use
|
|||
*/}}
|
||||
{{- define "jaeger.hotrod.serviceAccountName" -}}
|
||||
{{- if .Values.hotrod.serviceAccount.create -}}
|
||||
{{ default (printf "%s-hotrod" (include "jaeger.fullname" .)) .Values.hotrod.serviceAccount.name }}
|
||||
{{ default (printf "%s-hotrod" (include "jaeger.fullname" .)) .Values.hotrod.serviceAccount.name }}
|
||||
{{- else -}}
|
||||
{{ default "default" .Values.hotrod.serviceAccount.name }}
|
||||
{{ default "default" .Values.hotrod.serviceAccount.name }}
|
||||
{{- end -}}
|
||||
{{- end -}}
|
||||
|
||||
|
|
@ -122,9 +89,9 @@ Create the name of the query service account to use
|
|||
*/}}
|
||||
{{- define "jaeger.query.serviceAccountName" -}}
|
||||
{{- if .Values.query.serviceAccount.create -}}
|
||||
{{ default (include "jaeger.query.name" .) .Values.query.serviceAccount.name }}
|
||||
{{ default (include "jaeger.query.name" .) .Values.query.serviceAccount.name }}
|
||||
{{- else -}}
|
||||
{{ default "default" .Values.query.serviceAccount.name }}
|
||||
{{ default "default" .Values.query.serviceAccount.name }}
|
||||
{{- end -}}
|
||||
{{- end -}}
|
||||
|
||||
|
|
@ -133,9 +100,9 @@ Create the name of the agent service account to use
|
|||
*/}}
|
||||
{{- define "jaeger.agent.serviceAccountName" -}}
|
||||
{{- if .Values.agent.serviceAccount.create -}}
|
||||
{{ default (include "jaeger.agent.name" .) .Values.agent.serviceAccount.name }}
|
||||
{{ default (include "jaeger.agent.name" .) .Values.agent.serviceAccount.name }}
|
||||
{{- else -}}
|
||||
{{ default "default" .Values.agent.serviceAccount.name }}
|
||||
{{ default "default" .Values.agent.serviceAccount.name }}
|
||||
{{- end -}}
|
||||
{{- end -}}
|
||||
|
||||
|
|
@ -144,42 +111,20 @@ Create the name of the collector service account to use
|
|||
*/}}
|
||||
{{- define "jaeger.collector.serviceAccountName" -}}
|
||||
{{- if .Values.collector.serviceAccount.create -}}
|
||||
{{ default (include "jaeger.collector.name" .) .Values.collector.serviceAccount.name }}
|
||||
{{ default (include "jaeger.collector.name" .) .Values.collector.serviceAccount.name }}
|
||||
{{- else -}}
|
||||
{{ default "default" .Values.collector.serviceAccount.name }}
|
||||
{{ default "default" .Values.collector.serviceAccount.name }}
|
||||
{{- end -}}
|
||||
{{- end -}}
|
||||
|
||||
{{/*
|
||||
Create the collector ingress host
|
||||
*/}}
|
||||
{{- define "jaeger.collector.ingressHost" -}}
|
||||
{{- if (kindIs "string" .) }}
|
||||
{{- . }}
|
||||
{{- else }}
|
||||
{{- .host }}
|
||||
{{- end }}
|
||||
{{- end -}}
|
||||
|
||||
{{/*
|
||||
Create the collector ingress servicePort
|
||||
*/}}
|
||||
{{- define "jaeger.collector.ingressServicePort" -}}
|
||||
{{- if (kindIs "string" .context) }}
|
||||
{{- .defaultServicePort }}
|
||||
{{- else }}
|
||||
{{- .context.servicePort }}
|
||||
{{- end }}
|
||||
{{- end -}}
|
||||
|
||||
{{/*
|
||||
Create the name of the ingester service account to use
|
||||
*/}}
|
||||
{{- define "jaeger.ingester.serviceAccountName" -}}
|
||||
{{- if .Values.ingester.serviceAccount.create -}}
|
||||
{{ default (include "jaeger.ingester.name" .) .Values.ingester.serviceAccount.name }}
|
||||
{{ default (include "jaeger.ingester.name" .) .Values.ingester.serviceAccount.name }}
|
||||
{{- else -}}
|
||||
{{ default "default" .Values.ingester.serviceAccount.name }}
|
||||
{{ default "default" .Values.ingester.serviceAccount.name }}
|
||||
{{- end -}}
|
||||
{{- end -}}
|
||||
|
||||
|
|
@ -268,11 +213,7 @@ We truncate at 63 chars because some Kubernetes name fields are limited to this
|
|||
*/}}
|
||||
{{- define "elasticsearch.client.url" -}}
|
||||
{{- $port := .Values.storage.elasticsearch.port | toString -}}
|
||||
{{- $host := .Values.storage.elasticsearch.host }}
|
||||
{{- if .Values.provisionDataStore.elasticsearch }}
|
||||
{{- $host = printf "%s-elasticsearch" .Release.Name }}
|
||||
{{- end }}
|
||||
{{- printf "%s://%s:%s" .Values.storage.elasticsearch.scheme $host $port }}
|
||||
{{- printf "%s://%s:%s" .Values.storage.elasticsearch.scheme .Values.storage.elasticsearch.host $port }}
|
||||
{{- end -}}
|
||||
|
||||
{{- define "jaeger.hotrod.tracing.host" -}}
|
||||
|
|
@ -296,442 +237,3 @@ Configure list of IP CIDRs allowed access to load balancer (if supported)
|
|||
{{- $local := dict "first" true -}}
|
||||
{{- range $k, $v := . -}}{{- if not $local.first -}},{{- end -}}{{- $v -}}{{- $_ := set $local "first" false -}}{{- end -}}
|
||||
{{- end -}}
|
||||
|
||||
|
||||
{{/*
|
||||
Cassandra related environment variables
|
||||
*/}}
|
||||
{{- define "cassandra.env" -}}
|
||||
- name: CASSANDRA_SERVERS
|
||||
value: {{ include "cassandra.host" . }}
|
||||
- name: CASSANDRA_PORT
|
||||
value: {{ .Values.storage.cassandra.port | quote }}
|
||||
{{ if .Values.storage.cassandra.tls.enabled }}
|
||||
- name: CASSANDRA_TLS_ENABLED
|
||||
value: "true"
|
||||
- name: CASSANDRA_TLS_SERVER_NAME
|
||||
valueFrom:
|
||||
secretKeyRef:
|
||||
name: {{ .Values.storage.cassandra.tls.secretName }}
|
||||
key: commonName
|
||||
- name: CASSANDRA_TLS_KEY
|
||||
value: "/cassandra-tls/client-key.pem"
|
||||
- name: CASSANDRA_TLS_CERT
|
||||
value: "/cassandra-tls/client-cert.pem"
|
||||
- name: CASSANDRA_TLS_CA
|
||||
value: "/cassandra-tls/ca-cert.pem"
|
||||
{{- end }}
|
||||
{{- if .Values.storage.cassandra.keyspace }}
|
||||
- name: CASSANDRA_KEYSPACE
|
||||
value: {{ .Values.storage.cassandra.keyspace }}
|
||||
{{- end }}
|
||||
- name: CASSANDRA_USERNAME
|
||||
value: {{ .Values.storage.cassandra.user }}
|
||||
- name: CASSANDRA_PASSWORD
|
||||
valueFrom:
|
||||
secretKeyRef:
|
||||
name: {{ if .Values.storage.cassandra.existingSecret }}{{ .Values.storage.cassandra.existingSecret }}{{- else }}{{ include "jaeger.fullname" . }}-cassandra{{- end }}
|
||||
key: password
|
||||
{{- range $key, $value := .Values.storage.cassandra.env }}
|
||||
- name: {{ $key | quote }}
|
||||
value: {{ $value | quote }}
|
||||
{{ end -}}
|
||||
{{- if .Values.storage.cassandra.extraEnv }}
|
||||
{{ toYaml .Values.storage.cassandra.extraEnv }}
|
||||
{{- end }}
|
||||
{{- end -}}
|
||||
|
||||
{{/*
|
||||
Elasticsearch related environment variables
|
||||
*/}}
|
||||
{{- define "elasticsearch.env" -}}
|
||||
- name: ES_SERVER_URLS
|
||||
value: {{ include "elasticsearch.client.url" . }}
|
||||
{{- if not .Values.storage.elasticsearch.anonymous }}
|
||||
- name: ES_USERNAME
|
||||
value: {{ .Values.storage.elasticsearch.user }}
|
||||
{{- end }}
|
||||
{{- if .Values.storage.elasticsearch.usePassword }}
|
||||
- name: ES_PASSWORD
|
||||
valueFrom:
|
||||
secretKeyRef:
|
||||
name: {{ if .Values.storage.elasticsearch.existingSecret }}{{ .Values.storage.elasticsearch.existingSecret }}{{- else }}{{ include "jaeger.fullname" . }}-elasticsearch{{- end }}
|
||||
key: {{ default "password" .Values.storage.elasticsearch.existingSecretKey }}
|
||||
{{- end }}
|
||||
{{- if .Values.storage.elasticsearch.tls.enabled }}
|
||||
- name: ES_TLS_ENABLED
|
||||
value: "true"
|
||||
- name: ES_TLS_CA
|
||||
value: {{ .Values.storage.elasticsearch.tls.ca }}
|
||||
{{- end }}
|
||||
{{- if .Values.storage.elasticsearch.indexPrefix }}
|
||||
- name: ES_INDEX_PREFIX
|
||||
value: {{ .Values.storage.elasticsearch.indexPrefix }}
|
||||
{{- end }}
|
||||
{{- range $key, $value := .Values.storage.elasticsearch.env }}
|
||||
- name: {{ $key | quote }}
|
||||
value: {{ $value | quote }}
|
||||
{{ end -}}
|
||||
{{- if .Values.storage.elasticsearch.extraEnv }}
|
||||
{{ toYaml .Values.storage.elasticsearch.extraEnv }}
|
||||
{{- end }}
|
||||
{{- end -}}
|
||||
|
||||
{{/*
|
||||
grpcPlugin related environment variables
|
||||
*/}}
|
||||
{{- define "grpcPlugin.env" -}}
|
||||
{{- if .Values.storage.grpcPlugin.extraEnv }}
|
||||
{{- toYaml .Values.storage.grpcPlugin.extraEnv }}
|
||||
{{- end }}
|
||||
{{- end -}}
|
||||
|
||||
{{/*
|
||||
badger related environment variables
|
||||
*/}}
|
||||
{{- define "badger.env" -}}
|
||||
- name: BADGER_EPHEMERAL
|
||||
value: {{ .Values.storage.badger.ephemeral | quote }}
|
||||
{{- if not .Values.storage.badger.ephemeral }}
|
||||
- name: BADGER_DIRECTORY_VALUE
|
||||
value: {{ print .Values.storage.badger.persistence.mountPath "/badger/data" | quote }}
|
||||
- name: BADGER_DIRECTORY_KEY
|
||||
value: {{ print .Values.storage.badger.persistence.mountPath "/badger/key" | quote }}
|
||||
{{- end }}
|
||||
{{- if .Values.storage.badger.extraEnv }}
|
||||
{{- toYaml .Values.storage.badger.extraEnv }}
|
||||
{{- end }}
|
||||
{{- end -}}
|
||||
|
||||
{{/*
|
||||
memory related environment variables
|
||||
*/}}
|
||||
{{- define "memory.env" -}}
|
||||
{{- if .Values.storage.memory.extraEnv }}
|
||||
{{- toYaml .Values.storage.memory.extraEnv }}
|
||||
{{- end }}
|
||||
{{- end -}}
|
||||
|
||||
|
||||
{{/*
|
||||
Cassandra, Elasticsearch, or grpc-plugin, badger, memory related environment variables depending on which is used
|
||||
*/}}
|
||||
{{- define "storage.env" -}}
|
||||
{{- if eq .Values.storage.type "cassandra" -}}
|
||||
{{ include "cassandra.env" . }}
|
||||
{{- else if eq .Values.storage.type "elasticsearch" -}}
|
||||
{{ include "elasticsearch.env" . }}
|
||||
{{- else if or (eq .Values.storage.type "grpc-plugin") (eq .Values.storage.type "grpc") -}}
|
||||
{{ include "grpcPlugin.env" . }}
|
||||
{{- else if eq .Values.storage.type "badger" -}}
|
||||
{{ include "badger.env" . }}
|
||||
{{- else if eq .Values.storage.type "memory" -}}
|
||||
{{ include "memory.env" . }}
|
||||
{{- end -}}
|
||||
{{- end -}}
|
||||
|
||||
{{/*
|
||||
Cassandra related command line options
|
||||
*/}}
|
||||
{{- define "cassandra.cmdArgs" -}}
|
||||
{{- range $key, $value := .Values.storage.cassandra.cmdlineParams -}}
|
||||
{{- if $value }}
|
||||
- --{{ $key }}={{ $value }}
|
||||
{{- else }}
|
||||
- --{{ $key }}
|
||||
{{- end -}}
|
||||
{{- end -}}
|
||||
{{- end -}}
|
||||
|
||||
{{/*
|
||||
Elasticsearch related command line options
|
||||
*/}}
|
||||
{{- define "elasticsearch.cmdArgs" -}}
|
||||
{{- range $key, $value := .Values.storage.elasticsearch.cmdlineParams -}}
|
||||
{{- if $value }}
|
||||
- --{{ $key }}={{ $value }}
|
||||
{{- else }}
|
||||
- --{{ $key }}
|
||||
{{- end -}}
|
||||
{{- end -}}
|
||||
{{- end -}}
|
||||
|
||||
{{/*
|
||||
Cassandra or Elasticsearch related command line options depending on which is used
|
||||
*/}}
|
||||
{{- define "storage.cmdArgs" -}}
|
||||
{{- if eq .Values.storage.type "cassandra" -}}
|
||||
{{- include "cassandra.cmdArgs" . -}}
|
||||
{{- else if eq .Values.storage.type "elasticsearch" -}}
|
||||
{{- include "elasticsearch.cmdArgs" . -}}
|
||||
{{- end -}}
|
||||
{{- end -}}
|
||||
|
||||
{{/*
|
||||
Add extra argument to the command line options
|
||||
Usage:
|
||||
{{ include "extra.cmdArgs" ( dict "cmdlineParams" .Values.collector.cmdlineParams ) | nindent 10 }}
|
||||
*/}}
|
||||
{{- define "extra.cmdArgs" -}}
|
||||
{{- range $key, $value := .cmdlineParams -}}
|
||||
{{- if $value }}
|
||||
- --{{ $key }}={{ $value }}
|
||||
{{- else }}
|
||||
- --{{ $key }}
|
||||
{{- end }}
|
||||
{{- end -}}
|
||||
{{- end -}}
|
||||
|
||||
{{/*
|
||||
Provides a basic ingress network policy
|
||||
*/}}
|
||||
{{- define "jaeger.ingress.networkPolicy" -}}
|
||||
apiVersion: {{ include "common.capabilities.networkPolicy.apiVersion" . }}
|
||||
kind: NetworkPolicy
|
||||
metadata:
|
||||
name: {{ printf "%s-ingress" .Name }}
|
||||
namespace: {{ .Release.Namespace }}
|
||||
labels:
|
||||
app.kubernetes.io/component: {{ .Component }}
|
||||
{{- include "jaeger.labels" . | nindent 4 }}
|
||||
spec:
|
||||
podSelector:
|
||||
matchLabels:
|
||||
app.kubernetes.io/component: {{ .Component }}
|
||||
policyTypes:
|
||||
- Ingress
|
||||
ingress:
|
||||
{{- if or .ComponentValues.networkPolicy.ingressRules.namespaceSelector .ComponentValues.networkPolicy.ingressRules.podSelector }}
|
||||
- from:
|
||||
{{- if .ComponentValues.networkPolicy.ingressRules.namespaceSelector }}
|
||||
- namespaceSelector:
|
||||
matchLabels: {{- include "common.tplvalues.render" (dict "value" .ComponentValues.networkPolicy.ingressRules.namespaceSelector "context" $) | nindent 10 }}
|
||||
{{- end }}
|
||||
{{- if .ComponentValues.networkPolicy.ingressRules.podSelector }}
|
||||
- podSelector:
|
||||
matchLabels: {{- include "common.tplvalues.render" (dict "value" .ComponentValues.networkPolicy.ingressRules.podSelector "context" $) | nindent 10 }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- if .ComponentValues.networkPolicy.ingressRules.customRules }}
|
||||
{{- include "common.tplvalues.render" (dict "value" .ComponentValues.networkPolicy.ingressRules.customRules "context" $) | nindent 2 }}
|
||||
{{- end }}
|
||||
{{- end -}}
|
||||
|
||||
{{/*
|
||||
Provides a basic egress network policy
|
||||
*/}}
|
||||
{{- define "jaeger.egress.networkPolicy" -}}
|
||||
apiVersion: {{ include "common.capabilities.networkPolicy.apiVersion" . }}
|
||||
kind: NetworkPolicy
|
||||
metadata:
|
||||
name: {{ printf "%s-egress" .Name }}
|
||||
namespace: {{ .Release.Namespace }}
|
||||
labels:
|
||||
app.kubernetes.io/component: {{ .Component }}
|
||||
{{- include "jaeger.labels" . | nindent 4 }}
|
||||
spec:
|
||||
podSelector:
|
||||
matchLabels:
|
||||
app.kubernetes.io/component: {{ .Component }}
|
||||
policyTypes:
|
||||
- Egress
|
||||
egress:
|
||||
{{- if or .ComponentValues.networkPolicy.egressRules.namespaceSelector .ComponentValues.networkPolicy.egressRules.podSelector }}
|
||||
- to:
|
||||
{{- if .ComponentValues.networkPolicy.egressRules.namespaceSelector }}
|
||||
- namespaceSelector:
|
||||
matchLabels: {{- include "common.tplvalues.render" (dict "value" .ComponentValues.networkPolicy.egressRules.namespaceSelector "context" $) | nindent 10 }}
|
||||
{{- end }}
|
||||
{{- if .ComponentValues.networkPolicy.egressRules.podSelector }}
|
||||
- podSelector:
|
||||
matchLabels: {{- include "common.tplvalues.render" (dict "value" .ComponentValues.networkPolicy.egressRules.podSelector "context" $) | nindent 10 }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- if .ComponentValues.networkPolicy.egressRules.customRules }}
|
||||
{{- include "common.tplvalues.render" (dict "value" .ComponentValues.networkPolicy.egressRules.customRules "context" $) | nindent 2 }}
|
||||
{{- end }}
|
||||
{{- end -}}
|
||||
|
||||
{{/*
|
||||
Create image name value
|
||||
If not tag is provided, it defaults to .Chart.AppVersion.
|
||||
( dict "imageRoot" .Values.path.to.image "context" $ )
|
||||
*/}}
|
||||
{{- define "renderImage" -}}
|
||||
{{- $image := merge .imageRoot (dict "tag" .context.Chart.AppVersion) -}}
|
||||
{{- include "common.images.image" (dict "imageRoot" $image "global" .context.Values.global) -}}
|
||||
{{- end -}}
|
||||
|
||||
{{/*
|
||||
Create image name for all in one image
|
||||
*/}}
|
||||
{{- define "allInOne.image" -}}
|
||||
{{- include "renderImage" ( dict "imageRoot" .Values.allInOne.image "context" $ ) -}}
|
||||
{{- end -}}
|
||||
|
||||
{{/*
|
||||
Create pull secrets for all in one image
|
||||
*/}}
|
||||
{{- define "allInOne.imagePullSecrets" -}}
|
||||
{{- include "common.images.renderPullSecrets" (dict "images" (list .Values.allInOne.image) "context" $) -}}
|
||||
{{- end }}
|
||||
|
||||
{{/*
|
||||
Create image name for schema image
|
||||
*/}}
|
||||
{{- define "schema.image" -}}
|
||||
{{- include "renderImage" ( dict "imageRoot" .Values.schema.image "context" $ ) -}}
|
||||
{{- end -}}
|
||||
|
||||
{{/*
|
||||
Create pull secrets for schema image
|
||||
*/}}
|
||||
{{- define "schema.imagePullSecrets" -}}
|
||||
{{- include "common.images.renderPullSecrets" (dict "images" (list .Values.schema.image) "context" $) -}}
|
||||
{{- end }}
|
||||
|
||||
{{/*
|
||||
Create image name for ingester image
|
||||
*/}}
|
||||
{{- define "ingester.image" -}}
|
||||
{{- include "renderImage" ( dict "imageRoot" .Values.ingester.image "context" $ ) -}}
|
||||
{{- end -}}
|
||||
|
||||
{{/*
|
||||
Create pull secrets for ingester image
|
||||
*/}}
|
||||
{{- define "ingester.imagePullSecrets" -}}
|
||||
{{- include "common.images.renderPullSecrets" (dict "images" (list .Values.ingester.image) "context" $) -}}
|
||||
{{- end }}
|
||||
|
||||
{{/*
|
||||
Create image name for agent image
|
||||
*/}}
|
||||
{{- define "agent.image" -}}
|
||||
{{- include "renderImage" ( dict "imageRoot" .Values.agent.image "context" $ ) -}}
|
||||
{{- end -}}
|
||||
|
||||
{{/*
|
||||
Create pull secrets for agent image
|
||||
*/}}
|
||||
{{- define "agent.imagePullSecrets" -}}
|
||||
{{- include "common.images.renderPullSecrets" (dict "images" (list .Values.agent.image) "context" $) -}}
|
||||
{{- end }}
|
||||
|
||||
|
||||
{{/*
|
||||
Create image name for collector image
|
||||
*/}}
|
||||
{{- define "collector.image" -}}
|
||||
{{- include "renderImage" ( dict "imageRoot" .Values.collector.image "context" $ ) -}}
|
||||
{{- end -}}
|
||||
|
||||
{{/*
|
||||
Create pull secrets for collector image
|
||||
*/}}
|
||||
{{- define "collector.imagePullSecrets" -}}
|
||||
{{- include "common.images.renderPullSecrets" (dict "images" (list .Values.collector.image) "context" $) -}}
|
||||
{{- end }}
|
||||
|
||||
{{/*
|
||||
Create image name for query image
|
||||
*/}}
|
||||
{{- define "query.image" -}}
|
||||
{{- include "renderImage" ( dict "imageRoot" .Values.query.image "context" $ ) -}}
|
||||
{{- end -}}
|
||||
|
||||
{{/*
|
||||
Create pull secrets for query image
|
||||
*/}}
|
||||
{{- define "query.imagePullSecrets" -}}
|
||||
{{- include "common.images.renderPullSecrets" (dict "images" (list .Values.query.image .Values.query.oAuthSidecar.image) "context" $) -}}
|
||||
{{- end }}
|
||||
|
||||
{{/*
|
||||
Create image name for oAuthSidecar image
|
||||
*/}}
|
||||
{{- define "oAuthSidecar.image" -}}
|
||||
{{- include "common.images.image" (dict "imageRoot" .Values.query.oAuthSidecar.image "global" .Values.global) -}}
|
||||
{{- end -}}
|
||||
|
||||
{{/*
|
||||
Create image name for spark image
|
||||
*/}}
|
||||
{{- define "spark.image" -}}
|
||||
{{- include "common.images.image" (dict "imageRoot" .Values.spark.image "global" .Values.global) -}}
|
||||
{{- end -}}
|
||||
|
||||
{{/*
|
||||
Create pull secrets for spark image
|
||||
*/}}
|
||||
{{- define "spark.imagePullSecrets" -}}
|
||||
{{- include "common.images.renderPullSecrets" (dict "images" (list .Values.spark.image) "context" $) -}}
|
||||
{{- end }}
|
||||
|
||||
{{/*
|
||||
Create image name for esIndexCleaner image
|
||||
*/}}
|
||||
{{- define "esIndexCleaner.image" -}}
|
||||
{{- include "renderImage" ( dict "imageRoot" .Values.esIndexCleaner.image "context" $ ) -}}
|
||||
{{- end -}}
|
||||
|
||||
{{/*
|
||||
Create pull secrets for esIndexCleaner image
|
||||
*/}}
|
||||
{{- define "esIndexCleaner.imagePullSecrets" -}}
|
||||
{{- include "common.images.renderPullSecrets" (dict "images" (list .Values.esIndexCleaner.image) "context" $) -}}
|
||||
{{- end }}
|
||||
|
||||
{{/*
|
||||
Create image name for esRollover image
|
||||
*/}}
|
||||
{{- define "esRollover.image" -}}
|
||||
{{- include "renderImage" ( dict "imageRoot" .Values.esRollover.image "context" $ ) -}}
|
||||
{{- end -}}
|
||||
|
||||
{{/*
|
||||
Create pull secrets for esRollover image
|
||||
*/}}
|
||||
{{- define "esRollover.imagePullSecrets" -}}
|
||||
{{- include "common.images.renderPullSecrets" (dict "images" (list .Values.esRollover.image) "context" $) -}}
|
||||
{{- end }}
|
||||
|
||||
{{/*
|
||||
Create image name for esLookback image
|
||||
*/}}
|
||||
{{- define "esLookback.image" -}}
|
||||
{{- include "renderImage" ( dict "imageRoot" .Values.esLookback.image "context" $ ) -}}
|
||||
{{- end -}}
|
||||
|
||||
{{/*
|
||||
Create pull secrets for esLookback image
|
||||
*/}}
|
||||
{{- define "esLookback.imagePullSecrets" -}}
|
||||
{{- include "common.images.renderPullSecrets" (dict "images" (list .Values.esLookback.image) "context" $) -}}
|
||||
{{- end }}
|
||||
|
||||
{{/*
|
||||
Create image name for hotrod image
|
||||
*/}}
|
||||
{{- define "hotrod.image" -}}
|
||||
{{- include "renderImage" ( dict "imageRoot" .Values.hotrod.image "context" $ ) -}}
|
||||
{{- end -}}
|
||||
|
||||
{{/*
|
||||
Define curl image declaration
|
||||
*/}}
|
||||
{{- define "curl.image" -}}
|
||||
{{- $image := "curlimages/curl" -}}
|
||||
{{- if .Values.global.imageRegistry -}}
|
||||
{{ .Values.global.imageRegistry }}/{{ $image }}
|
||||
{{- else -}}
|
||||
{{ $image }}
|
||||
{{- end -}}
|
||||
{{- end -}}
|
||||
|
||||
{{/*
|
||||
Create pull secrets for hotrod image
|
||||
*/}}
|
||||
{{- define "hotrod.imagePullSecrets" -}}
|
||||
{{- include "common.images.renderPullSecrets" (dict "images" (list .Values.hotrod.image) "context" $) -}}
|
||||
{{- end }}
|
||||
|
|
|
|||
|
|
@ -8,64 +8,48 @@ metadata:
|
|||
app.kubernetes.io/component: agent
|
||||
{{- if .Values.agent.annotations }}
|
||||
annotations:
|
||||
{{- toYaml .Values.agent.annotations | nindent 4 }}
|
||||
{{ toYaml .Values.agent.annotations | indent 4 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
selector:
|
||||
matchLabels:
|
||||
{{- include "jaeger.selectorLabels" . | nindent 6 }}
|
||||
app.kubernetes.io/component: agent
|
||||
{{- with .Values.agent.daemonset.updateStrategy }}
|
||||
updateStrategy:
|
||||
{{- toYaml . | nindent 4 }}
|
||||
{{- end }}
|
||||
template:
|
||||
metadata:
|
||||
{{- if .Values.agent.podAnnotations }}
|
||||
annotations:
|
||||
{{- toYaml .Values.agent.podAnnotations | nindent 8 }}
|
||||
{{ toYaml .Values.agent.podAnnotations | indent 8 }}
|
||||
{{- end }}
|
||||
labels:
|
||||
{{- include "jaeger.selectorLabels" . | nindent 8 }}
|
||||
app.kubernetes.io/component: agent
|
||||
{{- if .Values.agent.podLabels }}
|
||||
{{- toYaml .Values.agent.podLabels | nindent 8 }}
|
||||
{{ toYaml .Values.agent.podLabels | indent 8 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
securityContext:
|
||||
{{- toYaml .Values.agent.podSecurityContext | nindent 8 }}
|
||||
{{ toYaml .Values.agent.podSecurityContext | indent 8 }}
|
||||
{{- if .Values.agent.useHostNetwork }}
|
||||
hostNetwork: true
|
||||
{{- end }}
|
||||
dnsPolicy: {{ .Values.agent.dnsPolicy }}
|
||||
{{- with .Values.agent.priorityClassName }}
|
||||
priorityClassName: {{ . }}
|
||||
{{- end }}
|
||||
serviceAccountName: {{ template "jaeger.agent.serviceAccountName" . }}
|
||||
{{- include "agent.imagePullSecrets" . | nindent 6 }}
|
||||
{{- if .Values.agent.initContainers }}
|
||||
initContainers:
|
||||
{{- toYaml .Values.agent.initContainers | nindent 8 }}
|
||||
{{- end}}
|
||||
containers:
|
||||
- name: {{ template "jaeger.agent.name" . }}
|
||||
securityContext:
|
||||
{{- toYaml .Values.agent.securityContext | nindent 10 }}
|
||||
image: {{ include "agent.image" . }}
|
||||
imagePullPolicy: {{ .Values.agent.image.pullPolicy }}
|
||||
args:
|
||||
{{ include "extra.cmdArgs" ( dict "cmdlineParams" .Values.agent.cmdlineParams ) | nindent 10 }}
|
||||
{{ toYaml .Values.agent.securityContext | indent 10 }}
|
||||
image: {{ .Values.agent.image }}:{{ .Values.tag }}
|
||||
imagePullPolicy: {{ .Values.agent.pullPolicy }}
|
||||
env:
|
||||
{{- if .Values.agent.extraEnv }}
|
||||
{{- toYaml .Values.agent.extraEnv | nindent 10 }}
|
||||
{{- end }}
|
||||
{{- if not (hasKey .Values.agent.cmdlineParams "reporter.grpc.host-port") }}
|
||||
- name: REPORTER_GRPC_HOST_PORT
|
||||
value: {{ include "jaeger.collector.name" . }}:{{ .Values.collector.service.grpc.port }}
|
||||
- name: REPORTER_GRPC_HOST_PORT
|
||||
value: {{ include "jaeger.collector.name" . }}:{{ .Values.collector.service.grpcPort }}
|
||||
{{- end }}
|
||||
{{- range $key, $value := .Values.agent.cmdlineParams }}
|
||||
- name: {{ $key | replace "." "_" | replace "-" "_" | upper | quote }}
|
||||
value: {{ $value | quote }}
|
||||
{{- end }}
|
||||
{{- with .Values.agent.envFrom }}
|
||||
envFrom: {{- toYaml . | nindent 10 }}
|
||||
{{- end }}
|
||||
ports:
|
||||
- name: zipkin-compact
|
||||
containerPort: {{ .Values.agent.service.zipkinThriftPort }}
|
||||
|
|
@ -103,7 +87,7 @@ spec:
|
|||
path: /
|
||||
port: admin
|
||||
resources:
|
||||
{{- toYaml .Values.agent.resources | nindent 10 }}
|
||||
{{ toYaml .Values.agent.resources | indent 10 }}
|
||||
volumeMounts:
|
||||
{{- range .Values.agent.extraConfigmapMounts }}
|
||||
- name: {{ .name }}
|
||||
|
|
|
|||
|
|
@ -6,9 +6,4 @@ metadata:
|
|||
labels:
|
||||
{{- include "jaeger.labels" . | nindent 4 }}
|
||||
app.kubernetes.io/component: agent
|
||||
{{- with .Values.agent.serviceAccount.annotations }}
|
||||
annotations:
|
||||
{{- toYaml . | nindent 4 }}
|
||||
{{- end }}
|
||||
automountServiceAccountToken: {{ .Values.agent.serviceAccount.automountServiceAccountToken }}
|
||||
{{- end -}}
|
||||
|
|
|
|||
|
|
@ -1,44 +0,0 @@
|
|||
{{- if and (.Values.agent.enabled) (.Values.agent.serviceMonitor.enabled)}}
|
||||
apiVersion: monitoring.coreos.com/v1
|
||||
kind: ServiceMonitor
|
||||
metadata:
|
||||
name: {{ template "jaeger.agent.name" . }}
|
||||
{{- if .Values.agent.serviceMonitor.namespace }}
|
||||
namespace: {{ .Values.agent.serviceMonitor.namespace }}
|
||||
{{- end }}
|
||||
labels:
|
||||
{{- include "jaeger.labels" . | nindent 4 }}
|
||||
app.kubernetes.io/component: agent
|
||||
{{- if .Values.agent.serviceMonitor.additionalLabels }}
|
||||
{{- toYaml .Values.agent.serviceMonitor.additionalLabels | nindent 4 }}
|
||||
{{- end }}
|
||||
{{- if .Values.agent.serviceMonitor.annotations }}
|
||||
annotations:
|
||||
{{- toYaml .Values.agent.serviceMonitor.annotations | nindent 4 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
endpoints:
|
||||
- port: admin
|
||||
path: /metrics
|
||||
{{- if .Values.agent.serviceMonitor.interval }}
|
||||
interval: {{ .Values.agent.serviceMonitor.interval }}
|
||||
{{- end }}
|
||||
{{- if .Values.agent.serviceMonitor.scrapeTimeout }}
|
||||
scrapeTimeout: {{ .Values.agent.serviceMonitor.scrapeTimeout }}
|
||||
{{- end }}
|
||||
{{- if .Values.agent.serviceMonitor.relabelings }}
|
||||
relabelings:
|
||||
{{- toYaml .Values.agent.serviceMonitor.relabelings | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- if .Values.agent.serviceMonitor.metricRelabelings }}
|
||||
metricRelabelings:
|
||||
{{- toYaml .Values.agent.serviceMonitor.metricRelabelings | nindent 8 }}
|
||||
{{- end }}
|
||||
namespaceSelector:
|
||||
matchNames:
|
||||
- {{ .Release.Namespace }}
|
||||
selector:
|
||||
matchLabels:
|
||||
app.kubernetes.io/component: agent
|
||||
app.kubernetes.io/instance: {{ .Release.Name }}
|
||||
{{- end }}
|
||||
|
|
@ -8,7 +8,7 @@ metadata:
|
|||
app.kubernetes.io/component: agent
|
||||
{{- if .Values.agent.service.annotations }}
|
||||
annotations:
|
||||
{{- toYaml .Values.agent.service.annotations | nindent 4 }}
|
||||
{{ toYaml .Values.agent.service.annotations | indent 4 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
ports:
|
||||
|
|
@ -28,10 +28,6 @@ spec:
|
|||
port: {{ .Values.agent.service.samplingPort }}
|
||||
protocol: TCP
|
||||
targetPort: http
|
||||
- name: admin
|
||||
port: 14271
|
||||
protocol: TCP
|
||||
targetPort: admin
|
||||
type: {{ .Values.agent.service.type }}
|
||||
selector:
|
||||
{{- include "jaeger.selectorLabels" . | nindent 4 }}
|
||||
|
|
|
|||
|
|
@ -1,30 +0,0 @@
|
|||
{{- if .Values.allInOne.enabled -}}
|
||||
apiVersion: v1
|
||||
kind: Service
|
||||
metadata:
|
||||
name: {{ template "jaeger.agent.name" . }}
|
||||
labels:
|
||||
{{- include "jaeger.labels" . | nindent 4 }}
|
||||
app.kubernetes.io/component: service-agent
|
||||
spec:
|
||||
clusterIP: None
|
||||
ports:
|
||||
- name: zk-compact-trft
|
||||
port: 5775
|
||||
protocol: UDP
|
||||
targetPort: 0
|
||||
- name: config-rest
|
||||
port: 5778
|
||||
targetPort: 0
|
||||
- name: jg-compact-trft
|
||||
port: 6831
|
||||
protocol: UDP
|
||||
targetPort: 0
|
||||
- name: jg-binary-trft
|
||||
port: 6832
|
||||
protocol: UDP
|
||||
targetPort: 0
|
||||
selector:
|
||||
{{- include "jaeger.selectorLabels" . | nindent 4 }}
|
||||
app.kubernetes.io/component: all-in-one
|
||||
{{- end -}}
|
||||
|
|
@ -1,48 +0,0 @@
|
|||
{{- if .Values.allInOne.enabled -}}
|
||||
apiVersion: v1
|
||||
kind: Service
|
||||
metadata:
|
||||
name: {{ template "jaeger.collector.name" . }}
|
||||
labels:
|
||||
{{- include "jaeger.labels" . | nindent 4 }}
|
||||
app.kubernetes.io/component: service-collector
|
||||
spec:
|
||||
clusterIP: {{ .Values.allInOne.service.headless | ternary "None" "null" }}
|
||||
ports:
|
||||
- name: http-zipkin
|
||||
port: 9411
|
||||
targetPort: 0
|
||||
{{- if semverCompare ">=1.20" .Capabilities.KubeVersion.Version }}
|
||||
appProtocol: http
|
||||
{{- end }}
|
||||
- name: grpc-http
|
||||
port: 14250
|
||||
targetPort: 0
|
||||
{{- if semverCompare ">=1.20" .Capabilities.KubeVersion.Version }}
|
||||
appProtocol: grpc
|
||||
{{- end }}
|
||||
- name: c-tchan-trft
|
||||
port: 14267
|
||||
targetPort: 0
|
||||
- name: http-c-binary-trft
|
||||
port: 14268
|
||||
targetPort: 0
|
||||
{{- if semverCompare ">=1.20" .Capabilities.KubeVersion.Version }}
|
||||
appProtocol: http
|
||||
{{- end }}
|
||||
- name: {{ .Values.allInOne.service.collector.otlp.grpc.name }}
|
||||
port: 4317
|
||||
targetPort: 0
|
||||
{{- if semverCompare ">=1.20" .Capabilities.KubeVersion.Version }}
|
||||
appProtocol: grpc
|
||||
{{- end }}
|
||||
- name: {{ .Values.allInOne.service.collector.otlp.http.name }}
|
||||
port: 4318
|
||||
targetPort: 0
|
||||
{{- if semverCompare ">=1.20" .Capabilities.KubeVersion.Version }}
|
||||
appProtocol: http
|
||||
{{- end }}
|
||||
selector:
|
||||
{{- include "jaeger.selectorLabels" . | nindent 4 }}
|
||||
app.kubernetes.io/component: all-in-one
|
||||
{{- end -}}
|
||||
|
|
@ -1,12 +0,0 @@
|
|||
{{- if .Values.allInOne.samplingConfig }}
|
||||
apiVersion: v1
|
||||
kind: ConfigMap
|
||||
metadata:
|
||||
name: {{ include "jaeger.fullname" . }}-sampling-strategies
|
||||
labels:
|
||||
{{- include "jaeger.labels" . | nindent 4 }}
|
||||
app.kubernetes.io/component: all-in-one
|
||||
data:
|
||||
strategies.json: |-
|
||||
{{ tpl .Values.allInOne.samplingConfig . | indent 4 }}
|
||||
{{- end }}
|
||||
|
|
@ -1,157 +0,0 @@
|
|||
{{- if .Values.allInOne.enabled -}}
|
||||
apiVersion: apps/v1
|
||||
kind: Deployment
|
||||
metadata:
|
||||
name: {{ template "jaeger.fullname" . }}
|
||||
labels:
|
||||
{{- include "jaeger.labels" . | nindent 4 }}
|
||||
app.kubernetes.io/component: all-in-one
|
||||
prometheus.io/port: "14269"
|
||||
prometheus.io/scrape: "true"
|
||||
spec:
|
||||
{{- if hasKey .Values.allInOne "replicas" }}
|
||||
replicas: {{ .Values.allInOne.replicas }}
|
||||
{{- end }}
|
||||
strategy:
|
||||
type: Recreate
|
||||
selector:
|
||||
matchLabels:
|
||||
{{- include "jaeger.selectorLabels" . | nindent 6 }}
|
||||
app.kubernetes.io/component: all-in-one
|
||||
template:
|
||||
metadata:
|
||||
labels:
|
||||
{{- include "jaeger.selectorLabels" . | nindent 8 }}
|
||||
app.kubernetes.io/component: all-in-one
|
||||
{{- if .Values.allInOne.podLabels }}
|
||||
{{- toYaml .Values.allInOne.podLabels | nindent 8 }}
|
||||
{{- end }}
|
||||
annotations:
|
||||
prometheus.io/port: "14269"
|
||||
prometheus.io/scrape: "true"
|
||||
spec:
|
||||
{{- include "allInOne.imagePullSecrets" . | nindent 6 }}
|
||||
containers:
|
||||
- env:
|
||||
{{- if .Values.allInOne.extraEnv }}
|
||||
{{- toYaml .Values.allInOne.extraEnv | nindent 12 }}
|
||||
{{- end }}
|
||||
- name: SPAN_STORAGE_TYPE
|
||||
value: {{ .Values.storage.type }}
|
||||
{{- include "storage.env" . | nindent 12 }}
|
||||
- name: COLLECTOR_ZIPKIN_HOST_PORT
|
||||
value: :9411
|
||||
- name: JAEGER_DISABLED
|
||||
value: "false"
|
||||
- name: COLLECTOR_OTLP_ENABLED
|
||||
value: "true"
|
||||
{{- if .Values.allInOne.samplingConfig }}
|
||||
- name: SAMPLING_STRATEGIES_FILE
|
||||
value: /etc/conf/strategies.json
|
||||
{{- end }}
|
||||
{{- with .Values.allInOne.envFrom }}
|
||||
envFrom: {{- toYaml . | nindent 12 }}
|
||||
{{- end }}
|
||||
securityContext:
|
||||
{{- toYaml .Values.allInOne.securityContext | nindent 12 }}
|
||||
image: {{ include "allInOne.image" . }}
|
||||
imagePullPolicy: {{ .Values.allInOne.image.pullPolicy }}
|
||||
name: jaeger
|
||||
args:
|
||||
{{- range $arg := .Values.allInOne.args }}
|
||||
- "{{ tpl $arg $ }}"
|
||||
{{- end }}
|
||||
ports:
|
||||
- containerPort: 5775
|
||||
protocol: UDP
|
||||
- containerPort: 6831
|
||||
protocol: UDP
|
||||
- containerPort: 6832
|
||||
protocol: UDP
|
||||
- containerPort: 5778
|
||||
protocol: TCP
|
||||
- containerPort: 16686
|
||||
protocol: TCP
|
||||
- containerPort: 16685
|
||||
protocol: TCP
|
||||
- containerPort: 9411
|
||||
protocol: TCP
|
||||
- containerPort: 4317
|
||||
protocol: TCP
|
||||
- containerPort: 4318
|
||||
protocol: TCP
|
||||
livenessProbe:
|
||||
failureThreshold: 5
|
||||
httpGet:
|
||||
path: /
|
||||
port: 14269
|
||||
scheme: HTTP
|
||||
initialDelaySeconds: 5
|
||||
periodSeconds: 15
|
||||
successThreshold: 1
|
||||
timeoutSeconds: 1
|
||||
readinessProbe:
|
||||
failureThreshold: 3
|
||||
httpGet:
|
||||
path: /
|
||||
port: 14269
|
||||
scheme: HTTP
|
||||
initialDelaySeconds: 1
|
||||
periodSeconds: 10
|
||||
successThreshold: 1
|
||||
timeoutSeconds: 1
|
||||
{{- with .Values.allInOne.resources }}
|
||||
resources:
|
||||
{{- toYaml . | nindent 12 }}
|
||||
{{- end }}
|
||||
volumeMounts:
|
||||
{{- if not .Values.storage.badger.ephemeral }}
|
||||
- name: badger-data
|
||||
mountPath: {{ .Values.storage.badger.persistence.mountPath }}
|
||||
{{- end }}
|
||||
{{- if .Values.allInOne.samplingConfig}}
|
||||
- name: strategies
|
||||
mountPath: /etc/conf/
|
||||
{{- end }}
|
||||
{{- range .Values.allInOne.extraSecretMounts }}
|
||||
- name: {{ .name }}
|
||||
mountPath: {{ .mountPath }}
|
||||
subPath: {{ .subPath }}
|
||||
readOnly: {{ .readOnly }}
|
||||
{{- end }}
|
||||
securityContext:
|
||||
{{- toYaml .Values.allInOne.podSecurityContext | nindent 8 }}
|
||||
serviceAccountName: {{ template "jaeger.fullname" . }}
|
||||
volumes:
|
||||
{{- if not .Values.storage.badger.ephemeral }}
|
||||
- name: badger-data
|
||||
persistentVolumeClaim:
|
||||
claimName: {{ .Values.storage.badger.persistence.useExistingPvcName | required "Using badger persistence it is required to set an existing PVC" }}
|
||||
{{- end }}
|
||||
{{- if .Values.allInOne.samplingConfig}}
|
||||
- name: strategies
|
||||
configMap:
|
||||
name: {{ include "jaeger.fullname" . }}-sampling-strategies
|
||||
{{- end }}
|
||||
{{- range .Values.allInOne.extraSecretMounts }}
|
||||
- name: {{ .name }}
|
||||
secret:
|
||||
secretName: {{ .secretName }}
|
||||
{{- end }}
|
||||
{{- with .Values.allInOne.affinity }}
|
||||
affinity:
|
||||
{{- toYaml . | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- with .Values.allInOne.topologySpreadConstraints }}
|
||||
topologySpreadConstraints:
|
||||
{{- toYaml . | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- with .Values.allInOne.nodeSelector }}
|
||||
nodeSelector:
|
||||
{{- toYaml . | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- with .Values.allInOne.tolerations }}
|
||||
tolerations:
|
||||
{{- toYaml . | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- end -}}
|
||||
|
|
@ -1,31 +0,0 @@
|
|||
{{- if and (.Values.allInOne.enabled) (.Values.allInOne.ingress.enabled) -}}
|
||||
{{- $ingressSupportsIngressClassName := eq (include "common.ingress.supportsIngressClassname" .) "true" }}
|
||||
apiVersion: networking.k8s.io/v1
|
||||
kind: Ingress
|
||||
metadata:
|
||||
name: {{ template "jaeger.query.name" . }}
|
||||
labels:
|
||||
{{- include "jaeger.labels" . | nindent 4 }}
|
||||
app.kubernetes.io/component: all-in-one
|
||||
{{- if .Values.allInOne.ingress.annotations }}
|
||||
annotations:
|
||||
{{- toYaml .Values.allInOne.ingress.annotations | nindent 4 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
{{- if and $ingressSupportsIngressClassName .Values.allInOne.ingress.ingressClassName }}
|
||||
ingressClassName: {{ .Values.allInOne.ingress.ingressClassName }}
|
||||
{{- end }}
|
||||
rules:
|
||||
{{- range $host := .Values.allInOne.ingress.hosts }}
|
||||
- host: {{ $host }}
|
||||
http:
|
||||
paths:
|
||||
- path: /
|
||||
pathType: {{ default "ImplementationSpecific" $.Values.allInOne.ingress.pathType }}
|
||||
backend: {{- include "common.ingress.backend" (dict "serviceName" (include "jaeger.query.name" $) "servicePort" 16686 "context" $) | nindent 14 }}
|
||||
{{- end -}}
|
||||
{{- if .Values.allInOne.ingress.tls }}
|
||||
tls:
|
||||
{{- toYaml .Values.allInOne.ingress.tls | nindent 4 }}
|
||||
{{- end -}}
|
||||
{{- end -}}
|
||||
|
|
@ -1,21 +0,0 @@
|
|||
{{- if .Values.allInOne.enabled -}}
|
||||
apiVersion: v1
|
||||
kind: Service
|
||||
metadata:
|
||||
name: {{ template "jaeger.query.name" . }}
|
||||
labels:
|
||||
{{- include "jaeger.labels" . | nindent 4 }}
|
||||
app.kubernetes.io/component: service-query
|
||||
spec:
|
||||
clusterIP: None
|
||||
ports:
|
||||
- name: http-query
|
||||
port: 16686
|
||||
targetPort: 16686
|
||||
- name: grpc-query
|
||||
port: 16685
|
||||
targetPort: 16685
|
||||
selector:
|
||||
{{- include "jaeger.selectorLabels" . | nindent 4 }}
|
||||
app.kubernetes.io/component: all-in-one
|
||||
{{- end -}}
|
||||
|
|
@ -1,14 +0,0 @@
|
|||
{{- if .Values.allInOne.enabled -}}
|
||||
apiVersion: v1
|
||||
kind: ServiceAccount
|
||||
metadata:
|
||||
name: {{ template "jaeger.fullname" . }}
|
||||
labels:
|
||||
{{- include "jaeger.labels" . | nindent 4 }}
|
||||
app.kubernetes.io/component: all-in-one
|
||||
{{- with .Values.allInOne.serviceAccount.annotations }}
|
||||
annotations:
|
||||
{{- toYaml . | nindent 4 }}
|
||||
{{- end }}
|
||||
automountServiceAccountToken: {{ .Values.allInOne.serviceAccount.automountServiceAccountToken }}
|
||||
{{- end -}}
|
||||
|
|
@ -1,6 +1,5 @@
|
|||
{{- if .Values.collector.enabled -}}
|
||||
{{- if eq .Values.storage.type "cassandra" -}}
|
||||
{{- if .Values.storage.cassandra.schemaJobEnabled -}}
|
||||
apiVersion: batch/v1
|
||||
kind: Job
|
||||
metadata:
|
||||
|
|
@ -10,55 +9,57 @@ metadata:
|
|||
app.kubernetes.io/component: cassandra-schema
|
||||
{{- if .Values.schema.annotations }}
|
||||
annotations:
|
||||
{{- toYaml .Values.schema.annotations | nindent 4 }}
|
||||
{{ toYaml .Values.schema.annotations | indent 4 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
activeDeadlineSeconds: {{ .Values.schema.activeDeadlineSeconds }}
|
||||
template:
|
||||
metadata:
|
||||
name: {{ include "jaeger.fullname" . }}-cassandra-schema
|
||||
{{- if .Values.schema.podAnnotations }}
|
||||
annotations:
|
||||
{{- toYaml .Values.schema.podAnnotations | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- if .Values.schema.podLabels }}
|
||||
labels:
|
||||
{{- toYaml .Values.schema.podLabels | nindent 8 }}
|
||||
{{ toYaml .Values.schema.podLabels | indent 8 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
securityContext:
|
||||
{{- toYaml .Values.schema.podSecurityContext | nindent 8 }}
|
||||
serviceAccountName: {{ template "jaeger.cassandraSchema.serviceAccountName" . }}
|
||||
{{- include "schema.imagePullSecrets" . | nindent 6 }}
|
||||
containers:
|
||||
- name: {{ include "jaeger.fullname" . }}-cassandra-schema
|
||||
image: {{ include "schema.image" . }}
|
||||
imagePullPolicy: {{ .Values.schema.image.pullPolicy }}
|
||||
securityContext:
|
||||
{{- toYaml .Values.schema.securityContext | nindent 10 }}
|
||||
image: {{ .Values.schema.image }}:{{ .Values.tag }}
|
||||
imagePullPolicy: {{ .Values.schema.pullPolicy }}
|
||||
env:
|
||||
{{- if .Values.schema.extraEnv }}
|
||||
{{- toYaml .Values.schema.extraEnv | nindent 10 }}
|
||||
{{- end }}
|
||||
{{ range $key, $value := .Values.schema.env }}
|
||||
- name: {{ $key | quote }}
|
||||
value: {{ $value | quote }}
|
||||
{{ end }}
|
||||
{{- include "cassandra.env" . | nindent 10 }}
|
||||
- name: CQLSH_HOST
|
||||
value: {{ template "cassandra.host" . }}
|
||||
{{ if .Values.storage.cassandra.tls.enabled }}
|
||||
- name: CQLSH_SSL
|
||||
value: "--ssl"
|
||||
{{- end }}
|
||||
- name: DATACENTER
|
||||
value: {{ .Values.cassandra.config.dc_name | quote }}
|
||||
{{- if .Values.storage.cassandra.keyspace }}
|
||||
- name: KEYSPACE
|
||||
value: {{ .Values.storage.cassandra.keyspace }}
|
||||
- name: CQLSH_HOST
|
||||
value: {{ template "cassandra.host" . }}
|
||||
{{ if .Values.storage.cassandra.tls.enabled }}
|
||||
- name: CQLSH_SSL
|
||||
value: "--ssl"
|
||||
{{- end }}
|
||||
- name: MODE
|
||||
value: {{ .Values.schema.mode | quote }}
|
||||
- name: DATACENTER
|
||||
value: {{ .Values.cassandra.config.dc_name | quote }}
|
||||
- name: CASSANDRA_PORT
|
||||
value: {{ .Values.storage.cassandra.port | quote }}
|
||||
- name: CASSANDRA_USERNAME
|
||||
value: {{ .Values.storage.cassandra.user }}
|
||||
- name: CASSANDRA_PASSWORD
|
||||
valueFrom:
|
||||
secretKeyRef:
|
||||
name: {{ if .Values.storage.cassandra.existingSecret }}{{ .Values.storage.cassandra.existingSecret }}{{- else }}{{ include "jaeger.fullname" . }}-cassandra{{- end }}
|
||||
key: password
|
||||
{{- if .Values.storage.cassandra.keyspace }}
|
||||
- name: KEYSPACE
|
||||
value: {{ .Values.storage.cassandra.keyspace | quote }}
|
||||
{{- end }}
|
||||
{{- if .Values.schema.traceTtl }}
|
||||
- name: TRACE_TTL
|
||||
value: {{ .Values.schema.traceTtl | quote }}
|
||||
{{- end }}
|
||||
{{- if .Values.schema.dependenciesTtl }}
|
||||
- name: DEPENDENCIES_TTL
|
||||
value: {{ .Values.schema.dependenciesTtl | quote }}
|
||||
{{- end }}
|
||||
resources:
|
||||
{{- toYaml .Values.schema.resources | nindent 10 }}
|
||||
{{ toYaml .Values.schema.resources | indent 10 }}
|
||||
volumeMounts:
|
||||
{{- range .Values.schema.extraConfigmapMounts }}
|
||||
- name: {{ .name }}
|
||||
|
|
@ -91,19 +92,5 @@ spec:
|
|||
configMap:
|
||||
name: {{ .configMap }}
|
||||
{{- end }}
|
||||
{{- if .Values.storage.cassandra.tls.enabled }}
|
||||
- name: {{ .Values.storage.cassandra.tls.secretName }}
|
||||
secret:
|
||||
secretName: {{ .Values.storage.cassandra.tls.secretName }}
|
||||
{{- end }}
|
||||
{{- with .Values.schema.tolerations }}
|
||||
tolerations:
|
||||
{{- toYaml . | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- with .Values.schema.nodeSelector }}
|
||||
nodeSelector:
|
||||
{{- toYaml . | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- end -}}
|
||||
{{- end -}}
|
||||
{{- end -}}
|
||||
|
|
|
|||
|
|
@ -6,5 +6,4 @@ metadata:
|
|||
labels:
|
||||
{{- include "jaeger.labels" . | nindent 4 }}
|
||||
app.kubernetes.io/component: cassandra-schema
|
||||
automountServiceAccountToken: {{ .Values.schema.serviceAccount.automountServiceAccountToken }}
|
||||
{{- end -}}
|
||||
|
|
|
|||
|
|
@ -8,7 +8,7 @@ metadata:
|
|||
app.kubernetes.io/component: collector
|
||||
{{- if .Values.collector.annotations }}
|
||||
annotations:
|
||||
{{- toYaml .Values.collector.annotations | nindent 4 }}
|
||||
{{ toYaml .Values.collector.annotations | indent 4 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
{{- if not .Values.collector.autoscaling.enabled }}
|
||||
|
|
@ -18,127 +18,122 @@ spec:
|
|||
matchLabels:
|
||||
{{- include "jaeger.selectorLabels" . | nindent 6 }}
|
||||
app.kubernetes.io/component: collector
|
||||
strategy:
|
||||
type: Recreate
|
||||
template:
|
||||
metadata:
|
||||
annotations:
|
||||
checksum/config-env: {{ include (print $.Template.BasePath "/collector-configmap.yaml") . | sha256sum }}
|
||||
{{- if .Values.collector.podAnnotations }}
|
||||
{{- toYaml .Values.collector.podAnnotations | nindent 8 }}
|
||||
{{ toYaml .Values.collector.podAnnotations | indent 8 }}
|
||||
{{- end }}
|
||||
labels:
|
||||
{{- include "jaeger.selectorLabels" . | nindent 8 }}
|
||||
app.kubernetes.io/component: collector
|
||||
{{- if .Values.collector.podLabels }}
|
||||
{{- toYaml .Values.collector.podLabels | nindent 8 }}
|
||||
{{ toYaml .Values.collector.podLabels | indent 8 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
{{- if .Values.provisionDataStore.elasticsearch }}
|
||||
initContainers:
|
||||
- name: elasticsearch-checker
|
||||
image: {{ include "curl.image" . }}
|
||||
command:
|
||||
- sh
|
||||
- "-c"
|
||||
- |
|
||||
url="{{ include "elasticsearch.client.url" . }}"
|
||||
until [ "$(curl -s -o /dev/null -w '%{http_code}' "$url/_cluster/health")" = "200" ]; do
|
||||
echo "Waiting for Elasticsearch at $url"
|
||||
sleep 5
|
||||
done
|
||||
{{- end}}
|
||||
{{- with .Values.collector.priorityClassName }}
|
||||
priorityClassName: {{ . }}
|
||||
{{- end }}
|
||||
securityContext:
|
||||
{{- toYaml .Values.collector.podSecurityContext | nindent 8 }}
|
||||
{{ toYaml .Values.collector.podSecurityContext | indent 8 }}
|
||||
serviceAccountName: {{ template "jaeger.collector.serviceAccountName" . }}
|
||||
{{- include "collector.imagePullSecrets" . | nindent 6 }}
|
||||
{{- if .Values.collector.initContainers }}
|
||||
initContainers:
|
||||
{{- toYaml .Values.collector.initContainers | nindent 8 }}
|
||||
{{- end}}
|
||||
containers:
|
||||
- name: {{ template "jaeger.collector.name" . }}
|
||||
securityContext:
|
||||
{{- toYaml .Values.collector.securityContext | nindent 10 }}
|
||||
image: {{ include "collector.image" . }}
|
||||
imagePullPolicy: {{ .Values.collector.image.pullPolicy }}
|
||||
args:
|
||||
{{ include "extra.cmdArgs" ( dict "cmdlineParams" .Values.collector.cmdlineParams ) | nindent 10 }}
|
||||
{{- if not .Values.ingester.enabled -}}
|
||||
{{- include "storage.cmdArgs" . | nindent 10 }}
|
||||
{{- end }}
|
||||
{{ toYaml .Values.collector.securityContext | indent 10 }}
|
||||
image: {{ .Values.collector.image }}:{{ .Values.tag }}
|
||||
imagePullPolicy: {{ .Values.collector.pullPolicy }}
|
||||
env:
|
||||
{{- if .Values.collector.extraEnv }}
|
||||
{{- toYaml .Values.collector.extraEnv | nindent 10 }}
|
||||
{{- end }}
|
||||
{{- if .Values.collector.service.zipkin }}
|
||||
- name: COLLECTOR_ZIPKIN_HOST_PORT
|
||||
value: {{ .Values.collector.service.zipkin.port | quote }}
|
||||
{{- end }}
|
||||
{{- if or .Values.collector.service.otlp.grpc .Values.collector.service.otlp.http }}
|
||||
- name: COLLECTOR_OTLP_ENABLED
|
||||
value: "true"
|
||||
{{- if ne (default 4317 .Values.collector.service.otlp.grpc.port | toString ) "4317" }}
|
||||
- name: COLLECTOR_OTLP_GRPC_HOST_PORT
|
||||
value: {{ .Values.collector.service.otlp.grpc.port | quote }}
|
||||
{{- end }}
|
||||
{{- if ne (default 4318 .Values.collector.service.otlp.http.port | toString) "4318" }}
|
||||
- name: COLLECTOR_OTLP_HTTP_HOST_PORT
|
||||
value: {{ .Values.collector.service.otlp.http.port | quote }}
|
||||
{{- range $key, $value := .Values.collector.cmdlineParams }}
|
||||
- name: {{ $key | replace "." "_" | replace "-" "_" | upper | quote }}
|
||||
value: {{ $value | quote }}
|
||||
{{- end }}
|
||||
{{- if .Values.collector.service.zipkinPort }}
|
||||
- name: COLLECTOR_ZIPKIN_HTTP_PORT
|
||||
value: {{ .Values.collector.service.zipkinPort | quote }}
|
||||
{{- end }}
|
||||
{{- if .Values.ingester.enabled }}
|
||||
- name: SPAN_STORAGE_TYPE
|
||||
value: kafka
|
||||
{{- range $key, $value := .Values.storage.kafka.env }}
|
||||
- name: {{ $key | quote }}
|
||||
value: {{ $value | quote }}
|
||||
{{- end }}
|
||||
{{- if .Values.storage.kafka.extraEnv }}
|
||||
{{- toYaml .Values.storage.kafka.extraEnv | nindent 10 }}
|
||||
{{- end }}
|
||||
- name: KAFKA_PRODUCER_BROKERS
|
||||
value: {{ tpl (include "helm-toolkit.utils.joinListWithComma" .Values.storage.kafka.brokers) . }}
|
||||
value: {{ include "helm-toolkit.utils.joinListWithComma" .Values.storage.kafka.brokers }}
|
||||
- name: KAFKA_PRODUCER_TOPIC
|
||||
value: {{ .Values.storage.kafka.topic }}
|
||||
- name: KAFKA_PRODUCER_AUTHENTICATION
|
||||
value: {{ .Values.storage.kafka.authentication }}
|
||||
{{ else }}
|
||||
- name: SPAN_STORAGE_TYPE
|
||||
value: {{ .Values.storage.type }}
|
||||
{{- include "storage.env" . | nindent 10 }}
|
||||
{{- if eq .Values.storage.type "cassandra" }}
|
||||
- name: CASSANDRA_SERVERS
|
||||
value: {{ template "cassandra.host" . }}
|
||||
- name: CASSANDRA_PORT
|
||||
value: {{ .Values.storage.cassandra.port | quote }}
|
||||
{{ if .Values.storage.cassandra.tls.enabled }}
|
||||
- name: CASSANDRA_TLS
|
||||
value: "true"
|
||||
- name: CASSANDRA_TLS_SERVER_NAME
|
||||
valueFrom:
|
||||
secretKeyRef:
|
||||
name: {{ .Values.storage.cassandra.tls.secretName }}
|
||||
key: commonName
|
||||
- name: CASSANDRA_TLS_KEY
|
||||
value: "/cassandra-tls/client-key.pem"
|
||||
- name: CASSANDRA_TLS_CERT
|
||||
value: "/cassandra-tls/client-cert.pem"
|
||||
- name: CASSANDRA_TLS_CA
|
||||
value: "/cassandra-tls/ca-cert.pem"
|
||||
{{- end }}
|
||||
{{- if .Values.storage.cassandra.keyspace }}
|
||||
- name: CASSANDRA_KEYSPACE
|
||||
value: {{ .Values.storage.cassandra.keyspace }}
|
||||
{{- end }}
|
||||
- name: CASSANDRA_USERNAME
|
||||
value: {{ .Values.storage.cassandra.user }}
|
||||
- name: CASSANDRA_PASSWORD
|
||||
valueFrom:
|
||||
secretKeyRef:
|
||||
name: {{ if .Values.storage.cassandra.existingSecret }}{{ .Values.storage.cassandra.existingSecret }}{{- else }}{{ include "jaeger.fullname" . }}-cassandra{{- end }}
|
||||
key: password
|
||||
{{- end }}
|
||||
{{- if eq .Values.storage.type "elasticsearch" }}
|
||||
{{- if .Values.storage.elasticsearch.usePassword }}
|
||||
- name: ES_PASSWORD
|
||||
valueFrom:
|
||||
secretKeyRef:
|
||||
name: {{ if .Values.storage.elasticsearch.existingSecret }}{{ .Values.storage.elasticsearch.existingSecret }}{{- else }}{{ include "jaeger.fullname" . }}-elasticsearch{{- end }}
|
||||
key: password
|
||||
{{- end }}
|
||||
- name: ES_SERVER_URLS
|
||||
value: {{ template "elasticsearch.client.url" . }}
|
||||
- name: ES_USERNAME
|
||||
value: {{ .Values.storage.elasticsearch.user }}
|
||||
{{- if .Values.storage.elasticsearch.indexPrefix }}
|
||||
- name: ES_INDEX_PREFIX
|
||||
value: {{ .Values.storage.elasticsearch.indexPrefix }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- if .Values.collector.samplingConfig}}
|
||||
- name: SAMPLING_STRATEGIES_FILE
|
||||
value: /etc/conf/strategies.json
|
||||
{{- end }}
|
||||
{{- with .Values.collector.envFrom }}
|
||||
envFrom: {{- toYaml . | nindent 10 }}
|
||||
{{- end }}
|
||||
ports:
|
||||
- containerPort: {{ .Values.collector.service.grpc.port }}
|
||||
- containerPort: {{ .Values.collector.service.grpcPort }}
|
||||
name: grpc
|
||||
protocol: TCP
|
||||
- containerPort: {{ .Values.collector.service.http.port }}
|
||||
- containerPort: {{ .Values.collector.service.tchannelPort }}
|
||||
name: tchannel
|
||||
protocol: TCP
|
||||
- containerPort: {{ .Values.collector.service.httpPort }}
|
||||
name: http
|
||||
protocol: TCP
|
||||
- containerPort: 14269
|
||||
name: admin
|
||||
protocol: TCP
|
||||
{{- if .Values.collector.service.zipkin }}
|
||||
- containerPort: {{ .Values.collector.service.zipkin.port }}
|
||||
{{- if .Values.collector.service.zipkinPort }}
|
||||
- containerPort: {{ .Values.collector.service.zipkinPort }}
|
||||
name: zipkin
|
||||
protocol: TCP
|
||||
{{- end }}
|
||||
{{- if or .Values.collector.service.otlp.grpc .Values.collector.service.otlp.http }}
|
||||
- containerPort: {{ default 4317 .Values.collector.service.otlp.grpc.port }}
|
||||
name: {{ .Values.collector.service.otlp.grpc.name }}
|
||||
protocol: TCP
|
||||
- containerPort: {{ default 4318 .Values.collector.service.otlp.http.port }}
|
||||
name: {{ .Values.collector.service.otlp.http.name }}
|
||||
protocol: TCP
|
||||
{{- end }}
|
||||
readinessProbe:
|
||||
httpGet:
|
||||
path: /
|
||||
|
|
@ -148,7 +143,7 @@ spec:
|
|||
path: /
|
||||
port: admin
|
||||
resources:
|
||||
{{- toYaml .Values.collector.resources | nindent 10 }}
|
||||
{{ toYaml .Values.collector.resources | indent 10 }}
|
||||
volumeMounts:
|
||||
{{- range .Values.collector.extraConfigmapMounts }}
|
||||
- name: {{ .name }}
|
||||
|
|
@ -176,12 +171,6 @@ spec:
|
|||
subPath: "client-key.pem"
|
||||
readOnly: true
|
||||
{{- end }}
|
||||
{{- if .Values.storage.elasticsearch.tls.enabled }}
|
||||
- name: {{ .Values.storage.elasticsearch.tls.secretName }}
|
||||
mountPath: {{ .Values.storage.elasticsearch.tls.mountPath }}
|
||||
subPath: {{ .Values.storage.elasticsearch.tls.subPath }}
|
||||
readOnly: true
|
||||
{{- end }}
|
||||
{{- if .Values.collector.samplingConfig}}
|
||||
- name: strategies
|
||||
mountPath: /etc/conf/
|
||||
|
|
@ -204,16 +193,6 @@ spec:
|
|||
configMap:
|
||||
name: {{ include "jaeger.fullname" . }}-sampling-strategies
|
||||
{{- end }}
|
||||
{{- if .Values.storage.cassandra.tls.enabled }}
|
||||
- name: {{ .Values.storage.cassandra.tls.secretName }}
|
||||
secret:
|
||||
secretName: {{ .Values.storage.cassandra.tls.secretName }}
|
||||
{{- end }}
|
||||
{{- if .Values.storage.elasticsearch.tls.enabled }}
|
||||
- name: {{ .Values.storage.elasticsearch.tls.secretName }}
|
||||
secret:
|
||||
secretName: {{ .Values.storage.elasticsearch.tls.secretName }}
|
||||
{{- end }}
|
||||
{{- with .Values.collector.nodeSelector }}
|
||||
nodeSelector:
|
||||
{{- toYaml . | nindent 8 }}
|
||||
|
|
@ -222,10 +201,6 @@ spec:
|
|||
affinity:
|
||||
{{- toYaml . | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- with .Values.collector.topologySpreadConstraints }}
|
||||
topologySpreadConstraints:
|
||||
{{- toYaml . | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- with .Values.collector.tolerations }}
|
||||
tolerations:
|
||||
{{- toYaml . | nindent 8 }}
|
||||
|
|
|
|||
|
|
@ -1,5 +1,5 @@
|
|||
{{- if and .Values.collector.enabled .Values.collector.autoscaling.enabled }}
|
||||
apiVersion: {{ include "common.capabilities.hpa.apiVersion" ( dict "context" $ ) }}
|
||||
{{- if .Values.collector.autoscaling.enabled }}
|
||||
apiVersion: autoscaling/v2beta1
|
||||
kind: HorizontalPodAutoscaler
|
||||
metadata:
|
||||
name: {{ template "jaeger.collector.name" . }}
|
||||
|
|
@ -8,36 +8,20 @@ metadata:
|
|||
app.kubernetes.io/component: collector
|
||||
spec:
|
||||
scaleTargetRef:
|
||||
apiVersion: {{ include "common.capabilities.deployment.apiVersion" . }}
|
||||
apiVersion: apps/v1
|
||||
kind: Deployment
|
||||
name: {{ template "jaeger.collector.name" . }}
|
||||
minReplicas: {{ .Values.collector.autoscaling.minReplicas }}
|
||||
maxReplicas: {{ .Values.collector.autoscaling.maxReplicas }}
|
||||
metrics:
|
||||
- type: Resource
|
||||
resource:
|
||||
name: cpu
|
||||
targetAverageUtilization: {{ .Values.collector.autoscaling.targetCPUUtilizationPercentage | default 80 }}
|
||||
{{- if .Values.collector.autoscaling.targetMemoryUtilizationPercentage }}
|
||||
- type: Resource
|
||||
resource:
|
||||
name: memory
|
||||
{{- if eq "autoscaling/v2" (include "common.capabilities.hpa.apiVersion" ( dict "context" $ )) }}
|
||||
target:
|
||||
averageUtilization: {{ .Values.collector.autoscaling.targetMemoryUtilizationPercentage }}
|
||||
type: Utilization
|
||||
{{- else }}
|
||||
targetAverageUtilization: {{ .Values.collector.autoscaling.targetMemoryUtilizationPercentage }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
- type: Resource
|
||||
resource:
|
||||
name: cpu
|
||||
{{- if eq "autoscaling/v2" (include "common.capabilities.hpa.apiVersion" ( dict "context" $ )) }}
|
||||
target:
|
||||
averageUtilization: {{ .Values.collector.autoscaling.targetCPUUtilizationPercentage | default 80 }}
|
||||
type: Utilization
|
||||
{{- else }}
|
||||
targetAverageUtilization: {{ .Values.collector.autoscaling.targetCPUUtilizationPercentage | default 80 }}
|
||||
{{- end }}
|
||||
{{- with .Values.collector.autoscaling.behavior }}
|
||||
behavior:
|
||||
{{- toYaml . | nindent 4 }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
|
|
|||
|
|
@ -1,38 +0,0 @@
|
|||
{{- if .Values.collector.ingress.enabled -}}
|
||||
{{- $ingressSupportsIngressClassName := eq (include "common.ingress.supportsIngressClassname" .) "true" }}
|
||||
{{- $defaultServicePort := .Values.collector.service.http.port -}}
|
||||
{{- $basePath := .Values.collector.basePath -}}
|
||||
apiVersion: {{ include "common.capabilities.ingress.apiVersion" $ }}
|
||||
kind: Ingress
|
||||
metadata:
|
||||
name: {{ template "jaeger.collector.name" . }}
|
||||
labels:
|
||||
{{- include "jaeger.labels" . | nindent 4 }}
|
||||
{{- if .Values.collector.ingress.labels }}
|
||||
{{- toYaml .Values.collector.ingress.labels | nindent 4 }}
|
||||
{{- end }}
|
||||
app.kubernetes.io/component: collector
|
||||
{{- if .Values.collector.ingress.annotations }}
|
||||
annotations:
|
||||
{{- toYaml .Values.collector.ingress.annotations | nindent 4 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
{{- if and $ingressSupportsIngressClassName .Values.collector.ingress.ingressClassName }}
|
||||
ingressClassName: {{ .Values.collector.ingress.ingressClassName }}
|
||||
{{- end }}
|
||||
rules:
|
||||
{{- range .Values.collector.ingress.hosts }}
|
||||
- host: {{ include "jaeger.collector.ingressHost" . | quote }}
|
||||
http:
|
||||
paths:
|
||||
- path: {{ $basePath }}
|
||||
pathType: {{ default "ImplementationSpecific" $.Values.collector.ingress.pathType }}
|
||||
{{- $servicePortString := (include "jaeger.collector.ingressServicePort" (dict "defaultServicePort" $defaultServicePort "context" .)) }}
|
||||
{{- $servicePort := default $servicePortString ($servicePortString | float64) }}
|
||||
backend: {{- include "common.ingress.backend" (dict "serviceName" (include "jaeger.collector.name" $) "servicePort" $servicePort "context" $) | nindent 14 }}
|
||||
{{- end -}}
|
||||
{{- if .Values.collector.ingress.tls }}
|
||||
tls:
|
||||
{{- toYaml .Values.collector.ingress.tls | nindent 4 }}
|
||||
{{- end -}}
|
||||
{{- end -}}
|
||||
|
|
@ -1,5 +0,0 @@
|
|||
{{- if and .Values.networkPolicy.enabled .Values.collector.networkPolicy.enabled .Values.collector.networkPolicy.egressRules }}
|
||||
{{- $extraVals := dict "Name" (include "jaeger.collector.name" .) "Component" "collector" "ComponentValues" .Values.collector -}}
|
||||
{{- $npVals := merge $extraVals . -}}
|
||||
{{ include "jaeger.egress.networkPolicy" $npVals }}
|
||||
{{- end }}
|
||||
|
|
@ -1,5 +0,0 @@
|
|||
{{- if and .Values.networkPolicy.enabled .Values.collector.networkPolicy.enabled .Values.collector.networkPolicy.ingressRules -}}
|
||||
{{- $extraVals := dict "Name" (include "jaeger.collector.name" .) "Component" "collector" "ComponentValues" .Values.collector -}}
|
||||
{{- $npVals := merge $extraVals . -}}
|
||||
{{ include "jaeger.ingress.networkPolicy" $npVals }}
|
||||
{{- end -}}
|
||||
|
|
@ -6,9 +6,4 @@ metadata:
|
|||
labels:
|
||||
{{- include "jaeger.labels" . | nindent 4 }}
|
||||
app.kubernetes.io/component: collector
|
||||
{{- with .Values.collector.serviceAccount.annotations }}
|
||||
annotations:
|
||||
{{- toYaml . | nindent 4 }}
|
||||
{{- end }}
|
||||
automountServiceAccountToken: {{ .Values.collector.serviceAccount.automountServiceAccountToken }}
|
||||
{{- end -}}
|
||||
|
|
|
|||
|
|
@ -1,44 +0,0 @@
|
|||
{{- if and (.Values.collector.enabled) (.Values.collector.serviceMonitor.enabled)}}
|
||||
apiVersion: monitoring.coreos.com/v1
|
||||
kind: ServiceMonitor
|
||||
metadata:
|
||||
name: {{ template "jaeger.collector.name" . }}
|
||||
{{- if .Values.collector.serviceMonitor.namespace }}
|
||||
namespace: {{ .Values.collector.serviceMonitor.namespace }}
|
||||
{{- end }}
|
||||
labels:
|
||||
{{- include "jaeger.labels" . | nindent 4 }}
|
||||
app.kubernetes.io/component: collector
|
||||
{{- if .Values.collector.serviceMonitor.additionalLabels }}
|
||||
{{- toYaml .Values.collector.serviceMonitor.additionalLabels | nindent 4 }}
|
||||
{{- end }}
|
||||
{{- if .Values.collector.serviceMonitor.annotations }}
|
||||
annotations:
|
||||
{{- toYaml .Values.collector.serviceMonitor.annotations | nindent 4 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
endpoints:
|
||||
- port: admin
|
||||
path: /metrics
|
||||
{{- if .Values.collector.serviceMonitor.interval }}
|
||||
interval: {{ .Values.collector.serviceMonitor.interval }}
|
||||
{{- end }}
|
||||
{{- if .Values.collector.serviceMonitor.scrapeTimeout }}
|
||||
scrapeTimeout: {{ .Values.collector.serviceMonitor.scrapeTimeout }}
|
||||
{{- end }}
|
||||
{{- if .Values.collector.serviceMonitor.relabelings }}
|
||||
relabelings:
|
||||
{{- toYaml .Values.collector.serviceMonitor.relabelings | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- if .Values.collector.serviceMonitor.metricRelabelings }}
|
||||
metricRelabelings:
|
||||
{{- toYaml .Values.collector.serviceMonitor.metricRelabelings | nindent 8 }}
|
||||
{{- end }}
|
||||
namespaceSelector:
|
||||
matchNames:
|
||||
- {{ .Release.Namespace }}
|
||||
selector:
|
||||
matchLabels:
|
||||
app.kubernetes.io/component: collector
|
||||
app.kubernetes.io/instance: {{ .Release.Name }}
|
||||
{{- end }}
|
||||
|
|
@ -8,70 +8,31 @@ metadata:
|
|||
app.kubernetes.io/component: collector
|
||||
{{- if .Values.collector.service.annotations }}
|
||||
annotations:
|
||||
{{- toYaml .Values.collector.service.annotations | nindent 4 }}
|
||||
{{ toYaml .Values.collector.service.annotations | indent 4 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
ports:
|
||||
- name: grpc
|
||||
port: {{ .Values.collector.service.grpc.port }}
|
||||
{{- if and (eq .Values.collector.service.type "NodePort") (.Values.collector.service.grpc.nodePort) }}
|
||||
nodePort: {{ .Values.collector.service.grpc.nodePort }}
|
||||
{{- end }}
|
||||
port: {{ .Values.collector.service.grpcPort }}
|
||||
protocol: TCP
|
||||
targetPort: grpc
|
||||
{{- if semverCompare ">=1.20" .Capabilities.KubeVersion.Version }}
|
||||
appProtocol: grpc
|
||||
{{- end }}
|
||||
- name: tchannel
|
||||
port: {{ .Values.collector.service.tchannelPort }}
|
||||
protocol: TCP
|
||||
targetPort: tchannel
|
||||
- name: http
|
||||
port: {{ .Values.collector.service.http.port }}
|
||||
{{- if and (eq .Values.collector.service.type "NodePort") (.Values.collector.service.http.nodePort) }}
|
||||
nodePort: {{ .Values.collector.service.http.nodePort }}
|
||||
{{- end }}
|
||||
port: {{ .Values.collector.service.httpPort }}
|
||||
protocol: TCP
|
||||
targetPort: http
|
||||
{{- if semverCompare ">=1.20" .Capabilities.KubeVersion.Version }}
|
||||
appProtocol: http
|
||||
{{- end }}
|
||||
{{- if .Values.collector.service.zipkin }}
|
||||
{{- if .Values.collector.service.zipkinPort }}
|
||||
- name: zipkin
|
||||
port: {{ .Values.collector.service.zipkin.port }}
|
||||
{{- if and (eq .Values.collector.service.type "NodePort") (.Values.collector.service.zipkin.nodePort) }}
|
||||
nodePort: {{ .Values.collector.service.zipkin.nodePort }}
|
||||
{{- end }}
|
||||
port: {{ .Values.collector.service.zipkinPort }}
|
||||
protocol: TCP
|
||||
targetPort: zipkin
|
||||
{{- if semverCompare ">=1.20" .Capabilities.KubeVersion.Version }}
|
||||
appProtocol: http
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- if or .Values.collector.service.otlp.grpc .Values.collector.service.otlp.http }}
|
||||
- name: {{ .Values.collector.service.otlp.grpc.name }}
|
||||
port: {{ default 4317 .Values.collector.service.otlp.grpc.port }}
|
||||
{{- if and (eq .Values.collector.service.type "NodePort") (.Values.collector.service.otlp.grpc.nodePort) }}
|
||||
nodePort: {{ .Values.collector.service.otlp.grpc.nodePort }}
|
||||
{{- end }}
|
||||
protocol: TCP
|
||||
targetPort: {{ .Values.collector.service.otlp.grpc.name }}
|
||||
- name: {{ .Values.collector.service.otlp.http.name }}
|
||||
port: {{ default 4318 .Values.collector.service.otlp.http.port }}
|
||||
{{- if and (eq .Values.collector.service.type "NodePort") (.Values.collector.service.otlp.http.nodePort) }}
|
||||
nodePort: {{ .Values.collector.service.otlp.http.nodePort }}
|
||||
{{- end }}
|
||||
protocol: TCP
|
||||
targetPort: {{ .Values.collector.service.otlp.http.name }}
|
||||
{{- end }}
|
||||
- name: {{ .Values.collector.service.admin.name }}
|
||||
port: 14269
|
||||
targetPort: {{ .Values.collector.service.admin.targetPort }}
|
||||
selector:
|
||||
{{- include "jaeger.selectorLabels" . | nindent 4 }}
|
||||
app.kubernetes.io/component: collector
|
||||
{{- if and (eq .Values.collector.service.type "ClusterIP") .Values.collector.service.clusterIP }}
|
||||
clusterIP: {{ .Values.collector.service.clusterIP }}
|
||||
{{- end }}
|
||||
type: {{ .Values.collector.service.type }}
|
||||
{{- if and (eq .Values.collector.service.type "LoadBalancer") .Values.collector.service.loadBalancerIP }}
|
||||
loadBalancerIP: {{ .Values.collector.service.loadBalancerIP }}
|
||||
{{- end -}}
|
||||
{{- template "loadBalancerSourceRanges" .Values.collector }}
|
||||
{{- end -}}
|
||||
|
|
|
|||
|
|
@ -5,11 +5,6 @@ metadata:
|
|||
name: {{ include "jaeger.fullname" . }}-elasticsearch
|
||||
labels:
|
||||
{{- include "jaeger.labels" . | nindent 4 }}
|
||||
annotations:
|
||||
"helm.sh/hook": pre-install,pre-upgrade
|
||||
"helm.sh/hook-weight": "-1"
|
||||
"helm.sh/hook-delete-policy": before-hook-creation
|
||||
"helm.sh/resource-policy": keep
|
||||
type: Opaque
|
||||
data:
|
||||
password: {{ .Values.storage.elasticsearch.password | b64enc | quote }}
|
||||
|
|
|
|||
|
|
@ -1,109 +0,0 @@
|
|||
{{- if .Values.esIndexCleaner.enabled -}}
|
||||
apiVersion: {{ include "common.capabilities.cronjob.apiVersion" $ }}
|
||||
kind: CronJob
|
||||
metadata:
|
||||
name: {{ include "jaeger.fullname" . }}-es-index-cleaner
|
||||
labels:
|
||||
{{- include "jaeger.labels" . | nindent 4 }}
|
||||
app.kubernetes.io/component: es-index-cleaner
|
||||
{{- if .Values.esIndexCleaner.annotations }}
|
||||
annotations:
|
||||
{{- toYaml .Values.esIndexCleaner.annotations | nindent 4 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
concurrencyPolicy: {{ .Values.esIndexCleaner.concurrencyPolicy }}
|
||||
schedule: {{ .Values.esIndexCleaner.schedule | quote }}
|
||||
successfulJobsHistoryLimit: {{ .Values.esIndexCleaner.successfulJobsHistoryLimit }}
|
||||
failedJobsHistoryLimit: {{ .Values.esIndexCleaner.failedJobsHistoryLimit }}
|
||||
suspend: false
|
||||
jobTemplate:
|
||||
spec:
|
||||
{{- if .Values.esIndexCleaner.activeDeadlineSeconds }}
|
||||
activeDeadlineSeconds: {{ .Values.esIndexCleaner.activeDeadlineSeconds }}
|
||||
{{- end }}
|
||||
{{- if .Values.esIndexCleaner.ttlSecondsAfterFinished }}
|
||||
ttlSecondsAfterFinished: {{ .Values.esIndexCleaner.ttlSecondsAfterFinished }}
|
||||
{{- end }}
|
||||
template:
|
||||
metadata:
|
||||
{{- if .Values.esIndexCleaner.podAnnotations }}
|
||||
annotations:
|
||||
{{- toYaml .Values.esIndexCleaner.podAnnotations | nindent 12 }}
|
||||
{{- end }}
|
||||
labels:
|
||||
{{- include "jaeger.selectorLabels" . | nindent 12 }}
|
||||
app.kubernetes.io/component: es-index-cleaner
|
||||
{{- if .Values.esIndexCleaner.podLabels }}
|
||||
{{- toYaml .Values.esIndexCleaner.podLabels | nindent 12 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
serviceAccountName: {{ template "jaeger.esIndexCleaner.serviceAccountName" . }}
|
||||
{{- include "esIndexCleaner.imagePullSecrets" . | nindent 10 }}
|
||||
securityContext:
|
||||
{{- toYaml .Values.esIndexCleaner.podSecurityContext | nindent 12 }}
|
||||
containers:
|
||||
- name: {{ include "jaeger.fullname" . }}-es-index-cleaner
|
||||
securityContext:
|
||||
{{- toYaml .Values.esIndexCleaner.securityContext | nindent 14 }}
|
||||
image: {{ include "esIndexCleaner.image" . }}
|
||||
imagePullPolicy: {{ .Values.esIndexCleaner.image.pullPolicy }}
|
||||
args:
|
||||
- {{ .Values.esIndexCleaner.numberOfDays | quote }}
|
||||
- {{ include "elasticsearch.client.url" . }}
|
||||
{{ include "extra.cmdArgs" ( dict "cmdlineParams" .Values.esIndexCleaner.cmdlineParams ) | nindent 14 }}
|
||||
env:
|
||||
{{- if .Values.esIndexCleaner.extraEnv }}
|
||||
{{- toYaml .Values.esIndexCleaner.extraEnv | nindent 14 }}
|
||||
{{- end }}
|
||||
{{ include "elasticsearch.env" . | nindent 14 }}
|
||||
resources:
|
||||
{{- toYaml .Values.esIndexCleaner.resources | nindent 14 }}
|
||||
volumeMounts:
|
||||
{{- range .Values.esIndexCleaner.extraConfigmapMounts }}
|
||||
- name: {{ .name }}
|
||||
mountPath: {{ .mountPath }}
|
||||
subPath: {{ .subPath }}
|
||||
readOnly: {{ .readOnly }}
|
||||
{{- end }}
|
||||
{{- range .Values.esIndexCleaner.extraSecretMounts }}
|
||||
- name: {{ .name }}
|
||||
mountPath: {{ .mountPath }}
|
||||
subPath: {{ .subPath }}
|
||||
readOnly: {{ .readOnly }}
|
||||
{{- end }}
|
||||
{{- if .Values.storage.elasticsearch.tls.enabled }}
|
||||
- name: {{ .Values.storage.elasticsearch.tls.secretName }}
|
||||
mountPath: {{ .Values.storage.elasticsearch.tls.mountPath }}
|
||||
subPath: {{ .Values.storage.elasticsearch.tls.subPath }}
|
||||
readOnly: true
|
||||
{{- end }}
|
||||
restartPolicy: OnFailure
|
||||
{{- with .Values.esIndexCleaner.nodeSelector }}
|
||||
nodeSelector:
|
||||
{{- toYaml . | nindent 12 }}
|
||||
{{- end }}
|
||||
{{- with .Values.esIndexCleaner.affinity }}
|
||||
affinity:
|
||||
{{- toYaml . | nindent 12 }}
|
||||
{{- end }}
|
||||
{{- with .Values.esIndexCleaner.tolerations }}
|
||||
tolerations:
|
||||
{{- toYaml . | nindent 12 }}
|
||||
{{- end }}
|
||||
volumes:
|
||||
{{- range .Values.esIndexCleaner.extraConfigmapMounts }}
|
||||
- name: {{ .name }}
|
||||
configMap:
|
||||
name: {{ .configMap }}
|
||||
{{- end }}
|
||||
{{- range .Values.esIndexCleaner.extraSecretMounts }}
|
||||
- name: {{ .name }}
|
||||
secret:
|
||||
secretName: {{ .secretName }}
|
||||
{{- end }}
|
||||
{{- if .Values.storage.elasticsearch.tls.enabled }}
|
||||
- name: {{ .Values.storage.elasticsearch.tls.secretName }}
|
||||
secret:
|
||||
secretName: {{ .Values.storage.elasticsearch.tls.secretName }}
|
||||
{{- end }}
|
||||
{{- end -}}
|
||||
|
|
@ -1,14 +0,0 @@
|
|||
{{- if and .Values.esIndexCleaner.enabled .Values.esIndexCleaner.serviceAccount.create -}}
|
||||
apiVersion: v1
|
||||
kind: ServiceAccount
|
||||
metadata:
|
||||
name: {{ template "jaeger.esIndexCleaner.serviceAccountName" . }}
|
||||
labels:
|
||||
{{- include "jaeger.labels" . | nindent 4 }}
|
||||
app.kubernetes.io/component: es-index-cleaner
|
||||
{{- with .Values.esIndexCleaner.serviceAccount.annotations }}
|
||||
annotations:
|
||||
{{- toYaml . | nindent 4 }}
|
||||
{{- end }}
|
||||
automountServiceAccountToken: {{ .Values.esIndexCleaner.serviceAccount.automountServiceAccountToken }}
|
||||
{{- end -}}
|
||||
|
|
@ -1,110 +0,0 @@
|
|||
{{- if .Values.esLookback.enabled -}}
|
||||
apiVersion: {{ include "common.capabilities.cronjob.apiVersion" $ }}
|
||||
kind: CronJob
|
||||
metadata:
|
||||
name: {{ include "jaeger.fullname" . }}-es-lookback
|
||||
labels:
|
||||
{{- include "jaeger.labels" . | nindent 4 }}
|
||||
app.kubernetes.io/component: es-lookback
|
||||
{{- if .Values.esLookback.annotations }}
|
||||
annotations:
|
||||
{{- toYaml .Values.esLookback.annotations | nindent 4 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
concurrencyPolicy: {{ .Values.esLookback.concurrencyPolicy }}
|
||||
schedule: {{ .Values.esLookback.schedule | quote }}
|
||||
successfulJobsHistoryLimit: {{ .Values.esLookback.successfulJobsHistoryLimit }}
|
||||
failedJobsHistoryLimit: {{ .Values.esLookback.failedJobsHistoryLimit }}
|
||||
suspend: false
|
||||
jobTemplate:
|
||||
spec:
|
||||
{{- if .Values.esLookback.activeDeadlineSeconds }}
|
||||
activeDeadlineSeconds: {{ .Values.esLookback.activeDeadlineSeconds }}
|
||||
{{- end }}
|
||||
{{- if .Values.esLookback.ttlSecondsAfterFinished }}
|
||||
ttlSecondsAfterFinished: {{ .Values.esLookback.ttlSecondsAfterFinished }}
|
||||
{{- end }}
|
||||
template:
|
||||
metadata:
|
||||
{{- if .Values.esLookback.podAnnotations }}
|
||||
annotations:
|
||||
{{- toYaml .Values.esLookback.podAnnotations | nindent 12 }}
|
||||
{{- end }}
|
||||
labels:
|
||||
{{- include "jaeger.selectorLabels" . | nindent 12 }}
|
||||
app.kubernetes.io/component: es-lookback
|
||||
{{- if .Values.esLookback.podLabels }}
|
||||
{{- toYaml .Values.esLookback.podLabels | nindent 12 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
serviceAccountName: {{ template "jaeger.esLookback.serviceAccountName" . }}
|
||||
{{- include "esLookback.imagePullSecrets" . | nindent 10 }}
|
||||
securityContext:
|
||||
{{- toYaml .Values.esLookback.podSecurityContext | nindent 12 }}
|
||||
restartPolicy: OnFailure
|
||||
{{- with .Values.esLookback.nodeSelector }}
|
||||
nodeSelector:
|
||||
{{- toYaml . | nindent 12 }}
|
||||
{{- end }}
|
||||
{{- with .Values.esLookback.affinity }}
|
||||
affinity:
|
||||
{{- toYaml . | nindent 12 }}
|
||||
{{- end }}
|
||||
{{- with .Values.esLookback.tolerations }}
|
||||
tolerations:
|
||||
{{- toYaml . | nindent 12 }}
|
||||
{{- end }}
|
||||
|
||||
containers:
|
||||
- name: {{ include "jaeger.fullname" . }}-es-lookback
|
||||
securityContext:
|
||||
{{- toYaml .Values.esLookback.securityContext | nindent 14 }}
|
||||
image: {{ include "esLookback.image" . }}
|
||||
imagePullPolicy: {{ .Values.esLookback.image.pullPolicy }}
|
||||
args:
|
||||
- lookback
|
||||
- {{ include "elasticsearch.client.url" . }}
|
||||
{{ include "extra.cmdArgs" ( dict "cmdlineParams" .Values.esLookback.cmdlineParams ) | nindent 14 }}
|
||||
env:
|
||||
{{ include "elasticsearch.env" . | nindent 14 }}
|
||||
{{- if .Values.esLookback.extraEnv }}
|
||||
{{- toYaml .Values.esLookback.extraEnv | nindent 14 }}
|
||||
{{- end }}
|
||||
resources:
|
||||
{{- toYaml .Values.esLookback.resources | nindent 14 }}
|
||||
volumeMounts:
|
||||
{{- range .Values.esLookback.extraConfigmapMounts }}
|
||||
- name: {{ .name }}
|
||||
mountPath: {{ .mountPath }}
|
||||
subPath: {{ .subPath }}
|
||||
readOnly: {{ .readOnly }}
|
||||
{{- end }}
|
||||
{{- range .Values.esLookback.extraSecretMounts }}
|
||||
- name: {{ .name }}
|
||||
mountPath: {{ .mountPath }}
|
||||
subPath: {{ .subPath }}
|
||||
readOnly: {{ .readOnly }}
|
||||
{{- end }}
|
||||
{{- if .Values.storage.elasticsearch.tls.enabled }}
|
||||
- name: {{ .Values.storage.elasticsearch.tls.secretName }}
|
||||
mountPath: {{ .Values.storage.elasticsearch.tls.mountPath }}
|
||||
subPath: {{ .Values.storage.elasticsearch.tls.subPath }}
|
||||
readOnly: true
|
||||
{{- end }}
|
||||
volumes:
|
||||
{{- range .Values.esLookback.extraConfigmapMounts }}
|
||||
- name: {{ .name }}
|
||||
configMap:
|
||||
name: {{ .configMap }}
|
||||
{{- end }}
|
||||
{{- range .Values.esLookback.extraSecretMounts }}
|
||||
- name: {{ .name }}
|
||||
secret:
|
||||
secretName: {{ .secretName }}
|
||||
{{- end }}
|
||||
{{- if .Values.storage.elasticsearch.tls.enabled }}
|
||||
- name: {{ .Values.storage.elasticsearch.tls.secretName }}
|
||||
secret:
|
||||
secretName: {{ .Values.storage.elasticsearch.tls.secretName }}
|
||||
{{- end }}
|
||||
{{- end -}}
|
||||
|
|
@ -1,14 +0,0 @@
|
|||
{{- if and .Values.esLookback.enabled .Values.esLookback.serviceAccount.create -}}
|
||||
apiVersion: v1
|
||||
kind: ServiceAccount
|
||||
metadata:
|
||||
name: {{ template "jaeger.esLookback.serviceAccountName" . }}
|
||||
labels:
|
||||
{{- include "jaeger.labels" . | nindent 4 }}
|
||||
app.kubernetes.io/component: es-lookback
|
||||
{{- with .Values.esLookback.serviceAccount.annotations }}
|
||||
annotations:
|
||||
{{- toYaml . | nindent 4 }}
|
||||
{{- end }}
|
||||
automountServiceAccountToken: {{ .Values.esLookback.serviceAccount.automountServiceAccountToken }}
|
||||
{{- end -}}
|
||||
|
|
@ -1,110 +0,0 @@
|
|||
{{- if .Values.esRollover.enabled -}}
|
||||
apiVersion: {{ include "common.capabilities.cronjob.apiVersion" $ }}
|
||||
kind: CronJob
|
||||
metadata:
|
||||
name: {{ include "jaeger.fullname" . }}-es-rollover
|
||||
labels:
|
||||
{{- include "jaeger.labels" . | nindent 4 }}
|
||||
app.kubernetes.io/component: es-rollover
|
||||
{{- if .Values.esRollover.annotations }}
|
||||
annotations:
|
||||
{{- toYaml .Values.esRollover.annotations | nindent 4 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
concurrencyPolicy: {{ .Values.esRollover.concurrencyPolicy }}
|
||||
schedule: {{ .Values.esRollover.schedule | quote }}
|
||||
successfulJobsHistoryLimit: {{ .Values.esRollover.successfulJobsHistoryLimit }}
|
||||
failedJobsHistoryLimit: {{ .Values.esRollover.failedJobsHistoryLimit }}
|
||||
suspend: false
|
||||
jobTemplate:
|
||||
spec:
|
||||
{{- if .Values.esRollover.activeDeadlineSeconds }}
|
||||
activeDeadlineSeconds: {{ .Values.esRollover.activeDeadlineSeconds }}
|
||||
{{- end }}
|
||||
{{- if .Values.esRollover.ttlSecondsAfterFinished }}
|
||||
ttlSecondsAfterFinished: {{ .Values.esRollover.ttlSecondsAfterFinished }}
|
||||
{{- end }}
|
||||
template:
|
||||
metadata:
|
||||
{{- if .Values.esRollover.podAnnotations }}
|
||||
annotations:
|
||||
{{- toYaml .Values.esRollover.podAnnotations | nindent 12 }}
|
||||
{{- end }}
|
||||
labels:
|
||||
{{- include "jaeger.selectorLabels" . | nindent 12 }}
|
||||
app.kubernetes.io/component: es-rollover
|
||||
{{- if .Values.esRollover.podLabels }}
|
||||
{{- toYaml .Values.esRollover.podLabels | nindent 12 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
serviceAccountName: {{ template "jaeger.esRollover.serviceAccountName" . }}
|
||||
{{- include "esRollover.imagePullSecrets" . | nindent 10 }}
|
||||
securityContext:
|
||||
{{- toYaml .Values.esRollover.podSecurityContext | nindent 12 }}
|
||||
restartPolicy: OnFailure
|
||||
{{- with .Values.esRollover.nodeSelector }}
|
||||
nodeSelector:
|
||||
{{- toYaml . | nindent 12 }}
|
||||
{{- end }}
|
||||
{{- with .Values.esRollover.affinity }}
|
||||
affinity:
|
||||
{{- toYaml . | nindent 12 }}
|
||||
{{- end }}
|
||||
{{- with .Values.esRollover.tolerations }}
|
||||
tolerations:
|
||||
{{- toYaml . | nindent 12 }}
|
||||
{{- end }}
|
||||
|
||||
containers:
|
||||
- name: {{ include "jaeger.fullname" . }}-es-rollover
|
||||
securityContext:
|
||||
{{- toYaml .Values.esRollover.securityContext | nindent 14 }}
|
||||
image: {{ include "esRollover.image" . }}
|
||||
imagePullPolicy: {{ .Values.esRollover.image.pullPolicy }}
|
||||
args:
|
||||
- rollover
|
||||
- {{ include "elasticsearch.client.url" . }}
|
||||
{{ include "extra.cmdArgs" ( dict "cmdlineParams" .Values.esRollover.cmdlineParams ) | nindent 14 }}
|
||||
env:
|
||||
{{ include "elasticsearch.env" . | nindent 14 }}
|
||||
{{- if .Values.esRollover.extraEnv }}
|
||||
{{- toYaml .Values.esRollover.extraEnv | nindent 14 }}
|
||||
{{- end }}
|
||||
resources:
|
||||
{{- toYaml .Values.esRollover.resources | nindent 14 }}
|
||||
volumeMounts:
|
||||
{{- range .Values.esRollover.extraConfigmapMounts }}
|
||||
- name: {{ .name }}
|
||||
mountPath: {{ .mountPath }}
|
||||
subPath: {{ .subPath }}
|
||||
readOnly: {{ .readOnly }}
|
||||
{{- end }}
|
||||
{{- range .Values.esRollover.extraSecretMounts }}
|
||||
- name: {{ .name }}
|
||||
mountPath: {{ .mountPath }}
|
||||
subPath: {{ .subPath }}
|
||||
readOnly: {{ .readOnly }}
|
||||
{{- end }}
|
||||
{{- if .Values.storage.elasticsearch.tls.enabled }}
|
||||
- name: {{ .Values.storage.elasticsearch.tls.secretName }}
|
||||
mountPath: {{ .Values.storage.elasticsearch.tls.mountPath }}
|
||||
subPath: {{ .Values.storage.elasticsearch.tls.subPath }}
|
||||
readOnly: true
|
||||
{{- end }}
|
||||
volumes:
|
||||
{{- range .Values.esRollover.extraConfigmapMounts }}
|
||||
- name: {{ .name }}
|
||||
configMap:
|
||||
name: {{ .configMap }}
|
||||
{{- end }}
|
||||
{{- range .Values.esRollover.extraSecretMounts }}
|
||||
- name: {{ .name }}
|
||||
secret:
|
||||
secretName: {{ .secretName }}
|
||||
{{- end }}
|
||||
{{- if .Values.storage.elasticsearch.tls.enabled }}
|
||||
- name: {{ .Values.storage.elasticsearch.tls.secretName }}
|
||||
secret:
|
||||
secretName: {{ .Values.storage.elasticsearch.tls.secretName }}
|
||||
{{- end }}
|
||||
{{- end -}}
|
||||
|
|
@ -1,99 +0,0 @@
|
|||
{{- if .Values.esRollover.enabled -}}
|
||||
apiVersion: batch/v1
|
||||
kind: Job
|
||||
metadata:
|
||||
name: {{ include "jaeger.fullname" . }}-es-rollover-init
|
||||
labels:
|
||||
{{- include "jaeger.labels" . | nindent 4 }}
|
||||
app.kubernetes.io/component: es-rollover-init
|
||||
annotations:
|
||||
"helm.sh/hook": pre-install,pre-upgrade
|
||||
"helm.sh/hook-delete-policy": before-hook-creation,hook-succeeded
|
||||
{{- if .Values.esRollover.initHook.annotations }}
|
||||
{{- toYaml .Values.esRollover.initHook.annotations | nindent 4 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
{{- if .Values.esRollover.initHook.activeDeadlineSeconds }}
|
||||
activeDeadlineSeconds: {{ .Values.esRollover.initHook.activeDeadlineSeconds }}
|
||||
{{- end }}
|
||||
{{- with .Values.esRollover.initHook.ttlSecondsAfterFinished }}
|
||||
ttlSecondsAfterFinished: {{ . }}
|
||||
{{- end }}
|
||||
|
||||
template:
|
||||
metadata:
|
||||
{{- with .Values.esRollover.initHook.podAnnotations }}
|
||||
annotations: {{- toYaml . | nindent 8 }}
|
||||
{{- end }}
|
||||
labels:
|
||||
{{- include "jaeger.selectorLabels" . | nindent 8 }}
|
||||
app.kubernetes.io/component: es-rollover-init
|
||||
{{- if .Values.esRollover.initHook.podLabels }}
|
||||
{{- toYaml .Values.esRollover.initHook.podLabels | nindent 10 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
serviceAccountName: {{ template "jaeger.esRollover.serviceAccountName" . }}
|
||||
{{- include "esRollover.imagePullSecrets" . | nindent 6 }}
|
||||
securityContext: {{- toYaml .Values.esRollover.podSecurityContext | nindent 8 }}
|
||||
restartPolicy: OnFailure
|
||||
{{- with .Values.esRollover.nodeSelector }}
|
||||
nodeSelector: {{- toYaml . | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- with .Values.esRollover.affinity }}
|
||||
affinity: {{- toYaml . | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- with .Values.esRollover.tolerations }}
|
||||
tolerations: {{- toYaml . | nindent 8 }}
|
||||
{{- end }}
|
||||
|
||||
containers:
|
||||
- name: {{ include "jaeger.fullname" . }}-es-rollover-init
|
||||
securityContext: {{- toYaml .Values.esRollover.securityContext | nindent 12 }}
|
||||
image: {{ include "esRollover.image" . }}
|
||||
imagePullPolicy: {{ .Values.esRollover.image.pullPolicy }}
|
||||
args:
|
||||
- init
|
||||
- {{ include "elasticsearch.client.url" . }}
|
||||
{{ include "extra.cmdArgs" ( dict "cmdlineParams" .Values.esRollover.cmdlineParams ) | nindent 12 }}
|
||||
env:
|
||||
{{ include "elasticsearch.env" . | nindent 12 }}
|
||||
{{- with .Values.esRollover.initHook.extraEnv }}
|
||||
{{- toYaml . | nindent 12 }}
|
||||
{{- end }}
|
||||
resources: {{- toYaml .Values.esRollover.resources | nindent 12 }}
|
||||
volumeMounts:
|
||||
{{- range .Values.esRollover.extraConfigmapMounts }}
|
||||
- name: {{ .name }}
|
||||
mountPath: {{ .mountPath }}
|
||||
subPath: {{ .subPath }}
|
||||
readOnly: {{ .readOnly }}
|
||||
{{- end }}
|
||||
{{- range .Values.esRollover.extraSecretMounts }}
|
||||
- name: {{ .name }}
|
||||
mountPath: {{ .mountPath }}
|
||||
subPath: {{ .subPath }}
|
||||
readOnly: {{ .readOnly }}
|
||||
{{- end }}
|
||||
{{- if .Values.storage.elasticsearch.tls.enabled }}
|
||||
- name: {{ .Values.storage.elasticsearch.tls.secretName }}
|
||||
mountPath: {{ .Values.storage.elasticsearch.tls.mountPath }}
|
||||
subPath: {{ .Values.storage.elasticsearch.tls.subPath }}
|
||||
readOnly: true
|
||||
{{- end }}
|
||||
volumes:
|
||||
{{- range .Values.esRollover.extraConfigmapMounts }}
|
||||
- name: {{ .name }}
|
||||
configMap:
|
||||
name: {{ .configMap }}
|
||||
{{- end }}
|
||||
{{- range .Values.esRollover.extraSecretMounts }}
|
||||
- name: {{ .name }}
|
||||
secret:
|
||||
secretName: {{ .secretName }}
|
||||
{{- end }}
|
||||
{{- if .Values.storage.elasticsearch.tls.enabled }}
|
||||
- name: {{ .Values.storage.elasticsearch.tls.secretName }}
|
||||
secret:
|
||||
secretName: {{ .Values.storage.elasticsearch.tls.secretName }}
|
||||
{{- end }}
|
||||
{{- end -}}
|
||||
|
|
@ -1,15 +0,0 @@
|
|||
{{- if and .Values.esRollover.enabled .Values.esRollover.serviceAccount.create -}}
|
||||
apiVersion: v1
|
||||
kind: ServiceAccount
|
||||
metadata:
|
||||
name: {{ template "jaeger.esRollover.serviceAccountName" . }}
|
||||
labels:
|
||||
{{- include "jaeger.labels" . | nindent 4 }}
|
||||
app.kubernetes.io/component: es-index-rollover
|
||||
annotations:
|
||||
"helm.sh/hook": pre-install,pre-upgrade
|
||||
# Must be created before the rollover init hook
|
||||
"helm.sh/hook-weight": "-10"
|
||||
"helm.sh/hook-delete-policy": before-hook-creation
|
||||
automountServiceAccountToken: {{ .Values.esRollover.serviceAccount.automountServiceAccountToken }}
|
||||
{{- end -}}
|
||||
|
|
@ -1,4 +0,0 @@
|
|||
{{- range .Values.extraObjects }}
|
||||
---
|
||||
{{ tpl (. | toYaml) $ }}
|
||||
{{- end }}
|
||||
|
|
@ -19,28 +19,19 @@ spec:
|
|||
app.kubernetes.io/component: hotrod
|
||||
spec:
|
||||
securityContext:
|
||||
{{- toYaml .Values.hotrod.podSecurityContext | nindent 8 }}
|
||||
{{ toYaml .Values.hotrod.podSecurityContext | indent 8 }}
|
||||
serviceAccountName: {{ template "jaeger.hotrod.serviceAccountName" . }}
|
||||
{{- include "hotrod.imagePullSecrets" . | nindent 6 }}
|
||||
containers:
|
||||
- name: {{ include "jaeger.fullname" . }}-hotrod
|
||||
securityContext:
|
||||
{{- toYaml .Values.hotrod.securityContext | nindent 12 }}
|
||||
image: {{ include "hotrod.image" . }}
|
||||
{{ toYaml .Values.hotrod.securityContext | indent 12 }}
|
||||
image: {{ .Values.hotrod.image.repository }}:{{ .Values.tag }}
|
||||
imagePullPolicy: {{ .Values.hotrod.image.pullPolicy }}
|
||||
args:
|
||||
{{- toYaml .Values.hotrod.args | nindent 12 }}
|
||||
{{- with .Values.hotrod.extraArgs }}
|
||||
{{- toYaml . | nindent 12 }}
|
||||
{{- end }}
|
||||
env:
|
||||
- name: JAEGER_AGENT_HOST
|
||||
value: {{ template "jaeger.hotrod.tracing.host" . }}
|
||||
- name: JAEGER_AGENT_PORT
|
||||
value: {{ .Values.hotrod.tracing.port | quote }}
|
||||
{{- if .Values.hotrod.extraEnv }}
|
||||
{{- toYaml .Values.hotrod.extraEnv | nindent 12 }}
|
||||
{{- end }}
|
||||
ports:
|
||||
- name: http
|
||||
containerPort: 8080
|
||||
|
|
@ -54,7 +45,7 @@ spec:
|
|||
path: /
|
||||
port: http
|
||||
resources:
|
||||
{{- toYaml .Values.hotrod.resources | nindent 12 }}
|
||||
{{ toYaml .Values.hotrod.resources | indent 12 }}
|
||||
{{- with .Values.hotrod.nodeSelector }}
|
||||
nodeSelector:
|
||||
{{- toYaml . | nindent 8 }}
|
||||
|
|
|
|||
|
|
@ -1,35 +1,32 @@
|
|||
{{- if .Values.hotrod.enabled -}}
|
||||
{{- if .Values.hotrod.ingress.enabled -}}
|
||||
{{- $ingressSupportsIngressClassName := eq (include "common.ingress.supportsIngressClassname" .) "true" }}
|
||||
{{- $serviceName := include "jaeger.fullname" . -}}
|
||||
{{- $servicePort := .Values.hotrod.service.port -}}
|
||||
apiVersion: {{ include "common.capabilities.ingress.apiVersion" $ }}
|
||||
{{- if .Values.hotrod.ingress.enabled -}}
|
||||
{{- $serviceName := include "jaeger.fullname" . -}}
|
||||
{{- $servicePort := .Values.hotrod.service.port -}}
|
||||
apiVersion: extensions/v1beta1
|
||||
kind: Ingress
|
||||
metadata:
|
||||
name: {{ include "jaeger.fullname" . }}-hotrod
|
||||
labels:
|
||||
{{- include "jaeger.labels" . | nindent 4 }}
|
||||
app.kubernetes.io/component: hotrod
|
||||
{{- if .Values.hotrod.ingress.annotations }}
|
||||
{{- if .Values.hotrod.ingress.annotations }}
|
||||
annotations:
|
||||
{{- toYaml .Values.hotrod.ingress.annotations | nindent 4 }}
|
||||
{{- end }}
|
||||
{{ toYaml .Values.hotrod.ingress.annotations | indent 4 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
{{- if and $ingressSupportsIngressClassName .Values.hotrod.ingress.ingressClassName }}
|
||||
ingressClassName: {{ .Values.hotrod.ingress.ingressClassName }}
|
||||
{{- end }}
|
||||
rules:
|
||||
{{- range $host := .Values.hotrod.ingress.hosts }}
|
||||
- host: {{ $host | quote}}
|
||||
- host: {{ $host }}
|
||||
http:
|
||||
paths:
|
||||
- path: /
|
||||
pathType: {{ default "ImplementationSpecific" $.Values.hotrod.ingress.pathType }}
|
||||
backend: {{- include "common.ingress.backend" (dict "serviceName" (printf "%s-hotrod" $serviceName) "servicePort" $servicePort "context" $) | nindent 14 }}
|
||||
{{- end -}}
|
||||
backend:
|
||||
serviceName: {{ $serviceName }}-hotrod
|
||||
servicePort: {{ $servicePort }}
|
||||
{{- end -}}
|
||||
{{- if .Values.hotrod.ingress.tls }}
|
||||
tls:
|
||||
{{- toYaml .Values.hotrod.ingress.tls | nindent 4 }}
|
||||
{{- end -}}
|
||||
{{- end -}}
|
||||
{{ toYaml .Values.hotrod.ingress.tls | indent 4 }}
|
||||
{{- end -}}
|
||||
{{- end -}}
|
||||
{{- end -}}
|
||||
|
|
|
|||
|
|
@ -6,9 +6,4 @@ metadata:
|
|||
labels:
|
||||
{{- include "jaeger.labels" . | nindent 4 }}
|
||||
app.kubernetes.io/component: hotrod
|
||||
{{- with .Values.hotrod.serviceAccount.annotations }}
|
||||
annotations:
|
||||
{{- toYaml . | nindent 4 }}
|
||||
{{- end }}
|
||||
automountServiceAccountToken: {{ .Values.hotrod.serviceAccount.automountServiceAccountToken }}
|
||||
{{- end -}}
|
||||
|
|
|
|||
|
|
@ -8,7 +8,7 @@ metadata:
|
|||
app.kubernetes.io/component: hotrod
|
||||
{{- if .Values.hotrod.service.annotations }}
|
||||
annotations:
|
||||
{{- toYaml .Values.hotrod.service.annotations | nindent 4 }}
|
||||
{{ toYaml .Values.hotrod.service.annotations | indent 4 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
type: {{ .Values.hotrod.service.type }}
|
||||
|
|
|
|||
|
|
@ -8,7 +8,7 @@ metadata:
|
|||
app.kubernetes.io/component: ingester
|
||||
{{- if .Values.ingester.annotations }}
|
||||
annotations:
|
||||
{{- toYaml .Values.ingester.annotations | nindent 4 }}
|
||||
{{ toYaml .Values.ingester.annotations | indent 4 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
{{- if not .Values.ingester.autoscaling.enabled }}
|
||||
|
|
@ -18,74 +18,93 @@ spec:
|
|||
matchLabels:
|
||||
{{- include "jaeger.selectorLabels" . | nindent 6 }}
|
||||
app.kubernetes.io/component: ingester
|
||||
strategy:
|
||||
type: Recreate
|
||||
template:
|
||||
metadata:
|
||||
annotations:
|
||||
{{- if .Values.ingester.podAnnotations }}
|
||||
{{- toYaml .Values.ingester.podAnnotations | nindent 8 }}
|
||||
{{ toYaml .Values.ingester.podAnnotations | indent 8 }}
|
||||
{{- end }}
|
||||
labels:
|
||||
{{- include "jaeger.selectorLabels" . | nindent 8 }}
|
||||
app.kubernetes.io/component: ingester
|
||||
{{- if .Values.ingester.podLabels }}
|
||||
{{- toYaml .Values.ingester.podLabels | nindent 8 }}
|
||||
{{ toYaml .Values.ingester.podLabels | indent 8 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
serviceAccountName: {{ include "jaeger.ingester.serviceAccountName" . }}
|
||||
securityContext:
|
||||
{{- toYaml .Values.ingester.podSecurityContext | nindent 8 }}
|
||||
{{- include "ingester.imagePullSecrets" . | nindent 6 }}
|
||||
{{- with .Values.ingester.nodeSelector }}
|
||||
{{ toYaml .Values.ingester.podSecurityContext | indent 8 }}
|
||||
nodeSelector:
|
||||
{{- toYaml . | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- with .Values.ingester.affinity }}
|
||||
affinity:
|
||||
{{- toYaml . | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- with .Values.ingester.topologySpreadConstraints }}
|
||||
topologySpreadConstraints:
|
||||
{{- toYaml . | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- with .Values.ingester.tolerations }}
|
||||
{{ toYaml .Values.ingester.nodeSelector | indent 8 }}
|
||||
{{- if .Values.ingester.tolerations }}
|
||||
tolerations:
|
||||
{{- toYaml . | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- if .Values.ingester.initContainers }}
|
||||
initContainers:
|
||||
{{- toYaml .Values.ingester.initContainers | nindent 8 }}
|
||||
{{- end}}
|
||||
{{ toYaml .Values.ingester.tolerations | indent 8 }}
|
||||
{{- end }}
|
||||
containers:
|
||||
- name: {{ include "jaeger.fullname" . }}-ingester
|
||||
securityContext:
|
||||
{{- toYaml .Values.ingester.securityContext | nindent 10 }}
|
||||
image: {{ include "ingester.image" . }}
|
||||
imagePullPolicy: {{ .Values.ingester.image.pullPolicy }}
|
||||
args:
|
||||
{{ include "extra.cmdArgs" ( dict "cmdlineParams" .Values.ingester.cmdlineParams ) | nindent 10 }}
|
||||
{{- include "storage.cmdArgs" . | nindent 10 }}
|
||||
{{ toYaml .Values.ingester.securityContext | indent 10 }}
|
||||
image: {{ .Values.ingester.image }}:{{ .Values.tag }}
|
||||
imagePullPolicy: {{ .Values.ingester.pullPolicy }}
|
||||
env:
|
||||
{{- if .Values.ingester.extraEnv }}
|
||||
{{- toYaml .Values.ingester.extraEnv | nindent 10 }}
|
||||
{{- end }}
|
||||
{{- range $key, $value := .Values.ingester.cmdlineParams }}
|
||||
- name: {{ $key | replace "." "_" | replace "-" "_" | upper | quote }}
|
||||
value: {{ $value | quote }}
|
||||
{{- end }}
|
||||
- name: SPAN_STORAGE_TYPE
|
||||
value: {{ .Values.storage.type }}
|
||||
{{- include "storage.env" . | nindent 10 }}
|
||||
{{ if .Values.storage.kafka.brokers }}
|
||||
- name: KAFKA_CONSUMER_BROKERS
|
||||
value: {{ tpl (include "helm-toolkit.utils.joinListWithComma" .Values.storage.kafka.brokers) . }}
|
||||
{{- end }}
|
||||
{{ if .Values.storage.kafka.topic }}
|
||||
value: {{ include "helm-toolkit.utils.joinListWithComma" .Values.storage.kafka.brokers }}
|
||||
- name: KAFKA_CONSUMER_TOPIC
|
||||
value: {{ .Values.storage.kafka.topic }}
|
||||
{{- if eq .Values.storage.type "cassandra" }}
|
||||
- name: CASSANDRA_SERVERS
|
||||
value: {{ .Values.storage.cassandra.host | quote }}
|
||||
- name: CASSANDRA_PORT
|
||||
value: {{ .Values.storage.cassandra.port | quote }}
|
||||
{{ if .Values.storage.cassandra.tls.enabled }}
|
||||
- name: CASSANDRA_TLS
|
||||
value: "true"
|
||||
- name: CASSANDRA_TLS_SERVER_NAME
|
||||
valueFrom:
|
||||
secretKeyRef:
|
||||
name: {{ .Values.storage.cassandra.tls.secretName }}
|
||||
key: commonName
|
||||
- name: CASSANDRA_TLS_KEY
|
||||
value: "/cassandra-tls/client-key.pem"
|
||||
- name: CASSANDRA_TLS_CERT
|
||||
value: "/cassandra-tls/client-cert.pem"
|
||||
- name: CASSANDRA_TLS_CA
|
||||
value: "/cassandra-tls/ca-cert.pem"
|
||||
{{- end }}
|
||||
- name: CASSANDRA_KEYSPACE
|
||||
value: {{ .Values.storage.cassandra.keyspace | quote }}
|
||||
- name: CASSANDRA_USERNAME
|
||||
value: {{ .Values.storage.cassandra.user }}
|
||||
- name: CASSANDRA_PASSWORD
|
||||
valueFrom:
|
||||
secretKeyRef:
|
||||
name: {{ if .Values.storage.cassandra.existingSecret }}{{ .Values.storage.cassandra.existingSecret }}{{- else }}{{ include "jaeger.fullname" . }}-cassandra{{- end }}
|
||||
key: password
|
||||
{{- end }}
|
||||
{{- if eq .Values.storage.type "elasticsearch" }}
|
||||
{{- if .Values.storage.elasticsearch.usePassword }}
|
||||
- name: ES_PASSWORD
|
||||
valueFrom:
|
||||
secretKeyRef:
|
||||
name: {{ if .Values.storage.elasticsearch.existingSecret }}{{ .Values.storage.elasticsearch.existingSecret }}{{- else }}{{ include "jaeger.fullname" . }}-elasticsearch{{- end }}
|
||||
key: password
|
||||
{{- end }}
|
||||
- name: ES_SERVER_URLS
|
||||
value: {{ template "elasticsearch.client.url" . }}
|
||||
- name: ES_USERNAME
|
||||
value: {{ .Values.storage.elasticsearch.user }}
|
||||
{{- if .Values.storage.elasticsearch.indexPrefix }}
|
||||
- name: ES_INDEX_PREFIX
|
||||
value: {{ .Values.storage.elasticsearch.indexPrefix }}
|
||||
{{- end }}
|
||||
{{ if .Values.storage.kafka.authentication }}
|
||||
- name: KAFKA_CONSUMER_AUTHENTICATION
|
||||
value: {{ .Values.storage.kafka.authentication }}
|
||||
{{- end }}
|
||||
{{- with .Values.ingester.envFrom }}
|
||||
envFrom: {{- toYaml . | nindent 10 }}
|
||||
{{- end }}
|
||||
ports:
|
||||
- containerPort: 14270
|
||||
name: admin
|
||||
|
|
@ -99,7 +118,7 @@ spec:
|
|||
path: /
|
||||
port: admin
|
||||
resources:
|
||||
{{- toYaml .Values.ingester.resources | nindent 10 }}
|
||||
{{ toYaml .Values.ingester.resources | indent 10 }}
|
||||
volumeMounts:
|
||||
{{- range .Values.ingester.extraConfigmapMounts }}
|
||||
- name: {{ .name }}
|
||||
|
|
@ -140,9 +159,4 @@ spec:
|
|||
secret:
|
||||
secretName: {{ .secretName }}
|
||||
{{- end }}
|
||||
{{- if .Values.storage.cassandra.tls.enabled }}
|
||||
- name: {{ .Values.storage.cassandra.tls.secretName }}
|
||||
secret:
|
||||
secretName: {{ .Values.storage.cassandra.tls.secretName }}
|
||||
{{- end }}
|
||||
{{- end -}}
|
||||
|
|
|
|||
|
|
@ -1,5 +1,5 @@
|
|||
{{- if and .Values.ingester.enabled .Values.ingester.autoscaling.enabled }}
|
||||
apiVersion: {{ include "common.capabilities.hpa.apiVersion" ( dict "context" $ ) }}
|
||||
{{- if .Values.ingester.autoscaling.enabled }}
|
||||
apiVersion: autoscaling/v2beta1
|
||||
kind: HorizontalPodAutoscaler
|
||||
metadata:
|
||||
name: {{ template "jaeger.ingester.name" . }}
|
||||
|
|
@ -8,36 +8,20 @@ metadata:
|
|||
app.kubernetes.io/component: ingester
|
||||
spec:
|
||||
scaleTargetRef:
|
||||
apiVersion: {{ include "common.capabilities.deployment.apiVersion" . }}
|
||||
apiVersion: apps/v1
|
||||
kind: Deployment
|
||||
name: {{ template "jaeger.ingester.name" . }}
|
||||
minReplicas: {{ .Values.ingester.autoscaling.minReplicas }}
|
||||
maxReplicas: {{ .Values.ingester.autoscaling.maxReplicas }}
|
||||
metrics:
|
||||
- type: Resource
|
||||
resource:
|
||||
name: cpu
|
||||
targetAverageUtilization: {{ .Values.ingester.autoscaling.targetCPUUtilizationPercentage | default 80 }}
|
||||
{{- if .Values.ingester.autoscaling.targetMemoryUtilizationPercentage }}
|
||||
- type: Resource
|
||||
resource:
|
||||
name: memory
|
||||
{{- if eq "autoscaling/v2" (include "common.capabilities.hpa.apiVersion" ( dict "context" $ )) }}
|
||||
target:
|
||||
averageUtilization: {{ .Values.ingester.autoscaling.targetMemoryUtilizationPercentage }}
|
||||
type: Utilization
|
||||
{{- else }}
|
||||
targetAverageUtilization: {{ .Values.ingester.autoscaling.targetMemoryUtilizationPercentage }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
- type: Resource
|
||||
resource:
|
||||
name: cpu
|
||||
{{- if eq "autoscaling/v2" (include "common.capabilities.hpa.apiVersion" ( dict "context" $ )) }}
|
||||
target:
|
||||
averageUtilization: {{ .Values.ingester.autoscaling.targetCPUUtilizationPercentage | default 80 }}
|
||||
type: Utilization
|
||||
{{- else }}
|
||||
targetAverageUtilization: {{ .Values.ingester.autoscaling.targetCPUUtilizationPercentage | default 80 }}
|
||||
{{- end }}
|
||||
{{- with .Values.ingester.autoscaling.behavior }}
|
||||
behavior:
|
||||
{{- toYaml . | nindent 4 }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
|
|
|
|||
|
|
@ -6,9 +6,4 @@ metadata:
|
|||
labels:
|
||||
{{- include "jaeger.labels" . | nindent 4 }}
|
||||
app.kubernetes.io/component: ingester
|
||||
{{- with .Values.ingester.serviceAccount.annotations }}
|
||||
annotations:
|
||||
{{- toYaml . | nindent 4 }}
|
||||
{{- end }}
|
||||
automountServiceAccountToken: {{ .Values.ingester.serviceAccount.automountServiceAccountToken }}
|
||||
{{- end -}}
|
||||
|
|
|
|||
|
|
@ -1,44 +0,0 @@
|
|||
{{- if and (.Values.ingester.enabled) (.Values.ingester.serviceMonitor.enabled)}}
|
||||
apiVersion: monitoring.coreos.com/v1
|
||||
kind: ServiceMonitor
|
||||
metadata:
|
||||
name: {{ template "jaeger.ingester.name" . }}
|
||||
{{- if .Values.ingester.serviceMonitor.namespace }}
|
||||
namespace: {{ .Values.ingester.serviceMonitor.namespace }}
|
||||
{{- end }}
|
||||
labels:
|
||||
{{- include "jaeger.labels" . | nindent 4 }}
|
||||
app.kubernetes.io/component: ingester
|
||||
{{- if .Values.ingester.serviceMonitor.additionalLabels }}
|
||||
{{- toYaml .Values.ingester.serviceMonitor.additionalLabels | nindent 4 }}
|
||||
{{- end }}
|
||||
{{- if .Values.ingester.serviceMonitor.annotations }}
|
||||
annotations:
|
||||
{{- toYaml .Values.ingester.serviceMonitor.annotations | nindent 4 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
endpoints:
|
||||
- port: admin
|
||||
path: /metrics
|
||||
{{- if .Values.ingester.serviceMonitor.interval }}
|
||||
interval: {{ .Values.ingester.serviceMonitor.interval }}
|
||||
{{- end }}
|
||||
{{- if .Values.ingester.serviceMonitor.scrapeTimeout }}
|
||||
scrapeTimeout: {{ .Values.ingester.serviceMonitor.scrapeTimeout }}
|
||||
{{- end }}
|
||||
{{- if .Values.ingester.serviceMonitor.relabelings }}
|
||||
relabelings:
|
||||
{{- toYaml .Values.ingester.serviceMonitor.relabelings | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- if .Values.ingester.serviceMonitor.metricRelabelings }}
|
||||
metricRelabelings:
|
||||
{{- toYaml .Values.ingester.serviceMonitor.metricRelabelings | nindent 8 }}
|
||||
{{- end }}
|
||||
namespaceSelector:
|
||||
matchNames:
|
||||
- {{ .Release.Namespace }}
|
||||
selector:
|
||||
matchLabels:
|
||||
app.kubernetes.io/component: ingester
|
||||
app.kubernetes.io/instance: {{ .Release.Name }}
|
||||
{{- end }}
|
||||
|
|
@ -1,23 +0,0 @@
|
|||
{{- if .Values.ingester.enabled -}}
|
||||
apiVersion: v1
|
||||
kind: Service
|
||||
metadata:
|
||||
name: {{ template "jaeger.ingester.name" . }}
|
||||
labels:
|
||||
{{- include "jaeger.labels" . | nindent 4 }}
|
||||
app.kubernetes.io/component: ingester
|
||||
{{- if .Values.ingester.service.annotations }}
|
||||
annotations:
|
||||
{{- toYaml .Values.ingester.service.annotations | nindent 4 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
ports:
|
||||
- name: admin
|
||||
port: 14270
|
||||
targetPort: admin
|
||||
selector:
|
||||
{{- include "jaeger.selectorLabels" . | nindent 4 }}
|
||||
app.kubernetes.io/component: ingester
|
||||
type: {{ .Values.ingester.service.type }}
|
||||
{{- template "loadBalancerSourceRanges" .Values.ingester }}
|
||||
{{- end -}}
|
||||
|
|
@ -1,12 +0,0 @@
|
|||
{{- if and .Values.query.oAuthSidecar.enabled .Values.query.oAuthSidecar.config}}
|
||||
apiVersion: v1
|
||||
kind: ConfigMap
|
||||
metadata:
|
||||
name: {{ include "jaeger.fullname" . }}-oauth-configuration
|
||||
labels:
|
||||
{{- include "jaeger.labels" . | nindent 4 }}
|
||||
app.kubernetes.io/component: query
|
||||
data:
|
||||
oauth2-proxy.cfg: |-
|
||||
{{ tpl .Values.query.oAuthSidecar.config . | indent 4 }}
|
||||
{{- end }}
|
||||
|
|
@ -1,12 +0,0 @@
|
|||
{{- if .Values.query.config }}
|
||||
apiVersion: v1
|
||||
kind: ConfigMap
|
||||
metadata:
|
||||
name: {{ include "jaeger.fullname" . }}-ui-configuration
|
||||
labels:
|
||||
{{- include "jaeger.labels" . | nindent 4 }}
|
||||
app.kubernetes.io/component: query
|
||||
data:
|
||||
query-ui-config.json: |-
|
||||
{{ tpl .Values.query.config . | indent 4 }}
|
||||
{{- end }}
|
||||
|
|
@ -8,7 +8,7 @@ metadata:
|
|||
app.kubernetes.io/component: query
|
||||
{{- if .Values.query.annotations }}
|
||||
annotations:
|
||||
{{- toYaml .Values.query.annotations | nindent 4 }}
|
||||
{{ toYaml .Values.query.annotations | indent 4 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
replicas: {{ .Values.query.replicaCount }}
|
||||
|
|
@ -16,101 +16,102 @@ spec:
|
|||
matchLabels:
|
||||
{{- include "jaeger.selectorLabels" . | nindent 6 }}
|
||||
app.kubernetes.io/component: query
|
||||
strategy:
|
||||
type: Recreate
|
||||
template:
|
||||
metadata:
|
||||
{{- if or .Values.query.config .Values.query.podAnnotations }}
|
||||
{{- if .Values.query.podAnnotations }}
|
||||
annotations:
|
||||
{{- if .Values.query.config }}
|
||||
checksum/ui-config: {{ include (print $.Template.BasePath "/query-configmap.yaml") . | sha256sum }}
|
||||
{{- end }}
|
||||
{{- if and .Values.query.oAuthSidecar.enabled .Values.query.oAuthSidecar.config }}
|
||||
checksum/oauth2-config: {{ sha256sum .Values.query.oAuthSidecar.config }}
|
||||
{{- end }}
|
||||
{{- if .Values.query.podAnnotations }}
|
||||
{{- toYaml .Values.query.podAnnotations | nindent 8 }}
|
||||
{{- end }}
|
||||
{{ toYaml .Values.query.podAnnotations | indent 8 }}
|
||||
{{- end }}
|
||||
labels:
|
||||
{{- include "jaeger.selectorLabels" . | nindent 8 }}
|
||||
app.kubernetes.io/component: query
|
||||
{{- if .Values.query.podLabels }}
|
||||
{{- toYaml .Values.query.podLabels | nindent 8 }}
|
||||
{{ toYaml .Values.query.podLabels | indent 8 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
{{- with .Values.query.priorityClassName }}
|
||||
priorityClassName: {{ . }}
|
||||
{{- end }}
|
||||
securityContext:
|
||||
{{- toYaml .Values.query.podSecurityContext | nindent 8 }}
|
||||
{{ toYaml .Values.query.podSecurityContext | indent 8 }}
|
||||
serviceAccountName: {{ template "jaeger.query.serviceAccountName" . }}
|
||||
{{- include "query.imagePullSecrets" . | nindent 6 }}
|
||||
{{- if or .Values.query.initContainers .Values.provisionDataStore.elasticsearch }}
|
||||
initContainers:
|
||||
{{- if .Values.query.initContainers }}
|
||||
{{- toYaml .Values.query.initContainers | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- if .Values.provisionDataStore.elasticsearch }}
|
||||
- name: elasticsearch-checker
|
||||
image: {{ include "curl.image" . }}
|
||||
command:
|
||||
- sh
|
||||
- "-c"
|
||||
- |
|
||||
url="{{ include "elasticsearch.client.url" . }}"
|
||||
until [ "$(curl -s -o /dev/null -w '%{http_code}' "$url/_cluster/health")" = "200" ]; do
|
||||
echo "waiting for Elasticsearch at $url"
|
||||
sleep 5
|
||||
done
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
containers:
|
||||
- name: {{ template "jaeger.query.name" . }}
|
||||
securityContext:
|
||||
{{- toYaml .Values.query.securityContext | nindent 10 }}
|
||||
image: {{ include "query.image" . }}
|
||||
imagePullPolicy: {{ .Values.query.image.pullPolicy }}
|
||||
args:
|
||||
{{ include "extra.cmdArgs" ( dict "cmdlineParams" .Values.query.cmdlineParams ) | nindent 10 }}
|
||||
{{- include "storage.cmdArgs" . | nindent 10 }}
|
||||
{{ toYaml .Values.query.securityContext | indent 10 }}
|
||||
image: {{ .Values.query.image }}:{{ .Values.tag }}
|
||||
imagePullPolicy: {{ .Values.query.pullPolicy }}
|
||||
env:
|
||||
{{- if .Values.query.extraEnv }}
|
||||
{{- toYaml .Values.query.extraEnv | nindent 10 }}
|
||||
{{- end }}
|
||||
{{- range $key, $value := .Values.query.cmdlineParams }}
|
||||
- name: {{ $key | replace "." "_" | replace "-" "_" | upper | quote }}
|
||||
value: {{ $value | quote }}
|
||||
{{- end }}
|
||||
- name: SPAN_STORAGE_TYPE
|
||||
value: {{ .Values.storage.type }}
|
||||
{{- include "storage.env" . | nindent 10 }}
|
||||
{{- if eq .Values.storage.type "cassandra" }}
|
||||
- name: CASSANDRA_SERVERS
|
||||
value: {{ template "cassandra.host" . }}
|
||||
- name: CASSANDRA_PORT
|
||||
value: {{ .Values.storage.cassandra.port | quote }}
|
||||
{{ if .Values.storage.cassandra.tls.enabled }}
|
||||
- name: CASSANDRA_TLS
|
||||
value: "true"
|
||||
- name: CASSANDRA_TLS_SERVER_NAME
|
||||
valueFrom:
|
||||
secretKeyRef:
|
||||
name: {{ .Values.storage.cassandra.tls.secretName }}
|
||||
key: commonName
|
||||
- name: CASSANDRA_TLS_KEY
|
||||
value: "/cassandra-tls/client-key.pem"
|
||||
- name: CASSANDRA_TLS_CERT
|
||||
value: "/cassandra-tls/client-cert.pem"
|
||||
- name: CASSANDRA_TLS_CA
|
||||
value: "/cassandra-tls/ca-cert.pem"
|
||||
{{- end }}
|
||||
{{- if .Values.storage.cassandra.keyspace }}
|
||||
- name: CASSANDRA_KEYSPACE
|
||||
value: {{ .Values.storage.cassandra.keyspace | quote }}
|
||||
{{- end }}
|
||||
- name: CASSANDRA_USERNAME
|
||||
value: {{ .Values.storage.cassandra.user }}
|
||||
- name: CASSANDRA_PASSWORD
|
||||
valueFrom:
|
||||
secretKeyRef:
|
||||
name: {{ if .Values.storage.cassandra.existingSecret }}{{ .Values.storage.cassandra.existingSecret }}{{- else }}{{ include "jaeger.fullname" . }}-cassandra{{- end }}
|
||||
key: password
|
||||
{{- end }}
|
||||
{{- if eq .Values.storage.type "elasticsearch" }}
|
||||
{{- if .Values.storage.elasticsearch.usePassword }}
|
||||
- name: ES_PASSWORD
|
||||
valueFrom:
|
||||
secretKeyRef:
|
||||
name: {{ if .Values.storage.elasticsearch.existingSecret }}{{ .Values.storage.elasticsearch.existingSecret }}{{- else }}{{ include "jaeger.fullname" . }}-elasticsearch{{- end }}
|
||||
key: password
|
||||
{{- end }}
|
||||
- name: ES_SERVER_URLS
|
||||
value: {{ template "elasticsearch.client.url" . }}
|
||||
- name: ES_USERNAME
|
||||
value: {{ .Values.storage.elasticsearch.user }}
|
||||
{{- if .Values.storage.elasticsearch.indexPrefix }}
|
||||
- name: ES_INDEX_PREFIX
|
||||
value: {{ .Values.storage.elasticsearch.indexPrefix }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- if .Values.query.basePath }}
|
||||
- name: QUERY_BASE_PATH
|
||||
value: {{ .Values.query.basePath | quote }}
|
||||
{{- end }}
|
||||
- name: JAEGER_AGENT_PORT
|
||||
value: "6831"
|
||||
{{- if .Values.query.config}}
|
||||
- name: QUERY_UI_CONFIG
|
||||
value: /etc/conf/query-ui-config.json
|
||||
{{- end }}
|
||||
{{- with .Values.query.envFrom }}
|
||||
envFrom: {{- toYaml . | nindent 10 }}
|
||||
{{- end }}
|
||||
ports:
|
||||
- name: query
|
||||
containerPort: 16686
|
||||
protocol: TCP
|
||||
- name: grpc
|
||||
containerPort: 16685
|
||||
protocol: TCP
|
||||
- name: admin
|
||||
containerPort: 16687
|
||||
protocol: TCP
|
||||
resources:
|
||||
{{- toYaml .Values.query.resources | nindent 10 }}
|
||||
{{ toYaml .Values.query.resources | indent 10 }}
|
||||
volumeMounts:
|
||||
{{- range .Values.query.extraSecretMounts }}
|
||||
- name: {{ .name }}
|
||||
mountPath: {{ .mountPath }}
|
||||
subPath: {{ .subPath }}
|
||||
readOnly: {{ .readOnly }}
|
||||
{{- end }}
|
||||
{{- range .Values.query.extraConfigmapMounts }}
|
||||
- name: {{ .name }}
|
||||
mountPath: {{ .mountPath }}
|
||||
|
|
@ -131,16 +132,6 @@ spec:
|
|||
subPath: "client-key.pem"
|
||||
readOnly: true
|
||||
{{- end }}
|
||||
{{- if .Values.storage.elasticsearch.tls.enabled }}
|
||||
- name: {{ .Values.storage.elasticsearch.tls.secretName }}
|
||||
mountPath: {{ .Values.storage.elasticsearch.tls.mountPath }}
|
||||
subPath: {{ .Values.storage.elasticsearch.tls.subPath }}
|
||||
readOnly: true
|
||||
{{- end }}
|
||||
{{- if .Values.query.config}}
|
||||
- name: ui-configuration
|
||||
mountPath: /etc/conf/
|
||||
{{- end }}
|
||||
livenessProbe:
|
||||
httpGet:
|
||||
path: /
|
||||
|
|
@ -149,76 +140,25 @@ spec:
|
|||
httpGet:
|
||||
path: /
|
||||
port: admin
|
||||
{{- if .Values.query.oAuthSidecar.enabled }}
|
||||
- name: {{ template "jaeger.agent.name" . }}-oauth2-sidecar
|
||||
securityContext:
|
||||
{{- toYaml .Values.query.securityContext | nindent 10 }}
|
||||
image: {{ include "oAuthSidecar.image" . }}
|
||||
imagePullPolicy: {{ .Values.query.oAuthSidecar.image.pullPolicy }}
|
||||
args:
|
||||
{{- range .Values.query.oAuthSidecar.args }}
|
||||
- {{ . }}
|
||||
{{- end }}
|
||||
{{- if .Values.query.oAuthSidecar.extraEnv }}
|
||||
env:
|
||||
{{- toYaml .Values.query.oAuthSidecar.extraEnv | nindent 10 }}
|
||||
{{- end }}
|
||||
volumeMounts:
|
||||
{{- range .Values.query.oAuthSidecar.extraConfigmapMounts }}
|
||||
- name: {{ .name }}
|
||||
mountPath: {{ .mountPath }}
|
||||
subPath: {{ .subPath }}
|
||||
readOnly: {{ .readOnly }}
|
||||
{{- end }}
|
||||
{{- range .Values.query.oAuthSidecar.extraSecretMounts }}
|
||||
- name: {{ .name }}
|
||||
mountPath: {{ .mountPath }}
|
||||
subPath: {{ .subPath }}
|
||||
readOnly: {{ .readOnly }}
|
||||
{{- end }}
|
||||
{{- if .Values.query.oAuthSidecar.config}}
|
||||
- name: jaeger-oauth-configuration
|
||||
mountPath: /etc/oauth2-proxy
|
||||
{{- end }}
|
||||
ports:
|
||||
- containerPort: {{ .Values.query.oAuthSidecar.containerPort }}
|
||||
name: oauth-proxy
|
||||
resources:
|
||||
{{- toYaml .Values.query.oAuthSidecar.resources | nindent 10 }}
|
||||
{{- if .Values.query.oAuthSidecar.livenessProbe }}
|
||||
livenessProbe:
|
||||
{{- toYaml .Values.query.oAuthSidecar.livenessProbe | nindent 10 }}
|
||||
{{- end }}
|
||||
{{- if .Values.query.oAuthSidecar.readinessProbe }}
|
||||
readinessProbe:
|
||||
{{- toYaml .Values.query.oAuthSidecar.readinessProbe | nindent 10 }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- if .Values.query.agentSidecar.enabled }}
|
||||
- name: {{ template "jaeger.agent.name" . }}-sidecar
|
||||
securityContext:
|
||||
{{- toYaml .Values.query.securityContext | nindent 10 }}
|
||||
image: {{ include "agent.image" . }}
|
||||
imagePullPolicy: {{ .Values.agent.image.pullPolicy }}
|
||||
args:
|
||||
{{- range $key, $value := .Values.agent.cmdlineParams }}
|
||||
{{- if $value }}
|
||||
- --{{ $key }}={{ $value }}
|
||||
{{- else }}
|
||||
- --{{ $key }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{ toYaml .Values.query.securityContext | indent 10 }}
|
||||
image: {{ .Values.agent.image }}:{{ .Values.tag }}
|
||||
imagePullPolicy: {{ .Values.agent.pullPolicy }}
|
||||
env:
|
||||
{{- if not (hasKey .Values.agent.cmdlineParams "reporter.grpc.host-port") }}
|
||||
- name: REPORTER_GRPC_HOST_PORT
|
||||
value: {{ include "jaeger.collector.name" . }}:{{ .Values.collector.service.grpc.port }}
|
||||
value: {{ include "jaeger.collector.name" . }}:{{ .Values.collector.service.grpcPort }}
|
||||
{{- end }}
|
||||
{{- range $key, $value := .Values.agent.cmdlineParams }}
|
||||
- name: {{ $key | replace "." "_" | replace "-" "_" | upper | quote }}
|
||||
value: {{ $value | quote }}
|
||||
{{- end }}
|
||||
ports:
|
||||
- name: admin
|
||||
containerPort: 14271
|
||||
protocol: TCP
|
||||
resources:
|
||||
{{- toYaml .Values.query.agentSidecar.resources | nindent 10 }}
|
||||
volumeMounts:
|
||||
{{- range .Values.agent.extraConfigmapMounts }}
|
||||
- name: {{ .name }}
|
||||
|
|
@ -241,9 +181,6 @@ spec:
|
|||
path: /
|
||||
port: admin
|
||||
{{- end }}
|
||||
{{- if .Values.query.sidecars }}
|
||||
{{- tpl (toYaml .Values.query.sidecars) . | nindent 6 }}
|
||||
{{- end }}
|
||||
dnsPolicy: {{ .Values.query.dnsPolicy }}
|
||||
restartPolicy: Always
|
||||
volumes:
|
||||
|
|
@ -252,44 +189,6 @@ spec:
|
|||
configMap:
|
||||
name: {{ .configMap }}
|
||||
{{- end }}
|
||||
{{- range .Values.query.extraSecretMounts }}
|
||||
- name: {{ .name }}
|
||||
secret:
|
||||
secretName: {{ .secretName }}
|
||||
{{- end }}
|
||||
{{- if .Values.query.config}}
|
||||
- name: ui-configuration
|
||||
configMap:
|
||||
name: {{ include "jaeger.fullname" . }}-ui-configuration
|
||||
{{- end }}
|
||||
{{- if .Values.storage.cassandra.tls.enabled }}
|
||||
- name: {{ .Values.storage.cassandra.tls.secretName }}
|
||||
secret:
|
||||
secretName: {{ .Values.storage.cassandra.tls.secretName }}
|
||||
{{- end }}
|
||||
{{- if .Values.storage.elasticsearch.tls.enabled }}
|
||||
- name: {{ .Values.storage.elasticsearch.tls.secretName }}
|
||||
secret:
|
||||
secretName: {{ .Values.storage.elasticsearch.tls.secretName }}
|
||||
{{- end }}
|
||||
{{- if .Values.query.oAuthSidecar.enabled }}
|
||||
{{- range .Values.query.oAuthSidecar.extraConfigmapMounts }}
|
||||
- name: {{ .name }}
|
||||
configMap:
|
||||
name: {{ .configMap }}
|
||||
{{- end }}
|
||||
{{- range .Values.query.oAuthSidecar.extraSecretMounts }}
|
||||
- name: {{ .name }}
|
||||
secret:
|
||||
secretName: {{ .secretName }}
|
||||
{{- end }}
|
||||
{{- if .Values.query.oAuthSidecar.config }}
|
||||
- name: jaeger-oauth-configuration
|
||||
configMap:
|
||||
name: {{ include "jaeger.fullname" . }}-oauth-configuration
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- if .Values.query.agentSidecar.enabled }}
|
||||
{{- range .Values.agent.extraSecretMounts }}
|
||||
- name: {{ .name }}
|
||||
secret:
|
||||
|
|
@ -300,10 +199,6 @@ spec:
|
|||
configMap:
|
||||
name: {{ .configMap }}
|
||||
{{- end }}
|
||||
{{- end }}
|
||||
{{- if .Values.query.extraVolumes }}
|
||||
{{- tpl (toYaml .Values.query.extraVolumes) . | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- with .Values.query.nodeSelector }}
|
||||
nodeSelector:
|
||||
{{- toYaml . | nindent 8 }}
|
||||
|
|
@ -312,10 +207,6 @@ spec:
|
|||
affinity:
|
||||
{{- toYaml . | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- with .Values.query.topologySpreadConstraints }}
|
||||
topologySpreadConstraints:
|
||||
{{- toYaml . | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- with .Values.query.tolerations }}
|
||||
tolerations:
|
||||
{{- toYaml . | nindent 8 }}
|
||||
|
|
|
|||
|
|
@ -1,41 +1,30 @@
|
|||
{{- if .Values.query.ingress.enabled -}}
|
||||
{{- $ingressSupportsIngressClassName := eq (include "common.ingress.supportsIngressClassname" .) "true" }}
|
||||
{{- $servicePort := .Values.query.service.port -}}
|
||||
{{- $basePath := .Values.query.basePath -}}
|
||||
apiVersion: {{ include "common.capabilities.ingress.apiVersion" $ }}
|
||||
{{- $servicePort := .Values.query.service.port -}}
|
||||
{{- $basePath := .Values.query.basePath -}}
|
||||
apiVersion: extensions/v1beta1
|
||||
kind: Ingress
|
||||
metadata:
|
||||
name: {{ template "jaeger.query.name" . }}
|
||||
labels:
|
||||
{{- include "jaeger.labels" . | nindent 4 }}
|
||||
{{- if .Values.query.ingress.labels }}
|
||||
{{- toYaml .Values.query.ingress.labels | nindent 4 }}
|
||||
{{- end }}
|
||||
app.kubernetes.io/component: query
|
||||
{{- if .Values.query.ingress.annotations }}
|
||||
annotations:
|
||||
{{- toYaml .Values.query.ingress.annotations | nindent 4 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
{{- if and $ingressSupportsIngressClassName .Values.query.ingress.ingressClassName }}
|
||||
ingressClassName: {{ .Values.query.ingress.ingressClassName }}
|
||||
{{ toYaml .Values.query.ingress.annotations | indent 4 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
rules:
|
||||
{{- range $host := .Values.query.ingress.hosts }}
|
||||
- host: {{ $host | quote }}
|
||||
- host: {{ $host }}
|
||||
http:
|
||||
paths:
|
||||
- path: {{ $basePath }}
|
||||
pathType: {{ default "ImplementationSpecific" $.Values.query.ingress.pathType }}
|
||||
backend: {{- include "common.ingress.backend" (dict "serviceName" (include "jaeger.query.name" $) "servicePort" $servicePort "context" $) | nindent 14 }}
|
||||
{{- end -}}
|
||||
{{- if .Values.query.ingress.health.exposed }}
|
||||
- path: /health
|
||||
pathType: {{ default "ImplementationSpecific" $.Values.query.ingress.pathType }}
|
||||
backend: {{- include "common.ingress.backend" (dict "serviceName" (include "jaeger.query.name" $) "servicePort" 16687 "context" $) | nindent 14 }}
|
||||
{{- end -}}
|
||||
backend:
|
||||
serviceName: {{ template "jaeger.query.name" $ }}
|
||||
servicePort: {{ $servicePort }}
|
||||
{{- end -}}
|
||||
{{- if .Values.query.ingress.tls }}
|
||||
tls:
|
||||
{{- toYaml .Values.query.ingress.tls | nindent 4 }}
|
||||
{{- end -}}
|
||||
{{ toYaml .Values.query.ingress.tls | indent 4 }}
|
||||
{{- end -}}
|
||||
{{- end -}}
|
||||
|
|
|
|||
|
|
@ -1,5 +0,0 @@
|
|||
{{- if and .Values.networkPolicy.enabled .Values.query.networkPolicy.enabled .Values.query.networkPolicy.egressRules }}
|
||||
{{- $extraVals := dict "Name" (include "jaeger.query.name" .) "Component" "query" "ComponentValues" .Values.query -}}
|
||||
{{- $npVals := merge $extraVals . -}}
|
||||
{{ include "jaeger.egress.networkPolicy" $npVals }}
|
||||
{{- end }}
|
||||
|
|
@ -1,5 +0,0 @@
|
|||
{{- if and .Values.networkPolicy.enabled .Values.query.networkPolicy.enabled .Values.query.networkPolicy.ingressRules }}
|
||||
{{- $extraVals := dict "Name" (include "jaeger.query.name" .) "Component" "query" "ComponentValues" .Values.query -}}
|
||||
{{- $npVals := merge $extraVals . -}}
|
||||
{{ include "jaeger.ingress.networkPolicy" $npVals }}
|
||||
{{- end }}
|
||||
|
|
@ -6,9 +6,4 @@ metadata:
|
|||
labels:
|
||||
{{- include "jaeger.labels" . | nindent 4 }}
|
||||
app.kubernetes.io/component: query
|
||||
{{- with .Values.query.serviceAccount.annotations }}
|
||||
annotations:
|
||||
{{- toYaml . | nindent 4 }}
|
||||
{{- end }}
|
||||
automountServiceAccountToken: {{ .Values.query.serviceAccount.automountServiceAccountToken }}
|
||||
{{- end -}}
|
||||
|
|
|
|||
|
|
@ -1,44 +0,0 @@
|
|||
{{- if and (.Values.query.enabled) (.Values.query.serviceMonitor.enabled)}}
|
||||
apiVersion: monitoring.coreos.com/v1
|
||||
kind: ServiceMonitor
|
||||
metadata:
|
||||
name: {{ template "jaeger.query.name" . }}
|
||||
{{- if .Values.query.serviceMonitor.namespace }}
|
||||
namespace: {{ .Values.query.serviceMonitor.namespace }}
|
||||
{{- end }}
|
||||
labels:
|
||||
{{- include "jaeger.labels" . | nindent 4 }}
|
||||
app.kubernetes.io/component: query
|
||||
{{- if .Values.query.serviceMonitor.additionalLabels }}
|
||||
{{- toYaml .Values.query.serviceMonitor.additionalLabels | nindent 4 }}
|
||||
{{- end }}
|
||||
{{- if .Values.query.serviceMonitor.annotations }}
|
||||
annotations:
|
||||
{{- toYaml .Values.query.serviceMonitor.annotations | nindent 4 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
endpoints:
|
||||
- port: admin
|
||||
path: /metrics
|
||||
{{- if .Values.query.serviceMonitor.interval }}
|
||||
interval: {{ .Values.query.serviceMonitor.interval }}
|
||||
{{- end }}
|
||||
{{- if .Values.query.serviceMonitor.scrapeTimeout }}
|
||||
scrapeTimeout: {{ .Values.query.serviceMonitor.scrapeTimeout }}
|
||||
{{- end }}
|
||||
{{- if .Values.query.serviceMonitor.relabelings }}
|
||||
relabelings:
|
||||
{{- toYaml .Values.query.serviceMonitor.relabelings | nindent 8 }}
|
||||
{{- end }}
|
||||
{{- if .Values.query.serviceMonitor.metricRelabelings }}
|
||||
metricRelabelings:
|
||||
{{- toYaml .Values.query.serviceMonitor.metricRelabelings | nindent 8 }}
|
||||
{{- end }}
|
||||
namespaceSelector:
|
||||
matchNames:
|
||||
- {{ .Release.Namespace }}
|
||||
selector:
|
||||
matchLabels:
|
||||
app.kubernetes.io/component: query
|
||||
app.kubernetes.io/instance: {{ .Release.Name }}
|
||||
{{- end }}
|
||||
|
|
@ -8,25 +8,14 @@ metadata:
|
|||
app.kubernetes.io/component: query
|
||||
{{- if .Values.query.service.annotations }}
|
||||
annotations:
|
||||
{{- toYaml .Values.query.service.annotations | nindent 4 }}
|
||||
{{ toYaml .Values.query.service.annotations | indent 4 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
ports:
|
||||
- name: query
|
||||
port: {{ .Values.query.service.port }}
|
||||
protocol: TCP
|
||||
targetPort: {{ default (ternary "oauth-proxy" "query" .Values.query.oAuthSidecar.enabled) .Values.query.service.targetPort }}
|
||||
{{- if and (eq .Values.query.service.type "NodePort") (.Values.query.service.nodePort) }}
|
||||
nodePort: {{ .Values.query.service.nodePort }}
|
||||
{{- end }}
|
||||
- name: grpc
|
||||
port: 16685
|
||||
protocol: TCP
|
||||
targetPort: grpc
|
||||
- name: {{ .Values.query.service.admin.name }}
|
||||
port: 16687
|
||||
protocol: TCP
|
||||
targetPort: {{ .Values.query.service.admin.targetPort }}
|
||||
targetPort: query
|
||||
selector:
|
||||
{{- include "jaeger.selectorLabels" . | nindent 4 }}
|
||||
app.kubernetes.io/component: query
|
||||
|
|
|
|||
|
|
@ -1,5 +1,5 @@
|
|||
{{- if .Values.spark.enabled -}}
|
||||
apiVersion: {{ include "common.capabilities.cronjob.apiVersion" $ }}
|
||||
apiVersion: batch/v1beta1
|
||||
kind: CronJob
|
||||
metadata:
|
||||
name: {{ include "jaeger.fullname" . }}-spark
|
||||
|
|
@ -8,63 +8,67 @@ metadata:
|
|||
app.kubernetes.io/component: spark
|
||||
{{- if .Values.spark.annotations }}
|
||||
annotations:
|
||||
{{- toYaml .Values.spark.annotations | nindent 4 }}
|
||||
{{ toYaml .Values.spark.annotations | indent 4 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
schedule: {{ .Values.spark.schedule | quote }}
|
||||
successfulJobsHistoryLimit: {{ .Values.spark.successfulJobsHistoryLimit }}
|
||||
failedJobsHistoryLimit: {{ .Values.spark.failedJobsHistoryLimit }}
|
||||
concurrencyPolicy: {{ .Values.spark.concurrencyPolicy }}
|
||||
jobTemplate:
|
||||
spec:
|
||||
{{- if .Values.spark.activeDeadlineSeconds }}
|
||||
activeDeadlineSeconds: {{ .Values.spark.activeDeadlineSeconds }}
|
||||
{{- end}}
|
||||
{{- if .Values.spark.ttlSecondsAfterFinished }}
|
||||
ttlSecondsAfterFinished: {{ .Values.spark.ttlSecondsAfterFinished }}
|
||||
{{- end }}
|
||||
template:
|
||||
metadata:
|
||||
{{- if .Values.spark.podAnnotations }}
|
||||
annotations:
|
||||
{{- toYaml .Values.spark.podAnnotations | nindent 12 }}
|
||||
{{- end }}
|
||||
labels:
|
||||
{{- include "jaeger.selectorLabels" . | nindent 12 }}
|
||||
app.kubernetes.io/component: spark
|
||||
{{- if .Values.spark.podLabels }}
|
||||
{{- toYaml .Values.spark.podLabels | nindent 12 }}
|
||||
{{ toYaml .Values.spark.podLabels | indent 12 }}
|
||||
{{- end }}
|
||||
spec:
|
||||
serviceAccountName: {{ template "jaeger.spark.serviceAccountName" . }}
|
||||
{{- include "spark.imagePullSecrets" . | nindent 10 }}
|
||||
securityContext:
|
||||
{{- toYaml .Values.spark.podSecurityContext | nindent 12 }}
|
||||
containers:
|
||||
- name: {{ include "jaeger.fullname" . }}-spark
|
||||
image: {{ include "spark.image" . }}
|
||||
imagePullPolicy: {{ .Values.spark.image.pullPolicy }}
|
||||
args:
|
||||
{{ include "extra.cmdArgs" ( dict "cmdlineParams" .Values.spark.cmdlineParams ) | nindent 14 }}
|
||||
image: {{ .Values.spark.image }}:{{ .Values.spark.tag }}
|
||||
imagePullPolicy: {{ .Values.spark.pullPolicy }}
|
||||
env:
|
||||
- name: STORAGE
|
||||
value: {{ .Values.storage.type }}
|
||||
{{- include "storage.env" . | nindent 14 }}
|
||||
{{- if .Values.spark.extraEnv }}
|
||||
{{- toYaml .Values.spark.extraEnv | nindent 14 }}
|
||||
{{- range $key, $value := .Values.spark.cmdlineParams }}
|
||||
- name: {{ $key | replace "." "_" | replace "-" "_" | upper | quote }}
|
||||
value: {{ $value | quote }}
|
||||
{{- end }}
|
||||
- name: STORAGE
|
||||
value: {{ .Values.storage.type }}
|
||||
{{- if eq .Values.storage.type "cassandra" }}
|
||||
- name: CASSANDRA_CONTACT_POINTS
|
||||
value: {{ include "cassandra.contact_points" . }}
|
||||
- name: CASSANDRA_CONTACT_POINTS
|
||||
value: {{ template "cassandra.contact_points" . }}
|
||||
- name: CASSANDRA_KEYSPACE
|
||||
value: {{ .Values.storage.cassandra.keyspace }}
|
||||
{{- if .Values.storage.cassandra.usePassword }}
|
||||
- name: CASSANDRA_PASSWORD
|
||||
valueFrom:
|
||||
secretKeyRef:
|
||||
name: {{ if .Values.storage.cassandra.existingSecret }}{{ .Values.storage.cassandra.existingSecret }}{{- else }}{{ include "jaeger.fullname" . }}-cassandra{{- end }}
|
||||
key: password
|
||||
{{- end }}
|
||||
- name: CASSANDRA_USERNAME
|
||||
value: {{ .Values.storage.cassandra.user }}
|
||||
{{- end }}
|
||||
{{- if eq .Values.storage.type "elasticsearch" }}
|
||||
- name: ES_NODES
|
||||
value: {{ include "elasticsearch.client.url" . }}
|
||||
- name: ES_NODES_WAN_ONLY
|
||||
value: {{ .Values.storage.elasticsearch.nodesWanOnly | quote }}
|
||||
- name: ES_NODES
|
||||
value: {{ template "elasticsearch.client.url" . }}
|
||||
- name: ES_NODES_WAN_ONLY
|
||||
value: {{ .Values.storage.elasticsearch.nodesWanOnly | quote }}
|
||||
{{- if .Values.storage.elasticsearch.usePassword }}
|
||||
- name: ES_PASSWORD
|
||||
valueFrom:
|
||||
secretKeyRef:
|
||||
name: {{ if .Values.storage.elasticsearch.existingSecret }}{{ .Values.storage.elasticsearch.existingSecret }}{{- else }}{{ include "jaeger.fullname" . }}-elasticsearch{{- end }}
|
||||
key: password
|
||||
{{- end }}
|
||||
- name: ES_USERNAME
|
||||
value: {{ .Values.storage.elasticsearch.user }}
|
||||
{{- end }}
|
||||
resources:
|
||||
{{- toYaml .Values.spark.resources | nindent 14 }}
|
||||
{{ toYaml .Values.spark.resources | indent 14 }}
|
||||
volumeMounts:
|
||||
{{- range .Values.spark.extraConfigmapMounts }}
|
||||
- name: {{ .name }}
|
||||
|
|
@ -78,8 +82,6 @@ spec:
|
|||
subPath: {{ .subPath }}
|
||||
readOnly: {{ .readOnly }}
|
||||
{{- end }}
|
||||
securityContext:
|
||||
{{- toYaml .Values.spark.securityContext | nindent 14 }}
|
||||
restartPolicy: OnFailure
|
||||
volumes:
|
||||
{{- range .Values.spark.extraConfigmapMounts }}
|
||||
|
|
|
|||
|
|
@ -6,9 +6,4 @@ metadata:
|
|||
labels:
|
||||
{{- include "jaeger.labels" . | nindent 4 }}
|
||||
app.kubernetes.io/component: spark
|
||||
{{- with .Values.spark.serviceAccount.annotations }}
|
||||
annotations:
|
||||
{{- toYaml . | nindent 4 }}
|
||||
{{- end }}
|
||||
automountServiceAccountToken: {{ .Values.spark.serviceAccount.automountServiceAccountToken }}
|
||||
{{- end -}}
|
||||
|
|
|
|||
File diff suppressed because it is too large
Load Diff
6
ct.yaml
6
ct.yaml
|
|
@ -3,8 +3,6 @@ remote: origin
|
|||
chart-dirs:
|
||||
- charts
|
||||
chart-repos:
|
||||
- incubator=https://charts.helm.sh/incubator
|
||||
- incubator=https://kubernetes-charts-incubator.storage.googleapis.com
|
||||
- elastic=https://helm.elastic.co
|
||||
- bitnami=https://charts.bitnami.com/bitnami
|
||||
helm-extra-args: --timeout=600s
|
||||
target-branch: main
|
||||
helm-extra-args: --timeout=500
|
||||
|
|
|
|||
Loading…
Reference in New Issue