|
|
||
|---|---|---|
| .azure-pipelines | ||
| docs | ||
| example | ||
| registry | ||
| scripts | ||
| static | ||
| version | ||
| .gitignore | ||
| .travis.yml | ||
| CHANGELOG.md | ||
| DEVELOPMENT.md | ||
| Dockerfile | ||
| LICENSE | ||
| Makefile | ||
| README.md | ||
| VERSION | ||
| annotations.go | ||
| aws.go | ||
| azure.go | ||
| gcp.go | ||
| go.mod | ||
| go.sum | ||
| main.go | ||
| settings.go | ||
| types.go | ||
| vault.go | ||
README.md

k8s-vault-webhook is a Kubernetes admission webhook which listen for the events related to Kubernetes resources for injecting secret directly from secret manager to pod, secret, and configmap. The motive of creating this project is to provide a dynamic secret injection to containers/pods running inside Kubernetes from different secret managers for enhanced security.
Documentation is available here:- https://ot-container-kit.github.io/k8s-vault-webhook/
Blog Link:- https://blog.opstree.com/2021/09/14/introducing-kubernetes-vault-web-hook/
The secret managers which are currently supported:-
This project is based on secret-consumer-webhook. Please check out the source code at https://github.com/innovia/secrets-consumer-webhook.
Supported Features
- Authentication to Hashicorp vault using Kubernetes service-account
- RBAC implementation of vault using different policies of vault and association of policy with service-account
- Inject secret directly to pods/containers running inside Kubernetes
- Inject secret directly to pods/containers from AWS Secret Manager
- Authentication with AWS Secret Manager with access key and iam role
- Fetch secrets from Azure Key Vault and inject them in pods/containers
- Pod AD identity and Service principal based authentication in Azure
- Authentication with AWS Secret Manager with access key and iam role
- Authenticate and authorize using GCP service-account and annotations
- Secret injection in pods/containers from GCP Secret Manager
- Support regex to inject all secrets from a certain path of Vault
- Inject secrets directly to the process of container, i.e. after the injection you cannot read secrets from the environment variable
Architecture
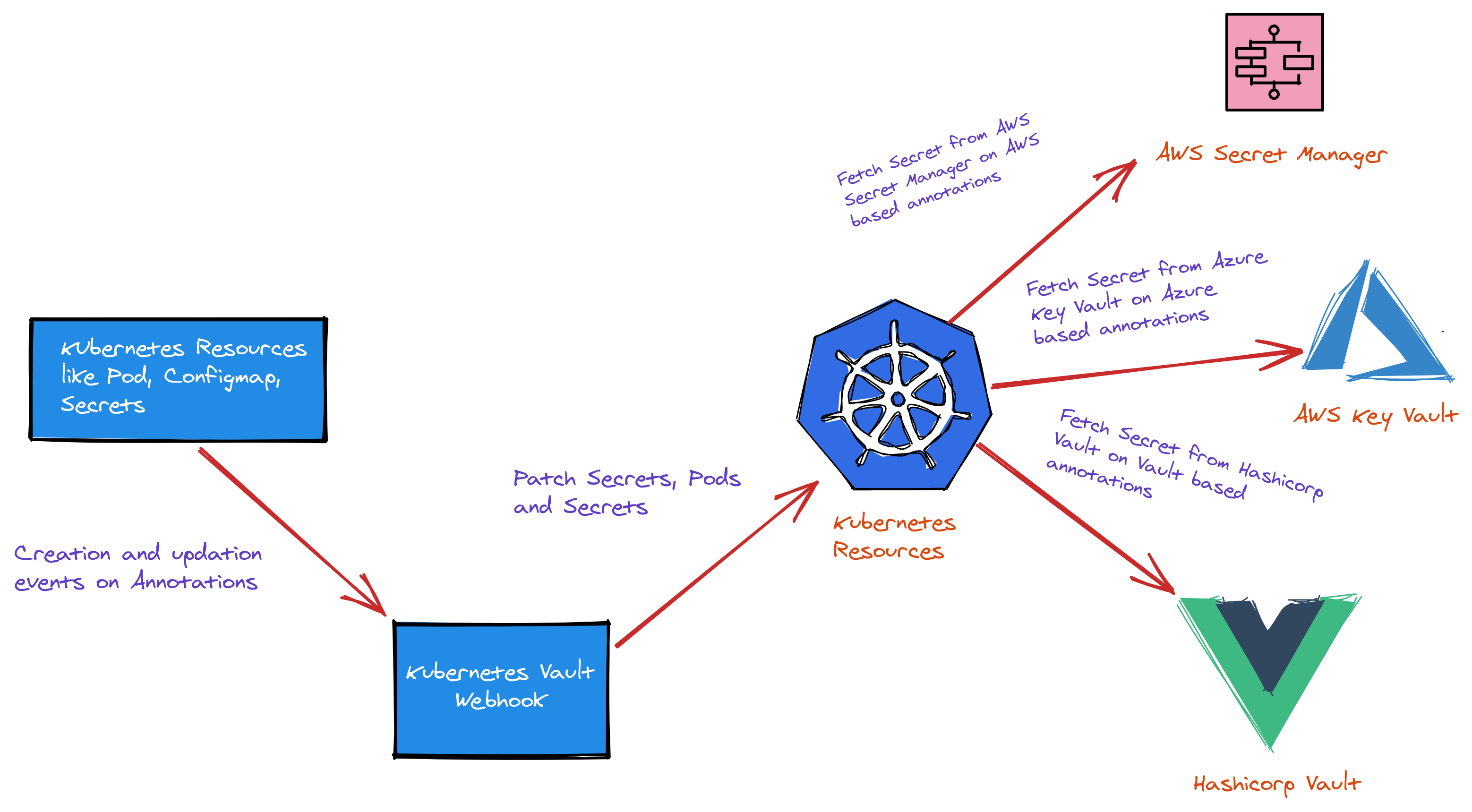
Installation
k8s-vault-webhook can easily get installed by using Helm. We just simple need to add the repository of our helm charts.
$ helm repo add ot-helm https://github.com/OT-CONTAINER-KIT/helm-charts
$ helm upgrade k8s-vault-webhook ot-helm/k8s-vault-webhook --namespace <namespace> --install
If you want to pass your custom values file while installing the chart, you can find the values file here
Quickstart
For setting up a quickstart environment for demo, you can start quickstart from here
Development
If you like to contribute to this project, you are more than welcome. Please see our DEVELOPMENT.md for details.
Release History
Please see our CHANGELOG.md for details.
Contact
If you have any suggestion or query. Contact us at



